Conference DEFCON 22. “Traveling on the dark side of the Internet. Introduction to Tor, Darknet and Bitcoin »
My name is Grifter, near my good friend Metacortex, we are from the DC801 group, which is based in Salt Lake City, Utah. We want to show something that looks pretty funny and take you on a tour of the dark side of the Internet.
We are both researchers who like to wander through the dark alleys, for example, in Tokyo, I do not even know where exactly this happened.
')
Metacortex: "In Shinjuku"!
Well, yes, it was in Shinjuku, I just did not pay attention to it. But this is exactly what we like to do, and we spent most of our trip on this occupation. I think the study of dark alleys is a good metaphor for describing the activities of hackers. We decided to take the train, and then we chose a random number, it was 6, we got off the train after 6 stops and just went where our eyes were. We did not know Japanese, could not read or speak this language, but just went for a walk. It was awesome, and we like that.
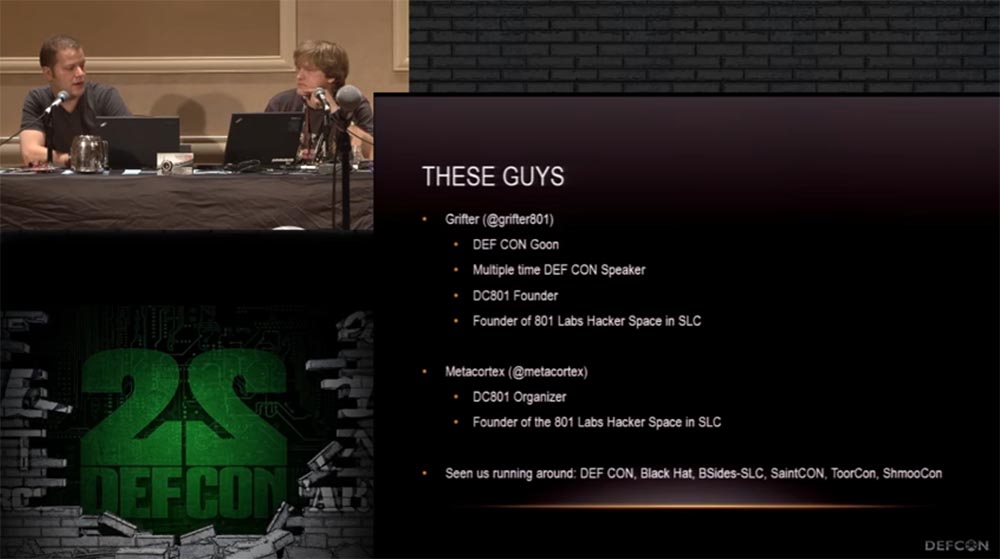
So, I, Griffer, the robber from DEFCON, who many times was the speaker of our conferences, is my sixth speech. I have been the creator of the DEFCON 801 group since ancient times and co-founder of the 801 Hacker Space Laboratory in Salt Lake City.
Metacortex: this is my first gig on DEFCON, so I'm a little worried. I am the assistant of this laboratory and the organizer of the 801st group, so if you get to Salt Lake City, come to visit, there you will find free drinks.
We can also be met at DEFCON, Black Hat, BSides-SLC, SaintCON and ToorCon conferences.
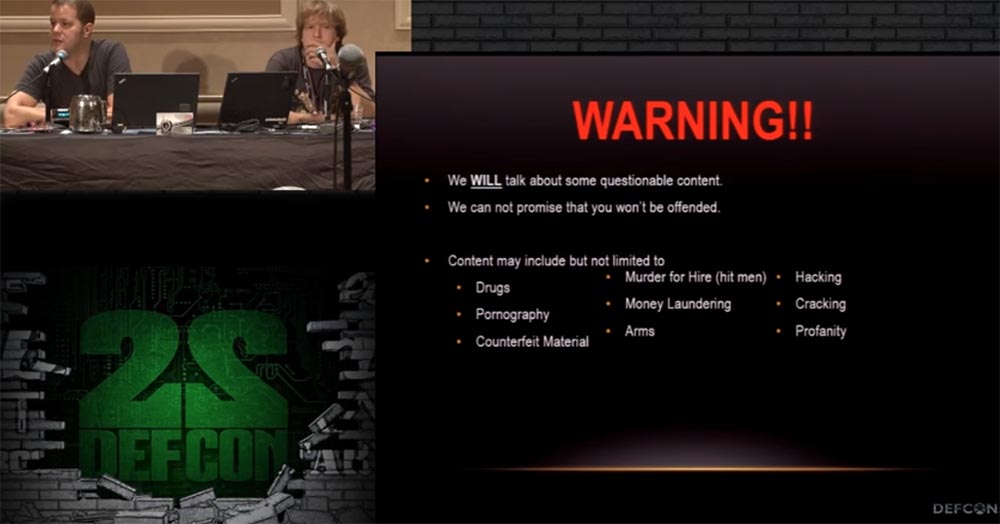
I'll start with a little caution. I know that this goes without saying, but we are still talking about rather dubious things. But who can determine what is doubtful and what can be proved? We cannot promise that what you heard will not offend you, because we can talk about drugs, assassinations, hacking, weapons, pornography, and if this makes you a sad panda, you should give up your place in this room to someone else.
Now Metacortex launched a clip on the screen. Who is a fan of this show, what is it called? "House of cards"? Yes exactly. For some reason, we have no sound. That is the sad panda. Help us, zvukoviki, all hope for you! Yeah, this is a bad cable ... this is USB for the sound card ... there is a problem ...
(Metacortex starts to look for another laptop cable, a guy comes on the scene trying to connect something, Griffer is humming into the microphone: “Come on guys, help, otherwise we look like headstuck assholes ...”).

Nothing happens, it was a bad idea!
But the video finally comes with sound:
"... 96% of the Internet, but in search engines most of it is unused, so we go here to find anything. Drugs, hired hackers.
- How did you get access to it?
- Pretty easy, I can show you if you want.
- Yes, of course, go on!
“Okay, the first thing you need is Thor.” Some people prefer ITP, but I think Top is better ... "
Yes, Thor is really much better!
And now we jumped on a slide about Darknet, because Metacortex continues to torment its laptop and can not find a desktop. Darknet is a really cool place, here you can hire hackers, wander around the black market and all that.

