CTF is not hard [NQ2K18]

And the next qualifying online-stage of the annual cybersecurity competition, NeoQUEST-2018, was completed again.
What happened? Hmm ... It turned out that in Atlantis they also use Android, but the files are transferred in the old fashioned way: using Bluetooth, worry about transaction security and create distributed networks, hack competitors' websites and use information intelligence, and almost all computers work on the mysterious "QECOS" written in LUA, but with a lot of typos. How to survive here? Read under the cut.
“But there are already several WriteUps! Why else? ”You say, but this one is different from the others. Here we will look at some tasks from NQ18 on the part of a person who may not know anything at all about information security.
The file with the APK extension and Unity reference is presented to our attention. If we do not know what these "hieroglyphs" mean - use any search engine. It becomes clear thatTask # 1 - “Green Union”
Next we have several options. The first is my traditional one. The second is correct.
')
- Open "1.apk" in iDefense MAP Strings or SysInternals Strings . We know from past experience that the key will hardly be less than 32 characters. We are looking for all the suspicious and similar to the key. We find.
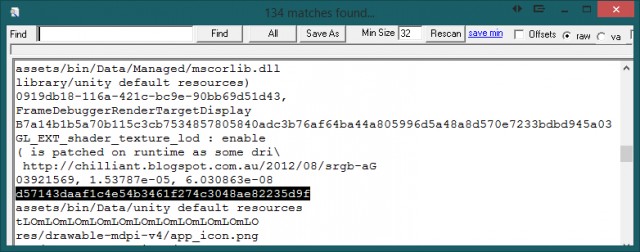
Unfortunately, nothing but the first key can be found this way. - We search on the Internet for something like “apk unpacker” and find - DevXUnity-Unpacker Magic Tools. We start. Open the file we need: "1.apk".

Furiously "poke" everything that moves.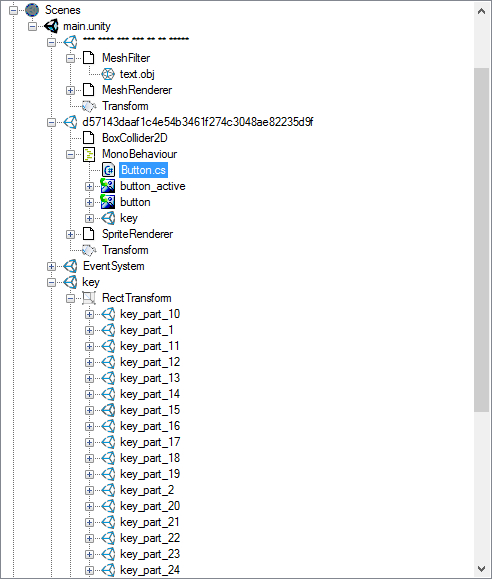
The first key is immediately apparent. We continue to study the file structure. Pay attention to the files: button.cs, key_part_N and the branch "*** ***".
The button.cs file contains the GetSequenceKey () function, consisting of an array of numbers, as well as the “text” variable (34 characters) of asterisks and points. It looks like an array is an ASCII code. Check: convert the height to hex !!!
We are politely asked to transfer heights to HEX. I wonder what heights talking about? Now it's time to watchTVon the button drawing:
Multicolored "steps" ... and how many? Exactly 34!
By any convenient method we measure height in pixels and translate to HEX. At the output we get the following array of values: ['68', '5b', '59', '00', '59', '58', '40', '44', '17', '58', '48 ',' 57 ',' 14 ',' 47 ',' 45 ',' 48 ',' 16 ',' 58 ',' 4f ',' 11 ',' 5c ',' 55 ',' 00 ', '5b', '49', '41', '40', '45', '0c', '0e', '11', '02', '00', '19']
Enter these values instead of “vertically arranged” in the function GetSequenceKey ()
Further on the function we see that these values will be gammed with a string in the variable "text". It seems that we have already seen these asterisks somewhere. Bingo!
