Tomorrow is March 31st. Please back up
Recently, security threats have noticeably battered the nerves of the entire IT field: Wanna Cry, Petya, Meltdown New Year's surprise, etc. These are all major incidents. It is almost impossible to calculate how many small SQL injections, DDoS attacks, hacks, and theft occurred in small and medium businesses. High technologies are transforming at an incredible speed: what was scientific research in university laboratories and in companies yesterday is actively being introduced into production and used in the commercial sphere today. And the more technologies, the higher the likelihood of attacks, and in the most unexpected directions.
Tomorrow is International Backup Day, or Backup Day. One of those dates, which is better not to celebrate, but to work out. Let's see where in the second decade of the XXI century it is worth waiting for attacks.

Interesting zoology. Arctic fox always sneaks up unnoticed.
Our company RegionSoft Developer Studio worked in 2011, works in 2018 - and, delivering business solutions and on-premise CRM-system in particular, we face the same security problems for companies in different business areas. Just because for security, they do ... nothing. Well, how much can you? After all, the dangers are growing literally day by day, and the threats are far from being aimed at the giants with 100,500 levels of protection, but at the invaluable data of almost any business.
')
Let's look at two infographics. The first is the number of recorded incidents in the field of information security in 2011, the second is the same, but in 2017. Six years is a fairly short amount of time, even in conditions of explosive technological growth. Nevertheless, the situation has changed radically, the number and scale of attacks grows from year to year, they change their vector - from a large number of minor incidents to large and astounding colossal amounts of data.
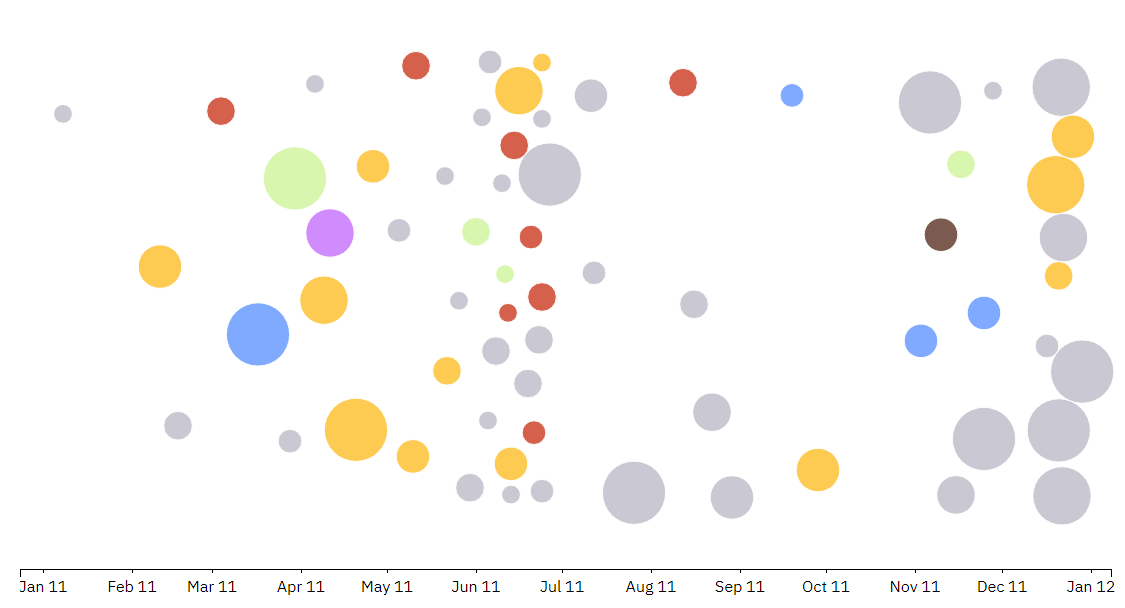 2011
2011
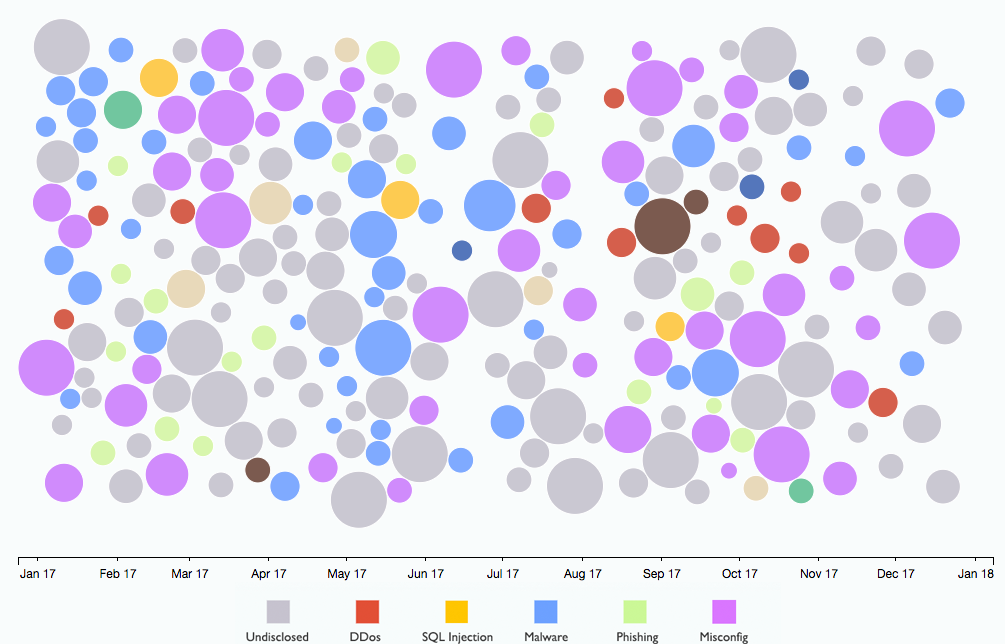
2017 year . Source Securityintelligence . This colorful picture illustrates not funny gaps in security. IBM X-Force identified 235 security incidents in 2017 based on 2.8 billion records. As you can see, DDoS has become more modest, but does not disappear, as well as malware. Among the novice leaders are attacks on the Internet of things, misconfigured cloud servers and attacks using cryptocurrencies.