Finally, Metacortex got to its desktop, and we continue the slide show in order.
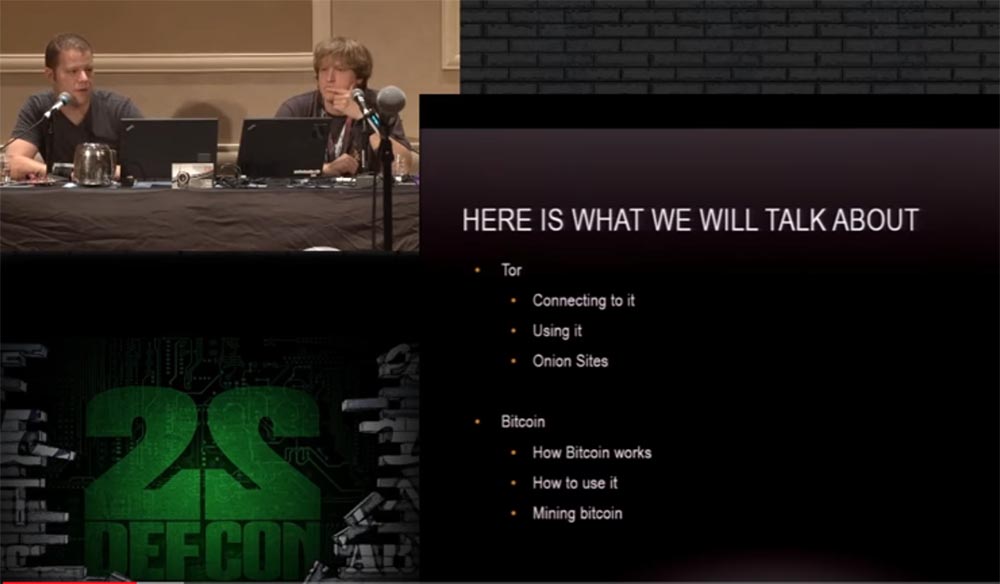
We will talk about Thor, how to connect with it and how to use it, and what Onion sites are. We will tell you about Bitcoin, how it works, how to use it and how to extract bitcoins.
Interesting information about this are on the Darknet forums, hacking forums and carding forums. Do not think that "Dark Network" is an extremely vile place. There are Internet platforms for people who want to avoid government censorship and freely discuss problems and things related to their country without fear of being raised in the middle of the night and wearing a black bag. I'll show you a couple of tricks, how to find them, remaining unidentified, and tell you about the Darknet search engines and the markets where you can order physical items. They will not be delivered to your home, but to another place from where these things can be taken away and no one will know who you are.
Metacortex: so, let's move on to the first topic and consider what Thor is, most of the DEFCON participants have probably heard about it.
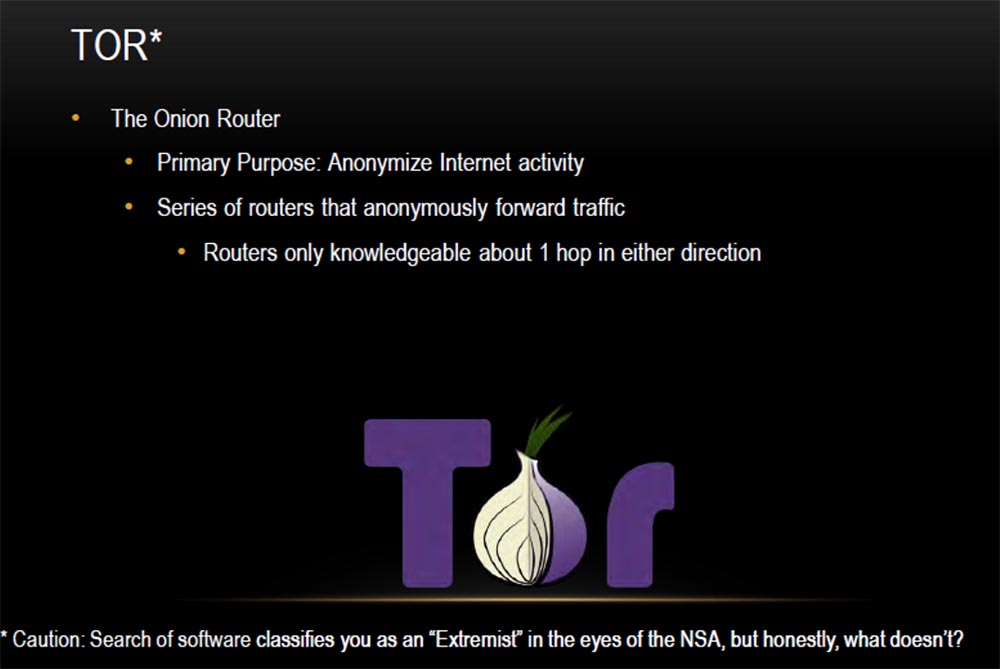
This is an onion router that makes your traffic anonymous. This is one of the most serious anonymizers, which is a series of routers that ensure the anonymity of your Internet activity.
Pay attention to the warning placed below: if you start looking for this anonymizer online, the NSA can put you on the list of extremists, but frankly, why not?
Griffinter: this does not happen so quickly, say, if you use the Thor and download something from there for 3 years, then yes, you will be included in the list. And now we will surely get to the first lines of this list, because we are talking about Thor here at DEFCON.
Metacortex: the next slide shows an excellent diagram showing the principle of Thor. The "+" symbol indicates the nodes of the Tor network (distributed servers), the green arrows indicate the encrypted data chains, and the red arrows indicate the unencrypted ones.

Alice uses a client called Thor, which chooses a random path to the correct server.
The only thing I don’t like here is the red arrow of Bob, which says that he uses unencrypted traffic, or, in the case of HTTP, it will be encrypted or unencrypted traffic.
We think that Thor works like this (shows a clip).