Change the asterisks in the function to the found text. We rewrite everything, for example, in Python:#!/usr/bin/python2 text_ojb='You hold the key to my heart . . .' heigth=['68', '5b', '59', '00', '59', '58', '40', '44', '17', '58', '48', '57', '14', '47', '45', '48', '16', '58', '4f', '11', '5c', '55', '00', '5b', '49', '41', '40', '45', '0c', '0e', '11', '02', '00', '19'] heigth_int=[int(x,16) for x in heigth] array=heigth_int arg = '' for i in range(len(array)): arg += chr(array[i] ^ ord(text_ojb[i])) print(arg)
The result is: 14, 17, 7, 24, 16, 11, 3, 21, 1, 7
It looks like it's a sequence. Whom? What? And again, it's time to rememberwhat you did last summerabout the key_part_N found in the file resources. We collect the key (40 characters) from the received sequence and we are proud!
We were given a file and said something about Bluetooth. What does it mean? Open the text editor.Task # 2 - “Pair-Pair-Pair!”
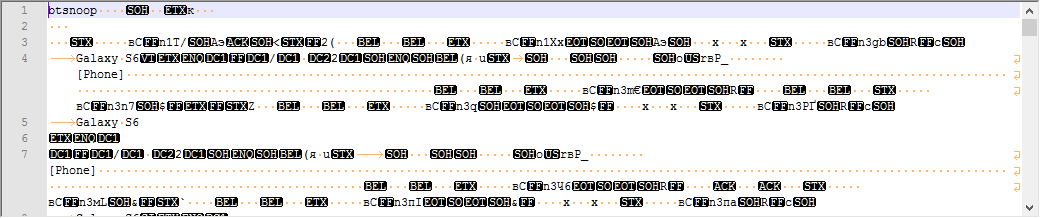
Nothing is clear. Some characters and phone models. Let's try to "google" the first available word - " btsnoop "
Yeah. This is a traffic dump of Bluetooth networking devices. You need to use the power of the earth again and find all the tools that can analyze network traffic. The most popular of these programs is Wireshark. Install. Open our file - 1513 network packets.
What to do next? RTFM and only hardcore!
After a little scrolling through the packages, you can see that there is an exchange between the Galaxy S6 (smartphone) and some device - ActionsS_32: 8f: a3 (TS007). Google again. Wireless headset.
We make an assumption that between the devices should go transfer the audio file.
Wireshark allows you to automatically track the queue of audio file transfer packets: Telephony -> RTP -> RTP Streams
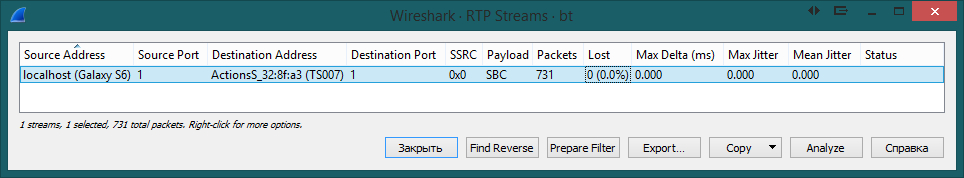
The program was able to identify and recognize the transfer of a single audio file. Click "Analyze", and then "Play Streams"
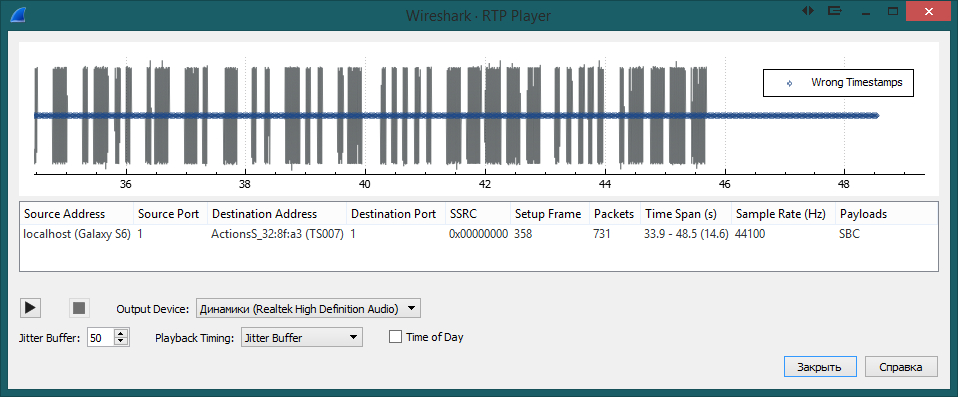
And here is our sound track. We listen, we realize the futility of life, we go either to learn Morse code, or directly from this window by ear we rewrite the signal in dots and dashes: "· - - · · ·· · - - · - ·· - ·· · - ···· · ––––– ····· · –––– ". We are looking for a Morse code decoding site. For example, this one . We get the word: "atlantida5051".