A relatively new field of security is big data and machine learning, which are in service with both large companies and tech startups. Data is collected and aggregated using web applications, internal systems, and so on. All of them can be attacked, and dozens of data sources just get out of control. These are complex, the data collection and processing mechanisms are overloaded, high demands are placed on storage systems - this entire colossus takes a lot of time that needs to be spent on creating and deploying a security system. Such systems, due to their complexity, are highly vulnerable to hackers and cyber fraudsters. Alas, the majority of companies working with big data protect data streams almost “manually” using proprietary software. And here it is unclear what the score will be in a fight with cybercriminals. But such a situation should not slow down the industry, but rather stimulate a developed infrastructure: the development of specialized software, the creation of new ultra-secure storage systems, etc.
 Cyber Security Conference
Cyber Security Conference
December 20, 2017 began the attack on the Mongo DB database. Initially, pinpoint incidents occurred, but literally within a week, thousands of Mongo DB servers were completely destroyed (approximately 28,000, or more than half of all Mongo DB databases accessible via the Internet). They attacked not all the databases in a row, but those that were accessible through the world wide network and did not have a password in the DBMS administrator account. Instead of their data, users received a redemption message, moreover, groups of hackers exchanged information and a redemption request could appear for the second and third time (at the same time, hackers asked for from 150 to 500 dollars, these are relatively small amounts that companies went with relative ease) . Alas, hackers were not ethical and often forgot to export and save the data of each of the databases, as a result of which some companies lost their data forever. By the way, the attack was so massive due to the fact that it was not carried out manually as a one-time act, but with the help of automated scripts. And then tell me after this, did the developers and system administrators have no idea that the default DBMS settings make the database open for attack and as vulnerable as possible? And where were the backups? Rhetorical questions, hard lesson, which, by the way, not all taught.
 Believe me, it's much easier to do online.
Believe me, it's much easier to do online.