Griffer: we also, as it were, jump over these little things and boxes!
Metacortex: I also scream for joy when I manage to join the Torah!
So how do we connect to the Thor network? There are several different possibilities - you can use the Linux command line or a Mac command line or an application to install the binary codes for this thing. I prefer Linux, you see it on the slides, this is the / etc / tor / torr command, with which you specify the connection configuration. This starts the socks5 proxy server on your local host and allows you to start the Top client on the selected port, by default it is port 9050, after you connect to the Thor network.
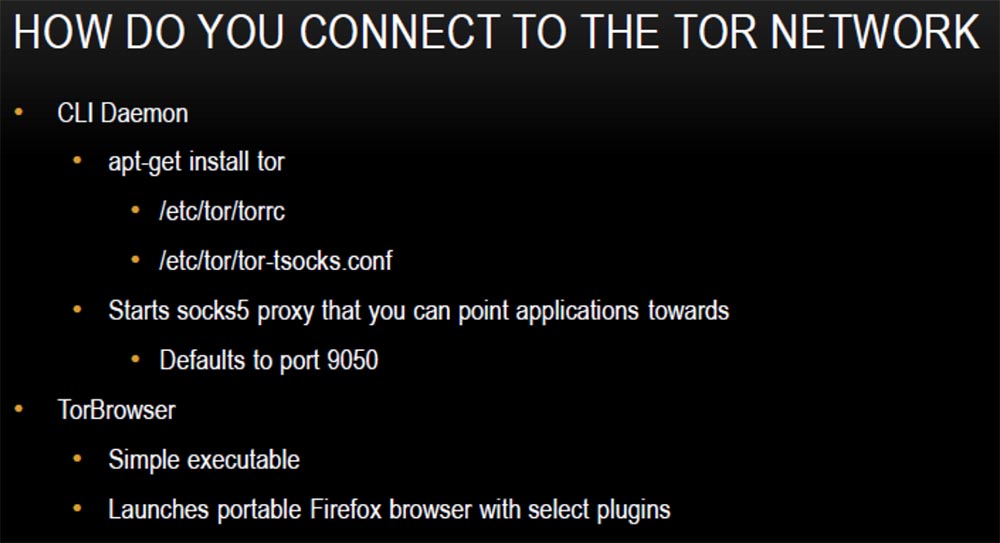
To work in the network you need to download and install the Thor client, it is very easy to use. It will connect and launch a portable version of the Firefox browser that will run under Thor. You can also use additional plugins.
We will quickly go over this issue, because we’ll show a demo, this is how your screen will look like after installation and connection to the Thor network.
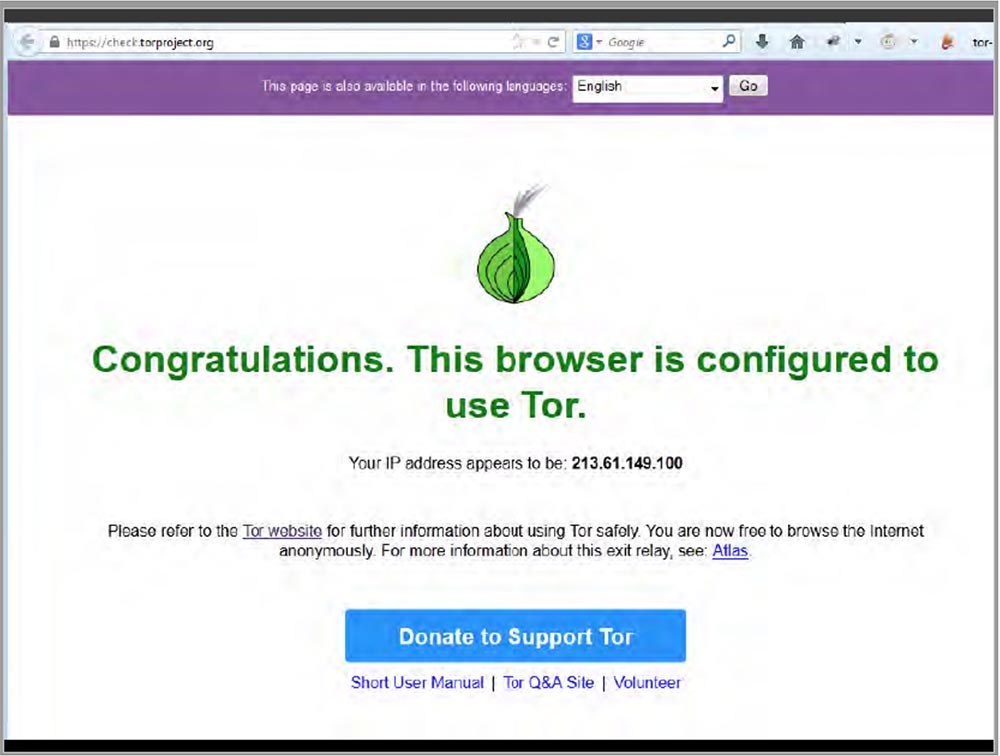
Today, the gods of video presentations are angry with me, but I’ll still try to show you how to connect your laptop to the Thor network. Here, a couple of seconds and you're done!
Griffer: you said that you yell like a jerk when you connect to Thor!
Metacortex publishes a cry of victory: "we see a message about the fact that this browser is configured to use Thor"!
I click the search bar and theoretically become an anonymous network user. After connecting to the browser, we see on the toolbar the icons of the already installed plug-ins.
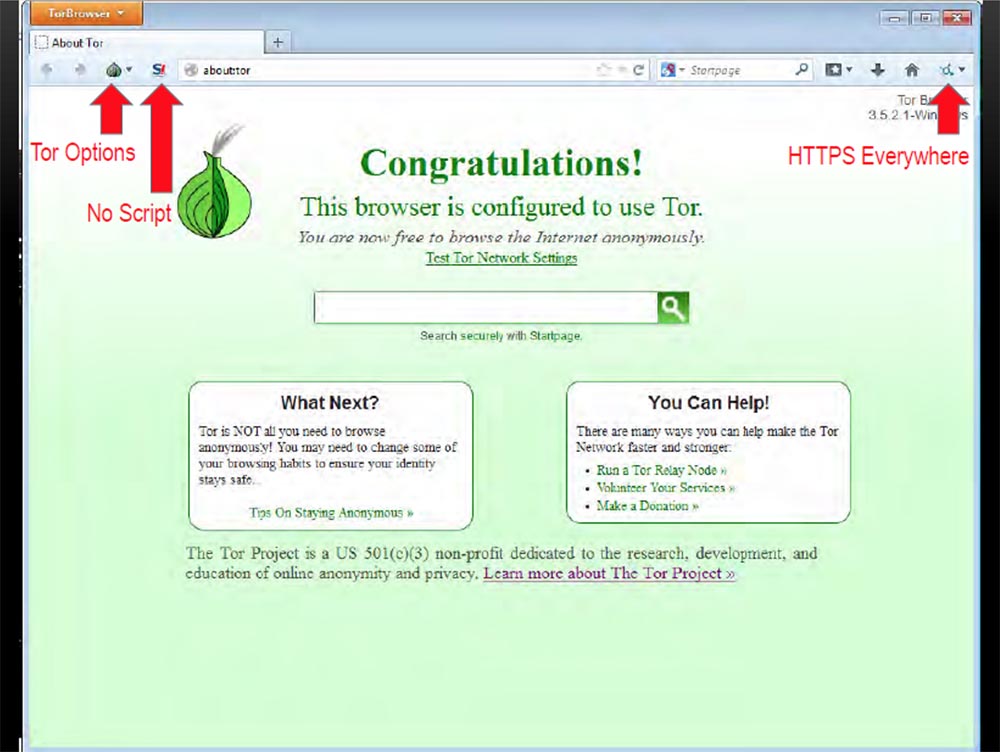
When you click the bulb icon, a drop-down menu will appear with options where you can customize the configuration of Thor. The S-shaped icon with an exclamation mark means “no script”, the use of this plug-in is very important, and the HTTPS Everywhere plug-in icon in the form of a small circle on the right shows that when browsing the pages, the HTTPS connection is used everywhere. This means that even when passing between Tor nodes in any direction, all our traffic will be encrypted.
Another way to ensure anonymity is to use the TAILS distribution. This is a Linux Live distribution based on Debian. It “wraps” all outgoing traffic in Tor and blocks non-anonymous traffic. This program does not leave any marks on the computer disk, so you can work completely anonymously. It works out-of-the-box and comes with pre-installed applications such as the HTTPS Everywhere plugin, OpenPGP, Pidgin OTR, Truecrypt and KeePassX, the most important of which is Truecrypt.
TAILS will transfer you to another interface - this is how it looks if you start it in Normal mode. This is the standard Debian desktop, nothing fun.
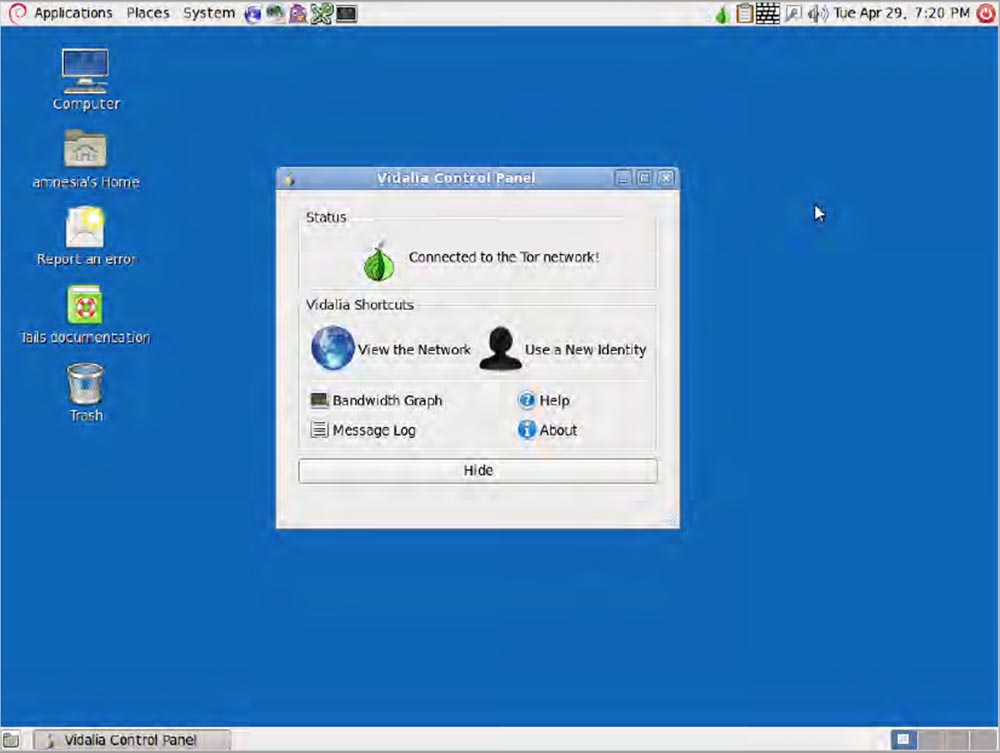
But you can easily transfer it to XP mode. If you are sitting at a table in a cafe and doing horrible hacker things, no one will pay attention to you if there is a regular Windows XP desktop on the monitor of your laptop.
So, when we connected to the Internet via Thor, we can do very interesting things:
Thor services are wonderful things that allow using Darknet, that is, sites that live exclusively in the Thor network and which cannot be reached without it. You will not be able to track who owns such a site if you do not have its trust. Most Darknet sites have an onion address. The Top documentation on the site describes how this all works.
Finding hidden services is the most difficult thing when you enter Thor.
This is Hidden Wiki Hidden Wikipedia, most people love to use it, but I found extremely outdated information, and most of the links in it are damaged or do not work. But you can still find "gems" in it.
Torfind and TorSearch are Tor search engines.
Gram is another search engine Tor, made in the style of the Google search engine, it will help you find any item on the Darknet markets, just enter its name in the search box.
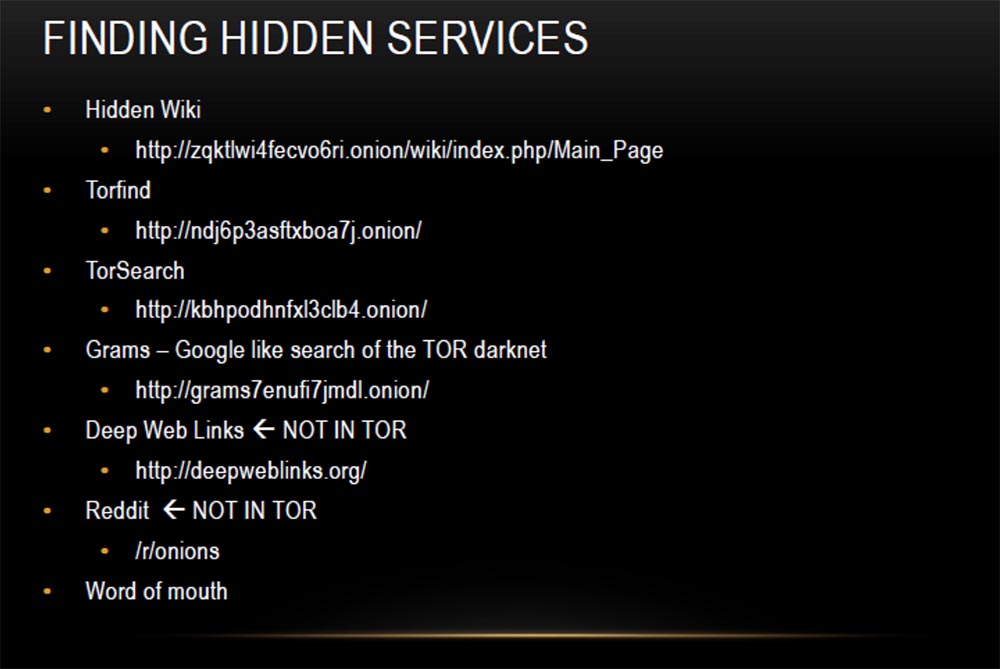
