Conference DEFCON 21. “The secret life of SIM cards”. Eric Butler, Karl Kosher
My name is Eric Butler, and this is Carl Kosher, and we want to talk with you about reading, creating, loading and using code on SIM-cards. This project started last year when I found out about the 2012 Tourcamp event, a hackers' camp on the coast of Washington, such a visiting DEFCON. There were no hotels, life in tents in the open air, it was already the second camp, I really liked the first one, I invited friends and we decided to go there. This event was dedicated to the launch of the GSM network in several areas of the United States, and my task was to obtain several SIM cards for this.

I didn’t know anything about what SIM cards are, so I had to study the question and find out the following:
')
The last point surprised me, because I had never heard before that SIM cards can work with applications. It turns out, a long time ago, when there were no “iPhones” or “androids”, applications were located on the SIM card. The phone was a simple call - you could pull a SIM card out of it and move it to another phone along with all your contacts, programs, and so on. Some operators, for example, Telcom, were the owners of SIM cards, controlling the applications installed on them.
A decade later, everything changed radically. Today, the sim card is a tiny handheld computer that you can not control. However, many of the principles of the mid-90s have been preserved to this day, and I tried to understand how it all works. I had a great opportunity to play with SIM cards in the camp, and I thought that it would be good to get cards that run applications.
It was not an easy task, because there are a lot of operators who want to sell about 500 thousand of such cards, but we only needed 500 pieces. Most of the operators force them to sign an agreement on non-disclosure of confidential information NDA, which we did not want to do, because we were going to tell everything that we would have learned from studying such cards.
Some of the cards that we found supported the operation of applications, but did not support GSM, and this did not suit us. In addition, there was too little documentation on how to program them. It took us a long time to summarize all the information found, but we learned a lot of interesting things about the technology of programmable SIM cards.
Sim cards, which we managed to get in the end, had such characteristics.
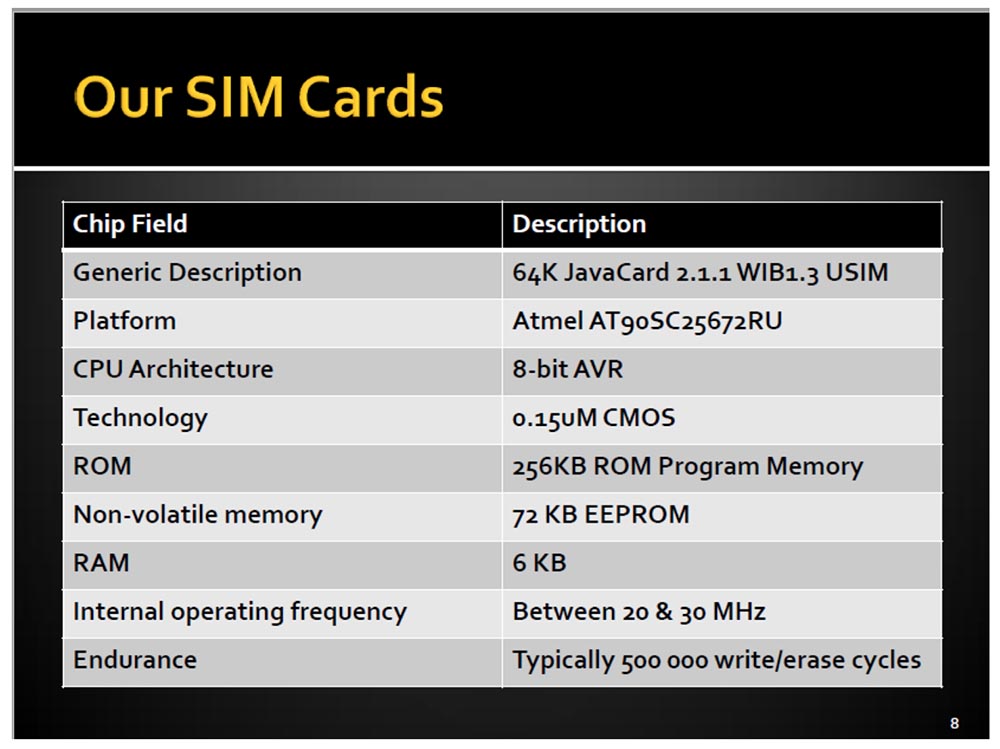
They had their own AVR processor, not the same as the Arduino, with 64 KB of memory and a tiny 6 KB of RAM. They were called JavaCard and worked with a frequency of 20 to 30 MHz, so these mini-computers had their limitations.
Based on these SIM cards, we invented our own cellular network for our camp. I wanted people who come to the camp to choose a tent for themselves, go through registration and get a schedule, receive our SIM cards at the entrance for use in a common internal network called Shadytel.

