Koteyki against the Black Lord: statistics online NeoQUEST-2018

From March 5 to March 16, the online cybersecurity competition NeoQUEST-2018 took place. Under the cut, we will tell you in detail about the tasks (but not all, some will go as separate write-ups) and the statistics of their progress, as well as why the participants filled the NeoQUEST team with
Grand total
The online stage included 11 tasks that, according to legend, contained parts of the key to the treasures of the mysterious Atlantis! No one managed to get all the keys - the second key to task # 11 “Cat Fur Grows” remained unconquered!

The first place was taken by mityada , gaining 1527 points and receiving all the keys, except for the ill-fated key number 2 from task 11! "Silver" got the bay , collecting the same keys, but slightly losing in time, its result - 1508 points. "Bronze" was at hackzard - all tasks, except the 11th, and 1429 points!
Congratulations guys! The fight for the 1st place was very tense, it happened that during the day the leader took turns 3 times. The top three are waiting for cool gifts, and all those who have completed at least one task completely - souvenirs from the NeoQUEST team!
')
Details about the tasks and Maaalen Easter Bunny!
The site with the tasks will be available for some time, so there is still a chance to understand them!
Task number 1 - "Green Association"
I see green - I understand that we are talking about Android!
Participants were provided with an APK file, which is an application developed using the Unity3D framework. In the main window of the application there is a button that, when clicked, shows 2 random bytes.
When decompiling an application and browsing the \ assets \ bin \ Data directory, packaged assets for Unity were found, they can be viewed using the Unity Assets Bundle Extractor program:

Careful examination of the directories allowed detecting one GameObject named e4e623ca0e06d69d7d63a7daae5fb27f - does it look like a key? So this is it! This easy first key was given to as many as 112 participants.
Also in this assembly were located different textures, each of which depicted 2 bytes, named from 1 to 24. Apparently, this is nothing but part of the flag! These textures, using the same program, can (and should!) Have been imported into the png format. Now it is necessary to understand whether all parts are used in the second flag, and in what order?
To do this, we decompile C # build \ assets \ bin \ Data \ Managed \ Assembly-CSharp.dll. After careful analysis, we see the GetSeqKey function, which is not called anywhere. Suspicious!
This function performs the XOR string and array, but at the same time, in the source code there are no valid values for the rows and array.
But in the array there is a hint "what's with the button?". If you look closely at the button, you can see a strange texture:
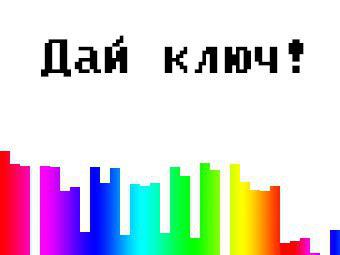
Gets the value of the height of each bar in px, this is our array of XOR (0x68, 0x5b, 0x59, 0x00, 0x59, 0x58, 0x40, 0x44, 0x17, 0x58, 0x48, 0x57, 0x14, 0x47, 0x45, 0x48, 0x16, 0x58, 0x4f, 0x11, 0x5c, 0x55, 0x00, 0x5b, 0x49, 0x41, 0x40, 0x45, 0xc, 0xe, 0x11, 0x2, 0x0, 0x19). But this is only part of the key!
To find the second part, carefully look at the package with assets and see a 3D object with the name text, import it in * .obj format and open, for example, in Photoshop. We see the text "You hold the key to my heart ...". To get the correct sequence, we make the XOR keys obtained and we get the sequence: 14, 17, 7, 24, 16, 11, 3, 21, 1, 7. It remains to extract all parts of the flag and assemble the whole, according to the received sequence!
The second key deal was more difficult: only 49 participants received it!
Task number 2 - "Pair-Pair-Pair!"
In this task, the participants were given an “input” file, which is a dump of Bluetooth traffic between the phone and the Bluetooth headset. In addition to service information, the traffic also contained audio data transmitted via the RTP / SBC protocol. Participants had to extract audio data, in which the word was encrypted using Morse code, SHA1 of which was the key!
78 participants successfully coped with this task!
Task number 3 - "Find Ihtiandra"
We love OSINT jobs, and we know that you love them too! Our member mr_umnik has already written a write-up on it, but only we have interesting details about this task! After all, who, if not you, dear participants, showed a violent imagination and loaded us so amazing photos that we even collected a collection!
All that was given in this task is the nickname andr_ihtiandr and a link to the “questionnaire” . Search VKontakte immediately gave the result ! From the profile photo was the name of the organization ( AtlanticNeoSecurity ) and a hint where to go next - to the “secure messenger”, that is, to Telegram!
Attempts to communicate with the user @andr_ihtiandr would lead to nothing, but in the profile photo there was a hint of the following social network: Ask.fm! From there it is possible to find out the name of the founder of the company where Ichthyander works: Nobody .
However, the VKontakte profile contained not only a hint of the Telegram, but also the phrase “And sometimes I write interesting things on text storage site =)”. And this is already a pointer to Pastebin, and indeed - there we also find Ihtiandra ! His profile contains one single entry , which, in fact, a picture in the format .jpg, encoded in Base64!
 The picture looked like this (here, the fantasy of the participants and bloomed with wild color). “Continue” referred to the further analysis of the picture, which (since it .jpg) also opened as a RAR-archive!
The picture looked like this (here, the fantasy of the participants and bloomed with wild color). “Continue” referred to the further analysis of the picture, which (since it .jpg) also opened as a RAR-archive!The contents of the archive (read more about this here ) consisted of a text file and a picture, opening which with a notebook or a HEX editor, the participants found a hint that this particular image would help them find the year the company was founded!
And indeed, a Google search for pictures gave results with the news about the remains of Atlantis found in 2009 !
All that remains is to get the key: download the file. And not just a file, but, as we specifically wrote in the onine-questionnaire , “a photo of the one who hid in an almost black and white picture”.
And it is necessary for such a thing to happen that the active mind of those passing the task tied the Black Ruler and the phrase “almost black and white” ... According to this logic - indeed, only a white slave could hide behind the Black Ruler!
As a result, the NeoQUEST team watched with horror as the number of half-naked men grew among the loaded photos! In addition to them, fortunately, there were abstract pictures, and even variations on the Ihtiandr theme! From a strange but decent we made a collage:

And only then, finally, seals began to appear! Yes, yes, they are! After all, on an almost black and white picture of VKontakte a yellow taxi was depicted, and the color letters were highlighted: “c” , “a” , “T” . Cat - that's whose photo we have been waiting for!
Cats also enjoyed variety, and we were not too lazy to make a selection of the most interesting ones:

When uploading the correct photo, participants received a key. 76 people coped with the task!
Task number 4 - "Airship? Yeah! ”
In this assignment, a distributed ZeroNet network was waiting for the participants, and for this assignment there is already a write-up from Nokta_strigo .
To get the first key, it was enough just to study the principles of ZeroNet. To get a second one, participants had to sweat, cracking a cipher based on a linear feedback shift register.
Task number 5 - "Torment the donkey!"
The input data for this task is the site address, which is a “technical support” page on which you can create an appeal and download a PDF file. After some time, the response received a message containing the first page of the downloaded PDF file and, at the very end, the phrase “Answered from Internet Explorer 11”. All of this hinted that the administrator opened the PDF in Internet Explorer 11.
To open a PDF in IE11, there is an Adobe Reader plugin, but so far this has not helped in finding the key. By carefully examining the page, it was possible to find the hidden menu item “GET KEY”, which redirected to the /setkey.php page.

In this form, only one element - user login. In different situations, different messages are issued, but when entering a valid username, the participant received the following message:
Apparently, it is necessary that this action is carried out by the administrator. How to do it?
Here came to the rescue vulnerability scanner (any) - when scanning the form it was found that it is not protected from CSRF ! Well, it remains only to prepare a special PDF-file.
One of the possible options is to write a POST request in the FormCalc language using the website address (213.170.100.210):
var b = Post("https://213/170.100.210/setkey.php", "login=test&setKey= ", "application/x-www-form-urlencoded")It seems to be true, but ... there is no key. Here it was necessary to remember that the site has an invalid SSL certificate! This is where a part of the tip “And to open your files, he has the Adobe plugin installed. It runs on the same server that hosts the web server. ” Watch Internet Explorer security settings - and for sure! Site localhost is secure. We change the site address 213.170.100.210 to localhost - and here it is, the key!
16 participants successfully coped with the task.
Task number 6 - "Who is the engineer here?"
The participants were given a log of the accelerometer of the smartphone, and according to the legend it was possible to find out about some message in the RTTY format and the RTTY coding parameters: carrier frequency - 100 Hz, 70 Hz offset.
After analyzing the accelerometer log, participants could see that the device acceleration values were measured only on one of the coordinate axes 600 times per second, and the acceleration readings look quite adequate: 0-60 m / s 2 .
The main idea of the task was that according to the available acceleration values you can calculate the location of the device, and many-many measurements of the location per unit of time - this is quite an audible sound track! Then - a matter of technology: remembering the basics of numerical integration, the participants had to calculate many pairs of “timestamp-location” and “overtake” the obtained data into a wav sound file. It remained only a little poshamanit with the amplitude of the sound and, strengthening the signal, decode the RTTY-message, which was the key!
Engineers were 29 participants.
Task number 7 - "Hellish reverser - my ampLUA!"
Task number 7 was devoted to finding and operating a use-after-free vulnerability, and besides, the task itself hinted at the use of the Lua language .
A detailed analysis of this task (and not only it!) Made GH0st3rs , write-up is available here ! Only four participants coped with the task!