Deep Web Links and Reddit are not in the Top network. They do not have onion addresses, but they do have a lot of word of mouth links. Many people spread the addresses of "onion" sites, so to speak, word of mouth, sending them to their friends. There are also “by interest” sites, such as The Pirate Bay, where you can download various content. It is therefore bad if your Bittorrent does not support working with onion sites. Also note that if you are trying to download illegal torrents, it is better to do it through Thor, because uploading files from Pirate Bay does not mean that you remain anonymous.
My favorite “Killing Market” is a web site created on the basis of “popular finance”. Now, regardless of whether it is legal or not, I doubt it. The essence of the market is that you pay bitcoins for someone to kill someone, and everyone around you starts to put bitcoins in it, and if someone can prove that he is the killer, then they give him all the collected bitcoins . There were rather funny names in this list, but, unfortunately, I cannot show it to you.
Another useful resource is the Rent-A-Hacker Hacker Hire Exchange, where you can order hacking anything for an appropriate bitcoin reward.
Next, I provide addresses of useful forums for you. TCF is a Thor carding forum, it is dedicated to hacking bank cards. Access to the database costs $ 50 so that spammers do not climb there. Paying for the entrance, you can buy credit card numbers, identification data and other hacking information, later we will talk about this in more detail.
Intellectual Exchange, or Intel Exchange, is visited by many people. This forum is dedicated to the exchange of various information that people share with each other, while remaining anonymous. Here, basically, all the “secret knowledge” troll, discuss the Deep web and the Miranda network, it's pretty fun. There is also a lot of useful information.
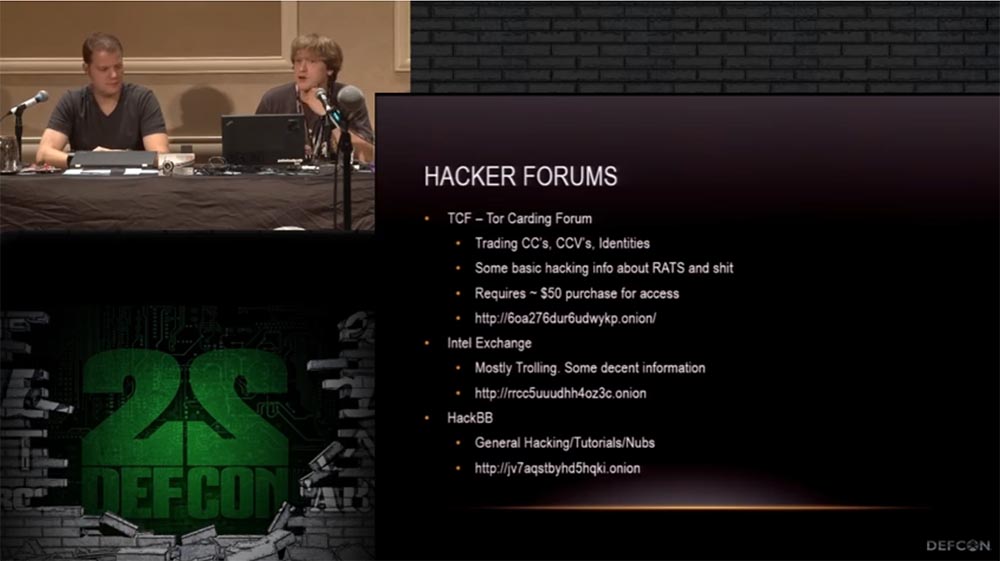
HackBB is a forum of a slightly different kind, here they make simple executive files that allow you to gain hidden control over anything.
Network markets are places where people are interested in buying just such things. You can check the Darknet markets, on the side of the page there is their regularly updated list with status, regardless of whether they are considered credible, and quality assessment. This is very relevant information.
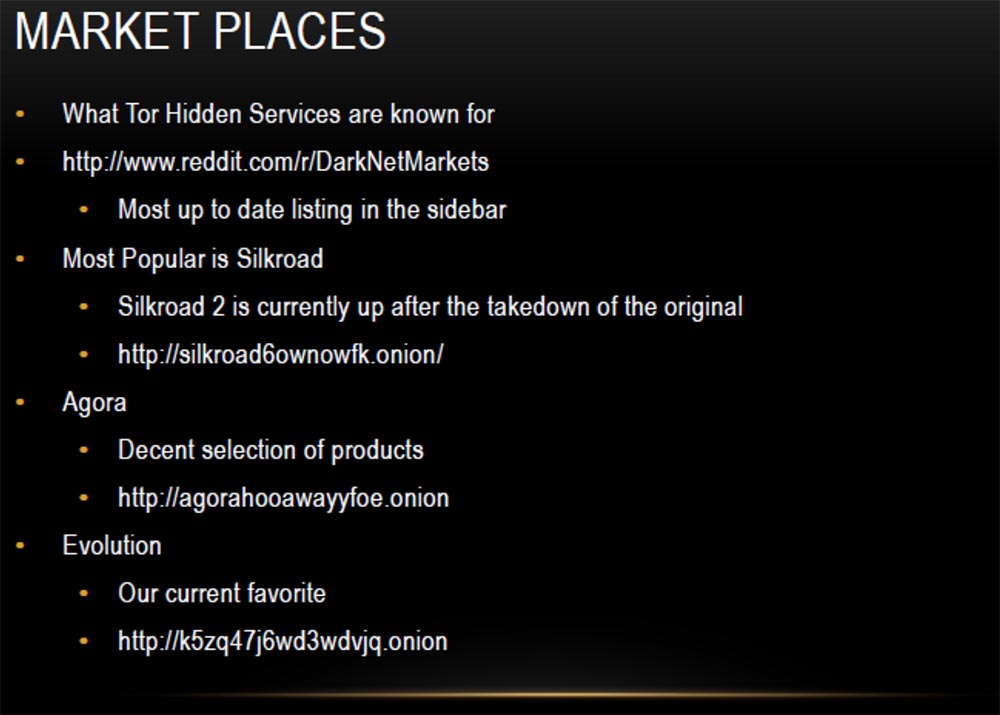
The most popular is the second version of Silkroad, or Silk Road, followed by Agora with a decent selection of products, but I like Evolution most of all, later I'll tell you more about it. Now I will give you a small demonstration of how to get to the Silkroad market. To do this, I copy the link and paste it into the Thor browser line. Done, now you need to enter your username and password.
This is the main page of Silkroad.
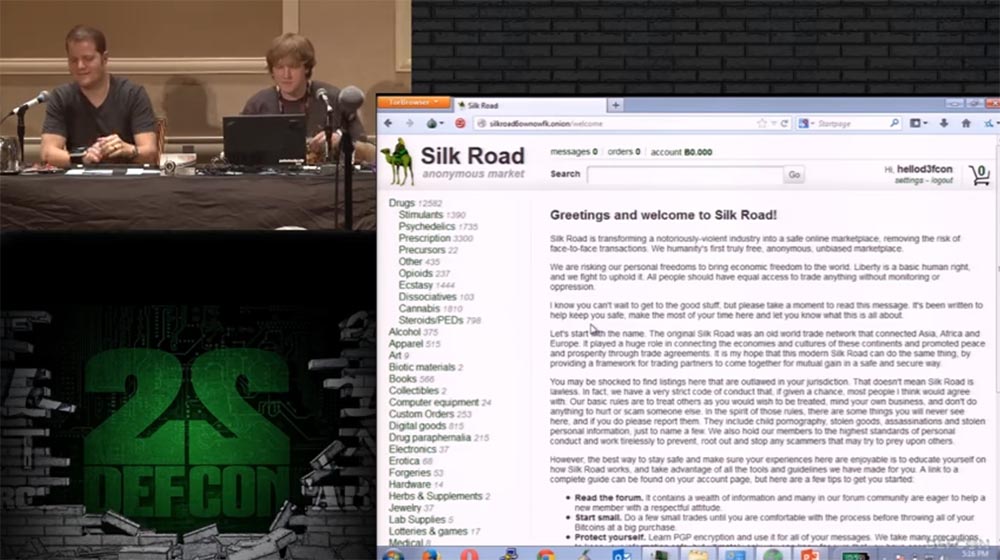
On the left you see a list of drugs that many people can find here, alcohol and more interesting things, such as electronics. We go to the electronics offer page, its range is updated all the time, and we do not know what we will find here today.
As you can see, here they offer anonymous SIM-cards, hacked Wi-Fi, MacBook Pro with a 13-inch screen, Virtual Honeyports book, quad-copter drone, external drives, Hackers Underground directory, and so on.
Griffer: as you can see, here you can find a lot of different things, some of them are worth their money, some are not, and you have to “sift” the entire range to find the thing you need. I will say this: if you do not want to lose your bitcoins, it is better not to waste them.
Metacortex: further follow the TCF carding sites and forums. As I said, for $ 50 you can buy credit card numbers, identification data, dates of birth, social security numbers. The actual cost of these things varies depending on inflation or bitcoin deflation, but in any case, the use of such data will cost you $ 50. The SS site does not look very convenient for purchases, and I do not know how legitimate it is, but here you can ask about such things. Now I will try to enter the TCF website at this link .