So we distributed more than 400 of our 500 cards, and each received their own mobile number. Our experimental network had the following capabilities:
We handed guests not only a SIM card, but also all private information necessary for its use, similar to the one that goes to a regular SIM card, and also open codes, which are usually encrypted on operators' cards. In addition, our network provided an opportunity to make free calls anywhere, so that you could freely call even your mom in Australia. Our network was very functional and not at all expensive; we even had a license from the US Federal Communications Commission (FCC), so our network worked quite legally.
Consider what allowed applications, or applets, which we have programmed on SIM cards.
They were launched on a SIM card processor, regardless of the phone, so that it didn’t even “see” what was happening, and, depending on the operating system used, they directly connected to the BaseBand (in the case of the iPhone). Applications could be remotely installed on the card in “silent installation” mode using media. What is a "carrier", I will explain later. Today, most carriers of SIM-cards support such applications.
Our cards supported the operation of several applications that were selected using the AID and controlled by the standard Card Manager selection application.
In fact, GSM support "SIM" is simply an application on a physical integrated circuit card (UICC).
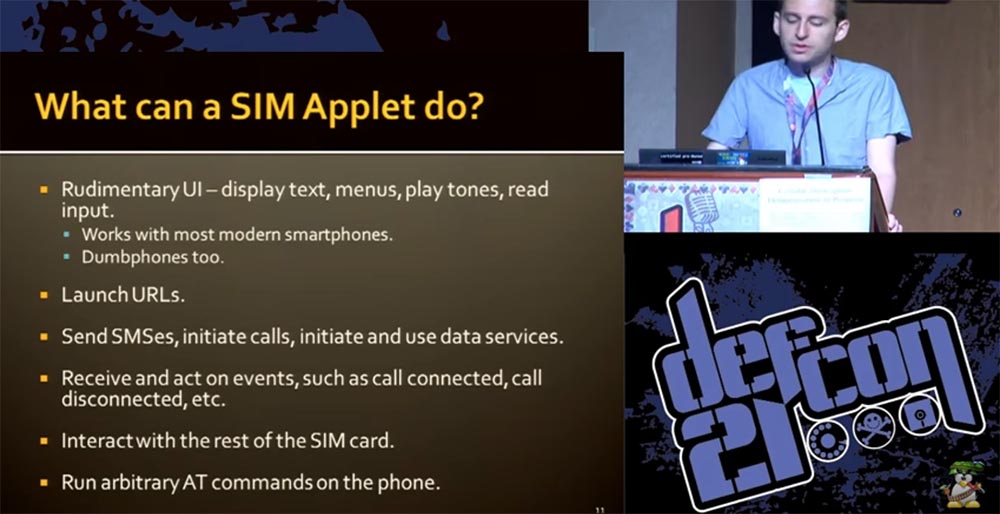
Here is what our applets could do:
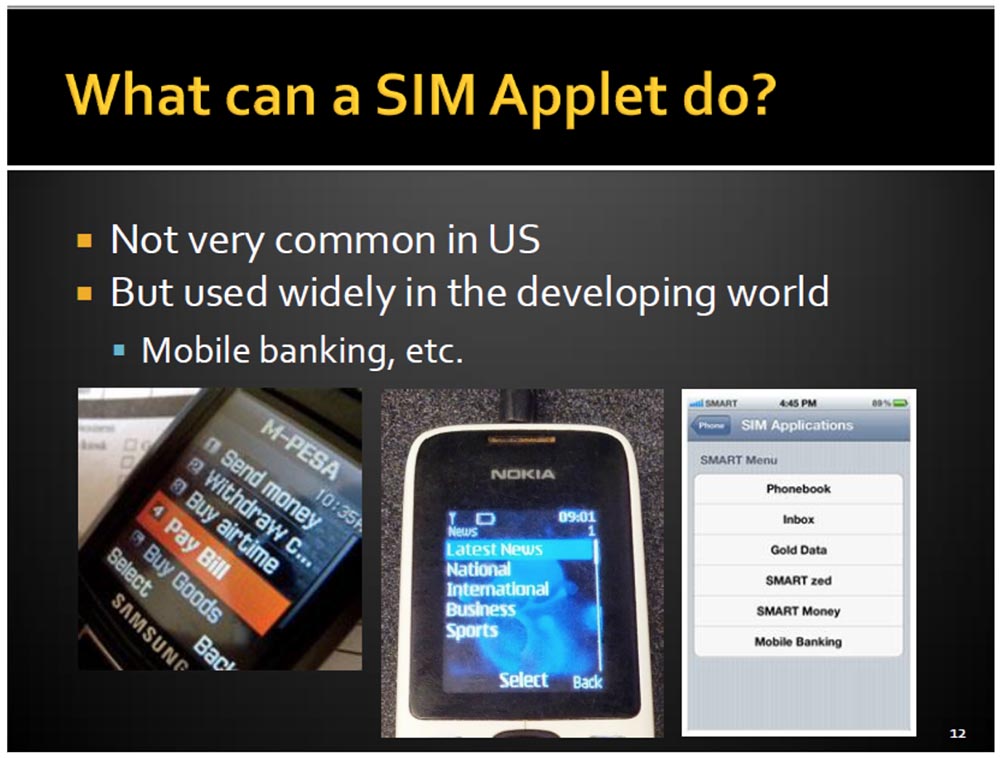
I will show you some examples of how the smartphone screen looks when using our maps. It depicts mobile banking features that are not particularly common in the US, but are widely used throughout the world.
And now Carl will tell you how our applications work.

We used the following technologies:
The design of a smart card is designed to secure data storage and processing, and communication is done using packets called APDUs.
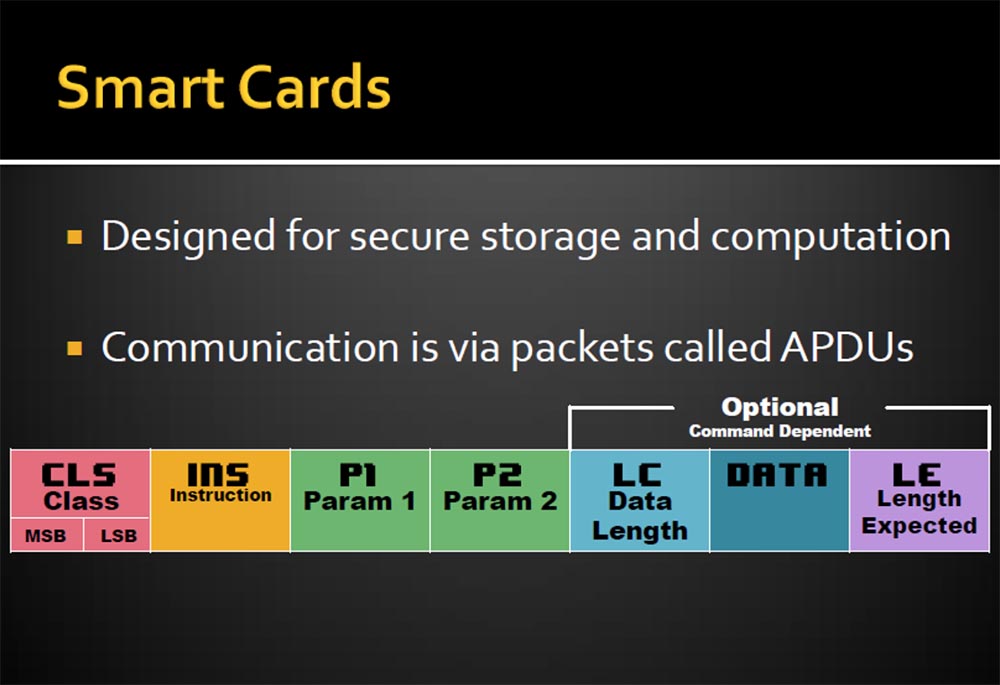
A feature of smart cards is the non-recoverability of keys and the procedure for encrypting and decrypting, so you can use personal data such as passwords and logins to access the banking system, digital signatures, access to satellite television. The CLS parameter is responsible for this. This is followed by instructions for processing information INS. APDU packets are a stream of bytes, which are described by parameters P1 and P2, and additional entries, such as the length of the LC data transmission, the data itself, and the extension of the LE length.
On the next slide, you see a JavaCard. This is Java and not Java at the same time, because there is no garbage, no letters, strings, multidimensional arrays. If you are lucky, you can find several integer data types int. The structure of these maps is extremely simple. Of course, there are no standard APIs, such as files or themes, you can get rid of verification, but there are some exceptions. Samples and classes of variables are stored in the EEPROM memory, which has a limited number of write cycles of approximately 500,000. Therefore, depending on the type of card, you may have problems updating these variables.
I will tell you how we created our smart card applications. There are several specialized commercial IDE development environments, but you can do without them, because firstly, we wanted to make our applications as open as possible to everyone, and secondly, these commercial tools cost about $ 3000.
From Oracle, we downloaded the free Java Card Development Kit editor. If you are using Eclipse, you need to remove the standard JRE (Java Runtime) library system from the map and add the Java Card library to help describe classes and the like. In addition, we ourselves wrote several programs to facilitate the work.
The STK application functions as follows:
Thus, after downloading the phone, the application can use all 200 available functions, selecting an application from the menu launches the corresponding event, then the application sends the phone back UI requests.
This is what our code looks like.

