Building an extended anti-virus protection system for a small enterprise. Part 1. Choosing a strategy and decision
Probably not worth much to write about the need to pay attention to IT security and what will happen if you do not. Therefore, we will immediately get down to business. As part of one of the projects, it was necessary to organize a comprehensive protection of one of the network IT infrastructures.
The management of this company was very puzzled by the victorious procession of cryptographers on computers and offices of partners. And the task was set quite correctly - to provide the necessary level of protection against such a disgrace. Of course, redundancy is not needed by anyone, but random infections should be absent.
If you dwell on the details, the company is small, the business on the legs is firm, but I do not intend to spend extra money and is ready to bargain for every penny.
At once I will say that simple measures from the “tighten the screws” series: to cut down the rights of users and so on — this has already been done.
')
It was the turn of more serious changes, such as the introduction of additional elements in the protection of IT infrastructure.
The work on building IT systems requires from the architect not only technical skills, but also strategic thinking. Like the ruler of a state, it is necessary to foresee and where enemy troops will move from, and how spies and saboteurs will make their way, trying to steal information or damage.
It is impossible to imagine a situation in which only one police in the person of a local district police officer or sheriff is engaged in the search and liquidation of enemy agents.
If we compare the state protection scheme with the IT infrastructure, then some analogies suggest themselves. For example, an Internet gateway with built-in protection can be considered border troops, ordinary anti-virus monitors can be considered by the police, and encryption of transmitted traffic along with its verification can be done by courier service.
It is worth noting an important point: when the anti-virus monitor reports a detected threat, this means that the malicious code has already entered the system. At what stage he was noticed and how much he managed to do harm at the same time - the question is still that ...
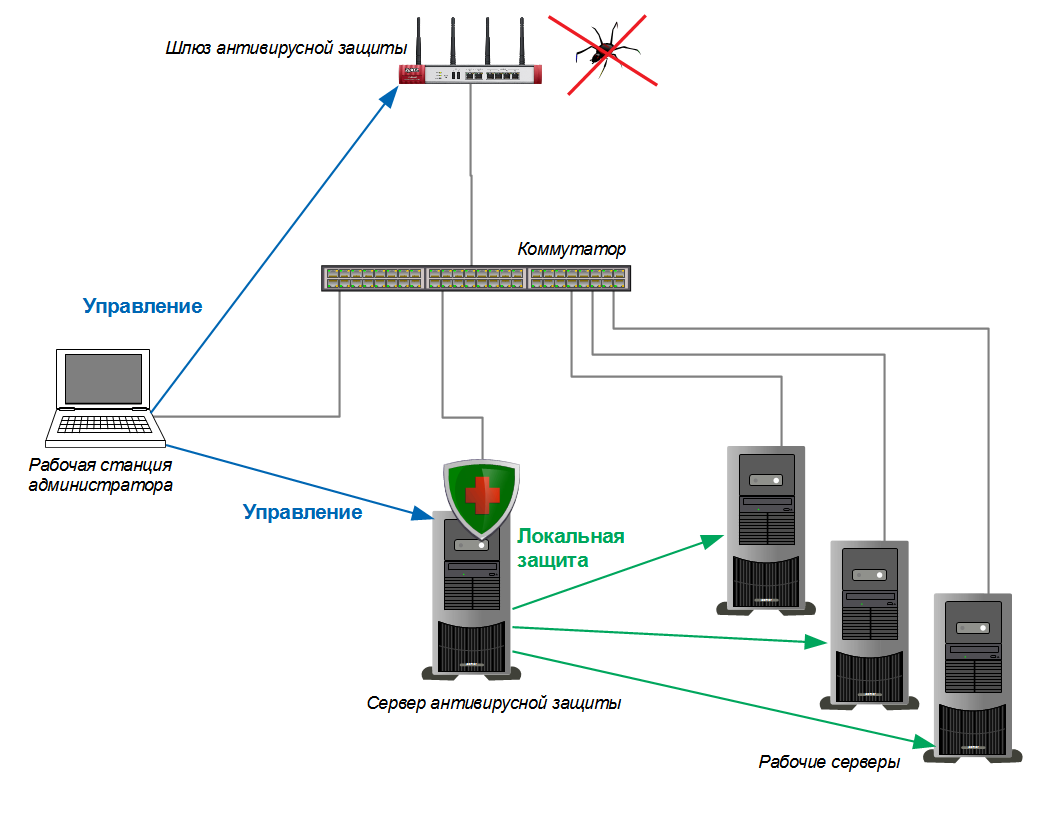
Figure 1. Anti-virus protection scheme with an Internet gateway.
