Manual cipher LS47
This cipher is a small improvement to the ElsieFour cipher, which was developed by Alan Kaminsky [1]. This version uses 7x7 characters instead of the original 6x6, which is barely enough even for the Latin alphabet. Additionally, a simple algorithm for obtaining a key by password is described, as a more familiar option. Resilience and safety are the same as ElsieFour.
In the repository there is a 3D – model of chips in the formats SCAD and STL.

If you print a model with a change in the color of the layers, the characters will be seen more clearly. Thanks to Martin Ptasek for the image.
If you trust your computer, you can use a simple python implementation of ls47.py Also, Bernard Esslinger (Bernhard Esslinger) from the CrypTool project provided a more convenient version of lc4.py , which implements several add-on options and the original ElsieFour cipher.
Alphabet and character arrangement
Compared with the original version, punctuation, quotation marks, symbols for writing arithmetic expressions are added. For the Cyrillic variant, I had to restrict myself to punctuation only. The symbols on the chips are arranged like this (shown alongside variants with Latin and Cyrillic):
_ abcdef _ ghijklm nopqrst uvwxyz . 0 1 2 3 4 5 6 1 7 8 9 , - + * 2 3 4 5 6 7 8 / : ? ! ' ( ) 9 0 . , ; ? ! As you can see, it is useful to have additional information on the chips to facilitate operations:

To perform encryption / decryption operations, a label is necessary, for example, a pebble, a nut or something similar that stably fits on the chip.
Operations
More processes are described in [1]. Here we give a brief summary of the processes.
Encryption
- The initial arrangement of the chips is a symmetric key. Place the chips in a 7x7 square according to the key.
- Place a mark on the position (0,0).
- Find among the chips the character you are going to encrypt, let's call its position
P - Look at the label, the numbers on its chip are the
Mcoordinates. - Determine the position of the encrypted character as
C := P + M mod (7,7). Write down the encrypted character located at positionC - Cycle to the right to move the line of chips on which is the original character that we encrypted. If the label is on this line, then it moves along with the chips.
- Cyclically slide down the column of chips that now contains the encrypted character. If the label is on this column, then it moves along with the chips.
- Update the label position:
M := M + C' mod (7,7), whereC'are the numbers on the chip with the encrypted character. - For all other characters of the remaining text, repeat the operations from step 3.
Encryption example
Steps 1.2. The initial position, it is the key. The label is on the chip with the symbol 'd'. The symbol that will be encrypted at this stage is marked with a green oval, the symbol – the result of the encryption is marked with a red oval.

Steps 3.4. Encrypt the character '.'. The chip tag looks like this:

Step 5. We count from the symbol '.' five steps to the right, zero steps down and get the desired character '1'. It will be the result of encryption at the current stage.
Step 6. Cyclically shift to the right a row of tokens containing the encrypted character '.'.


Step 7. Shift down the column of chips containing the encrypted character '1'

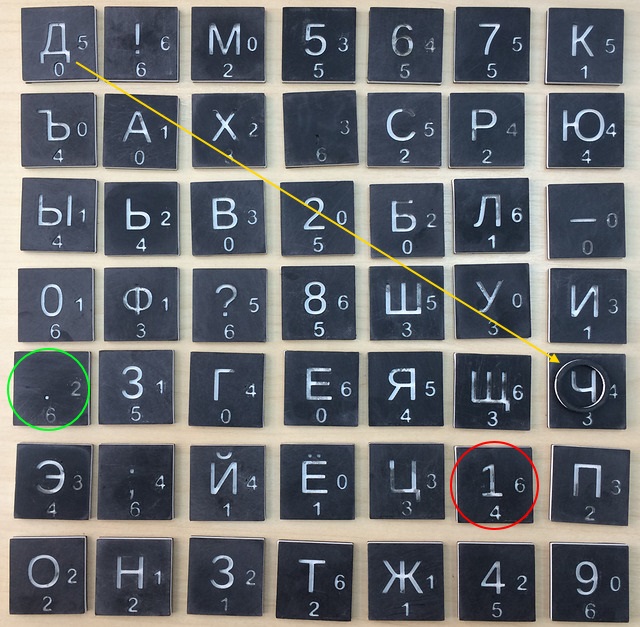
Step 8. Update the position of the label.
Let's look at the chip with the encrypted symbol:

Counting from the symbol 'D' six steps to the right, four steps down and we get a new position of the label.
Decryption
Decryption is performed in almost the same steps, except that in step 5 it is necessary to determine the position P by the known positions M and C P determined by subtracting P := C - M mod (7,7) . The remaining steps are identical.
Key generation
Mix the chips in the bag well and take them one by one. The key is to swap the 49 elements.
Key generation by password
Remembering the random permutation of the 49 elements is not very convenient, especially when there are service symbols among these elements. Instead, you can generate keys from an arbitrary string of sufficient length.
By "sufficient length" is meant "with a sufficient level of entropy." Full keys store about 208 bits of entropy. To achieve similar indicators, your password must be (for the Latin version):
- at least 61 digits if it consists only of randomly selected digits
- at least 44 letters if it consists of randomly selected letters only
- at least 40 alphanumeric characters if it consists of only them
To get the “standard” 128 bits of entropy, the numbers are reduced to about 39, 28, and 25, respectively.
The resulting arrangement can be saved, so as not to engage in key generation every time an encryption / decryption operation is performed.
The key generation algorithm is as follows:
- Arrange the chips in the initial order (that is, as in the original picture).
I := 0. - Take the first character of the password and tick the numbers on the appropriate chip:
Px, Py - Move line
ItoPxposition to the right - Move column I to position
Pydown I := I + 1 mod 7, repeat from point 2 and the next character of the password- The resulting placement of chips is the key
Indistinguishable Ciphertexts
To get different ciphertexts even for the same source text, you need to add a random one-time code of a predetermined length to it. For example, N randomly selected chips from a bag, the recommended N value is at least 10.
It is also worth complementing the original message with a random number of characters to prevent identification between 'yes, please' and 'no', which is easy to do without even knowing the key and seeing 2390238_ and 9 .
Authenticated Encryption
Since the ciphertext can be changed during transmission or a mistake can be made during processing by a person, it is recommended to add a signature at the end of the message. It is enough even just to __ . If the signature does not meet expectations, which can easily happen in case of an error during processing, then either try again (suddenly an error when decrypting?), Or ask the sender to send the message.
This is possible because the output of the cipher depends on the message: if the value is wrong somewhere in the middle, the message loses its meaning after several characters due to the avalanche effect.
Links
[1] Kaminsky, Alan. "ElsieFour: A Low-Tech Authenticated Encryption Algorithm For Human-to-Human Communication." IACR Cryptology ePrint Archive 2017 (2017): 339.
')
Source: https://habr.com/ru/post/352448/
All Articles