New life for XMPP. Making an instant messenger that fails to block

The idea to make an instant messenger independent of P2P corporations is not new, but the development of a new protocol and client applications for it is quite an expensive and long process. And what if you use the good old XMPP , in which everything has been thought out and filed long ago?
But this is not a real peer-to-peer, you say, for XMPP to work, you need your own server and domain. This is true, but we can start the server on a local host, and use a hidden service in the I2P virtual network to communicate with the servers of other users. Using I2P will save us from having to pay for a domain with hosting, as well as protect our communications from criminal online surveillance .
Thus, we get:
- Hybrid P2P messenger, which can be run on user devices, and on a full server.
- Features that other P2P messengers lack: offline messages, contact storage and history in the cloud, work of several clients with one account.
- Ready client applications for every taste.
- Due to the use of I2P, invulnerable for various * supervision (litter for mat).
Let's start the implementation ...
Installing I2P and creating a server tunnel
In this guide, we will use the lightweight C ++ client i2pd as an I2P router. Installation instructions are in the documentation .
After installation, we create a server I2P tunnel - this is the virtual address where our XMPP server will be available for the rest of the world. In the tunnels.conf file we add the following lines:
[prosody-s2s] type=server host=127.0.0.1 port=5269 inport=5269 keys=prosody.dat [prosody-c2s] type=server host=127.0.0.1 port=5222 inport=5222 keys=prosody.dat If you plan to use only on localhost, the prosody-c2s section can be not added. Restart i2pd to apply the settings. We are looking for the I2P address of the created tunnel in the web console http://127.0.0.1:7070/ on the I2P tunnels page.
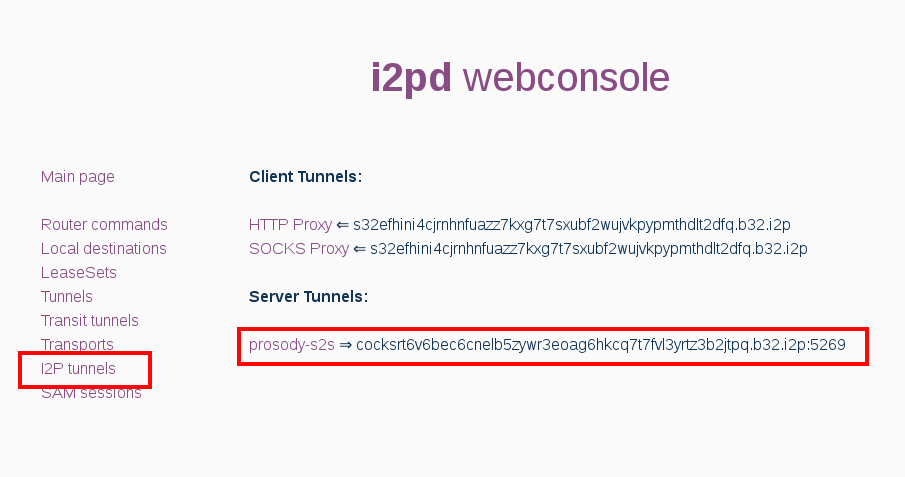
You can also find out the b32 address of the new tunnel by logging:
grep "New private keys file" /var/log/i2pd/i2pd.log | grep -Eo "([a-z0-9]+).b32.i2p" | tail -n1 Save this xxx.b32.i2p address, this will be the domain for your XMPP server.
Install and configure the XMPP server
We will use prosody as the XMPP server, it is the easiest and under it there is a ready-made module for working via I2P. The installation is described in the official documentation , in Ubuntu apt install prosody is done elementary.
For mod_darknet to work, mod_darknet need the mod_darknet lua library. If you have a lua version less than 5.2 (most likely), do apt install lua-bit32 .
Install the mod_darknet module. It is needed for prosody to make outgoing connections via Socks5 i2pd server. Download this file to the prosody modules directory, usually /usr/lib/prosody/modules .