We are the developers of the RegionSoft CRM desktop CRM system and, of course, every day we face a business that considers the cloud to be the pinnacle of corporate IT infrastructure. Aggressive marketing of providers, cloud service providers and even the world's largest corporations is doing its job - there is nothing to conceal. But no one excludes the human factor, configuration errors, insider stuffing and outright hacking. Alas, Mongo DB was not the only victim, among the victims of big trouble in the clouds - the customers of Salesforce, Amazon S3, Bitrix 24, and in the recent past, and Google. And the victims of such cloudy troubles are becoming not only a paralyzed and dataless business, but also real corporate monsters. So, in July 2017, the giant telecom operator Verizon came under attack, as a result of which more than 14 million personal data records of subscribers from the United States hit the Internet. One of the service providers of the operator, NICE Systems, was guilty, and, due to an accidental error, left the data open on an unprotected Amazon S3 cloud server. The leaked data included the names of customers, mobile phones, PIN-codes, - in general, everything that will allow to bypass any form of authentication. It is not known why Verizon entrusted the data to an Israeli company, but there is a version that NICE Systems simply controlled the work of call center operators for Verizon with this information. Leak investigators found out that the pseudo-supplier was also connected with the French operator Orange.
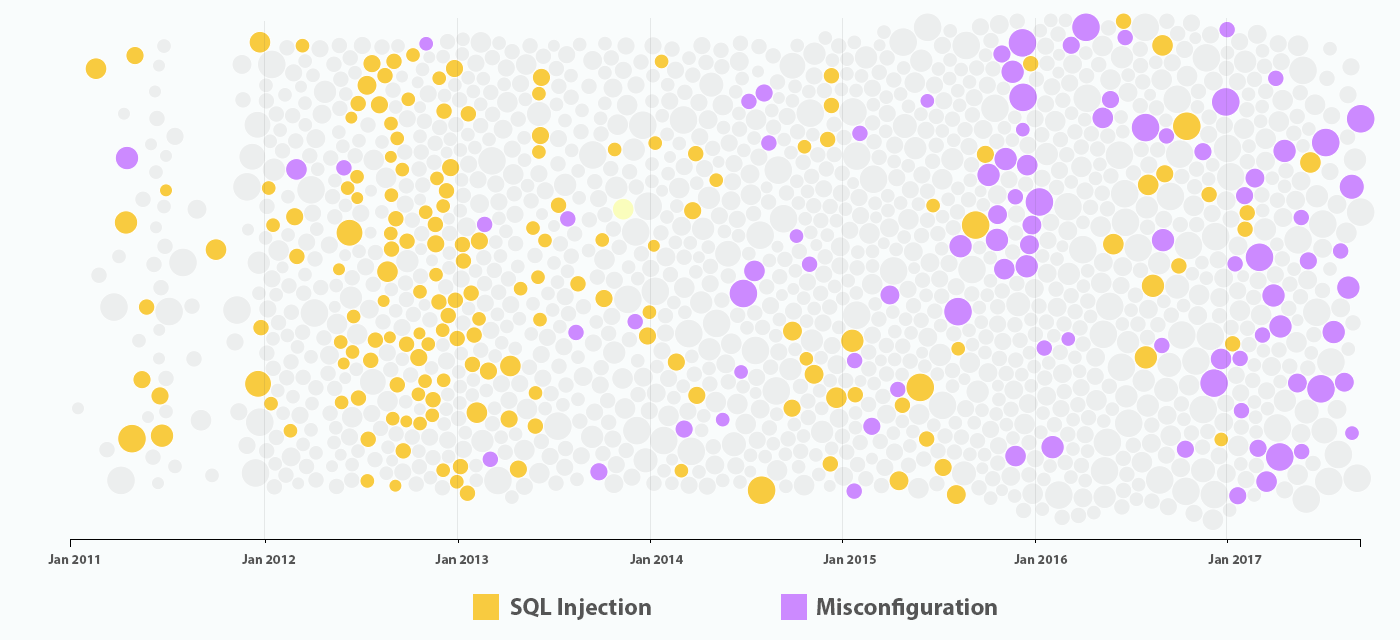 Source Securityintelligence . In 2017, as of September, IBM X-Force tracked more than 1.3 billion entries from incorrectly configured servers — a total of 24 incidents. To present this in perspective, such irregular configurations account for 71% of the total number of recorded leaks for the period up to 2017. Compared to SQL injections, this type of security breach has far more devastating consequences, since fewer attacks can compromise a thousand times more records (in SQL injections, millions, not billions, of records are compromised).
