Hacking Team is back in business: ESET has discovered new spyware samples of the company
Since it was founded in 2003, the Italian cyber espionage software developer Hacking Team has gained fame by selling its products to governments and intelligence agencies around the world. The company's flagship capabilities, the Remote Control System (RCS), include extracting files from a target device, intercepting letters and messages, as well as remotely controlling a webcam and microphone.
ESET has found previously unknown RCS samples in 14 countries. The analysis of new samples allows us to conclude that the development of these software tools continues to the Hacking Team itself.

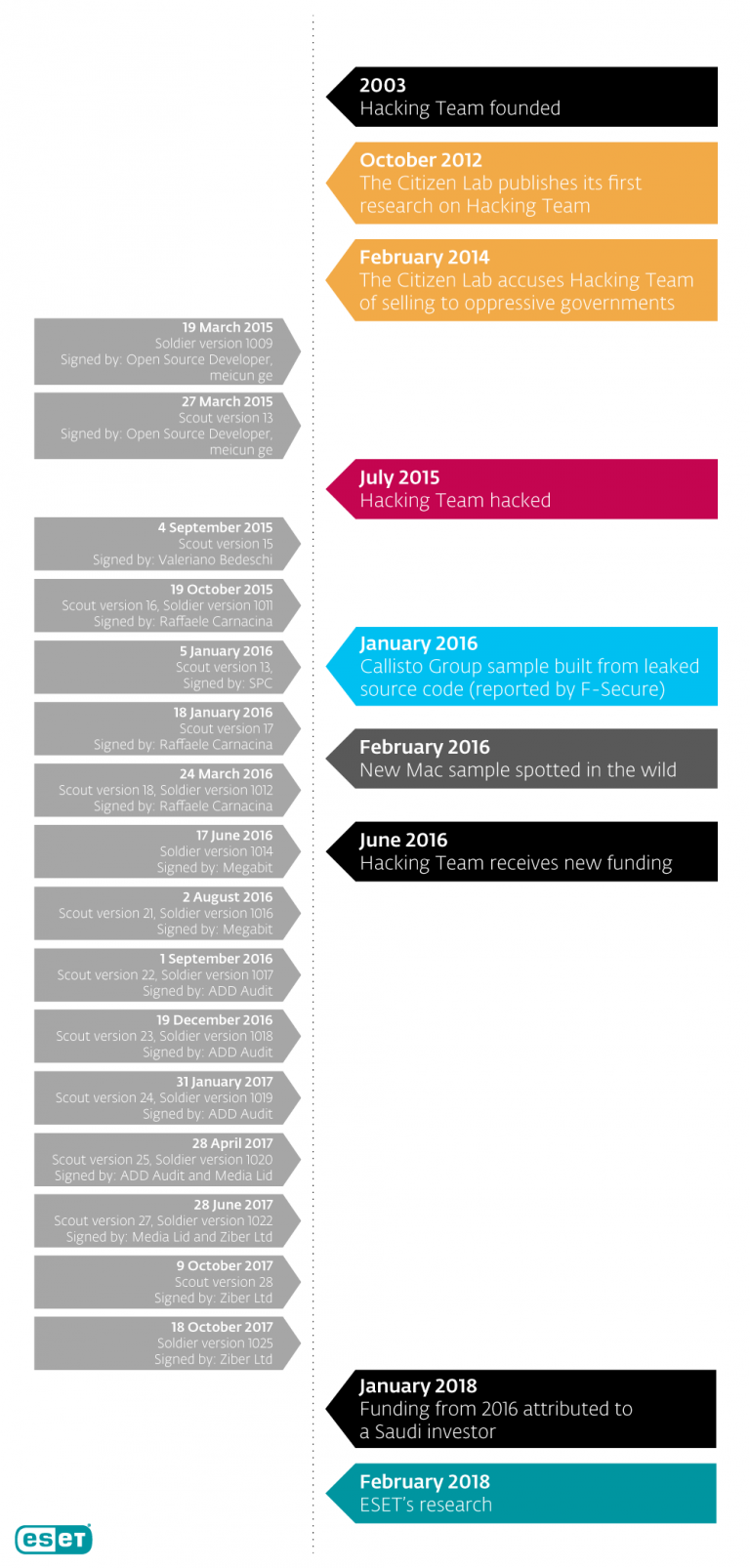
Hacking Team has repeatedly been criticized for selling spyware to authoritarian regimes , but it has always denied these allegations. The situation changed in July 2015, when the company became a victim of hacking and the facts of using RCS dictatorships were confirmed . After leaking 400 GB of data, including the customer list, employee correspondence, and spyware source code, the Hacking Team was forced to ask customers to stop using RCS and was in a state of uncertainty.