Java allows you to set a card class using two standard methods: creating and registering a class using Java Runtime and installing a class using the SIM card toolkit. The latter method is used when an event needs to be transferred to the card from the phone.
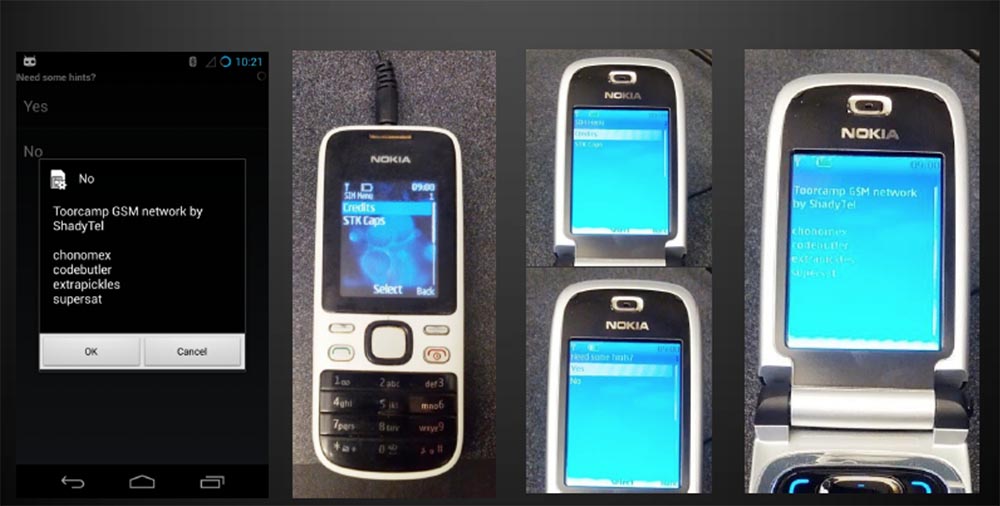
The next slide shows what the application we created for the Tourcamp camp looks like. By activating the card, you can choose one of the available networks. When you restart and connect to our network, you will be asked if you want to enable encryption, and this is another interesting feature of our application. It allows you to save hints on a protected device so that they cannot be extracted from there. In addition, we have implemented unwanted intervention markers that allow us to find out if someone has viewed these prompts and allow us to view the content remotely, which I will discuss later.
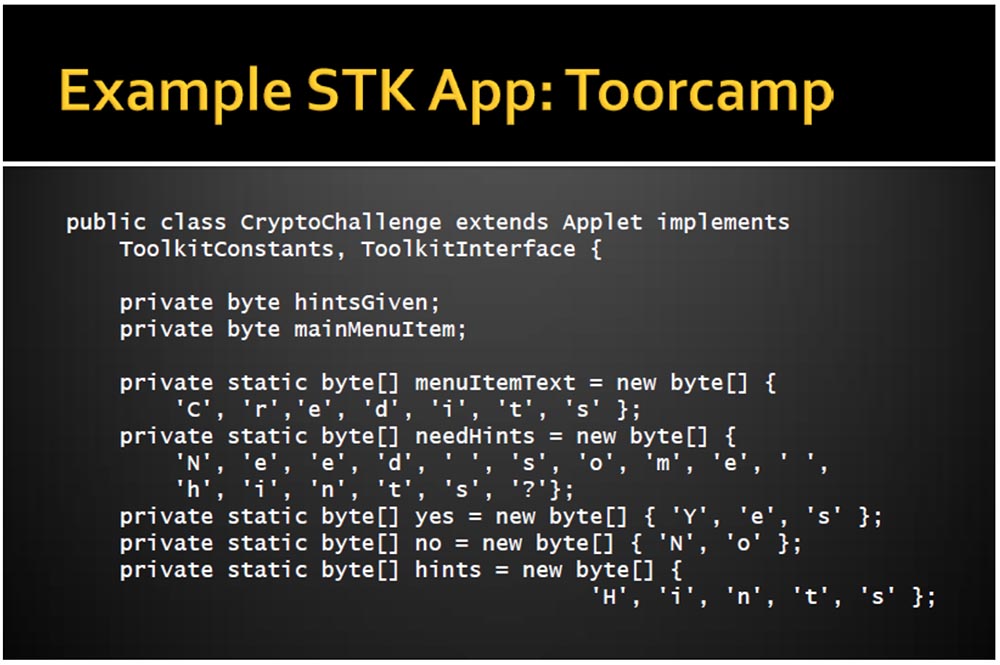
I warn you that the program code of our application looks pretty ugly. If you remember, there are no strings or groups here, so we are forced to create arrays of individual bytes with individual letters. This is a rather painful process, but we have withstood it.
Next, we programmatically described the application self-registration procedure using the SIM Toolkit, the process of selecting a program in the phone menu, displaying prompts on the screen and other features. We tried to prescribe everything to the maximum as we could, it looks awful, but it works. A full description of the program is given on our website, so you do not need to remember what is shown on these slides. Now our report will continue Eric.

