Basic Business Instinct: The Edge of Corporate Security
Have you ever tried to introduce new regulations and instructions in the company? If yes, then you probably know what a storm of indignation falls from the side of the collective. At a minimum, you begin to quietly hate you, at most - gossip, some unmotivated statements about leaving and general panic appear. Should I roll back the process? Not. If indignation and resistance to such a “restriction of freedom” appeared, most likely you touched someone’s interests. And it seems that you do not bend, but introduce minimum measures of protection, but according to some of the employees, you tighten the screws, impose a regime, press with authority and block the air of freedom. Calm down - you are on the right track. And having blocked that very “air of freedom”, you allow your company not about the *****, but to keep the “polymers”. Because you are working with corporate security, which in the past few years has changed the face. So let's meet her again.
 We really like the Soviet poster genre. There was a lot about safety. Business may well rethink industry advice. Do not step on a rake, bend in the nails - in short, work in advance.
We really like the Soviet poster genre. There was a lot about safety. Business may well rethink industry advice. Do not step on a rake, bend in the nails - in short, work in advance.
This article should not have been - in the plans were completely different, peaceful themes. But the discussion of the previous post in the comments and not only prompted us to the idea that with security in Russian business things are about the same as with CRM-systems : large and experienced, and so they know everything, and the rest is not necessary - "Excel" ( MS Excel) is enough. It was all the more surprising to see some statements on Habré. No, guys. The problem of security is absolutely in front of any company, regardless of its size, industry sector and turnover. Just because your company works in the external environment, it has employees, computers, networks, software, customers and the product or service itself. And if no one tries to hack you or DDoS, it does not mean that the company is completely safe. Too many aspects worth considering.
Let's start with the overview of the corporate security of the company.
')
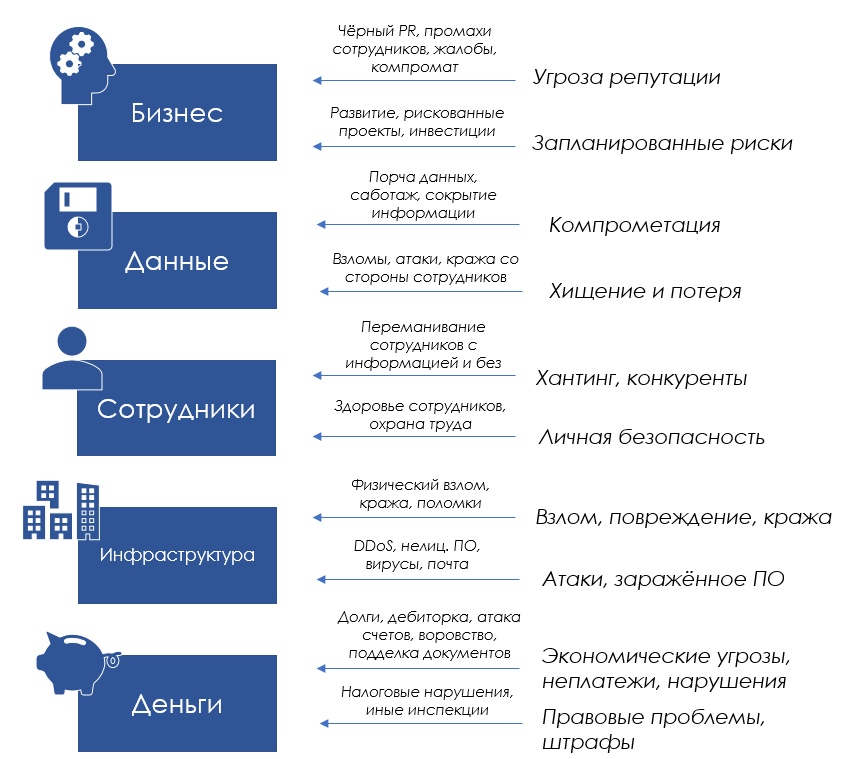
As you can see, there is nothing extraordinary in the list of threats to business entities - every business faces such aspects of work, and they all pose threats. Jerk can where you are not waiting.
Now we see the components of corporate security, about half of which companies don’t remember, or even don’t know at all.