')
After hacking, the security community closely followed the company's attempts to get back on its feet. The first reports of new operations Hacking Team appeared six months later - a new sample of spyware for Mac, apparently used in practice. A year after the leak, Tablem Limited invested in the Hacking Team, which received 20% of the developer’s shares. Tablem Limited is officially registered in Cyprus, but there are indications of its connection with Saudi Arabia .
After completing the study of another spyware, FinFisher , we noted two interesting events related to the Hacking Team: a report on the financial recovery of the group and the opening of a new version of RCS with a valid digital certificate.
In the early stages of the study, our colleagues from Citizen Lab , who have been monitoring the activities of the Hacking Team for a long time, provided us with valuable material that enabled us to open a new version of spyware. Malware is currently used in practice and has a new digital certificate.
Further research revealed several more samples of the Hacking Team programs created after the 2015 hack, all of which are slightly modified compared to tools released before the source code was leaked.
Samples were compiled from September 2015 to October 2017. We consider compilation dates to be reliable, as ESET telemetry recorded practical use of samples a few weeks after compilation.
Further analysis led to the conclusion that the origin of all samples is reduced to one cyber group; these are not isolated versions of different developers using the Hacking Team source code merged into the Internet.
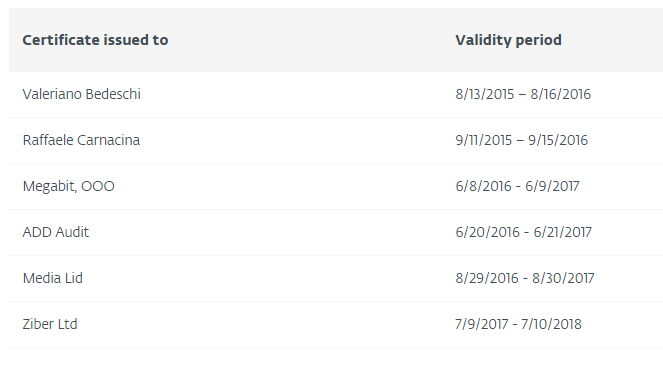
One of the arguments in favor of this point of view is the sequence of digital certificates that signed the samples. We found six different certificates issued one after another. Four of them were issued by Thawte certificate authority to four different companies, two - personal certificates in the name of Valeriano Bedeshi (co-founder of Hacking Team) and a certain Rafael Carnassin, as shown below:
Samples also contain fake manifest metadata to disguise as legitimate Advanced SystemCare 9 (9.3.0.1121), Toolwiz Care 3.1.0.0 and SlimDrivers (2.3.1.10).
Our analysis shows that the author (s) of the samples used VMProtect, apparently trying to make the samples less prone to detection. The method was used in the Hacking Team programs and before the leak.
By itself, the connection between these samples can point to almost any cyber group that modified the Hacking Team fusion source code or the installer, as was the case with the Callisto group in early 2016. However, we have collected other evidence that allows us to associate new samples with the developers of the Hacking Team themselves.
