All according to GOST. Information security when using virtualization technologies
06/01/2017 GOST R 56938-2016 “Information Security. Information security when using virtualization technologies. General provisions. It so happened that the review of this GOST in the many innovations of the legislation was lost and now I would like to fill this gap.
This GOST was developed by the Federal Autonomous Institution "State Research Testing Institute for Problems of Technical Information Protection of the Federal Service for Technical and Export Control" (FAA "GNIII PTZI FSTEK of Russia") and introduced by the Technical Committee on Standardization "Information Protection" (TC 362).
Before the release of GOST R 56938-2016, recommendations of FSTEC No. 17 and No. 21 were applied to ensure the protection of virtualized environments. There is a section in these orders that describes the requirements for protecting the virtualization environment. Below is a table from the annex to the orders that lists these requirements.
Xi. Protecting the Virtualization Environment | |
ZSV.1 | Identification and authentication of access subjects and access objects in the virtual infrastructure, including administrators of virtualization management |
ZSV.2 | Controlling access of access subjects to access objects in a virtual infrastructure, including inside virtual machines |
ZSV.3 | Registration of security events in the virtual infrastructure |
ZSV.4 | Management (filtering, routing, connection control, unidirectional transmission) of information flows between components of the virtual infrastructure, as well as along the perimeter of the virtual infrastructure |
ZSV.5 | Trusted loading of virtualization servers, virtual machine (container), virtualization management servers |
ZSV.6 | Managing the movement of virtual machines (containers) and the data processed on them |
ZSV.7 | Monitoring the integrity of the virtual infrastructure and its configurations |
ZSV.8 | Data backup, backup hardware, software, virtual infrastructure, as well as communication channels within the virtual infrastructure |
ZSV.9 | Implementation and management of anti-virus protection in a virtual infrastructure |
ZSV.10 | Splitting the virtual infrastructure into segments (segmentation of the virtual infrastructure) for information processing by an individual user and / or a group of users |
')
Terms
GOST R 56938-2016 defines 2 types of hypervisors:
- Type 1 hypervisor is installed directly on the hardware platform, such hypervisors according to GOST include VMware vSphere , Hyper-V, Citrix XenServer, etc.
- Type 2 hypervisor is installed in the host operating system. These hypervisors include VirtualBox, VMWare Workstation, etc.
Also in the block of terms, the storage hypervisor is highlighted:
A program installed directly on the hardware as system software or in a host operating system environment as application software, acting as an intermediary between logical and physical address spaces to provide a high level of storage resource management.In the same term block, the GOST provides definitions of a virtual machine, what types of virtualization are, for what resources is virtualization, etc.
Previously, there were many questions about what is meant by virtualization. Now there are specific definitions of terms, and for any discrepancy, you can resort to GOST.
So, according to GOST,
A virtual infrastructure is a composition of hierarchically interconnected groups of virtual devices for processing, storing and / or transmitting data, as well as groups of hardware and / or software necessary for their operation.GOST defines three levels of hierarchy in a virtual infrastructure:
- at the first (lower) level of the hierarchy (equipment level), the hardware of the perimeter of the virtual infrastructure is located — the hardware used to implement virtualization technologies, including the hardware support of virtualization implemented in them;
- at the second level of the hierarchy (virtualization level), hypervisors and objects generated by them (virtual machines, virtual servers, virtual processors, virtual disks, virtual memory, virtual active and passive network equipment, virtual information protection, etc.) are located;
- At the third (top) level of the hierarchy (management level), there is a means for centralized management of hypervisors within one virtual infrastructure - the virtual infrastructure management console.