Information security - today it is the type of security that needs to be addressed by everyone. There is a risk at all levels: from the inadvertent launching of malware from an email message to the risks associated with cloud technologies, third-party services and malicious actions of employees.
Economic (financial) security must resist all sources of "leaving" or non-receipt of money. It is also relevant for any company and is directly related to working with documents, paying taxes, accounting, investing in advertising and marketing, etc. By the way, this type of security is most vulnerable to human factors.
Legal security is protection against illegal actions and offenses that run counter to the norms of legislation: forgery of documents, the use of fraudulent schemes in work, kickbacks, and so on. It differs from the economic one in that violations of this type of security are most often directed not at someone's financial gain, but to protect the interests from already accomplished facts (we carried an extra load - bought a route sheet, overspending money - faked an act, lost a couple of servers - fabricated an act write-offs, etc.).
Physical and personal safety of employees - protection of employees from the penetration of ill-wishers into the company’s territory and from an attempt on their life and health. The wording sounds exaggerated and its fullness of perception depends on the status of the company. But usually the minimum requirements for physical security are met (security, access system, cameras, other types of authentication).
Physical security of the infrastructure - protection of equipment, networks and programs from access by unauthorized persons and persons whose work activity does not include contact with these elements of the infrastructure. There must be an external and internal safety loop. Security breaches in this area by employees are not always malicious — sometimes it can be tea spilled on expensive equipment or toner scattered around sensitive devices.
Security risk management is one of the most unobvious types that likes to joke with those who neglect it. The risks of violating this type of security are related to the fact that top management does not evaluate projects, investments and other perspectives in which they invest any resources. This could include risky venture capital investments, the purchase of used equipment, work with unreliable suppliers at a discount, etc.
 Personnel (HR) security - protects the company from brain drain. Good specialists are needed by everyone, so if your company is even lit up a bit on the market, your employees have already become desirable candidates among competitors (ideally, if we wrote about your work or client base, we wrote about this ). In addition, he is responsible for the system of measures related to training employees in a safe dialogue with competitors and other external agents - for example, during interviews, conferences, meetings, seminars, etc.
Personnel (HR) security - protects the company from brain drain. Good specialists are needed by everyone, so if your company is even lit up a bit on the market, your employees have already become desirable candidates among competitors (ideally, if we wrote about your work or client base, we wrote about this ). In addition, he is responsible for the system of measures related to training employees in a safe dialogue with competitors and other external agents - for example, during interviews, conferences, meetings, seminars, etc.
Reputational security - protection of business reputation and image of the company in the market. In modern conditions of high-speed dissemination of information, losing several levels of one’s reputation is a matter of one tweet / article / speech / complaint ... Unsuccessful advertising, illiterate content policy, hacking and data leaks, attempts to interfere with the interests of not your audience - all this can strike the company and inevitably lead to financial losses.
And now let's see what the main transformation took place in. Who is responsible for risk management security? Top management. Who is responsible for personnel? HR-service, internal PR manager, if you are a developer, then also DevRel. Who is responsible for the reputation? PR, marketing, advertising manager. The security service is no longer able to keep track of everything (especially if it is not in the company). Each is responsible for the safety of their actions in their place, often unaware of it. And this is wrong. So, there is a minimum task:
 Universal, in general, advice. But hard to do
Universal, in general, advice. But hard to do
Business in terms of security often hopes "at random." In the previous post, we conducted a survey and obtained the following results: 64% of the respondents have security problems, while the most popular methods of ensuring information security are complex password policies, rejecting cloud systems, prohibiting public disks and storage, and allocating a pool of IP addresses . A little more than a third do nothing. Of course, the sample is not so hot, but certain signals can be caught. Each company has its own reasons for inattention to safety, but there are five basic factors that occur in companies of all sizes and any industry sector.
Taking care of security, business cares not only about profits, but also about the employees themselves. Therefore, it is worthwhile to seek compromises and implement the necessary measures with a firm hand. Although we are convinced that the total recording of the employee’s working day, the camera behind everyone’s back and tight control of time and movement are definitely a rough exaggeration, which is justified literally in company units. Trust is still in value. Vigilant trust :-)
To think that security is only total control and strict accountability, can only a person not in the subject. The corporate security complex faces serious challenges directly related to the company's success.