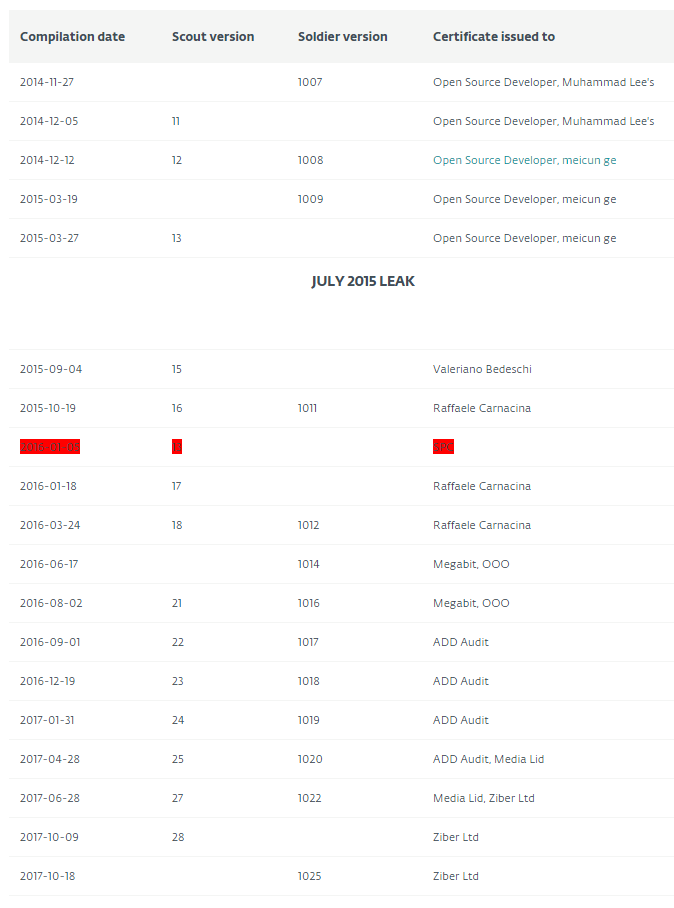
Versioning in new samples, access to which we received after overcoming VMProtect protection, begins before a leak, continues after it and follows the same patterns. It is typical for the developers of a company to compile the functional part of Malvari (called Scout and Soldier) consistently and often on the same day - this can be observed in new samples.
The table below shows the compilation dates, versions, and certificates of the Hacking Team spyware samples for Windows released from 2014 to 2017. Reuse of merged source code by the Callisto group is highlighted in red:
In addition, our research confirmed that the changes made after the leakage were made in accordance with the Hacking Team's own programming style and are often found in places that indicate a deep understanding of the code. It is unlikely that a player not from among the developers of the Hacking Team, who creates new versions based on the merged source code, could make changes to these particular fragments.
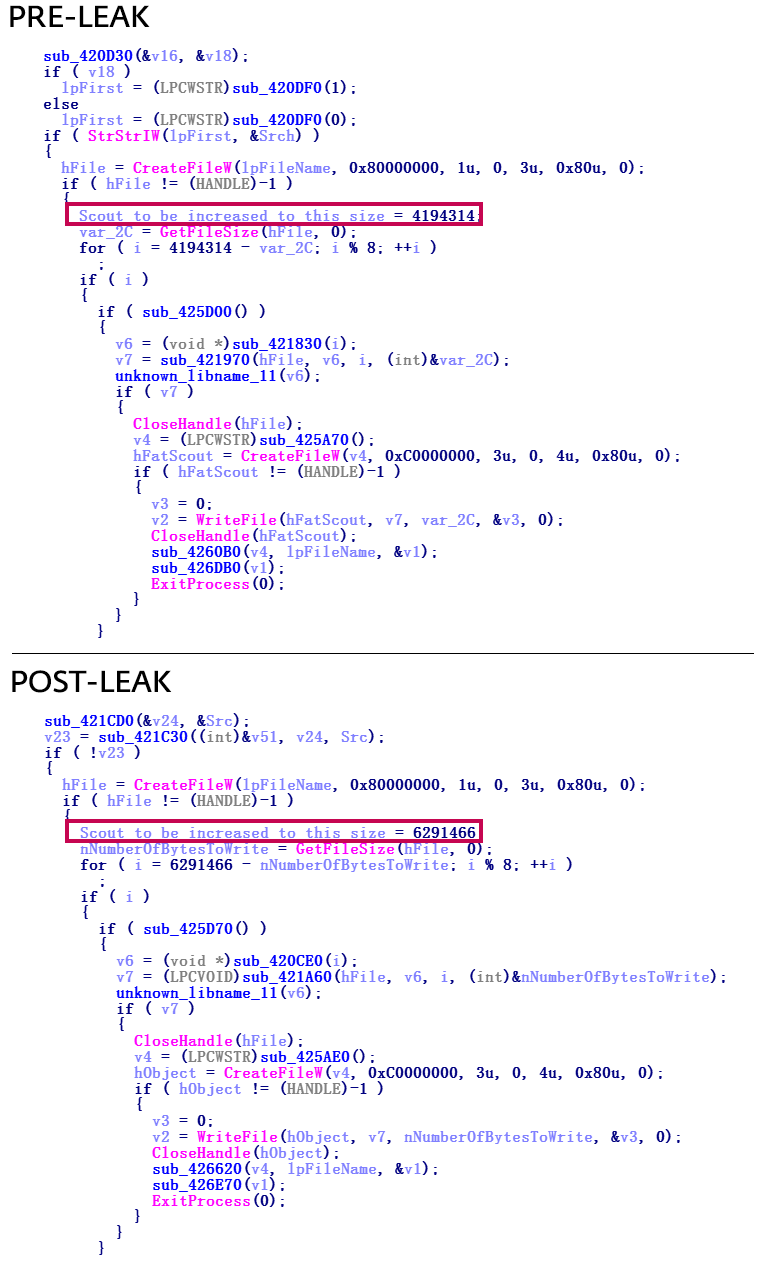
One of the differences between samples before and after a leak is the size of the autorun file. Before the leak, a copied file of about 4 MB was used. After the leak, the size was 6 MB - perhaps as a primitive method of protection against detection.