Now we edit the config /etc/prosody/prosody.cfg.lua. Replace xxx.b32.i2p with your address:
interfaces = { "127.0.0.1" }; admins = { "admin@xxx.b32.i2p" }; modules_enabled = { "roster"; "saslauth"; "tls"; "dialback"; "disco"; "posix"; "private"; "vcard"; "ping"; "register"; "admin_adhoc"; "darknet"; }; modules_disabled = {}; allow_registration = false; darknet_only = true; c2s_require_encryption = true; s2s_secure_auth = false; authentication = "internal_plain"; -- On Debian/Ubuntu daemonize = true; pidfile = "/var/run/prosody/prosody.pid"; log = { error = "/var/log/prosody/prosody.err"; "*syslog"; } certificates = "certs"; VirtualHost "xxx.b32.i2p"; ssl = { key = "/etc/prosody/certs/xxx.b32.i2p.key"; certificate = "/etc/prosody/certs/xxx.b32.i2p.crt"; } The last step in setting up prosody is the generation of encryption certificates. In Nix, this is done like this:
openssl genrsa -out /etc/prosody/certs/xxx.b32.i2p.key 2048 openssl req -new -x509 -key /etc/prosody/certs/xxx.b32.i2p.key -out /etc/prosody/certs/xxx.b32.i2p.crt -days 3650 chown root:prosody /etc/prosody/certs/*.b32.i2p.{key,crt} chmod 640 /etc/prosody/certs/*.b32.i2p.{key,crt} Restart the prosody server to apply the settings.
Here you need a small digression. In an I2P network, any connections are encrypted with end-to-end encryption and, it would seem, additional encryption is unnecessary here. But, in practice, it turned out to be easier to generate keys than to try to configure all the programs to use plain text. You can try, but I warned you.
Creating accounts and connecting customers
Add admin account:
prosodyctl adduser admin@xxx.b32.i2p Now we are setting up an XMPP client (for example, Pidgin ).
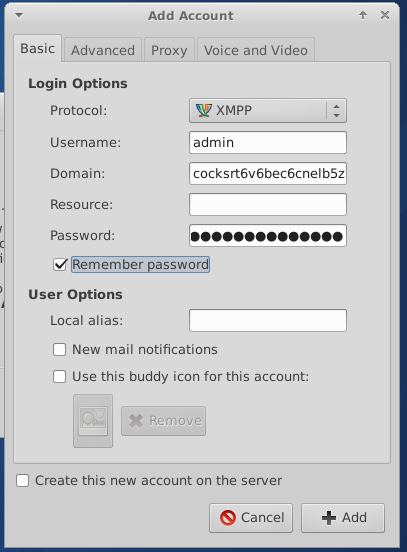
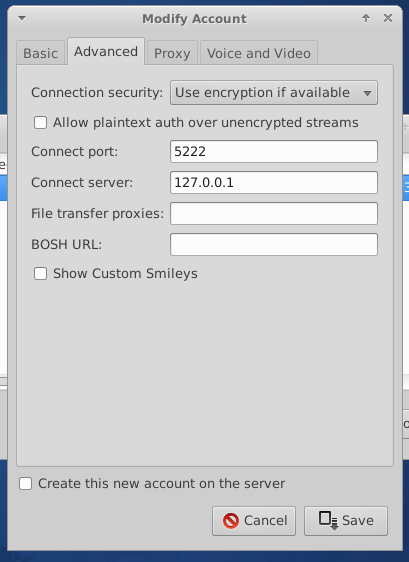
If you are connecting to a local host, then in the client settings we specify the connection to the server 127.0.0.1 port 5222.
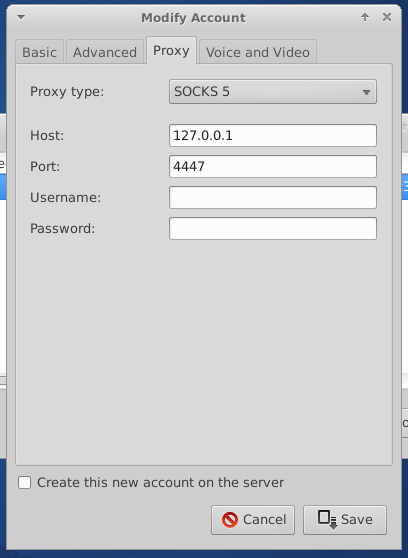
If you connect to the server remotely via I2P, then specify in the proxy settings Socks5 127.0.0.1:4447.
If everything is done correctly, you can add other users to I2P federation and correspond with them. It is also possible to set up your already working server on the regular Internet for correspondence with servers inside I2P. To do this, all other users will have to add prosody mapping for your domain to their config. For example, this is how I did it to communicate with the i2p.rocks server:
darknet_map = { ["i2p.rocks"] = "ynkz7ebfkllljitiodcq52pa7fgqziomz4wa7tv4qiqldghpx4uq.b32.i2p"; ["muc.i2p.rocks"] = "ynkz7ebfkllljitiodcq52pa7fgqziomz4wa7tv4qiqldghpx4uq.b32.i2p"; } That's all. Happy chatting!
')
Source: https://habr.com/ru/post/351936/
All Articles