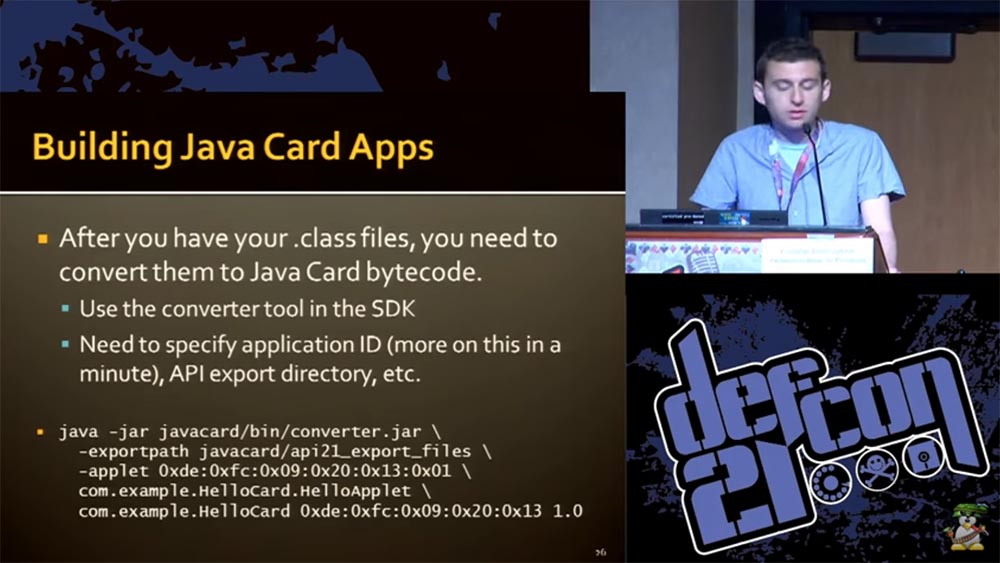
The easiest way is to use the old version of Java 1.1 encoding and version 1.3 code compatibility. After you have created the class files, you must re-encode them for the Java Card. To do this, use the converter available in our SDK. You will also need some ID applications (most literally for one minute), an API export directory, and so on. These files should be understandable by the OS of the phone, so they are made in the .jar format.
We also developed a special Makefiles program that is available on the site . The converter issues a CAP file, which is a Zip archive of CAP components (Java Card code).
One of the important questions that needed to be answered before starting work on the project was how to interact with the SIM card. We needed a card reader. They are of two types: for connection to the PCSC port (PC / Smart Card API) and connected to the serial port Serial. The first ones are usually universal, so you need to have an adapter for working with a standard-sized SIM card, and the second ones are much smaller and are used specifically for SIM cards.
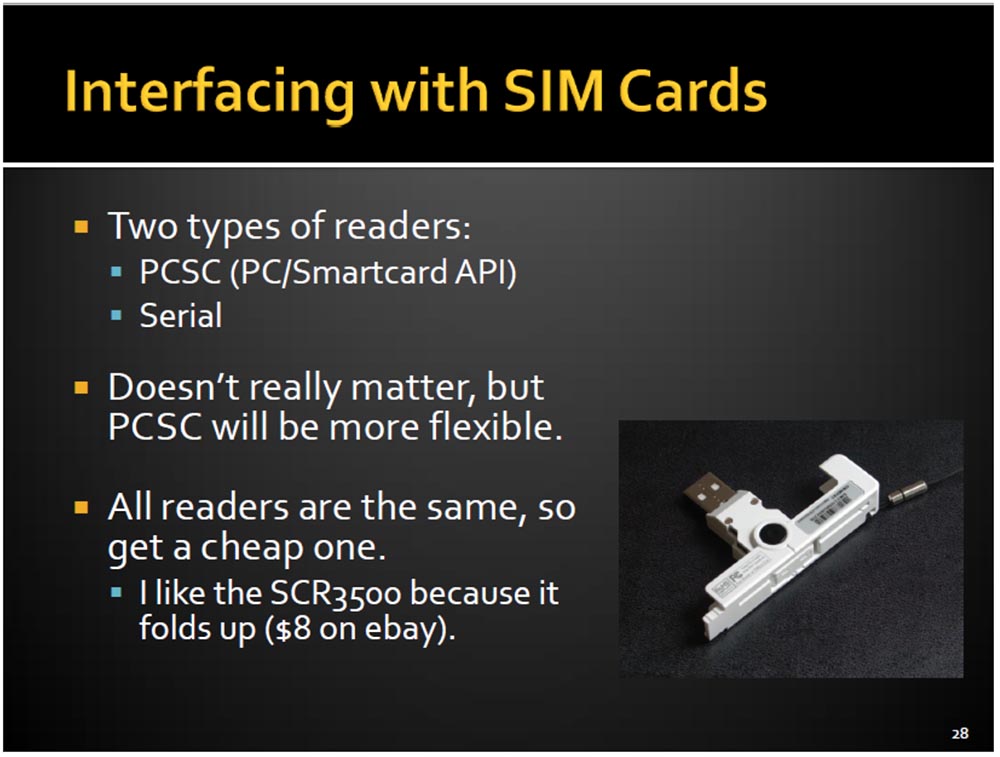
Functionally, there is no difference between them, but the PCSC version is more convenient to use. It uses official software designed specifically for the API and facilitating work with the computer. In addition, there are many open applications for working with SIM cards, which are easier to use with the PCSC option. All card readers are the same, so I used the cheapest SCR3500 bought on eBay for $ 8.
So, we wrote this awful looking code, then processed it with a Java compiler and converted it into a CAP file. Then we tried to place it on the SIM card, for which we used the popular GPShell Tool, but we did not succeed. The seller of SIM-cards advised us another program with a simple and convenient interface, which could not be found anywhere, and then promised us to sell it for $ 600, although he did not have this program either.
Therefore, we used a program called SIM Alliance Loader, the slide below shows its window. We used the first version of this program, but the second version is now available. SIM Alliance is a group that develops software for working with SIM cards. The SIM Alliance Loader program is an adaptation of Java applications for Windows and is intended for experts who understand what they are doing.