We found some other differences that completely convinced us of the participation of the Hacking Team. However, disclosing this data may interfere with further monitoring the activity of the group, so we cannot publish it. Ready to share information with other researchers, the request can be sent to threatintel@eset.com.
Spyware functionality largely corresponds to what was in the merged source code. Our analysis has not yet confirmed the release of any significant update that the Hacking Team promised after hacking.
At least two of the studied samples were distributed using phishing mailings. The malicious executable file was disguised as a PDF document using a double file extension. Names of bait documents are likely to target potential victims from among diplomatic mission staff.
Our research suggests that RCS spyware samples, in addition to one exception, are the result of the work of the Hacking Team, and not the reuse of code as in a case with the Callisto group in 2016.
At the time of this writing, our telemetry systems are detecting new Hacking Team spyware samples in 14 countries. We prefer not to name countries in order to prevent incorrect attribution, since the geolocation of detections does not always provide information about the source of the attack.
Detection by ESET products
Trojan.Win32 / CrisisHT.F
Trojan.Win32 / CrisisHT.H
Trojan.Win32 / CrisisHT.E
Trojan.Win32 / CrisisHT.L
Trojan.Win32 / CrisisHT.J
Trojan.Win32 / Agent.ZMW
Trojan.Win32 / Agent.ZMX
Trojan.Win32 / Agent.ZMY
Trojan.Win32 / Agent.ZMZ
Samples Signed by Ziber Ltd
Thumbprint: 14 56 d8 a0 0d 8b e9 63 e2 22 4d 84 5b 12 e5 08 4e a0 b7 07
Serial Number: 5e 15 20 5f 18 04 42 cc 6c 3c 0f 03 e1 a3 3d 9f
SHA-1
2eebf9d864bef5e08e2e8abd93561322de2ab33b
51506ed3392b9e59243312b0f798c898804913db
61eda4847845f49689ae582391cd1e6a216a8fa3
68ffd64b7534843ac2c66ed68f8b82a6ec81b3e8
6fd86649c6ca3d2a0653fd0da724bada9b6a6540
92439f659f14dac5b353b1684a4a4b848ecc70ef
a10ca5d8832bc2085592782bd140eb03cb31173a
a1c41f3dad59c9a1a126324a4612628fa174c45a
b7229303d71b500157fa668cece7411628d196e2
eede2e3fa512a0b1ac8230156256fc7d4386eb24
C & Cs
149.154.153.223
192.243.101.125
180.235.133.23
192.243.101.124
95.110.167.74
149.154.153.223
Samples signed by ADD Audit
Thumbprint: 3e 19 ad 16 4d c1 03 37 53 26 36 c3 7c a4 c5 97 64 6f bc c8
Serial Number: 4c 8e 3b 16 13 f7 35 42 f7 10 6f 27 20 94 eb 23
SHA-1
341dbcb6d17a3bc7fa813367414b023309eb69c4
86fad7c362a45097823220b77dcc30fb5671d6d4
9dfc7e78892a9f18d2d15adbfa52cda379ddd963
e8f6b7d10b90ad64f976c3bfb4c822cb1a3c34b2
C & Cs
188.166.244.225
45.33.108.172
178.79.186.40
95.110.167.74
173.236.149.166
Samples signed by Media Lid
Thumbprint: 17 f3 b5 e1 aa 0b 95 21 a8 94 9b 1c 69 a2 25 32 f2 b2 e1 f5
Serial Number: 2c e2 bd 0a d3 cf de 9e a7 3e ec 7c a3 04 00 da
SHA-1
27f4287e1a5348714a308e9175fb9486d95815a2
71a68c6140d066ca016efa9087d71f141e9e2806
dc817f86c1282382a1c21f64700b79fcd064ae5c
SHA-1
27f4287e1a5348714a308e9175fb9486d95815a2
71a68c6140d066ca016efa9087d71f141e9e2806
dc817f86c1282382a1c21f64700b79fcd064ae5c
C & Cs
188.226.170.222
173.236.149.166
Samples signed by Megabit, OOO
Thumbprint: 6d e3 a1 9d 00 1f 02 24 c1 c3 8b de fa 74 6f f2 3a aa 43 75
Serial Number: 0f bc 30 db 12 7a 53 6c 34 d7 a0 fa 81 b4 81 93
SHA-1