In general, it is very difficult to understand what is cooperation and what is competitive intelligence. In addition, sometimes such actions hit the very competitor. History from the 2010s. Two telecom operators, they are sold in the region by the same dealers. Before launching a new tariff, exclusive dealers receive information for a week in order to train employees, enter data into CRM and prices, prepare a layout. And now the dealer transfers information to the second operator for a special bonus (of course, officially issued). The second operator does not sleep for three nights and rolls out the tariff for exactly the same conditions on his site, doing an SMS-mailing, and then he is preparing a promo. It's a shame, sort of. But no - an important part of the description of the tariff will get to dealers only on the day of the start of sales when shipping leaflets with asterisks and small print. And the second operator essentially banged an unreasoned and unprofitable tariff. So, before hitting your competitors, you should learn how to manage information.


Accountability data. All information in the company must necessarily be classified and ranked so that employees have a clear understanding of what access they have and how much information can be transmitted beyond its competencies. For example, information about a company can be completely confidential, circulate within a firm, be common to all branches and partners and freely distributed.
Installed policies. Security policies should primarily concern the network infrastructure and workstations of employees to prevent intrusion from or leakage of information. In addition, there should be regulatory policies for the dissemination of commercial and other relevant information (for example, a PR manager in a press release may report that the company's turnover has increased by 27% over the past two years, but not in money terms, unless your company is public, and information about financial performance is open).
Post-incident response, conclusions from the situation. Each case of security breach must be analyzed and handled - based on the results, it is worthwhile to form a set of proactive measures and make corrections to the knowledge base on security management. If there are no lessons learned from the incident, most likely, he will return to you.
Security management should not be patchwork - a good security strategy provides an overview of the current situation and allows you to manage security in the complex. Holistic approach helps to track the relationship between business processes and cover all aspects of the company, not allowing you to discard factors that are not important at first glance. By the way, modern CRM systems are a good help for maximizing the review of business processes, because they have not focused on sales alone for a long time, but automate a maximum of aspects of a company's operations (especially universal ones, such as RegionSoft CRM ).
Want a real story about the complexity of security? One man created a business associated with a rather necessary B2B service. Hired staff, even a security guard, slowly swayed. He lacked a marketer. He took the marketer, but they didn’t agree on something - the new employee wanted mountains to the skies, preferably gold. The marketer decided to slam the door, the accountant read it out and did not transfer the calculation on time. An evil former employee decided that the world was unjust and wrote to the fire inspectorate that there was no fire extinguisher, to the labor inspectorate, that they did not immediately make an entry in the booklet, to the tax office with the message “about possible violations”, to the social network about how he was offended (lied) . A poor young businessman hit all the organs they could. The company has closed. And all that is: in time to do his job as a personnel officer and an accountant, buy a fire extinguisher for a security man, check the network for the admin, because This marketer did nothing at work and it could be “poured out” at least for his posts in social. networks, not to mention more serious measures. So much for the complexity of small business.
Security Continuity. It is necessary to work on reducing risks in the company constantly, and not from time to time, and even more so from incident to incident. Each employee, in carrying out his duties, must remember that he is responsible for his business processes, for their safe operation and for the security of all the interests of the company as a whole.

Security should be economical. You can hire a company to outsource, create a security service, invest in expensive monitoring systems, poke cameras, but it will be three times more expensive than all of your company's assets, including the customer base. Building a security system, proceed from considerations of expediency, that is, the economic sense of measures should not be lost. It is also useful to remember that timely prevention and anticipation cost the least, and response and elimination of the consequences of the incident are most expensive.
Security must be coordinated. At the stages of pre-emption, detection, response and analysis, all units must work smoothly, quickly and professionally. At the stage of detection and response, you should not make a showdown on the topic "Who is to blame?", For this you will have time right after the end of the security actions. In order for coordination to be optimal, job descriptions and regulations for action in a critical situation must be carefully prescribed.