The latest epidemics of encrypting viruses have definitively debunked the myth, that "one antivirus is enough, if only it is reliable ...".
So, we have come to the conclusion that a good defense should have several levels.
If everything is more or less clear with the internal protection system, you need to buy a good antivirus. And in this matter will have to rely on the reputation of its creators.
The perimeter defense is not so simple.
It is imperative that the local protection of computers and the perimeter are based on different products and platforms. Otherwise, the malware will be able to bypass, or, conversely, infect both protection systems. Ideally, these should be devices with different architectures, running under a different operating system that is difficult to access for virus writers.
Define a set of basic requirements for anti-virus gateway:
1) Anti-virus engine with signature updates
Here, as they say, neither add nor take away. Without this function, everything else loses its meaning.
2) Availability of comprehensive technical support
This is an interesting and important point that is often forgotten. While the IT infrastructure is relatively small, internal IT staff can easily cope with its support. However, as an organization grows and develops, accessibility and resiliency requirements increase. At the same time, the number of points of failure is increasing. Existing IT specialists are not enough. Many companies in the terms of reference for an integration project from the very beginning require the presence of support from the vendor as a prerequisite.
3) Convenient control system, preferably with a graphical web-interface
It makes no sense to comment on this feature for a long time. I will only note that a clear interface not only simplifies interaction with the device, but also makes it possible to delegate certain powers without any problems, for example, in case of vacation, illness, and so on.
4) Availability of good documentation
This makes no sense to write for a long time. I will only note that the documentation should be understandable not only to the developer of the system.
The first thing that comes to mind is to buy a small server, install an open operating system on it and install the appropriate software on it and configure everything yourself.
Many manufacturers of anti-virus systems offer their own software solutions that can be installed on an Internet gateway running Linux (or another Unix-like OS) and consider themselves to be protected to some extent.
At the same time, this approach is not without flaws.
No comprehensive support. That is, for support of protection software, you need to contact one manufacturer, with operating system problems - the second, and when resolving hardware issues - the third.
And according to the established sad tradition, each of these trinity can say: “This is not my problem, refer to ....”, thereby leaving the local IT staff to fight alone.
Another disadvantage is the need to update and configure different components separately, without disturbing their interaction. Suppose an antivirus works in conjunction with a proxy server. It is necessary to update the operating system, the proxy server software and the antivirus itself so that in the end it does not break their work.
If, for example, an intrusion protection system is additionally present, another set of maintenance components is added to this. If VPN is one more ... As a result, the local sysadmin needs to be highly qualified enough to support all this difficult business alone.
An equally important issue is the management of the system. If antivirus products usually have a nice built-in out-of-the-box interface, then no one promised the same amenities for the rest of the system, for example, a proxy server. It is necessary to select products for management, delegation of authority, then it’s all set up, updated, and so on.
As a result, we have a rather difficult task of creating, setting up and maintaining such an improvised system of independent "bricks".
If we talk about documentation, then the principle most often works: “I will write when the time is ...”. Comments are superfluous.
All of the above problems suggest an interesting idea: did anyone try to calculate how much a self-made decision on perimeter defense costs in the end?
But it is necessary to consider not according to the “soft + hardware” formula, but in combination with the salary of personnel, taking into account deductions from the payroll, with lost profits and other costs in case of downtime, and so on. And the amount may be very, very considerable.
The second question: what to do if the creator of the system is unavailable? Everyone can get sick or just quit.
And what should small companies do, including those on the periphery, who so far cannot find a highly qualified specialist in the above areas?
The conclusion suggests itself - to search the market for an inexpensive (!) Ready-made device that has all the above described functions. Available to purchase in the territory of the Russian Federation.
In addition to being in stock at the seller, you need to consider whether the manufacturer supports economic sanctions against Russia. The possible prospect of being not only without technical support, but also without updating the anti-virus database is somehow not encouraging.
You can try to look for such a thing from antivirus vendors. However, the search yielded links only to software for installation on a computer. We did not manage to find ready-made hardware and software systems for perimeter protection here.
But the desired options were found among the network equipment. Many manufacturers in one form or another have solutions to protect the perimeter of the network. It should be noted that many network equipment vendors are American companies that are obliged to support anti-Russian sanctions. Probably, few people will be delighted with the perspective of “playing cat and mouse”, trying to save the projected structure of this kind of trouble.