508f935344d95ffe9e7aedff726264a9b500b854
7cc213a26f8df47ddd252365fadbb9cca611be20
98a98bbb488b6a6737b12344b7db1acf0b92932a
cd29b37272f8222e19089205975ac7798aac7487
d21fe0171f662268ca87d4e142aedfbe6026680b
5BF1742D540F08A187B571C3BF2AEB64F141C4AB
854600B2E42BD45ACEA9A9114747864BE002BF0B
C & Cs
95.110.167.74
188.226.170.222
173.236.149.166
46.165.236.62
Samples signed by Rafael Karnasina
Thumbprint: 8a 85 4f 99 2a 5f 20 53 07 f8 2d 45 93 89 af da 86 de 6c 41
Serial Number: 08 44 8b d6 ee 91 05 ae 31 22 8e a5 fe 49 6f 63
SHA-1
4ac42c9a479b34302e1199762459b5e775eec037
2059e2a90744611c7764c3b1c7dcf673bb36f7ab
b5fb3147b43b5fe66da4c50463037c638e99fb41
9cd2ff4157e4028c58cef9372d3bb99b8f2077ec
b23046f40fbc931b364888a7bc426b56b186d60e
cc209f9456f0a2c5a17e2823bdb1654789fcadc8
99c978219fe49e55441e11db0d1df4bda932e021
e85c2eab4c9eea8d0c99e58199f313ca4e1d1735
141d126d41f1a779dca69dd09640aa125afed15a
C & Cs
199.175.54.209
199.175.54.228
95.110.167.74
Samples Signed by Valeriano Bedeshi
Thumbprint: 44 a0 f7 f5 39 fc 0c 8b f6 7b cd b7 db 44 e4 f1 4c 68 80 d0
Serial Number: 02 f1 75 66 ef 56 8d c0 6c 9a 37 9e a2 f4 fa ea
SHA-1
baa53ddba627f2c38b26298d348ca2e1a31be52e
5690a51384661602cd796e53229872ff87ab8aa4
aa2a408fcaa5c86d2972150fc8dd3ad3422f807a
83503513a76f82c8718fad763f63fcd349b8b7fc
C & Cs
172.16.1.206 is the internal address found in the samples.
ESET has found previously unknown RCS samples in 14 countries. The analysis of new samples allows us to conclude that the development of these software tools continues to the Hacking Team itself.

From Hacking Team to Hacked Team
Hacking Team has repeatedly been criticized for selling spyware to authoritarian regimes , but it has always denied these allegations. The situation changed in July 2015, when the company became a victim of hacking and the facts of using RCS dictatorships were confirmed . After leaking 400 GB of data, including the customer list, employee correspondence, and spyware source code, the Hacking Team was forced to ask customers to stop using RCS and was in a state of uncertainty.
')
After hacking, the security community closely followed the company's attempts to get back on its feet. The first reports of new operations Hacking Team appeared six months later - a new sample of spyware for Mac, apparently used in practice. A year after the leak, Tablem Limited invested in the Hacking Team, which received 20% of the developer’s shares. Tablem Limited is officially registered in Cyprus, but there are indications of its connection with Saudi Arabia .
After completing the study of another spyware, FinFisher , we noted two interesting events related to the Hacking Team: a report on the financial recovery of the group and the opening of a new version of RCS with a valid digital certificate.
RCS: life goes on
In the early stages of the study, our colleagues from Citizen Lab , who have been monitoring the activities of the Hacking Team for a long time, provided us with valuable material that enabled us to open a new version of spyware. Malware is currently used in practice and has a new digital certificate.
Further research revealed several more samples of the Hacking Team programs created after the 2015 hack, all of which are slightly modified compared to tools released before the source code was leaked.