But if you understand the question, transferring the application to the SIM card will take just a couple of minutes. However, given that we had about a thousand cards that we wanted to prepare for Tourcamp, this recording technology would take too much time, so we decided to use something more productive. Therefore, we turned to the Global Platform - the standard for downloading, installing and managing applications on the Java Card. Depending on the application, this software allows the use of protocols and commands, as well as encryption and authentication. It also allows you to perform some external procedures without a SIM card, for example, to verify the binary codes of our applets.
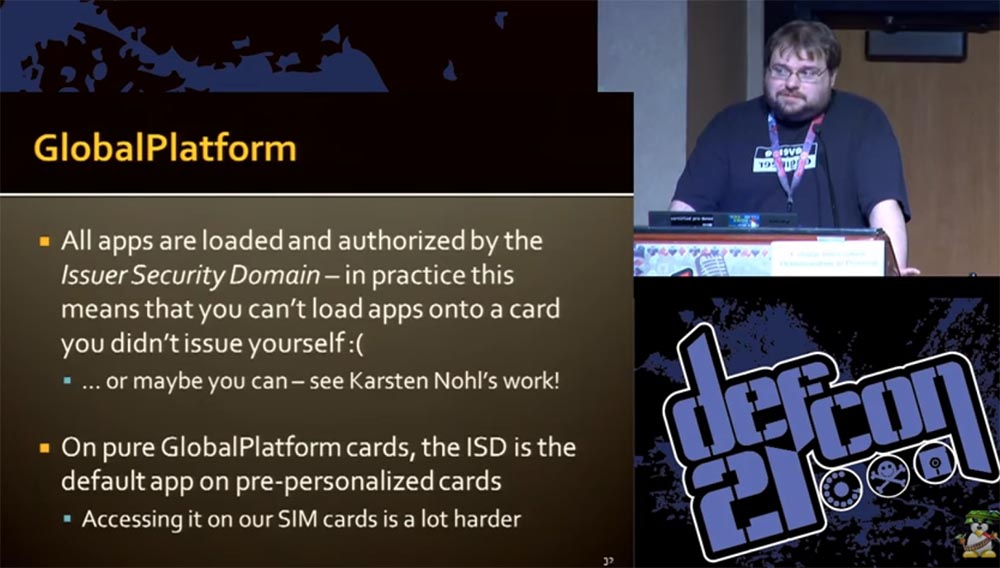
In the process, it turned out that all applications are loaded and are authorized in the Issuer Security Domain (ISD) application - the Global Platform authentication system. In practice, this means that you cannot load an application onto a map if you have not developed it yourself, but there are exceptions described in the work of Karsten Knowl.
On pure Global Platform SIM cards, the ISD application is available by default, but our cards are much more difficult to access because the GSM application is installed by default on them and there is not even an opportunity to access the Global Platform application. I will briefly describe the procedure for installing our application on a SIM card.
The process consists of two stages: the DOWNLOAD command (loading an array of binary codes) and the SETUP command (creating an instance of the application on the SIM card). Single CAP components are combined together and sent to the map in blocks using the LOAD command. There are three types of Application ID (AID) involved in this process:
As a result, the CAP-file is unarchived, data is extracted and recorded on the SIM card. The only way to “communicate” the Global Platform application with our SIM card is through the air transfer mechanism, that is, via SMS messages. In fact, we did not send traditional SMS, but simply generated commands on the map using SMS packages.
It was a long and rather time-consuming process. For the GSM 03.48 standard, it consisted in using the CAT shell (AoC2), which allows us to perform the necessary actions with the card. At the first stage of the process, it includes the SMS PP (D1) download, which, in turn, consists of the identification of the device and the SMS TPDU transport data packet.

SMS TPDU includes user header and data. User data also includes a header, a batch of commands, a subtitle (security settings, application selection). It, in turn, uses a TAR ID of 3 bytes in size (I wonder how PowerPoint withstood such nonsense). At this, the internal data limit is exhausted, and at the very end of the list there is the very APDU that our Global Platform needs. Thus, this entire cumbersome mechanism serves to send a tiny array of data.
In case you do not want to do this, there is one more mechanism for remotely sending the APDU to the SIM card. It requires the use of cellular communication to send SMS with installation commands, which requires network authentication. However, Carsten Knowle describes a method when encryption errors allow you to extract the keys of a symmetric DES encryption algorithm using the brute-force method, that is, without network authentication.
The Shadysim boot script is written in Python and runs on OSX, Linux and Windows. The next slide shows how it looks. Downloading is performed using a PC to which a SIM card card reader is connected.