Here you also need to enter a username and password. Let's see if we can buy the stolen information. There is a section of virtual cards and physical bank cards.
Griffer: we do not contribute to the dissemination and use of stolen personal information, we just want to show how valuable your data is to other people. Keep this in mind when Metacortex calls them cost. From media reports, you know how topical the problem of identity theft is and how the data of millions of credit cards from various stores are stolen, and this site eloquently testifies to the activities of such intermediaries.
Metacortex: I have never seen such low prices - a dollar for each card!
Griffer: You are worth $ 1!
Metacortex: here is the product page, here you have the credit card number, information about the card’s expiration date, CVV code, card name, country, state, city, address and postal code. $ 6, but if you need a European card - $ 10. Everybody hates us!
Griffer: You ask, what is the chance that the card seller will not be torn apart? The chances are quite small, because there is the same system of reviews as, for example, on Amazon, where people write that they purchased goods from this seller, and used it for a while, and recommend this seller as verified.
For us, these markets are not consumer, but research interest. We come here to look at the dynamics of prices, what they sell, how they sell and how this system works. And when we start a conversation with the seller, it is completely open to dialogue, because it also works anonymously.
Metacortex: we continue further, and again I can not find the right video. There are still very interesting things for me, such as fake documents.
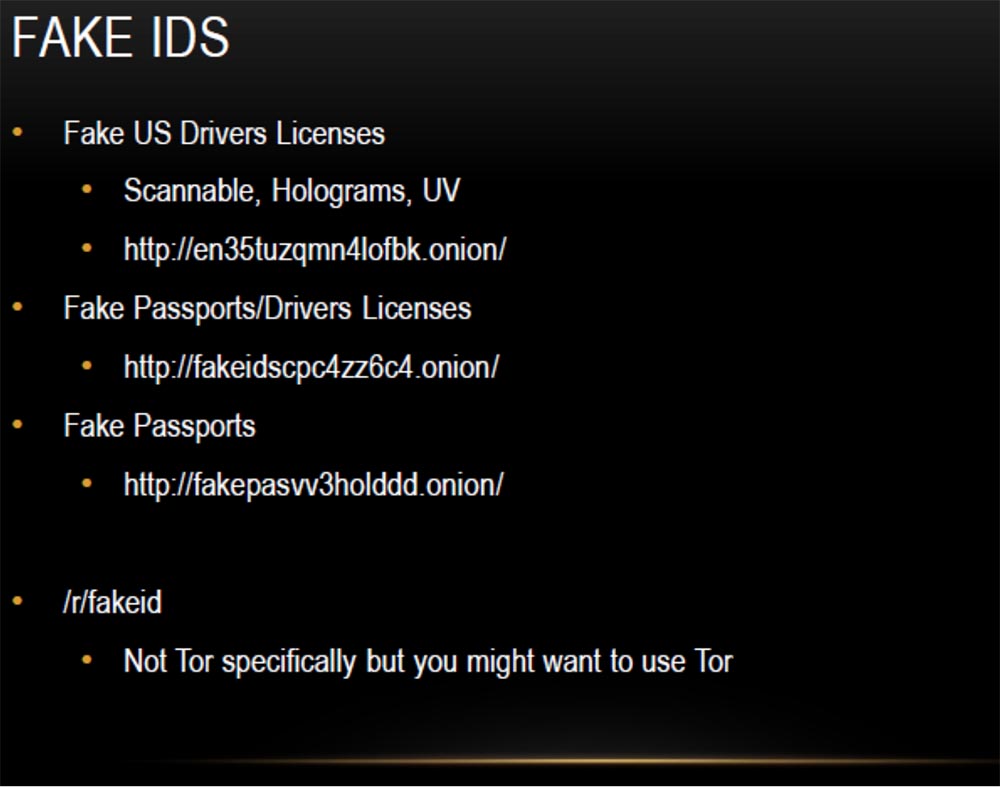
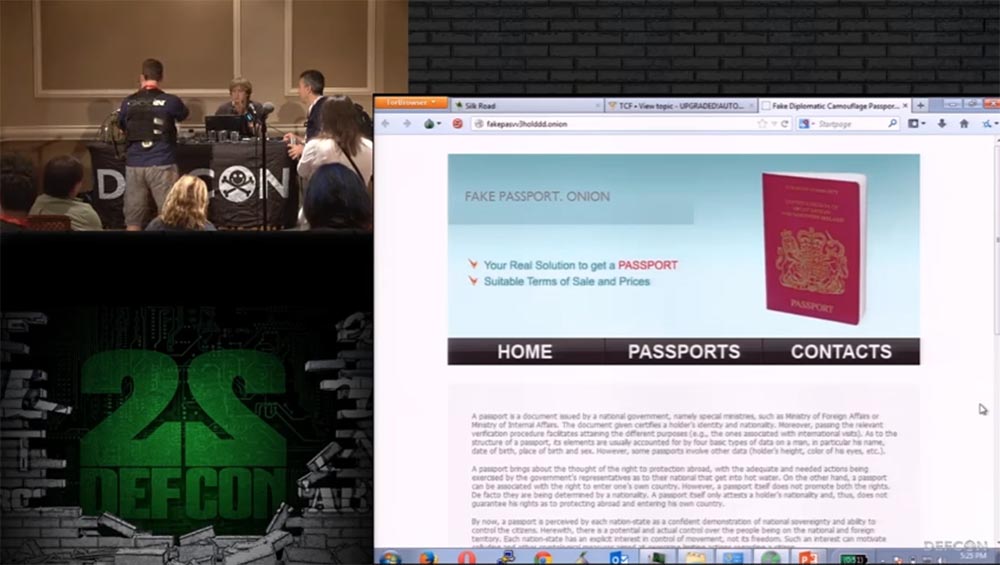
On the first site you can buy fake US licenses, which can be safely scanned, they have a hologram and UV tags. On the second, fake passports and driver's licenses are sold, on the third, fake passports are needed so that you can disappear to commit any unseemly deeds. I have heard that all fake documents are completely legal, because they are made with the highest quality, and you do not need to use Thor when buying them, but I would advise you to use Thor for this.