Samples were compiled from September 2015 to October 2017. We consider compilation dates to be reliable, as ESET telemetry recorded practical use of samples a few weeks after compilation.
Further analysis led to the conclusion that the origin of all samples is reduced to one cyber group; these are not isolated versions of different developers using the Hacking Team source code merged into the Internet.
One of the arguments in favor of this point of view is the sequence of digital certificates that signed the samples. We found six different certificates issued one after another. Four of them were issued by Thawte certificate authority to four different companies, two - personal certificates in the name of Valeriano Bedeshi (co-founder of Hacking Team) and a certain Rafael Carnassin, as shown below:

Samples also contain fake manifest metadata to disguise as legitimate Advanced SystemCare 9 (9.3.0.1121), Toolwiz Care 3.1.0.0 and SlimDrivers (2.3.1.10).
Our analysis shows that the author (s) of the samples used VMProtect, apparently trying to make the samples less prone to detection. The method was used in the Hacking Team programs and before the leak.
By itself, the connection between these samples can point to almost any cyber group that modified the Hacking Team fusion source code or the installer, as was the case with the Callisto group in early 2016. However, we have collected other evidence that allows us to associate new samples with the developers of the Hacking Team themselves.
Versioning in new samples, access to which we received after overcoming VMProtect protection, begins before a leak, continues after it and follows the same patterns. It is typical for the developers of a company to compile the functional part of Malvari (called Scout and Soldier) consistently and often on the same day - this can be observed in new samples.
The table below shows the compilation dates, versions, and certificates of the Hacking Team spyware samples for Windows released from 2014 to 2017. Reuse of merged source code by the Callisto group is highlighted in red:

In addition, our research confirmed that the changes made after the leakage were made in accordance with the Hacking Team's own programming style and are often found in places that indicate a deep understanding of the code. It is unlikely that a player not from among the developers of the Hacking Team, who creates new versions based on the merged source code, could make changes to these particular fragments.
One of the differences between samples before and after a leak is the size of the autorun file. Before the leak, a copied file of about 4 MB was used. After the leak, the size was 6 MB - perhaps as a primitive method of protection against detection.

We found some other differences that completely convinced us of the participation of the Hacking Team. However, disclosing this data may interfere with further monitoring the activity of the group, so we cannot publish it. Ready to share information with other researchers, the request can be sent to threatintel@eset.com.
Spyware functionality largely corresponds to what was in the merged source code. Our analysis has not yet confirmed the release of any significant update that the Hacking Team promised after hacking.
At least two of the studied samples were distributed using phishing mailings. The malicious executable file was disguised as a PDF document using a double file extension. Names of bait documents are likely to target potential victims from among diplomatic mission staff.

findings
Our research suggests that RCS spyware samples, in addition to one exception, are the result of the work of the Hacking Team, and not the reuse of code as in a case with the Callisto group in 2016.
At the time of this writing, our telemetry systems are detecting new Hacking Team spyware samples in 14 countries. We prefer not to name countries in order to prevent incorrect attribution, since the geolocation of detections does not always provide information about the source of the attack.