The next slide shows the parameters that must be set to install the application on the map.
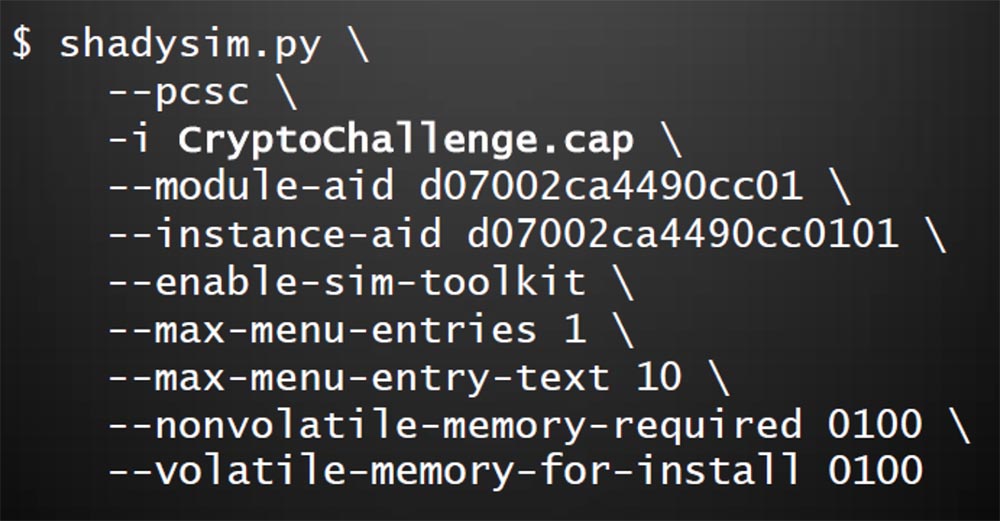
Here you can set the main class of the card, reserve physical and operational memory, determine the size of the text menu that will be displayed on the smartphone screen, record the command to launch the Toolkit, and so on. You can enter any more parameters using hex-code. Finally, a list of applications is entered with the - t parameter, which allows you to update the phone book.
How do we know that our application works? Eric will tell you about this.
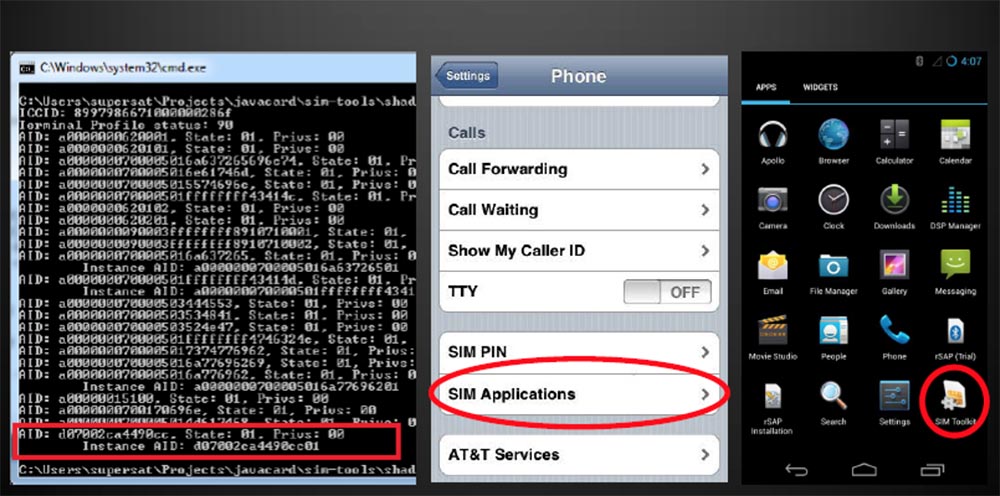
The next slide shows what a running application looks like. The screen of the screen with the Python program is shown on the left, the iPhone settings menu with the SIM Applications item and the icon of our program on the Android Applications tab are shown in the middle.
Karl told you how hard programming was, but testing was no easier. In order to check whether our program works, it was necessary to do the following:
If the code does not work, the whole procedure must be repeated. How can you speed up and facilitate this procedure?
To do this, you can use the Android simulator for SIM cards. There is an open source SEEK, which is an SDK for Android. It includes patches for accessing a SIM card or SD card via a USB PCSC card reader and prevents the incompatibility of the SIM card from connecting to a computer and phone. You run the Android emulator on your computer and test your card without using a smartphone.
Can I use my smartphone as a card reader? Karl will answer this question.
The fact is that most radio interfaces do not allow direct communication with a SIM card. You can solve this problem using the Remote SIM Access Protocol. This method exists in Europe under the name "remote access to the SIM card via Bluetooth." This is a profile with built-in authentication. He needs to write an application that can send and receive APDUs. However, this method in some cases can turn your smartphone into a “brick”, so you should not install this profile on all smartphones in a row.
I want to introduce you to the future directions of our development. The STK kit is a great tool, but has limitations in use. Hence the question arises, is it possible to create an SMS botnet? After all, SIM cards are designed to communicate via a cellular network and do not need operating systems to exchange information, so it is possible to integrate them into a common network.
The integration of Android applications with SIM applets, for example, storing secure SSH private keys for authorization on a SIM card and secure operations with BitCoin e-currency, also opens up wide opportunities. We have an idea to use Android applications for OTA technology - “software update over the air”, using SMS packages for this.
Another direction is the improvement of the functions of NFS, Eric will tell you about it.

For example, using the single-wire SWP protocol, it will be possible to establish a direct connection between the SIM card and the NFS controller. This means that your SIM card will be able to work without the help of the phone’s operating system directly, just as VISA or MasterCard bank cards work.
The SIM card can work as a security element or be used in ISIS mobile payment systems. This is an American system that is being introduced very slowly, it combines mobile banking and Telcos mobile communications, and our idea may be useful for them.
The sim card can also be used to regain lost control of the mobile app store. The use of SIM cards as a security element is possible due to the following properties:

Therefore, I think that manufacturers of SIM cards should reflect on their potential capabilities and develop their functions in the areas described by us.
If you wish, you can download our application on the site , for its operation you will need certain devices with a cost of no more than $ 20, for example, a card reader. In the same place you can find slides of this presentation, scripts for applets, the Makefiles program for the Java Card, patches for the Android emulator and many more useful things.
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The Truth About VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?

I didn’t know anything about what SIM cards are, so I had to study the question and find out the following:
')
- SIM, or Subscriber Identification Module is a mobile subscriber identification module;
- the SIM card has an IMSI identification key and a symmetric Ki key;
- it has a built-in security module that does not allow you to either extract or clone keys;
- they are used by GSM operators, and now LTE (Verizon 4G network);
- can also run applications.
The last point surprised me, because I had never heard before that SIM cards can work with applications. It turns out, a long time ago, when there were no “iPhones” or “androids”, applications were located on the SIM card. The phone was a simple call - you could pull a SIM card out of it and move it to another phone along with all your contacts, programs, and so on. Some operators, for example, Telcom, were the owners of SIM cards, controlling the applications installed on them.
A decade later, everything changed radically. Today, the sim card is a tiny handheld computer that you can not control. However, many of the principles of the mid-90s have been preserved to this day, and I tried to understand how it all works. I had a great opportunity to play with SIM cards in the camp, and I thought that it would be good to get cards that run applications.
It was not an easy task, because there are a lot of operators who want to sell about 500 thousand of such cards, but we only needed 500 pieces. Most of the operators force them to sign an agreement on non-disclosure of confidential information NDA, which we did not want to do, because we were going to tell everything that we would have learned from studying such cards.
Some of the cards that we found supported the operation of applications, but did not support GSM, and this did not suit us. In addition, there was too little documentation on how to program them. It took us a long time to summarize all the information found, but we learned a lot of interesting things about the technology of programmable SIM cards.
Sim cards, which we managed to get in the end, had such characteristics.

They had their own AVR processor, not the same as the Arduino, with 64 KB of memory and a tiny 6 KB of RAM. They were called JavaCard and worked with a frequency of 20 to 30 MHz, so these mini-computers had their limitations.
Based on these SIM cards, we invented our own cellular network for our camp. I wanted people who come to the camp to choose a tent for themselves, go through registration and get a schedule, receive our SIM cards at the entrance for use in a common internal network called Shadytel.