And it would seem that this is all, but no! We know that the key is 40 characters. We take from the key SHA1 - the task is completed!
The essence of this task is very well painted @Nokta_strigo . However, obtaining a second key is described by words that are too clever for the average person. And what are we? And we will do this task through ... Microsoft Excel 2016 and without programming (no, this is not a joke)Task # 4 - “Airship? Yeah! ”
First of all, open the NeoChat site database using DB Browser for SQLite :
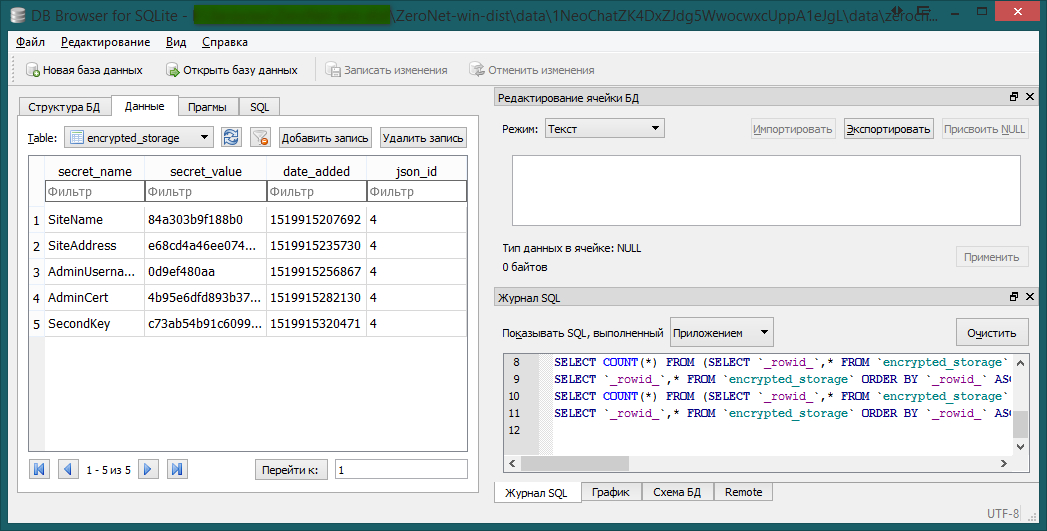
We see that in the table there are 5 encrypted records of different lengths. But how to restore them and get SecondKey?
We recall that in addition to this database, we also have a copy of all user profiles. The one we need (admin) has ID = 4 (look at the table)

And here is his folder where to look for data. Go to it and open the files "data.json" and "content.json". What we need of them:
"username": "admin" "address": "1NeoChatZK4DxZJdg5WwocwxcUppA1eJgL" "cert_user_id": "neochatadmin@zeroid.bit" So, now we can compare the table encrypted values and the original. But what is the encryption algorithm? The secret lies in the file "lfsr.js":
data[i] = data[i] ^ keystream[i] The link to the article about gammating is slightly higher in the text. Yes, here it is also.