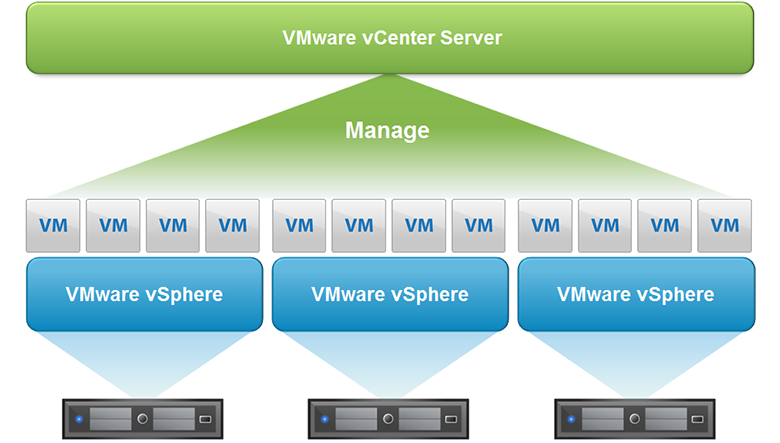
Three levels of hierarchy in the virtual infrastructure using the example of VMware technology stack
Objects of protection
GOST identifies the following main objects of protection when using virtualization technologies:
- means of creating and managing a virtual infrastructure (type I hypervisor, type II hypervisor, data storage system hypervisor, virtual infrastructure management console, etc.);
- virtual computing systems (virtual machines, virtual servers, etc.);
- virtual storage systems;
- virtual data transmission channels;
- separate virtual devices for processing, storing and transferring data (virtual processors, virtual disks, virtual memory, virtual active and passive network equipment, etc.);
- virtual information protection tools (GIS) and GIS tools intended for use in a virtualization environment;
- virtual infrastructure perimeter (central processors involved in the implementation of virtualization technologies and their cores, memory address space, network interfaces, ports for connecting external devices, etc.).
Security threats
GOST focuses on the fact that the use of virtualization technologies creates prerequisites for the emergence of security threats that are not characteristic of information systems built without the use of virtualization technologies. The threats that may additionally arise from the use of virtualization technologies are listed below.
GOST identifies 18 such threats:
- threats of attacks on active and / or passive virtual and / or physical network equipment from a physical and / or virtual network;
- threats to attack virtual transmission channels;
- threats of attack on the hypervisor from a virtual machine and / or physical network;
- threats of attacks on protected virtual devices from a virtual and / or physical network;
- threats of attacks on protected virtual machines from a virtual and / or physical network;
- threats of attacks on protected virtual machines from a virtual and / or physical network; (here in the published copies of the GOST there is a duplicated item, it may have made a mistake when typing)
- threats of attacks on storage systems from a virtual and / or physical network;
- threats of the process going beyond the virtual machine;
- threats of unauthorized access to data outside the reserved address space, including allocated for virtual hardware;
- threats of breaking user data isolation inside a virtual machine;
- the threat of violation of the procedure for authenticating subjects of virtual information interaction;
- threats to intercept control hypervisor;
- threats to intercept control of the virtualization environment;
- the threat of an uncontrolled growth in the number of virtual machines;
- the threat of an uncontrolled increase in the number of reserved computing resources;
- threats of violation of information processing technology by unauthorized changes in the images of virtual machines;
- threats of unauthorized access to protected information stored in the virtual space;
- threats of hypervisor update errors.
It is worth noting here that GOST considers threats related to the security of virtualization, other security threats do not lose relevance, and they also need to be considered when building a threat model, for example, threats related to physical access to the infrastructure, organizational issues of access to information, protection access details, etc. As we see from the list of threats, the virtualization environment introduces its own additional threats, which are not present at a lower hardware level.
Protection measures
In GOST only the list of protective measures is presented. ZI measures are divided into several groups depending on the object of protection. The following groups are distinguished:
- protection of the creation and management of virtual infrastructure;
- protection of virtual computing systems;
- protection of virtual storage systems;
- protection of virtual data transmission channels;
- protection of individual virtual devices for processing, storing and transferring data;
- protection of virtual information security tools and information security tools intended for use in a virtualization environment.
Summary data on threats and measures to protect information processed using virtualization technologies are summarized in a table and are given in Appendix B of this GOST.
In addition to traditional protection measures, there are also new ones, it is not yet clear what is being implemented. For example, encryption of the transmitted image files of virtual machines. To date, there are no encryption tools for virtual machine images transmitted from the cloud and uploaded to the cloud (for example, when “moving”). It is possible that this functionality will acquire the existing means of protecting virtualization, such as vGate or Dallas Lock.