 Security should be clear, transparent, but open to a limited circle of people. All employees must understand what actions may lead to security breaches, what to do if problems occur, and what consequences this or that event has. All the postulates set forth in the instructions and communicated to the employees must be interpreted unequivocally. But a complete vision of the situation, as well as an arsenal of means for protecting and minimizing damage, should be in the hands of several responsible persons. The more employees have information about the system to counter various violations, the higher the likelihood of incidents.
Security should be clear, transparent, but open to a limited circle of people. All employees must understand what actions may lead to security breaches, what to do if problems occur, and what consequences this or that event has. All the postulates set forth in the instructions and communicated to the employees must be interpreted unequivocally. But a complete vision of the situation, as well as an arsenal of means for protecting and minimizing damage, should be in the hands of several responsible persons. The more employees have information about the system to counter various violations, the higher the likelihood of incidents.
Professionals must manage safety. Of course, most small and medium businesses can not afford the contents of the security service. The first and obvious option is to outsource security, even here, in Habré, there are quite a few such companies for different areas, not just IT. The second option is to prioritize security threats and form a “response team” based on their employees at the most critical points. This is quite an effective measure, since knowledge and understanding of the business process is no less important than the arsenal of tools that you choose and learn in the process of preemption. In addition, the correlation between the company's goals and the likelihood of threats, that is, the formation of security priorities, provides a good saving of expenses on protection measures. The main thing is not to leave corporate security unattended and responsible.
And remember - the security of a business must first of all be taken care of by its owners and employees. You should not be offended by hosters, providers, vendors, service providers, if you have obvious problems, ranging from physical security to informational. In the open door, someone must enter.

While we were writing an article and looking through security management practices, in order not to miss anything, we were broughtto the beginning of the dashing 90s to one site, where in the detailed article about the security of the company there is such a paragraph about - attention! - “non-governmental organizations”. Also a kind of experience. Hopefully not in the IT field :-)
One of the main success factors in dealing with problems in security is to see markers in time that indicate that something went wrong somewhere. Here is a basic action plan for managing corporate security:

The picture is clickable
So, the general recommendations for dealing with threats to corporate security.
The schemes and methods given by us are the basis that almost any company is able to implement. We have been developing and implementing our CRM-system for many (many, many) years, we work in the enterprise and know firsthand how security threats can stifle a business, deprive it of valuable information, scare or lead away its customers. The consequences are always the same - losses, problems with employees, the huge costs of recovery. Fulfilling even the smallest safety standards significantly reduces risks. In the end, you spend THAT car, put the password on the smartphone, close the apartment, buy alarm systems for movable and immovable property. Why is the company worse?
Our site with absolutely desktop business software and our flagship RegionSoft CRM.
 Our Telegram channel is BizBreeze . Anything about CRM and business, according to the mind, without copy-paste and 90% without advertising. Join reckless ranks.
Our Telegram channel is BizBreeze . Anything about CRM and business, according to the mind, without copy-paste and 90% without advertising. Join reckless ranks.

And what, someone threatens us or something?
This article should not have been - in the plans were completely different, peaceful themes. But the discussion of the previous post in the comments and not only prompted us to the idea that with security in Russian business things are about the same as with CRM-systems : large and experienced, and so they know everything, and the rest is not necessary - "Excel" ( MS Excel) is enough. It was all the more surprising to see some statements on Habré. No, guys. The problem of security is absolutely in front of any company, regardless of its size, industry sector and turnover. Just because your company works in the external environment, it has employees, computers, networks, software, customers and the product or service itself. And if no one tries to hack you or DDoS, it does not mean that the company is completely safe. Too many aspects worth considering.
Let's start with the overview of the corporate security of the company.
')

As you can see, there is nothing extraordinary in the list of threats to business entities - every business faces such aspects of work, and they all pose threats. Jerk can where you are not waiting.
Now we see the components of corporate security, about half of which companies don’t remember, or even don’t know at all.
Information security - today it is the type of security that needs to be addressed by everyone. There is a risk at all levels: from the inadvertent launching of malware from an email message to the risks associated with cloud technologies, third-party services and malicious actions of employees.
Economic (financial) security must resist all sources of "leaving" or non-receipt of money. It is also relevant for any company and is directly related to working with documents, paying taxes, accounting, investing in advertising and marketing, etc. By the way, this type of security is most vulnerable to human factors.
