Payloads for testing web applications

Using payloads (payloads) allows you to fuzz a web application to detect anomalies / signs of vulnerabilities. In this article I will look at several options for payloads to test web applications.
Payloads
Payloads are a list of sequences of characters, service commands, file names, so-called. polyglots , etc. and serve for semi-automated web application research. In simple terms, the researcher detects entry points (including forms, arguments, dynamically fields) and gives payloads as values.
Most modern security tools contain predefined lists of payloads, usually represented as text files.
')
For example, to identify critical files with tools like wfuzz or dirb, you can use a good list from Bo0oM .
Sample payloads:
.ftpquota .gem .gfclient/ .gfclient/pass .git .git-credentials .git-rewrite/ .git/ .git/config .git/HEAD .git/index .git/logs/ After the web application has been examined, a site map has been compiled, web forms, inputs, parameters, and arguments have been identified — you can begin testing. To do this, select the payload position (using the example of Burp Suite):
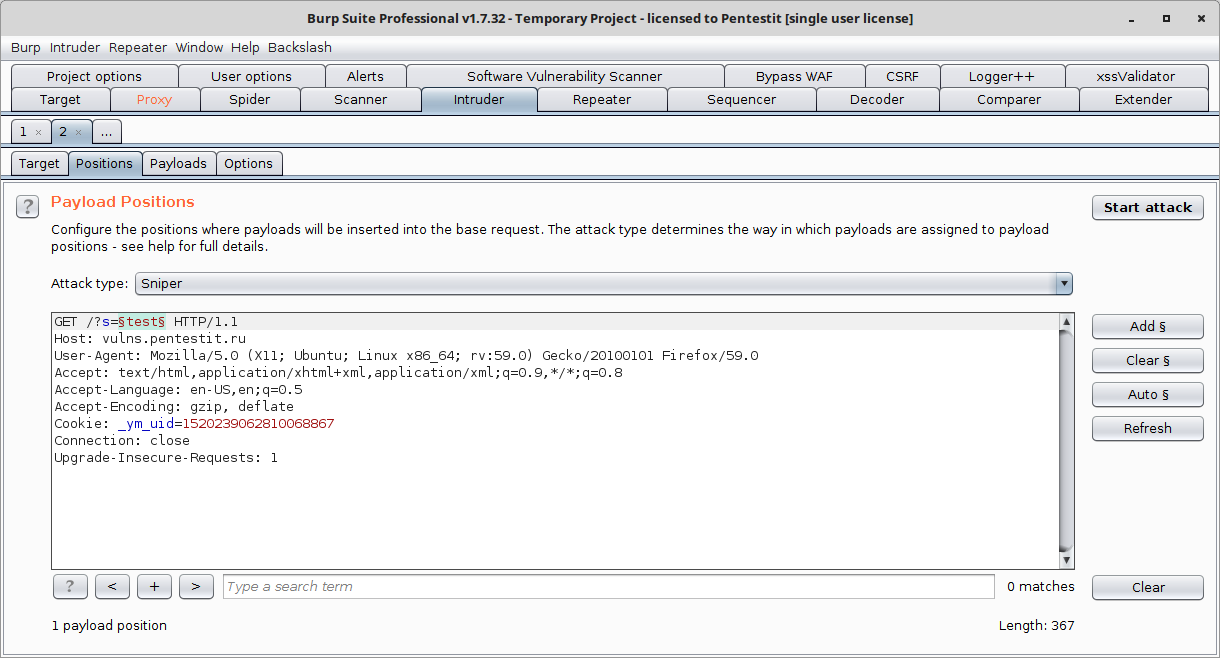
After selecting a position, you must select the list of payloads to apply, if necessary, set the signs of selection (to filter the results) and launch the attack:
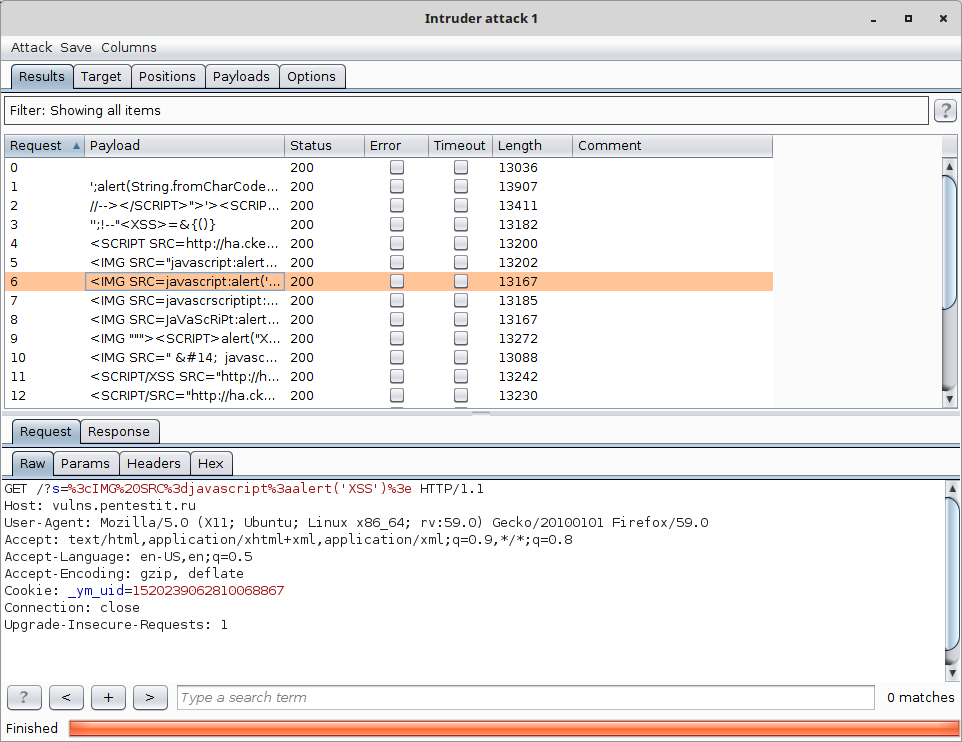
To identify various vulnerabilities, various sets of payloads are used, assembled into various “assemblies” and distributed by type.