Source Securityintelligence . In 2017, as of September, IBM X-Force tracked more than 1.3 billion entries from incorrectly configured servers — a total of 24 incidents. To present this in perspective, such irregular configurations account for 71% of the total number of recorded leaks for the period up to 2017. Compared to SQL injections, this type of security breach has far more devastating consequences, since fewer attacks can compromise a thousand times more records (in SQL injections, millions, not billions, of records are compromised).
Another story related to the configuration of Amazon Web Services S3 Cloud, occurred in October 2017. Due to an error in determining the rights of access to data, an open consumer database of consumer data (from personal information to preferences, mortgages, etc.) was discovered by 123 million US citizens. Any authenticated Amazon AWS user could get access — that is, in essence, anyone who could register even a fresh account (even from the “left” mail). As it turned out, two analytical companies and the Census Bureau were involved in the records.
 Save your personal data here.
Save your personal data here.
So what are these “misconfigurations” (misconfigurations)? This is an internal problem of the company, and sometimes the provider or service provider, which can lead to easy access to the database without any hacker tricks. Gartner analysts believe that this type of security breach accounts for from 70 to 99% of all incidents. Anyone on any side of the relationship can be nosyachit: admin, developer, and even a testing engineer who has been approved for "live" assembly. The good news is that these problems can be avoided by being a bit more attentive, not leaving the DBMS without a password, and avoiding the favorite admin / admin combination and no less favorite root / root.
This does not mean giving up the cloud. But the customer base and important commercial information is better to keep and protect more reliably.
This year's cryptocurrency will not cease to “delight” us with new schemes of fraud, theft and cybercrime. Obviously, there will be a wave of high-profile disappearances (we, as a business representative, can hardly call these processes bankruptcy) Bitcoin companies that hit the bank at ICO. But it is much more interesting what cyber fraudsters will find in security holes of the blockchain. At the moment, there have already been several giant acts on the scale of the theft of bitcoins.
Cryptocurrency startup Tether lost $ 31 million in tokens. The company immediately stated that it would not go to buy tokens from fraudsters and would by all means prevent the release of this volume to cryptobirds. Despite the fact that Tether has already found the address where the hacker holds the stolen funds, the attack mechanism could not be understood.
Slovenian cryptobirth NiceHash recently stated that bitcoins worth $ 64 million were stolen. This is about 4,700 BTC, at the time of the theft each was worth 13,617 dollars. Again, the mechanism of the attack is unclear, as, indeed, the amount of the loss is very estimated. There is a version that bitcoins left the wallet of one of the users, and at the time of the sharp rise in the cost of cryptocurrency.
Meanwhile, each such theft sharply compromises the essence of cryptocurrency and can reduce the rate. When in 2016, Bitfinex stole almost 120,000 bitcoins worth $ 77 million from Bitfinex crypto-exchange, the fall in the rate was 20%. For the exchange rate of any asset, this is simply a tremendous fall, in fact, a collapse. Again, the fraud scheme was not fully disclosed. By the way, for several weeks of that August event, hackers managed to steal Ethereum for $ 50 million.
Cryptocurrency has not yet taken root in the Russian business, and, I think, it will not take root in serious companies. But if you suddenly want to attract a new audience and accept payments in Bitcoins or something else, remember that security needs to be given double attention.
In November 2016, the Mirai botnet turned hundreds of thousands of cameras and DVR devices into bots for DDoS attacks. In 2017, he returned and continued the destructive business, using also the NVR and expanding its geography. Such attacks can lead to the most unpredictable consequences, because the affected devices can be part of the urban infrastructure, an element of physical security of potentially dangerous objects, etc.
In August 2017, a WireX botnet consisting of tens of thousands of infected Android devices hit hotels in hotels. It is noteworthy (sadly, in fact) that the infection occurred after more than 300 official applications on Google Play, including such innocuous programs like file managers and media players.
Another manifestation of IoT threats is a Bluetooth vulnerability called BlueBorn. Without noise and dust, it can be used to compromise systems in the nearest area of coverage. This is a very dangerous threat from the point of view of potential scale: Bluetooth uses almost all wearable devices, as well as systems and elements of the smart home system, which, for reasons of economy, are often used in offices, in warehouses, in small industrial premises.