So we distributed more than 400 of our 500 cards, and each received their own mobile number. Our experimental network had the following capabilities:
- all calls and text messages were free;
- people outside the camp could call you on a mobile phone using the prefix 1-337-422-4364 in front of your number;
- You could create your own SMS encoder using our API hosted on the site ;
- SIM card supported software JavaCard v.2.1.1. and STK applets and you could learn about creating your own applets on the same site;
- to call the 911 service, it was necessary to use another network, since our Shadytel did not support such a call.
We handed guests not only a SIM card, but also all private information necessary for its use, similar to the one that goes to a regular SIM card, and also open codes, which are usually encrypted on operators' cards. In addition, our network provided an opportunity to make free calls anywhere, so that you could freely call even your mom in Australia. Our network was very functional and not at all expensive; we even had a license from the US Federal Communications Commission (FCC), so our network worked quite legally.
Consider what allowed applications, or applets, which we have programmed on SIM cards.
They were launched on a SIM card processor, regardless of the phone, so that it didn’t even “see” what was happening, and, depending on the operating system used, they directly connected to the BaseBand (in the case of the iPhone). Applications could be remotely installed on the card in “silent installation” mode using media. What is a "carrier", I will explain later. Today, most carriers of SIM-cards support such applications.
Our cards supported the operation of several applications that were selected using the AID and controlled by the standard Card Manager selection application.
In fact, GSM support "SIM" is simply an application on a physical integrated circuit card (UICC).

Here is what our applets could do:
- perform the usual functions of cell phones using the software interface of the OS - show text, menu, play ringtones, read incoming messages;
- work with modern “smart” phones (and with “unintelligent” ones too);
- upload URL;
- send SMS, initiate calls and data services;
- accept and implement events such as connecting and disconnecting calls, and carry out about 200 more functions available to regular SIM cards;
- interact with other SIM-cards;
- execute arbitrary AT commands on the phone to control the GSM modem.
I will show you some examples of how the smartphone screen looks when using our maps. It depicts mobile banking features that are not particularly common in the US, but are widely used throughout the world.

And now Carl will tell you how our applications work.

We used the following technologies:
- SmartCard - the physical connection between the SIM card and the phone, the same as any smart card;
- Java Card - Java programming for smart cards, which is the easiest way to write applications, it appeared in the early 90s;
- SIM Toolkit (STK) API - interface of interaction between applications and the interface of the operating system of the smartphone, which allows the card to "talk" with the phone, taking from it and sending it events;
- GlobalPlatform is a standard for downloading and managing applications on a SIM card, developed by the creators of the VISA system.
The design of a smart card is designed to secure data storage and processing, and communication is done using packets called APDUs.

A feature of smart cards is the non-recoverability of keys and the procedure for encrypting and decrypting, so you can use personal data such as passwords and logins to access the banking system, digital signatures, access to satellite television. The CLS parameter is responsible for this. This is followed by instructions for processing information INS. APDU packets are a stream of bytes, which are described by parameters P1 and P2, and additional entries, such as the length of the LC data transmission, the data itself, and the extension of the LE length.
On the next slide, you see a JavaCard. This is Java and not Java at the same time, because there is no garbage, no letters, strings, multidimensional arrays. If you are lucky, you can find several integer data types int. The structure of these maps is extremely simple. Of course, there are no standard APIs, such as files or themes, you can get rid of verification, but there are some exceptions. Samples and classes of variables are stored in the EEPROM memory, which has a limited number of write cycles of approximately 500,000. Therefore, depending on the type of card, you may have problems updating these variables.
I will tell you how we created our smart card applications. There are several specialized commercial IDE development environments, but you can do without them, because firstly, we wanted to make our applications as open as possible to everyone, and secondly, these commercial tools cost about $ 3000.
From Oracle, we downloaded the free Java Card Development Kit editor. If you are using Eclipse, you need to remove the standard JRE (Java Runtime) library system from the map and add the Java Card library to help describe classes and the like. In addition, we ourselves wrote several programs to facilitate the work.
The STK application functions as follows:
- the application is loaded on the card;
- the application registers itself using the SIM Toolkit API;
- the phone informs the STK about its capabilities, and the STK informs the phone about the registered application.
Thus, after downloading the phone, the application can use all 200 available functions, selecting an application from the menu launches the corresponding event, then the application sends the phone back UI requests.
This is what our code looks like.

Java allows you to set a card class using two standard methods: creating and registering a class using Java Runtime and installing a class using the SIM card toolkit. The latter method is used when an event needs to be transferred to the card from the phone.
The next slide shows what the application we created for the Tourcamp camp looks like. By activating the card, you can choose one of the available networks. When you restart and connect to our network, you will be asked if you want to enable encryption, and this is another interesting feature of our application. It allows you to save hints on a protected device so that they cannot be extracted from there. In addition, we have implemented unwanted intervention markers that allow us to find out if someone has viewed these prompts and allow us to view the content remotely, which I will discuss later.

I warn you that the program code of our application looks pretty ugly. If you remember, there are no strings or groups here, so we are forced to create arrays of individual bytes with individual letters. This is a rather painful process, but we have withstood it.

Next, we programmatically described the application self-registration procedure using the SIM Toolkit, the process of selecting a program in the phone menu, displaying prompts on the screen and other features. We tried to prescribe everything to the maximum as we could, it looks awful, but it works. A full description of the program is given on our website, so you do not need to remember what is shown on these slides. Now our report will continue Eric.

The easiest way is to use the old version of Java 1.1 encoding and version 1.3 code compatibility. After you have created the class files, you must re-encode them for the Java Card. To do this, use the converter available in our SDK. You will also need some ID applications (most literally for one minute), an API export directory, and so on. These files should be understandable by the OS of the phone, so they are made in the .jar format.

We also developed a special Makefiles program that is available on the site . The converter issues a CAP file, which is a Zip archive of CAP components (Java Card code).
One of the important questions that needed to be answered before starting work on the project was how to interact with the SIM card. We needed a card reader. They are of two types: for connection to the PCSC port (PC / Smart Card API) and connected to the serial port Serial. The first ones are usually universal, so you need to have an adapter for working with a standard-sized SIM card, and the second ones are much smaller and are used specifically for SIM cards.

Functionally, there is no difference between them, but the PCSC version is more convenient to use. It uses official software designed specifically for the API and facilitating work with the computer. In addition, there are many open applications for working with SIM cards, which are easier to use with the PCSC option. All card readers are the same, so I used the cheapest SCR3500 bought on eBay for $ 8.
So, we wrote this awful looking code, then processed it with a Java compiler and converted it into a CAP file. Then we tried to place it on the SIM card, for which we used the popular GPShell Tool, but we did not succeed. The seller of SIM-cards advised us another program with a simple and convenient interface, which could not be found anywhere, and then promised us to sell it for $ 600, although he did not have this program either.
Therefore, we used a program called SIM Alliance Loader, the slide below shows its window. We used the first version of this program, but the second version is now available. SIM Alliance is a group that develops software for working with SIM cards. The SIM Alliance Loader program is an adaptation of Java applications for Windows and is intended for experts who understand what they are doing.