This encryption algorithm is not cryptographic, which means that you can restore the keystream from the source and encrypted text:
keystream[i] = XOR(HEX([i]), HEX(_[i])) Recover keystream:
cac66cfa99e9c4 = XOR(84a303b9f188b0,4e656f43686174) <- SiteName 25f089bcb0f2c713f7936d7fc8b708ffcac66cfa99e9c4 = XOR(6e656f6368617461646d696e407a65726f69642e626974, 4b95e6dfd893b37293fe041188cd6d8da5af08d4fb80b0) <- AdminCert d7c2b1cb2d881566404f3e25f089bcb0f2c713f7936d7fc8b708ffcac66cfa99e9c4 = XOR(e68cd4a46ee074121a040a6188d3f6d495f24480fc0e08b0d45d8fba875d9fd38e88, 314e656f436861745a4b3444785a4a64673557776f637778635570704131654a674c) <- SiteAddress We see that the same keystream is used for all encryption operations (note that the same string is obtained if you look backwards at it).
To decrypt SecondKey you need another 72 characters, but where do you get them?
And now, my young Padawans, it is time for the fundamentals of cryptography.
LFSR - The linear feedback shift register ( LFSR ) - has several disadvantages. One of them is the ability to restore the chain by the method of correlation dissection, or by using the Berlekamp-Massey algorithm (hereinafter - ABM).
Here we have again two options for solving the problem:
- Flip keystream, as well as open and closed text, then restore the sequence using a polynomial, get the plaintext, and then turn the result again
- Restore the sequence from end to beginning, i.e. on the principle of "AS IS" (for perverts like me)
As you may have guessed, here I will describe exactly the second method. Launch the universal cryptanalysis tool - CrypTool . We use the module "Algorithm Berlekampa - Massey" from the tab "Cryptanalysis". We add the element “Text Input”, connecting it with the input of the module ABM, and for the output of the generator of the polynomial we add “Text Output”. We transform the received keystream (68 characters) into a binary form and enter it into the “Text Input”. Run the project.

At the output we get the polynomial of formation of the pseudo-random sequence of the RSLOS. Yes, he is so scary. Yes, we will work through Excel. No, there is no rope and soap.
Have you forgotten what we are doing? That's right - restoring the sequence of PSH
And now the highlight of this post is opening Microsoft Excel 2016 (starting with this version, the EXCLUDE () function has been added for several arguments).
Rewind the page somewhere to the "AAA" column. And in the line we place our keystream in binary form (bit by bit in each cell).
Now you need to understand - what is a polynom (which we got). A bit of theory:
The polynomial, in this case, is the key to the formation of a pseudo-random sequence. For example, if you have the sequence “010101” and you specify a polynom for it: then the next element of the sequence will always be generated using the formula: x [i] = x [i-3] ^ x [i-1]. After the first iteration, we will have: "0101010", after the second: "01010100", after the third: "010101001". Similarly, with us. Hey! Remove the scissors from the eyes.
In this example, I looked at the normal generation of the sequence “from beginning to end,” and we need the opposite. Let's go back to our Excel book.
Now, knowing what a polynom is, you need to slightly change it and write the formula for generating a PPCHP in the ZZ cell [1] (if the keystream starts with AAA [1]).
What is Excel advantage? The fact that here you do not need to think about how to change the formula, which indices will be relative to the generated element, because all cells have a relative address. All that is needed is to change the first and last arguments of the formula (in essence, swap). We get (in cell ZZ [1]):
=((AEV1;AEU1;AER1;AEP1;AEO1;AEN1;AEM1;AEL1;AEI1;AEH1;AEG1; AEC1;AEB1;AEA1;ADX1;ADW1;ADU1;ADT1;ADO1;ADK1;ADJ1;ADI1;ADH1;ADG1;ADE1;ADB1; ADA1;ACY1;ACR1;ACQ1;ACP1;ACN1;ACL1;ACK1;ACI1;ACH1;ACF1;ACE1;ABZ1;ABV1;ABU1; ABS1;ABP1;ABM1;ABL1;ABK1;ABF1;ABE1;ABD1;ABB1;ABA1;AAZ1;AAX1;AAV1;AAU1;AAS1;AAJ1; AAH1;AAF1;AAE1;AAB1;AAA1;AEX1);1;0) And now just take the corner of the cell and pull it [formula] to the left until, for example, cell AA [1].