If you use IoT, you can theoretically get a huge network of bots that will be able to “put” hundreds of thousands of infrastructure facilities for a long time and collect the most valuable data (preferences, movements, health, etc.).
 Listen, and we made a backup?
Listen, and we made a backup?
We have previously cited stories related to data leakage from partners and employees, but we will repeat once again. If the reasons we talked about above often do not depend on us, and attacks are difficult to detect, then in the case of a business ecosystem, you yourself can hurt yourself. These are untested and unreliable employees, business coaches and consultants whom you trust your data yourself, naively believing that these are like doctors in your business. These are also partners, contractors and other companies that do something for you or have a relationship with you. When it comes to benefits, they will not be stopped by any signed NDA. Firstly, not everyone will go to court, secondly, they will still need to be found, and thirdly, even if problems are resolved, there will still be damage in the legal field. The advice here is one and rather universal - think with your head.
 In the right corner of the ring we have a firewall, encryption, antivirus and other cyber security. And in the left corner of the ring we have ... Vasya (human factor).
In the right corner of the ring we have a firewall, encryption, antivirus and other cyber security. And in the left corner of the ring we have ... Vasya (human factor).
We will not engage in moralizing and shipping you detailed advice on the protection of corporate information (we will write about this separately later). Remember just one thing. Here is a list:
There is nothing particularly complicated and unusual in it. But the execution of these points will already make your company several times more secure. Especially pay attention to the last three points - we still do not understand why they are so often not done? Maybe someone will open the secret in the comments.
Well, and so for that matter, today is Friday, the evening of which, by tradition, may be interesting. Here is another warning to you:

Our site with absolutely desktop business software and our flagship RegionSoft CRM.
 Our Telegram channel is BizBreeze . Anything about CRM and business, according to the mind, without copy-paste and 90% without advertising. Join reckless ranks.
Our Telegram channel is BizBreeze . Anything about CRM and business, according to the mind, without copy-paste and 90% without advertising. Join reckless ranks.
Tomorrow is International Backup Day, or Backup Day. One of those dates, which is better not to celebrate, but to work out. Let's see where in the second decade of the XXI century it is worth waiting for attacks.

Interesting zoology. Arctic fox always sneaks up unnoticed.
Our company RegionSoft Developer Studio worked in 2011, works in 2018 - and, delivering business solutions and on-premise CRM-system in particular, we face the same security problems for companies in different business areas. Just because for security, they do ... nothing. Well, how much can you? After all, the dangers are growing literally day by day, and the threats are far from being aimed at the giants with 100,500 levels of protection, but at the invaluable data of almost any business.
')
Let's look at two infographics. The first is the number of recorded incidents in the field of information security in 2011, the second is the same, but in 2017. Six years is a fairly short amount of time, even in conditions of explosive technological growth. Nevertheless, the situation has changed radically, the number and scale of attacks grows from year to year, they change their vector - from a large number of minor incidents to large and astounding colossal amounts of data.


2017 year . Source Securityintelligence . This colorful picture illustrates not funny gaps in security. IBM X-Force identified 235 security incidents in 2017 based on 2.8 billion records. As you can see, DDoS has become more modest, but does not disappear, as well as malware. Among the novice leaders are attacks on the Internet of things, misconfigured cloud servers and attacks using cryptocurrencies.
Where were the main "punctures" of the last two years?
Machine learning and big data
A relatively new field of security is big data and machine learning, which are in service with both large companies and tech startups. Data is collected and aggregated using web applications, internal systems, and so on. All of them can be attacked, and dozens of data sources just get out of control. These are complex, the data collection and processing mechanisms are overloaded, high demands are placed on storage systems - this entire colossus takes a lot of time that needs to be spent on creating and deploying a security system. Such systems, due to their complexity, are highly vulnerable to hackers and cyber fraudsters. Alas, the majority of companies working with big data protect data streams almost “manually” using proprietary software. And here it is unclear what the score will be in a fight with cybercriminals. But such a situation should not slow down the industry, but rather stimulate a developed infrastructure: the development of specialized software, the creation of new ultra-secure storage systems, etc.