This is the main page of the FakeID passport sale site. You see that here you can buy passports of all these beautiful countries: Australia, Austria, Belgium, Canada, Finland, France, Germany, Japan, Switzerland, the UK and the USA.
Griffer: Now we will see that the US passport is as expensive as a $ 1 credit card.
Metacortex: here is a scan of the passport and its description, it is written that it consists of 28 pages, has holographic marks and lamination, it looks absolutely legal, people can take their picture, and they will place it in the passport with a UV mark. Theoretically, you can send them all the necessary information and get a ready passport.
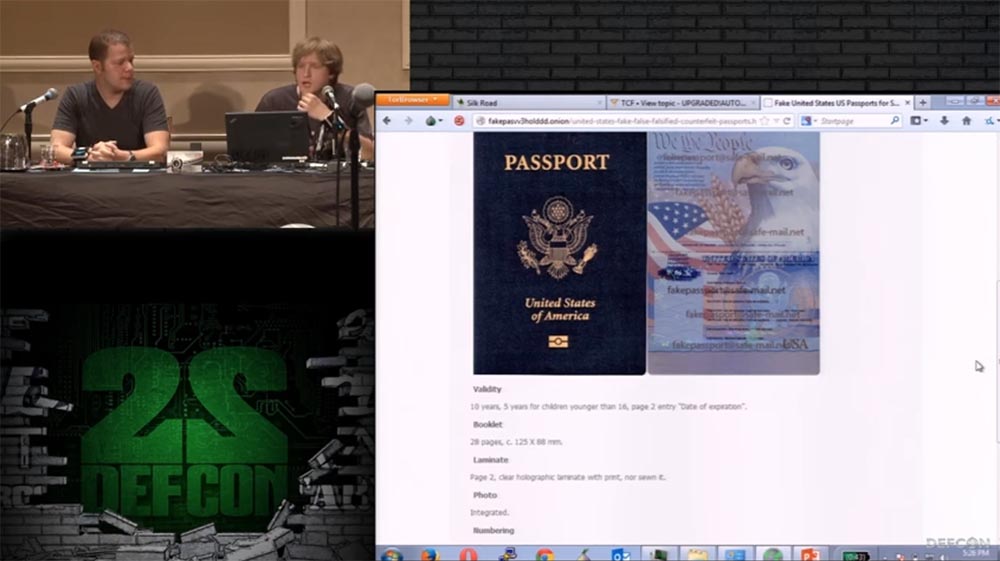
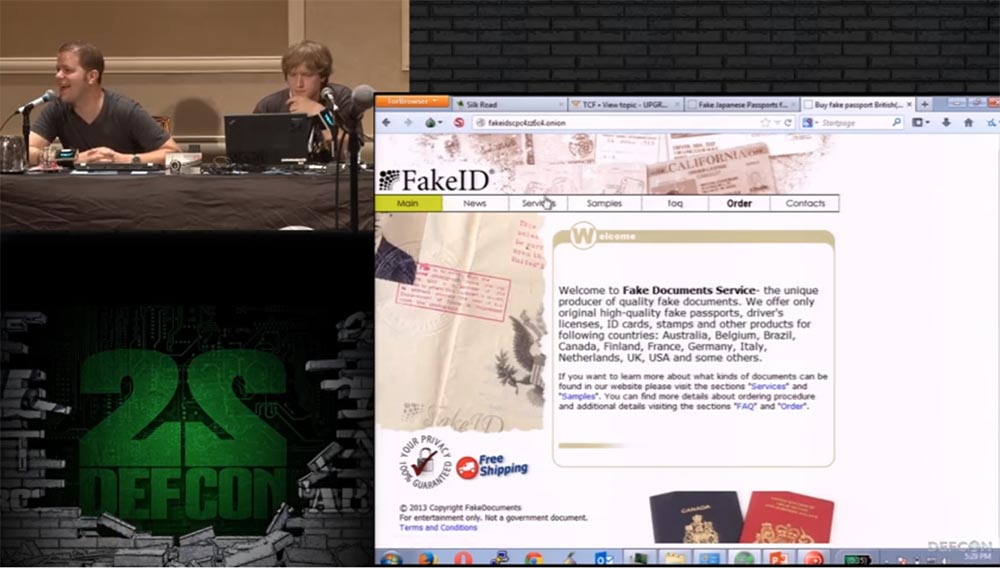
It is worth making it $ 1,000. For a Japanese passport asking $ 700. And now we went to the site where they sell a driver's license. Here are listed several states, the cost of a driver's license for each of these states is $ 200. Let's try to go to the last site.
Greater: “Free Shipping” is written here! !
: , . 700 . , .
25-110 .
: , , . , , , , , , .
: , ? « ».
: -, ! .
: , , ?
, . Defcoin', , (). , Escrow, , Escrow . , , OPSEC.
, , . «tumbler», . — , , , . , , Tumbler , . , , . ( , ), .
, , - . , TOR . - , . , , , Darknet. , .
, . «» JavaScript, Firefox, XSS , , .
, . , , . , Bitcoin. . , , , .
, OPSEC.
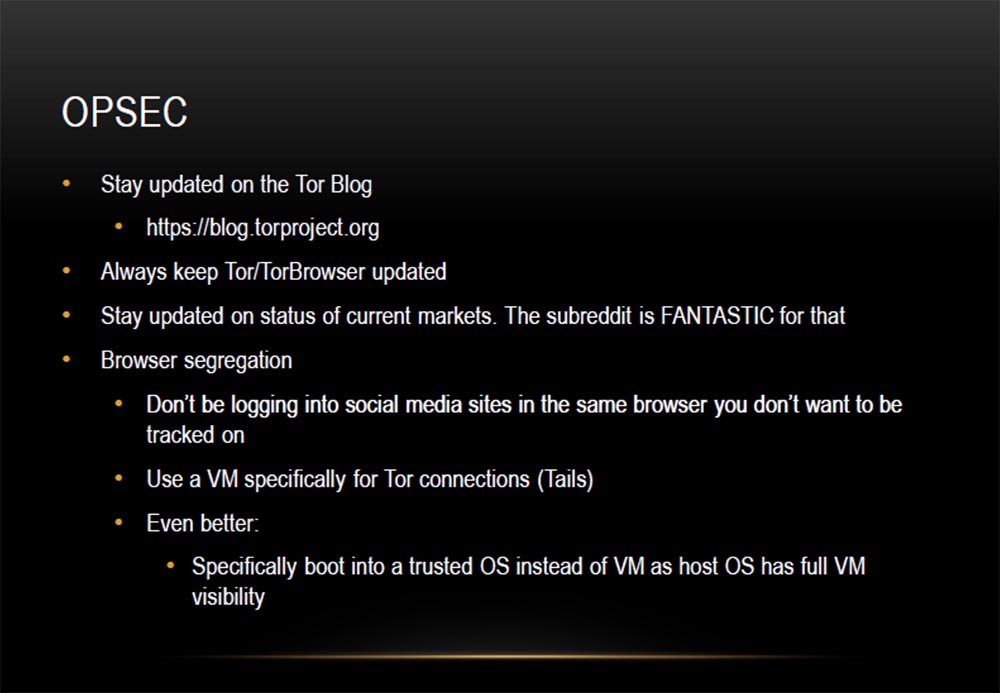
: , . -, , . , , Tails. , , . -, Tor. .
Subreddit . , «» . , . , Facebook , Darkmarket , , .
VM (Tails). Tails. Windows 8. , , - . , Tails-. , Tails , DEFCON101 . .
: , .
: , , .
: , . .
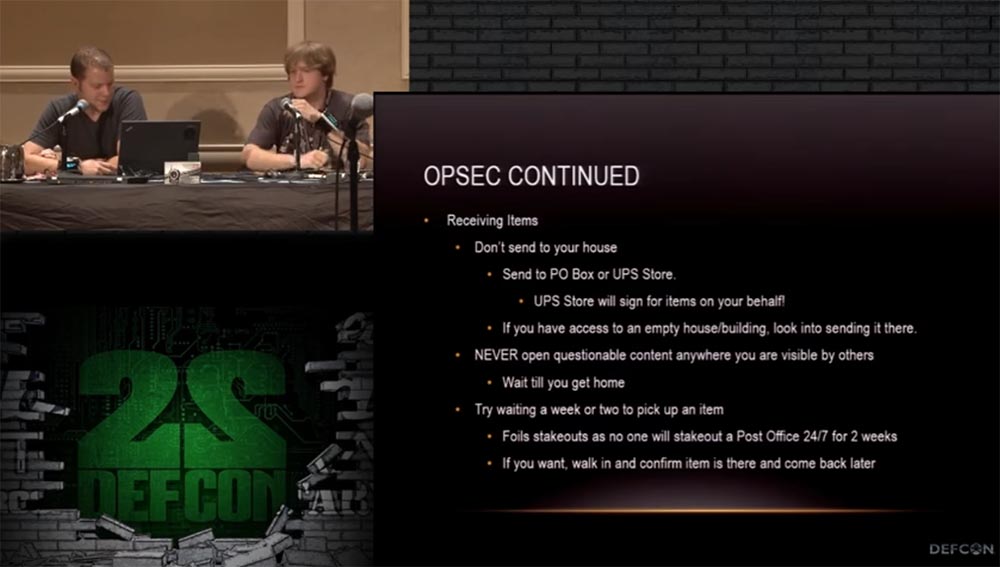
Darkmarket . PO Box UPS. , UPS ! - , . - , , .
, . , , , .
: , , « ». , .
, « ». Baby Monitor. GSM, SIM-, . , , , . . , , , , . SMS 1111, – 0000. «», . , , «» .
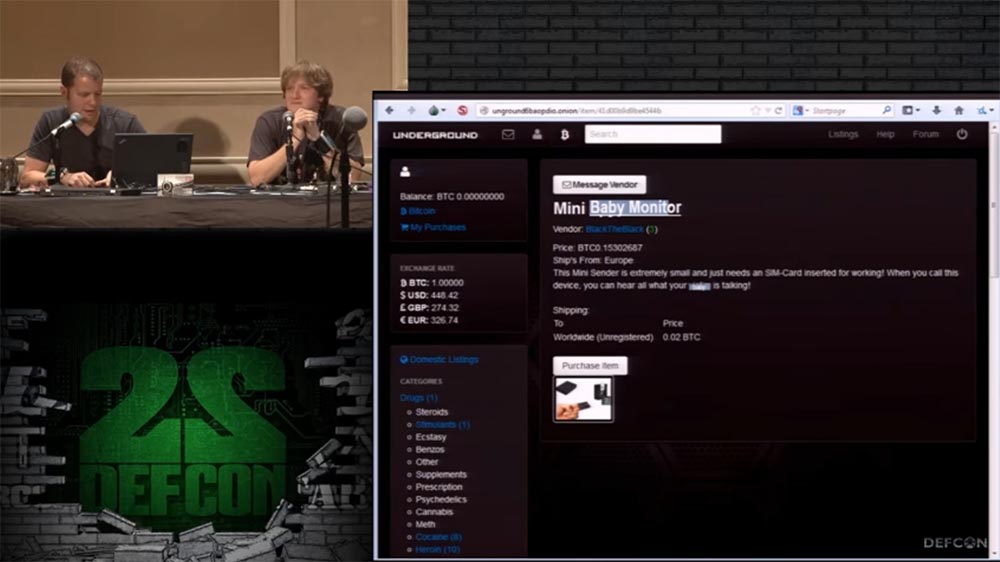
- USPS.