Therefore, the choice fell on a neutral option in the form of products Zyxel. The company is Taiwanese and headquarters in Taiwan and does not support sanctions. Another advantage of the Taiwanese company is that the equipment is manufactured here in Taiwan, which is called “side by side”, and the prices due to logistics and the absence of customs and other fees will be lower. If only because they do not need to bring components from abroad, as is the case with the Russian assembly.
At the same time, Zyxel is a well-known company with a good reputation, so there is no need to fear that it will disappear without a trace, leaving its customers without support.
Summing up all the pros and cons, it remains to make a choice on the devices of the USG / ZyWALL family: USG60W and USG40W
In this case, we get a built-in antivirus, antispam, content filtering and as a bonus - intrusion detection and protection (IDP).

Figure 2. Unified Next-Gen USG USG60W Security Gateway.
Still interested in some of the features of the "gentleman's set" of the Internet gateway:
If we recall the problems of delegation, then for very simple situations there is a simplified configuration option - Easy Mode. This can be useful when creating an infrastructure of the "center-and-branches" type, and in branches, sometimes the problem of finding highly qualified IT specialists emerges.
In this article, we decided on the IT infrastructure protection scheme: perimeter protection in conjunction with local anti-virus agents, and both directions should be based on products from different vendors.
Found that the integrated software and hardware solution has additional advantages primarily due to the internal integration of all components.
Picked up the device, free from anti-Russian sanctions.
In the next part, we will look at building complex protection using the examples of selected USG / ZyWALL families.
Sources :
How it all began
The management of this company was very puzzled by the victorious procession of cryptographers on computers and offices of partners. And the task was set quite correctly - to provide the necessary level of protection against such a disgrace. Of course, redundancy is not needed by anyone, but random infections should be absent.
If you dwell on the details, the company is small, the business on the legs is firm, but I do not intend to spend extra money and is ready to bargain for every penny.
At once I will say that simple measures from the “tighten the screws” series: to cut down the rights of users and so on — this has already been done.
')
It was the turn of more serious changes, such as the introduction of additional elements in the protection of IT infrastructure.
Principles of reliable protection
The work on building IT systems requires from the architect not only technical skills, but also strategic thinking. Like the ruler of a state, it is necessary to foresee and where enemy troops will move from, and how spies and saboteurs will make their way, trying to steal information or damage.
It is impossible to imagine a situation in which only one police in the person of a local district police officer or sheriff is engaged in the search and liquidation of enemy agents.
If we compare the state protection scheme with the IT infrastructure, then some analogies suggest themselves. For example, an Internet gateway with built-in protection can be considered border troops, ordinary anti-virus monitors can be considered by the police, and encryption of transmitted traffic along with its verification can be done by courier service.
It is worth noting an important point: when the anti-virus monitor reports a detected threat, this means that the malicious code has already entered the system. At what stage he was noticed and how much he managed to do harm at the same time - the question is still that ...

Figure 1. Anti-virus protection scheme with an Internet gateway.
The latest epidemics of encrypting viruses have definitively debunked the myth, that "one antivirus is enough, if only it is reliable ...".
Organization of multi-level protection
So, we have come to the conclusion that a good defense should have several levels.
If everything is more or less clear with the internal protection system, you need to buy a good antivirus. And in this matter will have to rely on the reputation of its creators.
The perimeter defense is not so simple.
It is imperative that the local protection of computers and the perimeter are based on different products and platforms. Otherwise, the malware will be able to bypass, or, conversely, infect both protection systems. Ideally, these should be devices with different architectures, running under a different operating system that is difficult to access for virus writers.
Define a set of basic requirements for anti-virus gateway:
1) Anti-virus engine with signature updates
Here, as they say, neither add nor take away. Without this function, everything else loses its meaning.
2) Availability of comprehensive technical support
This is an interesting and important point that is often forgotten. While the IT infrastructure is relatively small, internal IT staff can easily cope with its support. However, as an organization grows and develops, accessibility and resiliency requirements increase. At the same time, the number of points of failure is increasing. Existing IT specialists are not enough. Many companies in the terms of reference for an integration project from the very beginning require the presence of support from the vendor as a prerequisite.
3) Convenient control system, preferably with a graphical web-interface
It makes no sense to comment on this feature for a long time. I will only note that a clear interface not only simplifies interaction with the device, but also makes it possible to delegate certain powers without any problems, for example, in case of vacation, illness, and so on.
4) Availability of good documentation
This makes no sense to write for a long time. I will only note that the documentation should be understandable not only to the developer of the system.