Legal security is protection against illegal actions and offenses that run counter to the norms of legislation: forgery of documents, the use of fraudulent schemes in work, kickbacks, and so on. It differs from the economic one in that violations of this type of security are most often directed not at someone's financial gain, but to protect the interests from already accomplished facts (we carried an extra load - bought a route sheet, overspending money - faked an act, lost a couple of servers - fabricated an act write-offs, etc.).

Physical and personal safety of employees - protection of employees from the penetration of ill-wishers into the company’s territory and from an attempt on their life and health. The wording sounds exaggerated and its fullness of perception depends on the status of the company. But usually the minimum requirements for physical security are met (security, access system, cameras, other types of authentication).
Physical security of the infrastructure - protection of equipment, networks and programs from access by unauthorized persons and persons whose work activity does not include contact with these elements of the infrastructure. There must be an external and internal safety loop. Security breaches in this area by employees are not always malicious — sometimes it can be tea spilled on expensive equipment or toner scattered around sensitive devices.
Security risk management is one of the most unobvious types that likes to joke with those who neglect it. The risks of violating this type of security are related to the fact that top management does not evaluate projects, investments and other perspectives in which they invest any resources. This could include risky venture capital investments, the purchase of used equipment, work with unreliable suppliers at a discount, etc.
 Personnel (HR) security - protects the company from brain drain. Good specialists are needed by everyone, so if your company is even lit up a bit on the market, your employees have already become desirable candidates among competitors (ideally, if we wrote about your work or client base, we wrote about this ). In addition, he is responsible for the system of measures related to training employees in a safe dialogue with competitors and other external agents - for example, during interviews, conferences, meetings, seminars, etc.
Personnel (HR) security - protects the company from brain drain. Good specialists are needed by everyone, so if your company is even lit up a bit on the market, your employees have already become desirable candidates among competitors (ideally, if we wrote about your work or client base, we wrote about this ). In addition, he is responsible for the system of measures related to training employees in a safe dialogue with competitors and other external agents - for example, during interviews, conferences, meetings, seminars, etc.Reputational security - protection of business reputation and image of the company in the market. In modern conditions of high-speed dissemination of information, losing several levels of one’s reputation is a matter of one tweet / article / speech / complaint ... Unsuccessful advertising, illiterate content policy, hacking and data leaks, attempts to interfere with the interests of not your audience - all this can strike the company and inevitably lead to financial losses.
A new paradigm of responsibility and stick in the wheels
Security service fails
And now let's see what the main transformation took place in. Who is responsible for risk management security? Top management. Who is responsible for personnel? HR-service, internal PR manager, if you are a developer, then also DevRel. Who is responsible for the reputation? PR, marketing, advertising manager. The security service is no longer able to keep track of everything (especially if it is not in the company). Each is responsible for the safety of their actions in their place, often unaware of it. And this is wrong. So, there is a minimum task:
- train detection - employees should be able to develop a set of markers of the threat to their area of responsibility, select detection tools (for example, a monitoring system for the administrator, alerts for webmasters and alerts for PR, etc.) and most importantly, learn how to distinguish threats from other forms of deviations in the standard system behavior;
- teach how to analyze threats — be able to quickly either find or hypothetically assume the source of the threat, evaluate the possible scale, understand where potential security gaps are located;
- to train in confrontation - to develop adequate and prompt measures to anticipate, respond and prevent possible problems;
- introduce certain regulations and instructions - no matter how negatively the employees treat them, this is a necessary and important element of security, if only because it is in a critical situation to turn to the document faster than to get together and start to think up ways to react;
- Do not overreact and turn the company into a special service . Employees should be aware of the measure of responsibility for their actions and inaction, do everything to ensure safety in their workplace. But at the same time, the work should not be formalized to the point that it becomes impossible to communicate with colleagues and clients, address management, discuss and propose solutions. The internal atmosphere outside the incidents should remain as comfortable and trustful as possible.

What is the main obstacle to building a security system?