, .
, , , « ». , – . , , , « ». . , Darknet .
, , Darknet , , , , . , , . , , , , Darknet . , .
Darknet , . , , , , , , . , .
, . , , .
, !

--, c , !
, . ? ? , 30% entry-level , : VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps $20 ? ( RAID1 RAID10, 24 40GB DDR4).
Dell R730xd 2 ? 2 Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 $249 ! . c Dell R730xd 5-2650 v4 9000 ?

We are both researchers who like to wander through the dark alleys, for example, in Tokyo, I do not even know where exactly this happened.
')
Metacortex: "In Shinjuku"!
Well, yes, it was in Shinjuku, I just did not pay attention to it. But this is exactly what we like to do, and we spent most of our trip on this occupation. I think the study of dark alleys is a good metaphor for describing the activities of hackers. We decided to take the train, and then we chose a random number, it was 6, we got off the train after 6 stops and just went where our eyes were. We did not know Japanese, could not read or speak this language, but just went for a walk. It was awesome, and we like that.
So, I, Griffer, the robber from DEFCON, who many times was the speaker of our conferences, is my sixth speech. I have been the creator of the DEFCON 801 group since ancient times and co-founder of the 801 Hacker Space Laboratory in Salt Lake City.
Metacortex: this is my first gig on DEFCON, so I'm a little worried. I am the assistant of this laboratory and the organizer of the 801st group, so if you get to Salt Lake City, come to visit, there you will find free drinks.
We can also be met at DEFCON, Black Hat, BSides-SLC, SaintCON and ToorCon conferences.
I'll start with a little caution. I know that this goes without saying, but we are still talking about rather dubious things. But who can determine what is doubtful and what can be proved? We cannot promise that what you heard will not offend you, because we can talk about drugs, assassinations, hacking, weapons, pornography, and if this makes you a sad panda, you should give up your place in this room to someone else.

Now Metacortex launched a clip on the screen. Who is a fan of this show, what is it called? "House of cards"? Yes exactly. For some reason, we have no sound. That is the sad panda. Help us, zvukoviki, all hope for you! Yeah, this is a bad cable ... this is USB for the sound card ... there is a problem ...
(Metacortex starts to look for another laptop cable, a guy comes on the scene trying to connect something, Griffer is humming into the microphone: “Come on guys, help, otherwise we look like headstuck assholes ...”).

Nothing happens, it was a bad idea!
But the video finally comes with sound:
"... 96% of the Internet, but in search engines most of it is unused, so we go here to find anything. Drugs, hired hackers.
- How did you get access to it?
- Pretty easy, I can show you if you want.
- Yes, of course, go on!
“Okay, the first thing you need is Thor.” Some people prefer ITP, but I think Top is better ... "
Yes, Thor is really much better!
And now we jumped on a slide about Darknet, because Metacortex continues to torment its laptop and can not find a desktop. Darknet is a really cool place, here you can hire hackers, wander around the black market and all that.

Finally, Metacortex got to its desktop, and we continue the slide show in order.

We will talk about Thor, how to connect with it and how to use it, and what Onion sites are. We will tell you about Bitcoin, how it works, how to use it and how to extract bitcoins.
Interesting information about this are on the Darknet forums, hacking forums and carding forums. Do not think that "Dark Network" is an extremely vile place. There are Internet platforms for people who want to avoid government censorship and freely discuss problems and things related to their country without fear of being raised in the middle of the night and wearing a black bag. I'll show you a couple of tricks, how to find them, remaining unidentified, and tell you about the Darknet search engines and the markets where you can order physical items. They will not be delivered to your home, but to another place from where these things can be taken away and no one will know who you are.
Metacortex: so, let's move on to the first topic and consider what Thor is, most of the DEFCON participants have probably heard about it.

This is an onion router that makes your traffic anonymous. This is one of the most serious anonymizers, which is a series of routers that ensure the anonymity of your Internet activity.
Pay attention to the warning placed below: if you start looking for this anonymizer online, the NSA can put you on the list of extremists, but frankly, why not?
Griffinter: this does not happen so quickly, say, if you use the Thor and download something from there for 3 years, then yes, you will be included in the list. And now we will surely get to the first lines of this list, because we are talking about Thor here at DEFCON.
Metacortex: the next slide shows an excellent diagram showing the principle of Thor. The "+" symbol indicates the nodes of the Tor network (distributed servers), the green arrows indicate the encrypted data chains, and the red arrows indicate the unencrypted ones.

Alice uses a client called Thor, which chooses a random path to the correct server.
The only thing I don’t like here is the red arrow of Bob, which says that he uses unencrypted traffic, or, in the case of HTTP, it will be encrypted or unencrypted traffic.
We think that Thor works like this (shows a clip).

Griffer: we also, as it were, jump over these little things and boxes!
Metacortex: I also scream for joy when I manage to join the Torah!
So how do we connect to the Thor network? There are several different possibilities - you can use the Linux command line or a Mac command line or an application to install the binary codes for this thing. I prefer Linux, you see it on the slides, this is the / etc / tor / torr command, with which you specify the connection configuration. This starts the socks5 proxy server on your local host and allows you to start the Top client on the selected port, by default it is port 9050, after you connect to the Thor network.

To work in the network you need to download and install the Thor client, it is very easy to use. It will connect and launch a portable version of the Firefox browser that will run under Thor. You can also use additional plugins.
We will quickly go over this issue, because we’ll show a demo, this is how your screen will look like after installation and connection to the Thor network.

Today, the gods of video presentations are angry with me, but I’ll still try to show you how to connect your laptop to the Thor network. Here, a couple of seconds and you're done!

Griffer: you said that you yell like a jerk when you connect to Thor!
Metacortex publishes a cry of victory: "we see a message about the fact that this browser is configured to use Thor"!
I click the search bar and theoretically become an anonymous network user. After connecting to the browser, we see on the toolbar the icons of the already installed plug-ins.

When you click the bulb icon, a drop-down menu will appear with options where you can customize the configuration of Thor. The S-shaped icon with an exclamation mark means “no script”, the use of this plug-in is very important, and the HTTPS Everywhere plug-in icon in the form of a small circle on the right shows that when browsing the pages, the HTTPS connection is used everywhere. This means that even when passing between Tor nodes in any direction, all our traffic will be encrypted.
Another way to ensure anonymity is to use the TAILS distribution. This is a Linux Live distribution based on Debian. It “wraps” all outgoing traffic in Tor and blocks non-anonymous traffic. This program does not leave any marks on the computer disk, so you can work completely anonymously. It works out-of-the-box and comes with pre-installed applications such as the HTTPS Everywhere plugin, OpenPGP, Pidgin OTR, Truecrypt and KeePassX, the most important of which is Truecrypt.
TAILS will transfer you to another interface - this is how it looks if you start it in Normal mode. This is the standard Debian desktop, nothing fun.

But you can easily transfer it to XP mode. If you are sitting at a table in a cafe and doing horrible hacker things, no one will pay attention to you if there is a regular Windows XP desktop on the monitor of your laptop.

So, when we connected to the Internet via Thor, we can do very interesting things:
- anonymously surf the internet;
- enter the selected resource through the tunnel laid by Thor;
- fight censorship;
- criticize the government and its officials;
- just remain anonymous;
- use the services of Torah.
Thor services are wonderful things that allow using Darknet, that is, sites that live exclusively in the Thor network and which cannot be reached without it. You will not be able to track who owns such a site if you do not have its trust. Most Darknet sites have an onion address. The Top documentation on the site describes how this all works.
Finding hidden services is the most difficult thing when you enter Thor.
This is Hidden Wiki Hidden Wikipedia, most people love to use it, but I found extremely outdated information, and most of the links in it are damaged or do not work. But you can still find "gems" in it.
Torfind and TorSearch are Tor search engines.
Gram is another search engine Tor, made in the style of the Google search engine, it will help you find any item on the Darknet markets, just enter its name in the search box.