It is also worth noting that neither the GOST nor the orders address the notion of snapshots of virtual machines (snapshots), and as a result, the threats related to the snapshots are not considered. For example, in the US NIST, a snapshot of a virtual machine is considered as a separate protection object.
Finally
Information protection systems created in pursuance of legislation, for example, according to the 17th Order considered in the previous article, require consideration of the entire list of possible threats. Based on this GOST, we can not reinvent the wheel when using virtualization technologies in our solutions. As spelled out in the 17th Order, the choice of protection measures consists of several steps:
- defining a base set of safeguards;
- adaptation of the basic set of protection measures;
- clarification of the adapted basic set of protection measures;
- addition of a refined adapted basic set of protection measures.
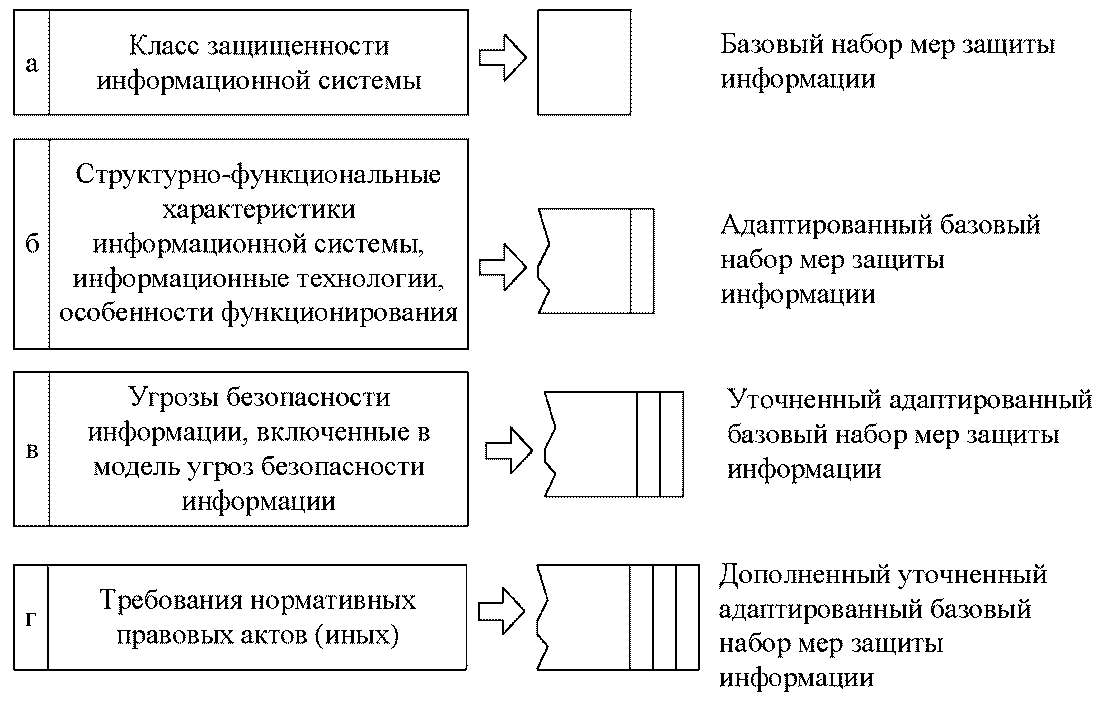
Thus, when using virtualization technologies, the addition of an updated adapted basic set of protection measures can be carried out with a clear conscience based on the requirements of GOST.
When using this GOST, it is necessary to keep in mind that there is a project that has not yet been approved, but already fully discussed, “Information security. Information security when using cloud technologies. General provisions. The project focuses specifically on the protection of information, when interacting with cloud providers. Therefore, it is necessary to understand the difference between the use of virtualization technologies and the consumption and / or provision of cloud services. The draft GOST is quite interesting, and, probably, we will consider its provisions in the following articles.
You can test our virtual infrastructure for free by leaving a request . Cloud4Y provides a cloud that complies with information security requirements in accordance with the 17 and 21 FSTEC Orders.
Source: https://habr.com/ru/post/352178/
All Articles