Indicators of compromise
Detection by ESET products
Trojan.Win32 / CrisisHT.F
Trojan.Win32 / CrisisHT.H
Trojan.Win32 / CrisisHT.E
Trojan.Win32 / CrisisHT.L
Trojan.Win32 / CrisisHT.J
Trojan.Win32 / Agent.ZMW
Trojan.Win32 / Agent.ZMX
Trojan.Win32 / Agent.ZMY
Trojan.Win32 / Agent.ZMZ
Samples Signed by Ziber Ltd
Thumbprint: 14 56 d8 a0 0d 8b e9 63 e2 22 4d 84 5b 12 e5 08 4e a0 b7 07
Serial Number: 5e 15 20 5f 18 04 42 cc 6c 3c 0f 03 e1 a3 3d 9f
SHA-1
2eebf9d864bef5e08e2e8abd93561322de2ab33b
51506ed3392b9e59243312b0f798c898804913db
61eda4847845f49689ae582391cd1e6a216a8fa3
68ffd64b7534843ac2c66ed68f8b82a6ec81b3e8
6fd86649c6ca3d2a0653fd0da724bada9b6a6540
92439f659f14dac5b353b1684a4a4b848ecc70ef
a10ca5d8832bc2085592782bd140eb03cb31173a
a1c41f3dad59c9a1a126324a4612628fa174c45a
b7229303d71b500157fa668cece7411628d196e2
eede2e3fa512a0b1ac8230156256fc7d4386eb24
C & Cs
149.154.153.223
192.243.101.125
180.235.133.23
192.243.101.124
95.110.167.74
149.154.153.223
Samples signed by ADD Audit
Thumbprint: 3e 19 ad 16 4d c1 03 37 53 26 36 c3 7c a4 c5 97 64 6f bc c8
Serial Number: 4c 8e 3b 16 13 f7 35 42 f7 10 6f 27 20 94 eb 23
SHA-1
341dbcb6d17a3bc7fa813367414b023309eb69c4
86fad7c362a45097823220b77dcc30fb5671d6d4
9dfc7e78892a9f18d2d15adbfa52cda379ddd963
e8f6b7d10b90ad64f976c3bfb4c822cb1a3c34b2
C & Cs
188.166.244.225
45.33.108.172
178.79.186.40
95.110.167.74
173.236.149.166
Samples signed by Media Lid
Thumbprint: 17 f3 b5 e1 aa 0b 95 21 a8 94 9b 1c 69 a2 25 32 f2 b2 e1 f5
Serial Number: 2c e2 bd 0a d3 cf de 9e a7 3e ec 7c a3 04 00 da
SHA-1
27f4287e1a5348714a308e9175fb9486d95815a2
71a68c6140d066ca016efa9087d71f141e9e2806
dc817f86c1282382a1c21f64700b79fcd064ae5c
SHA-1
27f4287e1a5348714a308e9175fb9486d95815a2
71a68c6140d066ca016efa9087d71f141e9e2806
dc817f86c1282382a1c21f64700b79fcd064ae5c
C & Cs
188.226.170.222
173.236.149.166
Samples signed by Megabit, OOO
Thumbprint: 6d e3 a1 9d 00 1f 02 24 c1 c3 8b de fa 74 6f f2 3a aa 43 75
Serial Number: 0f bc 30 db 12 7a 53 6c 34 d7 a0 fa 81 b4 81 93
SHA-1
508f935344d95ffe9e7aedff726264a9b500b854
7cc213a26f8df47ddd252365fadbb9cca611be20
98a98bbb488b6a6737b12344b7db1acf0b92932a
cd29b37272f8222e19089205975ac7798aac7487
d21fe0171f662268ca87d4e142aedfbe6026680b
5BF1742D540F08A187B571C3BF2AEB64F141C4AB
854600B2E42BD45ACEA9A9114747864BE002BF0B
C & Cs
95.110.167.74
188.226.170.222
173.236.149.166
46.165.236.62
Samples signed by Rafael Karnasina
Thumbprint: 8a 85 4f 99 2a 5f 20 53 07 f8 2d 45 93 89 af da 86 de 6c 41
Serial Number: 08 44 8b d6 ee 91 05 ae 31 22 8e a5 fe 49 6f 63
SHA-1
4ac42c9a479b34302e1199762459b5e775eec037
2059e2a90744611c7764c3b1c7dcf673bb36f7ab
b5fb3147b43b5fe66da4c50463037c638e99fb41
9cd2ff4157e4028c58cef9372d3bb99b8f2077ec
b23046f40fbc931b364888a7bc426b56b186d60e
cc209f9456f0a2c5a17e2823bdb1654789fcadc8
99c978219fe49e55441e11db0d1df4bda932e021
e85c2eab4c9eea8d0c99e58199f313ca4e1d1735
141d126d41f1a779dca69dd09640aa125afed15a
C & Cs
199.175.54.209
199.175.54.228
95.110.167.74
Samples Signed by Valeriano Bedeshi
Thumbprint: 44 a0 f7 f5 39 fc 0c 8b f6 7b cd b7 db 44 e4 f1 4c 68 80 d0
Serial Number: 02 f1 75 66 ef 56 8d c0 6c 9a 37 9e a2 f4 fa ea
SHA-1
baa53ddba627f2c38b26298d348ca2e1a31be52e
5690a51384661602cd796e53229872ff87ab8aa4
aa2a408fcaa5c86d2972150fc8dd3ad3422f807a
83503513a76f82c8718fad763f63fcd349b8b7fc
C & Cs
172.16.1.206 is the internal address found in the samples.
Source: https://habr.com/ru/post/352022/
All Articles