Business in terms of security often hopes "at random." In the previous post, we conducted a survey and obtained the following results: 64% of the respondents have security problems, while the most popular methods of ensuring information security are complex password policies, rejecting cloud systems, prohibiting public disks and storage, and allocating a pool of IP addresses . A little more than a third do nothing. Of course, the sample is not so hot, but certain signals can be caught. Each company has its own reasons for inattention to safety, but there are five basic factors that occur in companies of all sizes and any industry sector.
- Lack of business instinct self-preservation. Companies always hope that trouble happens with Google, Salesforce, anyone - just not with them. In fact, security threats will surely arise sooner or later: even if competitors do not encroach on you, there will be dishonest employees or other counterparties who take advantage of the security breach.
- Low security competency . Companies do not have a vision of what a security system should be, how to manage its components, and work to prevent incidents. Unfortunately, training programs also leave much to be desired, as well as textbooks and the so-called best practices. Therefore, everyone is forced to learn from their mistakes.
- Lack of professional staff . It is very difficult and expensive to find a security specialist with a high level of competence. These are usually already engaged in highly critical industries and it is unlikely that small and medium businesses will be able to entice a professional. Competences of most security guards on the market come down either to industry-specific experience (telecom, banks), or to experience in the internal affairs agencies, which are terribly far from the business and the processes inside it.
- Cost savings . Leaving this item without comment, as saving on security is to take a huge step towards the situation “frade’s greed has ruined”.
- Fear of losing employees . Very interesting and multifaceted reason. Often, employees resist any innovations aimed at restrictions. This is primarily due to the usual psychological resistance, but it happens that indicates that additional security can prevent employees. The employer, for fear of losing staff, retreats and does not introduce security measures, but tries to negotiate and persuade. As a result, such slack can only aggravate the situation and lead to dismissals and offenses.
Taking care of security, business cares not only about profits, but also about the employees themselves. Therefore, it is worthwhile to seek compromises and implement the necessary measures with a firm hand. Although we are convinced that the total recording of the employee’s working day, the camera behind everyone’s back and tight control of time and movement are definitely a rough exaggeration, which is justified literally in company units. Trust is still in value. Vigilant trust :-)
What are the challenges facing the company's security system?
To think that security is only total control and strict accountability, can only a person not in the subject. The corporate security complex faces serious challenges directly related to the company's success.
- Protection of information in the company. In principle, information constitutes a large part of the activity of any business entity: data about the product, customers, suppliers, partners, advertising, strategy, marketing, etc. And it is information that is the most desired and, alas, still the most easily accessible asset of the company. You can remove traffic through a breach in the protection of Wi-Fi, you can send a malware, you can pick up passwords, you can buy an employee who will merge everything you need. And from all these actions inevitably comes harm to the business. Therefore, information protection is the hottest front of corporate security, which is worth financing, automating and insuring against the human factor. The set of tools in this situation is different for all companies, but it is better to use the maximum number of tools.
- Prevention of threats from competitors. Find a company that does not have at least one competitor is extremely difficult. So, at some point, your rival in the market will want to get your technology, information, personnel, code, etc. Because if your business is still in trend, it means that in some ways you are better and somehow attract your segment of consumers. The task of corporate security is to build a powerful contour of protection from the external environment and carefully monitor all implementation attempts. This is almost a spy war, and sometimes real industrial and commercial espionage.
In general, it is very difficult to understand what is cooperation and what is competitive intelligence. In addition, sometimes such actions hit the very competitor. History from the 2010s. Two telecom operators, they are sold in the region by the same dealers. Before launching a new tariff, exclusive dealers receive information for a week in order to train employees, enter data into CRM and prices, prepare a layout. And now the dealer transfers information to the second operator for a special bonus (of course, officially issued). The second operator does not sleep for three nights and rolls out the tariff for exactly the same conditions on his site, doing an SMS-mailing, and then he is preparing a promo. It's a shame, sort of. But no - an important part of the description of the tariff will get to dealers only on the day of the start of sales when shipping leaflets with asterisks and small print. And the second operator essentially banged an unreasoned and unprofitable tariff. So, before hitting your competitors, you should learn how to manage information.