Payloads all the things
Payloads All The Things - one of the most popular payload repositories, contains the following categories (which are enough for almost all occasions testing of web applications):
CRLF injection; Methodology and Resources; Remote commands execution; Web cache deception; CSV injection; NoSQL injection; Server Side Template injections; XPATH injection; CVE Exploits; OAuth; SQL injection; XSS injection File Inclusion - Path Traversal; Open redirect; SSRF injection; XXE injections; Insecured source code management; PHP juggling type; Tar commands execution; Java Deserialization; PHP serialization; Traversal directory. Seclists
SecLists is another popular “payload” build, designed to test both web applications and network infrastructure.
This assembly is notable for a more "narrow" specialization of payloads for specific types of vulnerabilities. For example, it contains specialized payloads for XSS:
XSS-BYPASS-STRINGS-BRUTELOGIC.txt; XSS-BruteLogic.txt; XSS-JHADDIX.txt; XSS-RSNAKE.txt; XSS-Vectors-Mario.txt; XSS-WITH-CONTEXT-JHADDIX.txt. Specialized payloads for SQL / NoSQL injection:
MSSQL-Enumeration.fuzzdb.txt; MSSQL.fuzzdb.txt; MYSQL.fuzzdb.txt; Metacharacters.fuzzdb.txt; MySQL-Read-Local-Files.fuzzdb.txt; MySQL-SQLi-Login-Bypass.fuzzdb.txt; NoSQL.txt. Intruder Payloads
Intruder Payloads - payloads repository by BruteX, Sn1per and Findsploit. In addition to fuzzing sheets, it contains attacking paylodes for various instruments (repeater, intruder) of the BurpSuite utility:
01_burpattack_basic_methods; 01_burpattack_dirbuster; 01_burpattack_fast_fuzz; 02_burpattack_vulnerabilities_all; 03_burpattack_find_inject; 03_burpattack_find_injectx; 04_burpattack_basic_fuzz; 04_burpattack_sqli_quick_fuzz; 05_burpattack_full_fuzz; burpattack_basic_auth_brute; burpattack_brute_force; burpattack_command_exec; burpattack_find_injectx; burpattack_nums_1-100; burpattack_overflow; burpattack_server_side_include; burpattack_shellshock; burpattack_sqli_authbypass; burpattack_sqli_error_based; burpattack_sqli_quick_fuzz; burpattack_sqli_time_based; burpattack_url_attacks; burpattack_wordpress; burpattack_xmlrpc_dos; burpattack_xpath_injection; burpattack_xss; burpattack_xss_stored; burpattack_xxe; burpconfig_default; burprepeater_xxe; shellshock_attack. Fuzzdb project
Fuzzdb contains lists of various payloads. For testing web applications, the “attack” list will be useful:
business-logic; control-chars; disclosure-directory; disclosure-localpaths/unix; disclosure-source; email; file-upload; format-strings; html_js_fuzz; http-protocol; integer-overflow; ip; json; ldap; lfi; mimetypes; no-sql-injection; os-cmd-execution; os-dir-indexing; path-traversal; redirect; rfi; server-side-include; sql-injection; string-expansion; unicode; xml; xpath; xss. Foospidy
The Foospidy repository contains a list of payloads to identify critical files and folders on a web server:
apache-user-enum-1.0.txt; apache-user-enum-2.0.txt; directory-list-1.0.txt; directory-list-2.3-big.txt; directory-list-2.3-medium.txt; directory-list-2.3-small.txt; directory-list-lowercase-2.3-big.txt; directory-list-lowercase-2.3-medium.txt; directory-list-lowercase-2.3-small.txt. These payloads will help to form the basis for the use of certain attacks, including obfuscation of payloads , their modification and combination.
Source: https://habr.com/ru/post/352422/
All Articles