But if you understand the question, transferring the application to the SIM card will take just a couple of minutes. However, given that we had about a thousand cards that we wanted to prepare for Tourcamp, this recording technology would take too much time, so we decided to use something more productive. Therefore, we turned to the Global Platform - the standard for downloading, installing and managing applications on the Java Card. Depending on the application, this software allows the use of protocols and commands, as well as encryption and authentication. It also allows you to perform some external procedures without a SIM card, for example, to verify the binary codes of our applets.

In the process, it turned out that all applications are loaded and are authorized in the Issuer Security Domain (ISD) application - the Global Platform authentication system. In practice, this means that you cannot load an application onto a map if you have not developed it yourself, but there are exceptions described in the work of Karsten Knowl.
On pure Global Platform SIM cards, the ISD application is available by default, but our cards are much more difficult to access because the GSM application is installed by default on them and there is not even an opportunity to access the Global Platform application. I will briefly describe the procedure for installing our application on a SIM card.
The process consists of two stages: the DOWNLOAD command (loading an array of binary codes) and the SETUP command (creating an instance of the application on the SIM card). Single CAP components are combined together and sent to the map in blocks using the LOAD command. There are three types of Application ID (AID) involved in this process:
- AID of the application associated with the boot file;
- modular AIDs associated with the main card class;
- Single AIDs used when selecting a particular parameter.
As a result, the CAP-file is unarchived, data is extracted and recorded on the SIM card. The only way to “communicate” the Global Platform application with our SIM card is through the air transfer mechanism, that is, via SMS messages. In fact, we did not send traditional SMS, but simply generated commands on the map using SMS packages.
It was a long and rather time-consuming process. For the GSM 03.48 standard, it consisted in using the CAT shell (AoC2), which allows us to perform the necessary actions with the card. At the first stage of the process, it includes the SMS PP (D1) download, which, in turn, consists of the identification of the device and the SMS TPDU transport data packet.

SMS TPDU includes user header and data. User data also includes a header, a batch of commands, a subtitle (security settings, application selection). It, in turn, uses a TAR ID of 3 bytes in size (I wonder how PowerPoint withstood such nonsense). At this, the internal data limit is exhausted, and at the very end of the list there is the very APDU that our Global Platform needs. Thus, this entire cumbersome mechanism serves to send a tiny array of data.
In case you do not want to do this, there is one more mechanism for remotely sending the APDU to the SIM card. It requires the use of cellular communication to send SMS with installation commands, which requires network authentication. However, Carsten Knowle describes a method when encryption errors allow you to extract the keys of a symmetric DES encryption algorithm using the brute-force method, that is, without network authentication.
The Shadysim boot script is written in Python and runs on OSX, Linux and Windows. The next slide shows how it looks. Downloading is performed using a PC to which a SIM card card reader is connected.

The next slide shows the parameters that must be set to install the application on the map.

Here you can set the main class of the card, reserve physical and operational memory, determine the size of the text menu that will be displayed on the smartphone screen, record the command to launch the Toolkit, and so on. You can enter any more parameters using hex-code. Finally, a list of applications is entered with the - t parameter, which allows you to update the phone book.

How do we know that our application works? Eric will tell you about this.
The next slide shows what a running application looks like. The screen of the screen with the Python program is shown on the left, the iPhone settings menu with the SIM Applications item and the icon of our program on the Android Applications tab are shown in the middle.

Karl told you how hard programming was, but testing was no easier. In order to check whether our program works, it was necessary to do the following:
- turn off the phone;
- remove the SIM card, and it is better to remove the battery;
- insert a SIM card into the card reader;
- upload new code;
- pull the card out of the card reader;
- insert it back into the phone and insert the battery;
- wait until the phone boots;
- check the work code.
If the code does not work, the whole procedure must be repeated. How can you speed up and facilitate this procedure?
To do this, you can use the Android simulator for SIM cards. There is an open source SEEK, which is an SDK for Android. It includes patches for accessing a SIM card or SD card via a USB PCSC card reader and prevents the incompatibility of the SIM card from connecting to a computer and phone. You run the Android emulator on your computer and test your card without using a smartphone.
Can I use my smartphone as a card reader? Karl will answer this question.
The fact is that most radio interfaces do not allow direct communication with a SIM card. You can solve this problem using the Remote SIM Access Protocol. This method exists in Europe under the name "remote access to the SIM card via Bluetooth." This is a profile with built-in authentication. He needs to write an application that can send and receive APDUs. However, this method in some cases can turn your smartphone into a “brick”, so you should not install this profile on all smartphones in a row.
I want to introduce you to the future directions of our development. The STK kit is a great tool, but has limitations in use. Hence the question arises, is it possible to create an SMS botnet? After all, SIM cards are designed to communicate via a cellular network and do not need operating systems to exchange information, so it is possible to integrate them into a common network.
The integration of Android applications with SIM applets, for example, storing secure SSH private keys for authorization on a SIM card and secure operations with BitCoin e-currency, also opens up wide opportunities. We have an idea to use Android applications for OTA technology - “software update over the air”, using SMS packages for this.
Another direction is the improvement of the functions of NFS, Eric will tell you about it.

For example, using the single-wire SWP protocol, it will be possible to establish a direct connection between the SIM card and the NFS controller. This means that your SIM card will be able to work without the help of the phone’s operating system directly, just as VISA or MasterCard bank cards work.
The SIM card can work as a security element or be used in ISIS mobile payment systems. This is an American system that is being introduced very slowly, it combines mobile banking and Telcos mobile communications, and our idea may be useful for them.
The sim card can also be used to regain lost control of the mobile app store. The use of SIM cards as a security element is possible due to the following properties:

- today, the sim card processor is located inside most mobile devices running Android;
- The SIM card is usually part of the NFS controller;
- the security element uses the same technology as the sim card;
- SIM card can be used by Google Wallet e-wallet.
Therefore, I think that manufacturers of SIM cards should reflect on their potential capabilities and develop their functions in the areas described by us.
If you wish, you can download our application on the site , for its operation you will need certain devices with a cost of no more than $ 20, for example, a card reader. In the same place you can find slides of this presentation, scripts for applets, the Makefiles program for the Java Card, patches for the Android emulator and many more useful things.
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The Truth About VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
Source: https://habr.com/ru/post/352268/
All Articles