Congratulations! You have restored the sequence.
We translate from the binary form to HEX and take the last 140 characters:
«847bf908c48a48cf4a4dd8b9d965d3867bc55e2aa33a56197228e1050ffb5157f21e4c1ad7c2b1cb2d881566404f3e25f089bcb0f2c713f7936d7fc8b708ffcac66cfa99e9c4»
Now we do the XOR (keystream, secondkey) and decode from HEX to the text view:
"CALCULATEMYSHA1suA1EeNRrIiIeGUopBSyVLU7juqgNaOmGLsTf2erZHfQ0VgB6CwxykY"
The string as if tells us that we need to get a SHA1 digest. The end.
Already in the briefing, they throw in a pair of abstruse words: accelerometer, RTTY, displacement, cup.Task # 6 - “Who is the engineer here?”
The file is formatted in two columns, the text: time and value.
By carefully searching, you can find out that some software for working with RTTY (for example, fldigi) allows you to play a recording of a broadcast from “WAV” files - the playback function. Maybe we need to make an audio file from a text file?
Again we use the search in the world wide web - they say that the well-known audio editor Audacity is able to do it.
We start. Select "Create" -> "Sample Data Import". Specify the path to the file. Error: Audacity does not understand this file structure. Well, I would also not immediately understand what they want from me.
Let's think: do we need time?
Re-import:
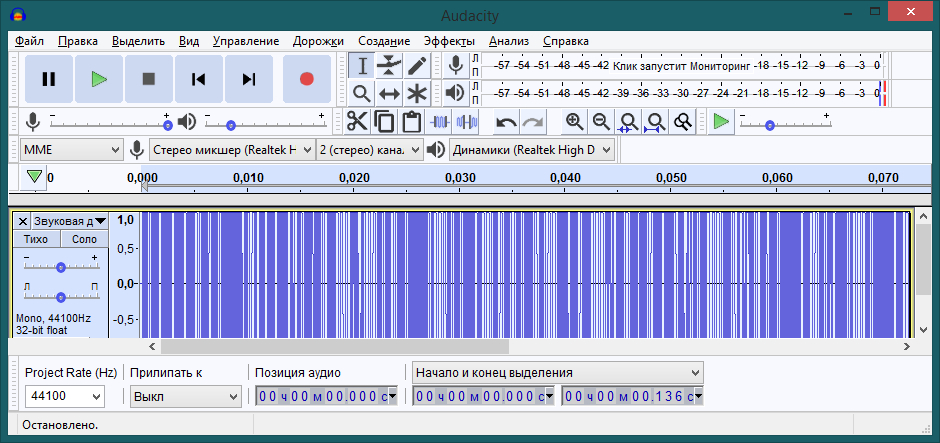
It is immediately noticeable that Audacity does not understand “raw data” beyond normalized (from -1 to 1) values.
The fastest and most effective solution is to divide each value in the file by the maximum. Any convenient ways to implement this (and even here Excel can help). And once again import:

Very beautiful ... Stop! Why does the whole file last 0.135 seconds? There seems to be about 10 seconds.
Once again select the entire audio track and select "Effects" -> "Speed change". Set the following values:
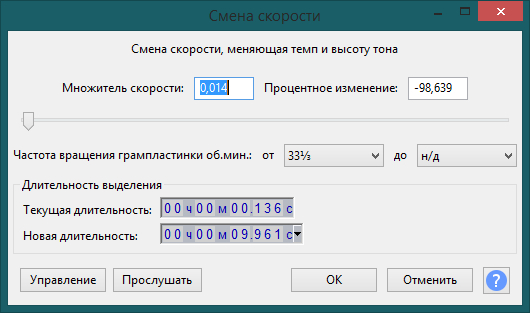
Now it is good! We export to an audio file with the extension "WAV".