Deep Web Links and Reddit are not in the Top network. They do not have onion addresses, but they do have a lot of word of mouth links. Many people spread the addresses of "onion" sites, so to speak, word of mouth, sending them to their friends. There are also “by interest” sites, such as The Pirate Bay, where you can download various content. It is therefore bad if your Bittorrent does not support working with onion sites. Also note that if you are trying to download illegal torrents, it is better to do it through Thor, because uploading files from Pirate Bay does not mean that you remain anonymous.
My favorite “Killing Market” is a web site created on the basis of “popular finance”. Now, regardless of whether it is legal or not, I doubt it. The essence of the market is that you pay bitcoins for someone to kill someone, and everyone around you starts to put bitcoins in it, and if someone can prove that he is the killer, then they give him all the collected bitcoins . There were rather funny names in this list, but, unfortunately, I cannot show it to you.
Another useful resource is the Rent-A-Hacker Hacker Hire Exchange, where you can order hacking anything for an appropriate bitcoin reward.
Next, I provide addresses of useful forums for you. TCF is a Thor carding forum, it is dedicated to hacking bank cards. Access to the database costs $ 50 so that spammers do not climb there. Paying for the entrance, you can buy credit card numbers, identification data and other hacking information, later we will talk about this in more detail.
Intellectual Exchange, or Intel Exchange, is visited by many people. This forum is dedicated to the exchange of various information that people share with each other, while remaining anonymous. Here, basically, all the “secret knowledge” troll, discuss the Deep web and the Miranda network, it's pretty fun. There is also a lot of useful information.

HackBB is a forum of a slightly different kind, here they make simple executive files that allow you to gain hidden control over anything.
Network markets are places where people are interested in buying just such things. You can check the Darknet markets, on the side of the page there is their regularly updated list with status, regardless of whether they are considered credible, and quality assessment. This is very relevant information.

The most popular is the second version of Silkroad, or Silk Road, followed by Agora with a decent selection of products, but I like Evolution most of all, later I'll tell you more about it. Now I will give you a small demonstration of how to get to the Silkroad market. To do this, I copy the link and paste it into the Thor browser line. Done, now you need to enter your username and password.

This is the main page of Silkroad.

On the left you see a list of drugs that many people can find here, alcohol and more interesting things, such as electronics. We go to the electronics offer page, its range is updated all the time, and we do not know what we will find here today.
As you can see, here they offer anonymous SIM-cards, hacked Wi-Fi, MacBook Pro with a 13-inch screen, Virtual Honeyports book, quad-copter drone, external drives, Hackers Underground directory, and so on.
Griffer: as you can see, here you can find a lot of different things, some of them are worth their money, some are not, and you have to “sift” the entire range to find the thing you need. I will say this: if you do not want to lose your bitcoins, it is better not to waste them.
Metacortex: further follow the TCF carding sites and forums. As I said, for $ 50 you can buy credit card numbers, identification data, dates of birth, social security numbers. The actual cost of these things varies depending on inflation or bitcoin deflation, but in any case, the use of such data will cost you $ 50. The SS site does not look very convenient for purchases, and I do not know how legitimate it is, but here you can ask about such things. Now I will try to enter the TCF website at this link .

Here you also need to enter a username and password. Let's see if we can buy the stolen information. There is a section of virtual cards and physical bank cards.
Griffer: we do not contribute to the dissemination and use of stolen personal information, we just want to show how valuable your data is to other people. Keep this in mind when Metacortex calls them cost. From media reports, you know how topical the problem of identity theft is and how the data of millions of credit cards from various stores are stolen, and this site eloquently testifies to the activities of such intermediaries.
Metacortex: I have never seen such low prices - a dollar for each card!
Griffer: You are worth $ 1!
Metacortex: here is the product page, here you have the credit card number, information about the card’s expiration date, CVV code, card name, country, state, city, address and postal code. $ 6, but if you need a European card - $ 10. Everybody hates us!
Griffer: You ask, what is the chance that the card seller will not be torn apart? The chances are quite small, because there is the same system of reviews as, for example, on Amazon, where people write that they purchased goods from this seller, and used it for a while, and recommend this seller as verified.
For us, these markets are not consumer, but research interest. We come here to look at the dynamics of prices, what they sell, how they sell and how this system works. And when we start a conversation with the seller, it is completely open to dialogue, because it also works anonymously.
Metacortex: we continue further, and again I can not find the right video. There are still very interesting things for me, such as fake documents.

On the first site you can buy fake US licenses, which can be safely scanned, they have a hologram and UV tags. On the second, fake passports and driver's licenses are sold, on the third, fake passports are needed so that you can disappear to commit any unseemly deeds. I have heard that all fake documents are completely legal, because they are made with the highest quality, and you do not need to use Thor when buying them, but I would advise you to use Thor for this.
This is the main page of the FakeID passport sale site. You see that here you can buy passports of all these beautiful countries: Australia, Austria, Belgium, Canada, Finland, France, Germany, Japan, Switzerland, the UK and the USA.
Griffer: Now we will see that the US passport is as expensive as a $ 1 credit card.

Metacortex: here is a scan of the passport and its description, it is written that it consists of 28 pages, has holographic marks and lamination, it looks absolutely legal, people can take their picture, and they will place it in the passport with a UV mark. Theoretically, you can send them all the necessary information and get a ready passport.

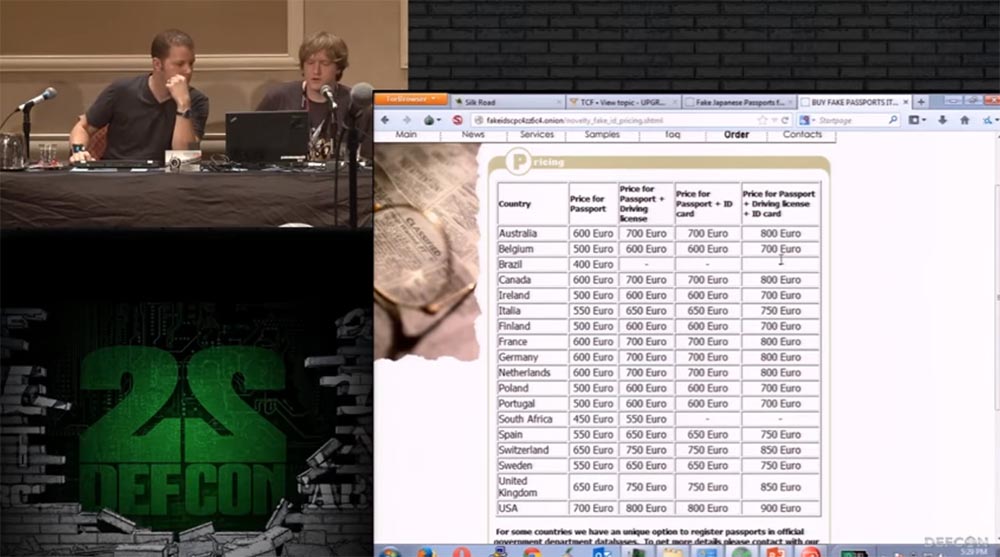
It is worth making it $ 1,000. For a Japanese passport asking $ 700. And now we went to the site where they sell a driver's license. Here are listed several states, the cost of a driver's license for each of these states is $ 200. Let's try to go to the last site.
Greater: “Free Shipping” is written here! !

: , . 700 . , .

25-110 .
: , , . , , , , , , .
: , ? « ».
: -, ! .
: , , ?
, . Defcoin', , (). , Escrow, , Escrow . , , OPSEC.
, , . «tumbler», . — , , , . , , Tumbler , . , , . ( , ), .
, , - . , TOR . - , . , , , Darknet. , .
, . «» JavaScript, Firefox, XSS , , .
, . , , . , Bitcoin. . , , , .
, OPSEC.

: , . -, , . , , Tails. , , . -, Tor. .
Subreddit . , «» . , . , Facebook , Darkmarket , , .
VM (Tails). Tails. Windows 8. , , - . , Tails-. , Tails , DEFCON101 . .
: , .
: , , .
: , . .

Darkmarket . PO Box UPS. , UPS ! - , . - , , .
, . , , , .
: , , « ». , .
, « ». Baby Monitor. GSM, SIM-, . , , , . . , , , , . SMS 1111, – 0000. «», . , , «» .

- USPS.

, .
, , , « ». , – . , , , « ». . , Darknet .
, , Darknet , , , , . , , . , , , , Darknet . , .
Darknet , . , , , , , , . , .
, . , , .
, !

--, c , !
, . ? ? , 30% entry-level , : VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps $20 ? ( RAID1 RAID10, 24 40GB DDR4).
Dell R730xd 2 ? 2 Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 $249 ! . c Dell R730xd 5-2650 v4 9000 ?
Source: https://habr.com/ru/post/352792/
All Articles