- Ensuring sustainable operations of the company and stability of business processes . A very important feature. Corporate security should be designed to ensure that incidents do not affect the speed of work and the performance of duties by employees. Each stage of the business process is fraught with vulnerabilities and risks, so it is worthwhile to cover and take them into account already at the stage of building the process as “bottlenecks”. Then each employee responsible for a particular stage will know what to pay special attention to.
- Preservation and development of staff. Personnel service (HR) should not only take one-time measures, but develop personnel security system throughout the entire life cycle of an employee: search - recruitment - hiring - adaptation - training - work - dismissal (and in some companies there is part of the “former employee” cycle, and this is not a loyalty tool, but a security measure). Initially, it is necessary to check personnel for reliability and history of work, to adapt and train with internal mentors, to develop and maintain loyalty. Dismissal must also take place exclusively within the framework of the requirements of the Labor Code of the Russian Federation, in compliance with all rules and regulations.
- Protection from illegal actions of customers and partners. Business cannot exist in a vacuum, so it is important to conduct thorough work in the external environment: document all significant relationships, control external access to corporate systems (for example, access to a personal account in CRM), monitor the extent to which counterparties gain access to information. Special attention should be paid to business coaches and consultants - they easily get access to the sales system, training and customer base, and therefore they can potentially share information with competitors, use the customer base for commercial purposes, etc. Some coaches and coaches have a bad habit of posting photos from companies on social networks and describing the features of the business with which they were led to work. Do you need it?
- Saving company finances. The security system usually requires investment and does not bring obvious profit. Its main task is to save the company's money and create all the conditions for business to continue earning.

Principles of security in the company
Accountability data. All information in the company must necessarily be classified and ranked so that employees have a clear understanding of what access they have and how much information can be transmitted beyond its competencies. For example, information about a company can be completely confidential, circulate within a firm, be common to all branches and partners and freely distributed.
Installed policies. Security policies should primarily concern the network infrastructure and workstations of employees to prevent intrusion from or leakage of information. In addition, there should be regulatory policies for the dissemination of commercial and other relevant information (for example, a PR manager in a press release may report that the company's turnover has increased by 27% over the past two years, but not in money terms, unless your company is public, and information about financial performance is open).
Post-incident response, conclusions from the situation. Each case of security breach must be analyzed and handled - based on the results, it is worthwhile to form a set of proactive measures and make corrections to the knowledge base on security management. If there are no lessons learned from the incident, most likely, he will return to you.
Security management should not be patchwork - a good security strategy provides an overview of the current situation and allows you to manage security in the complex. Holistic approach helps to track the relationship between business processes and cover all aspects of the company, not allowing you to discard factors that are not important at first glance. By the way, modern CRM systems are a good help for maximizing the review of business processes, because they have not focused on sales alone for a long time, but automate a maximum of aspects of a company's operations (especially universal ones, such as RegionSoft CRM ).
Want a real story about the complexity of security? One man created a business associated with a rather necessary B2B service. Hired staff, even a security guard, slowly swayed. He lacked a marketer. He took the marketer, but they didn’t agree on something - the new employee wanted mountains to the skies, preferably gold. The marketer decided to slam the door, the accountant read it out and did not transfer the calculation on time. An evil former employee decided that the world was unjust and wrote to the fire inspectorate that there was no fire extinguisher, to the labor inspectorate, that they did not immediately make an entry in the booklet, to the tax office with the message “about possible violations”, to the social network about how he was offended (lied) . A poor young businessman hit all the organs they could. The company has closed. And all that is: in time to do his job as a personnel officer and an accountant, buy a fire extinguisher for a security man, check the network for the admin, because This marketer did nothing at work and it could be “poured out” at least for his posts in social. networks, not to mention more serious measures. So much for the complexity of small business.
Security Continuity. It is necessary to work on reducing risks in the company constantly, and not from time to time, and even more so from incident to incident. Each employee, in carrying out his duties, must remember that he is responsible for his business processes, for their safe operation and for the security of all the interests of the company as a whole.

Security should be economical. You can hire a company to outsource, create a security service, invest in expensive monitoring systems, poke cameras, but it will be three times more expensive than all of your company's assets, including the customer base. Building a security system, proceed from considerations of expediency, that is, the economic sense of measures should not be lost. It is also useful to remember that timely prevention and anticipation cost the least, and response and elimination of the consequences of the incident are most expensive.