Databases - watch out for protection
December 20, 2017 began the attack on the Mongo DB database. Initially, pinpoint incidents occurred, but literally within a week, thousands of Mongo DB servers were completely destroyed (approximately 28,000, or more than half of all Mongo DB databases accessible via the Internet). They attacked not all the databases in a row, but those that were accessible through the world wide network and did not have a password in the DBMS administrator account. Instead of their data, users received a redemption message, moreover, groups of hackers exchanged information and a redemption request could appear for the second and third time (at the same time, hackers asked for from 150 to 500 dollars, these are relatively small amounts that companies went with relative ease) . Alas, hackers were not ethical and often forgot to export and save the data of each of the databases, as a result of which some companies lost their data forever. By the way, the attack was so massive due to the fact that it was not carried out manually as a one-time act, but with the help of automated scripts. And then tell me after this, did the developers and system administrators have no idea that the default DBMS settings make the database open for attack and as vulnerable as possible? And where were the backups? Rhetorical questions, hard lesson, which, by the way, not all taught.

Cloud systems and services - data is shed by rain
We are the developers of the RegionSoft CRM desktop CRM system and, of course, every day we face a business that considers the cloud to be the pinnacle of corporate IT infrastructure. Aggressive marketing of providers, cloud service providers and even the world's largest corporations is doing its job - there is nothing to conceal. But no one excludes the human factor, configuration errors, insider stuffing and outright hacking. Alas, Mongo DB was not the only victim, among the victims of big trouble in the clouds - the customers of Salesforce, Amazon S3, Bitrix 24, and in the recent past, and Google. And the victims of such cloudy troubles are becoming not only a paralyzed and dataless business, but also real corporate monsters. So, in July 2017, the giant telecom operator Verizon came under attack, as a result of which more than 14 million personal data records of subscribers from the United States hit the Internet. One of the service providers of the operator, NICE Systems, was guilty, and, due to an accidental error, left the data open on an unprotected Amazon S3 cloud server. The leaked data included the names of customers, mobile phones, PIN-codes, - in general, everything that will allow to bypass any form of authentication. It is not known why Verizon entrusted the data to an Israeli company, but there is a version that NICE Systems simply controlled the work of call center operators for Verizon with this information. Leak investigators found out that the pseudo-supplier was also connected with the French operator Orange.

Another story related to the configuration of Amazon Web Services S3 Cloud, occurred in October 2017. Due to an error in determining the rights of access to data, an open consumer database of consumer data (from personal information to preferences, mortgages, etc.) was discovered by 123 million US citizens. Any authenticated Amazon AWS user could get access — that is, in essence, anyone who could register even a fresh account (even from the “left” mail). As it turned out, two analytical companies and the Census Bureau were involved in the records.

So what are these “misconfigurations” (misconfigurations)? This is an internal problem of the company, and sometimes the provider or service provider, which can lead to easy access to the database without any hacker tricks. Gartner analysts believe that this type of security breach accounts for from 70 to 99% of all incidents. Anyone on any side of the relationship can be nosyachit: admin, developer, and even a testing engineer who has been approved for "live" assembly. The good news is that these problems can be avoided by being a bit more attentive, not leaving the DBMS without a password, and avoiding the favorite admin / admin combination and no less favorite root / root.
This does not mean giving up the cloud. But the customer base and important commercial information is better to keep and protect more reliably.
Yesterday is exotic, today is the threat: cryptocurrency
This year's cryptocurrency will not cease to “delight” us with new schemes of fraud, theft and cybercrime. Obviously, there will be a wave of high-profile disappearances (we, as a business representative, can hardly call these processes bankruptcy) Bitcoin companies that hit the bank at ICO. But it is much more interesting what cyber fraudsters will find in security holes of the blockchain. At the moment, there have already been several giant acts on the scale of the theft of bitcoins.
Cryptocurrency startup Tether lost $ 31 million in tokens. The company immediately stated that it would not go to buy tokens from fraudsters and would by all means prevent the release of this volume to cryptobirds. Despite the fact that Tether has already found the address where the hacker holds the stolen funds, the attack mechanism could not be understood.
Slovenian cryptobirth NiceHash recently stated that bitcoins worth $ 64 million were stolen. This is about 4,700 BTC, at the time of the theft each was worth 13,617 dollars. Again, the mechanism of the attack is unclear, as, indeed, the amount of the loss is very estimated. There is a version that bitcoins left the wallet of one of the users, and at the time of the sharp rise in the cost of cryptocurrency.