Creating a manual protection system
The first thing that comes to mind is to buy a small server, install an open operating system on it and install the appropriate software on it and configure everything yourself.
Many manufacturers of anti-virus systems offer their own software solutions that can be installed on an Internet gateway running Linux (or another Unix-like OS) and consider themselves to be protected to some extent.
At the same time, this approach is not without flaws.
No comprehensive support. That is, for support of protection software, you need to contact one manufacturer, with operating system problems - the second, and when resolving hardware issues - the third.
And according to the established sad tradition, each of these trinity can say: “This is not my problem, refer to ....”, thereby leaving the local IT staff to fight alone.
Another disadvantage is the need to update and configure different components separately, without disturbing their interaction. Suppose an antivirus works in conjunction with a proxy server. It is necessary to update the operating system, the proxy server software and the antivirus itself so that in the end it does not break their work.
If, for example, an intrusion protection system is additionally present, another set of maintenance components is added to this. If VPN is one more ... As a result, the local sysadmin needs to be highly qualified enough to support all this difficult business alone.
An equally important issue is the management of the system. If antivirus products usually have a nice built-in out-of-the-box interface, then no one promised the same amenities for the rest of the system, for example, a proxy server. It is necessary to select products for management, delegation of authority, then it’s all set up, updated, and so on.
As a result, we have a rather difficult task of creating, setting up and maintaining such an improvised system of independent "bricks".
If we talk about documentation, then the principle most often works: “I will write when the time is ...”. Comments are superfluous.
Use ready-made solutions
All of the above problems suggest an interesting idea: did anyone try to calculate how much a self-made decision on perimeter defense costs in the end?
But it is necessary to consider not according to the “soft + hardware” formula, but in combination with the salary of personnel, taking into account deductions from the payroll, with lost profits and other costs in case of downtime, and so on. And the amount may be very, very considerable.
The second question: what to do if the creator of the system is unavailable? Everyone can get sick or just quit.
And what should small companies do, including those on the periphery, who so far cannot find a highly qualified specialist in the above areas?
The conclusion suggests itself - to search the market for an inexpensive (!) Ready-made device that has all the above described functions. Available to purchase in the territory of the Russian Federation.
In addition to being in stock at the seller, you need to consider whether the manufacturer supports economic sanctions against Russia. The possible prospect of being not only without technical support, but also without updating the anti-virus database is somehow not encouraging.
You can try to look for such a thing from antivirus vendors. However, the search yielded links only to software for installation on a computer. We did not manage to find ready-made hardware and software systems for perimeter protection here.
But the desired options were found among the network equipment. Many manufacturers in one form or another have solutions to protect the perimeter of the network. It should be noted that many network equipment vendors are American companies that are obliged to support anti-Russian sanctions. Probably, few people will be delighted with the perspective of “playing cat and mouse”, trying to save the projected structure of this kind of trouble.
Therefore, the choice fell on a neutral option in the form of products Zyxel. The company is Taiwanese and headquarters in Taiwan and does not support sanctions. Another advantage of the Taiwanese company is that the equipment is manufactured here in Taiwan, which is called “side by side”, and the prices due to logistics and the absence of customs and other fees will be lower. If only because they do not need to bring components from abroad, as is the case with the Russian assembly.
At the same time, Zyxel is a well-known company with a good reputation, so there is no need to fear that it will disappear without a trace, leaving its customers without support.
Summing up all the pros and cons, it remains to make a choice on the devices of the USG / ZyWALL family: USG60W and USG40W
In this case, we get a built-in antivirus, antispam, content filtering and as a bonus - intrusion detection and protection (IDP).

Figure 2. Unified Next-Gen USG USG60W Security Gateway.
Still interested in some of the features of the "gentleman's set" of the Internet gateway:
- firewall;
- Virtual Private Network (VPN);
- bandwidth control;
- event log and monitoring;
- unified security policy.
If we recall the problems of delegation, then for very simple situations there is a simplified configuration option - Easy Mode. This can be useful when creating an infrastructure of the "center-and-branches" type, and in branches, sometimes the problem of finding highly qualified IT specialists emerges.
Conclusion to the 1st part
In this article, we decided on the IT infrastructure protection scheme: perimeter protection in conjunction with local anti-virus agents, and both directions should be based on products from different vendors.
Found that the integrated software and hardware solution has additional advantages primarily due to the internal integration of all components.
Picked up the device, free from anti-Russian sanctions.
In the next part, we will look at building complex protection using the examples of selected USG / ZyWALL families.
Sources :
Source: https://habr.com/ru/post/352734/
All Articles