Security must be coordinated. At the stages of pre-emption, detection, response and analysis, all units must work smoothly, quickly and professionally. At the stage of detection and response, you should not make a showdown on the topic "Who is to blame?", For this you will have time right after the end of the security actions. In order for coordination to be optimal, job descriptions and regulations for action in a critical situation must be carefully prescribed.
 Security should be clear, transparent, but open to a limited circle of people. All employees must understand what actions may lead to security breaches, what to do if problems occur, and what consequences this or that event has. All the postulates set forth in the instructions and communicated to the employees must be interpreted unequivocally. But a complete vision of the situation, as well as an arsenal of means for protecting and minimizing damage, should be in the hands of several responsible persons. The more employees have information about the system to counter various violations, the higher the likelihood of incidents.
Security should be clear, transparent, but open to a limited circle of people. All employees must understand what actions may lead to security breaches, what to do if problems occur, and what consequences this or that event has. All the postulates set forth in the instructions and communicated to the employees must be interpreted unequivocally. But a complete vision of the situation, as well as an arsenal of means for protecting and minimizing damage, should be in the hands of several responsible persons. The more employees have information about the system to counter various violations, the higher the likelihood of incidents.Professionals must manage safety. Of course, most small and medium businesses can not afford the contents of the security service. The first and obvious option is to outsource security, even here, in Habré, there are quite a few such companies for different areas, not just IT. The second option is to prioritize security threats and form a “response team” based on their employees at the most critical points. This is quite an effective measure, since knowledge and understanding of the business process is no less important than the arsenal of tools that you choose and learn in the process of preemption. In addition, the correlation between the company's goals and the likelihood of threats, that is, the formation of security priorities, provides a good saving of expenses on protection measures. The main thing is not to leave corporate security unattended and responsible.
And remember - the security of a business must first of all be taken care of by its owners and employees. You should not be offended by hosters, providers, vendors, service providers, if you have obvious problems, ranging from physical security to informational. In the open door, someone must enter.

While we were writing an article and looking through security management practices, in order not to miss anything, we were brought
Threat Detection Cheat Sheet
One of the main success factors in dealing with problems in security is to see markers in time that indicate that something went wrong somewhere. Here is a basic action plan for managing corporate security:

The picture is clickable
So, the general recommendations for dealing with threats to corporate security.
- Approach threats from all sides - assess the affected business processes, possible damage, repeatability, danger level, methods of elimination.
- Develop a minimum set of documentation. In addition to job descriptions and general safety regulations, it should include: a provision on a company's commercial secret, an agreement on NDA, a provision on a company’s regime (pass, access, working hours, exceptions), a provision and rules for conducting an internal investigation. The presence of documents signed by each employee will cut off some of the internal threats.
- Have a set of tools to detect, eliminate and prevent threats to corporate security.
- Careful attitude to the selection of personnel, the stage of training and adaptation of beginners.
- Conduct a conversation with employees (describe on the portal, in the knowledge base, etc.) on the subject of disclosure of information, including in public places, relatives, friends.
- To accumulate experience in eliminating incidents and store it as information for official use.
- Use specialized software (CRM-system for the client base, monitoring system for managing the IT infrastructure, antivirus software, protected services, including telephony and email clients).
- Carefully monitor the sources by which inside information can be transmitted outside.
- Develop employee loyalty, control HR-resources.
- Broadcast your understanding of security to counterparties, partners, remote branches and employees.
- Make backups (your favorite!).
- Do not choke :-)
The schemes and methods given by us are the basis that almost any company is able to implement. We have been developing and implementing our CRM-system for many (many, many) years, we work in the enterprise and know firsthand how security threats can stifle a business, deprive it of valuable information, scare or lead away its customers. The consequences are always the same - losses, problems with employees, the huge costs of recovery. Fulfilling even the smallest safety standards significantly reduces risks. In the end, you spend THAT car, put the password on the smartphone, close the apartment, buy alarm systems for movable and immovable property. Why is the company worse?
Our site with absolutely desktop business software and our flagship RegionSoft CRM.
Source: https://habr.com/ru/post/352708/
All Articles