Meanwhile, each such theft sharply compromises the essence of cryptocurrency and can reduce the rate. When in 2016, Bitfinex stole almost 120,000 bitcoins worth $ 77 million from Bitfinex crypto-exchange, the fall in the rate was 20%. For the exchange rate of any asset, this is simply a tremendous fall, in fact, a collapse. Again, the fraud scheme was not fully disclosed. By the way, for several weeks of that August event, hackers managed to steal Ethereum for $ 50 million.
Cryptocurrency has not yet taken root in the Russian business, and, I think, it will not take root in serious companies. But if you suddenly want to attract a new audience and accept payments in Bitcoins or something else, remember that security needs to be given double attention.
IoT: they will take away both the clothes and the bike
In November 2016, the Mirai botnet turned hundreds of thousands of cameras and DVR devices into bots for DDoS attacks. In 2017, he returned and continued the destructive business, using also the NVR and expanding its geography. Such attacks can lead to the most unpredictable consequences, because the affected devices can be part of the urban infrastructure, an element of physical security of potentially dangerous objects, etc.
In August 2017, a WireX botnet consisting of tens of thousands of infected Android devices hit hotels in hotels. It is noteworthy (sadly, in fact) that the infection occurred after more than 300 official applications on Google Play, including such innocuous programs like file managers and media players.
Another manifestation of IoT threats is a Bluetooth vulnerability called BlueBorn. Without noise and dust, it can be used to compromise systems in the nearest area of coverage. This is a very dangerous threat from the point of view of potential scale: Bluetooth uses almost all wearable devices, as well as systems and elements of the smart home system, which, for reasons of economy, are often used in offices, in warehouses, in small industrial premises.
If you use IoT, you can theoretically get a huge network of bots that will be able to “put” hundreds of thousands of infrastructure facilities for a long time and collect the most valuable data (preferences, movements, health, etc.).

Their merge
We have previously cited stories related to data leakage from partners and employees, but we will repeat once again. If the reasons we talked about above often do not depend on us, and attacks are difficult to detect, then in the case of a business ecosystem, you yourself can hurt yourself. These are untested and unreliable employees, business coaches and consultants whom you trust your data yourself, naively believing that these are like doctors in your business. These are also partners, contractors and other companies that do something for you or have a relationship with you. When it comes to benefits, they will not be stopped by any signed NDA. Firstly, not everyone will go to court, secondly, they will still need to be found, and thirdly, even if problems are resolved, there will still be damage in the legal field. The advice here is one and rather universal - think with your head.

We will not engage in moralizing and shipping you detailed advice on the protection of corporate information (we will write about this separately later). Remember just one thing. Here is a list:
- set complex passwords on the DBMS
- change default settings
- pursue an ITAM and ITSM strategy
- don't trust beginners
- Do not disclose data before business coaches
- put minimal protection on the site
- train employees to work safely with information
- upgrade to the latest versions of corporate software and OS
- make backups
- make backups
- make backups.
There is nothing particularly complicated and unusual in it. But the execution of these points will already make your company several times more secure. Especially pay attention to the last three points - we still do not understand why they are so often not done? Maybe someone will open the secret in the comments.
Well, and so for that matter, today is Friday, the evening of which, by tradition, may be interesting. Here is another warning to you:

Our site with absolutely desktop business software and our flagship RegionSoft CRM.
Interesting links:
When preparing the article, we were most pleased with the IBM Securityintelligence security blog, which we recommend to read to everyone - security is fair, interesting, and most importantly, fairly accessible English.
→ By the way, if you want to take a closer look at security incidents, IBM has a cool interactive map . With her, the rest of Friday will pass unnoticeably noticeable. Look through the year on the right in the block of text - and you will see that 2011 is very different from 2017. Incidents have become larger in scope (more circles - this is more data covered).
→ By the way, if you want to take a closer look at security incidents, IBM has a cool interactive map . With her, the rest of Friday will pass unnoticeably noticeable. Look through the year on the right in the block of text - and you will see that 2011 is very different from 2017. Incidents have become larger in scope (more circles - this is more data covered).
Source: https://habr.com/ru/post/352412/
All Articles