Run fldigi: “Op Mode” -> “RTTY” -> “Custom”. We set the following settings in the "Tx" tab:
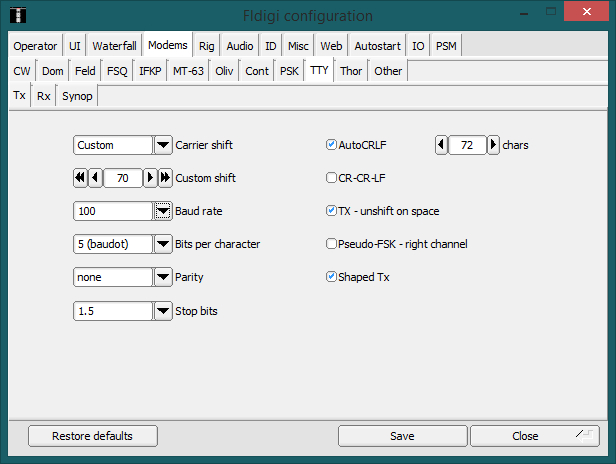
Save the settings and close the configuration window.
Select “File” -> “Audio” -> “Playback” and specify the path to the exported audio file “WAV”. The answer to the question of looping playback is affirmative. Configure the receiver and “catch the key”:
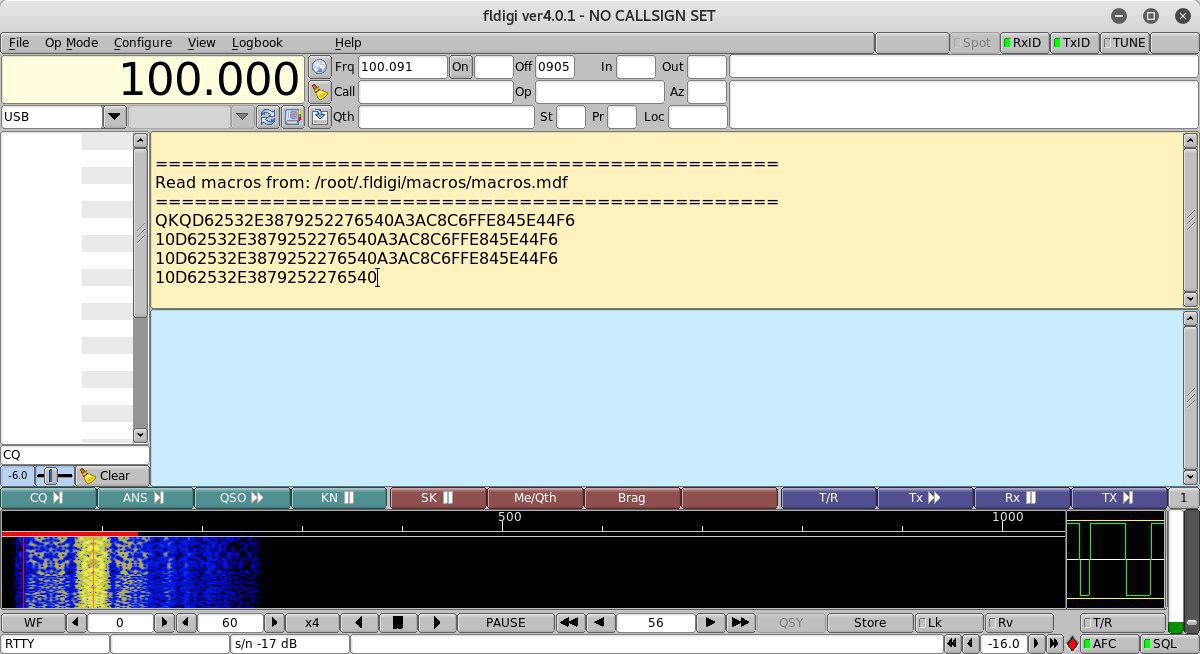
On this note, this WriteUp ends, but you should not be upset: there is still a lot of time to sharpen your skills to win the contests and the cybersecurity Olympiad, which (I am sure) will definitely be in the framework of MITSOBI.
Many thanks to the organizers and each of those who participated in the creation of NeoQUEST-2018.
See you at the "confrontation"
Source: https://habr.com/ru/post/352158/
All Articles