Task number 8 - "Blockchain got even to Atlantis ..."
In this task, the participants were given a client to interact with a simple blockchain. To obtain the key, it was necessary to smaynit the block containing the nickname of the participant. But the standard mining algorithm was too slow! To increase speed, participants needed to find a vulnerability in the hash function that was used to test the blocks.
The task passed only 10 participants, and we will analyze it in more detail, wait for the write-up!
Assignments №9 - "QEMU + eCos = QECOS" and №10 - "Specter"
For these two tasks, the active GH0st3rs also managed to write a write-up! Read them on the link . Let us just say that task number 9 was devoted to working with the eCos operating system, which was unusual for many, it contained 2 keys, the first of which was received by only 5 participants, and the second - and even less: four participants!
The name of the task number 10 immediately said that Specter was not without a vulnerability ! NeoQUEST participants needed to extract the keys (as many as 3 pieces!) From a broken application, first finding errors in it and “fixing” it.
The first and third keys received 29 participants each, and the second was more difficult and was found only by 19 participants.
Task number 11 - "Cat Fur Grows"
With this unusual name, we strongly hinted to the participants that without circumventing the Windows protection mechanism called Control Flow Guard (CFG), this is not enough! In the task, it was necessary to find / naphazzit vulnerabilities and get ReadWrite primitive to bypass everything that is in the latest Windows - DEP , ASLR , CFG, etc.
The first of the two keys received only four participants, but the second key did not obey anyone. We will devote this task to a separate habrastatyu, because, in addition to being the most difficult, he had several options for passing!
Easter egg
A few days before the end of the competition, one of our developers decided to make a small surprise to the participants and came up with a small engineering easter egg. In the text of the legend, some characters were highlighted in bold:
Introduction - ON (for hours)
Task 1 - FW (contained), and (expedition)
Task 2 - ON (but we are all this)
Task 3 - CT (my status)
Task 5 - AR (they are not unarmed)
Task 6 - T (Smartphone)
Task 7 - 7 (from IP address)
Task 8 - P (chic), AZ (Analyz)
By putting all the characters together, the participants received the following phrase: "CLICK ON START 7 TIMES."

Yes, yes, at the very start that is under the airship!
After 7 clicks, the following page was opened:

To get the missing piece of the link, participants needed to find the pixel-by-pixel difference between the pictures. There are enough ways to do it, but the easiest one is to find an online tool, for example, this one , she found the following difference:

The phrase “W3Are1n1AMMn0W! 11” reflected the developer’s joyful emotions as his home department , Information Security of Computer Systems, SPbPU (one of the organizers of NeoQUEST!), Became part of the Institute of Applied Mathematics and Mechanics . Well, applicants, bachelors and graduate students - now you know where to find us! Moreover, the successful participation in NeoQUEST is taken into account when entering the department "IBKS"!
But enough of the lyrics, because Easter eggs have not yet been completed! Clicking on the link received, the participants received a new riddle:

Gears, formulas ... It is not clear. Although soon, looking closer, the participants understood that the upper formula is nothing but the ratio of the number of teeth on the largest gear to the number of teeth on the smallest! Now the whole difficulty was to correctly calculate the teeth (63 and 16, respectively), divide one by the other (3.9375), multiply by 10 4 and take SHA1 from the resulting value (6246a5c59e9cd5944ab1b196dcb9d950c2172254)!
46 participants passed Paschal, each received 10 points - the dynamic scale did not work for this task.
And now - statistics!
The competition was attended by 1253 people, at least one key received 167 participants. Changes in the tournament table - in our traditional gif:
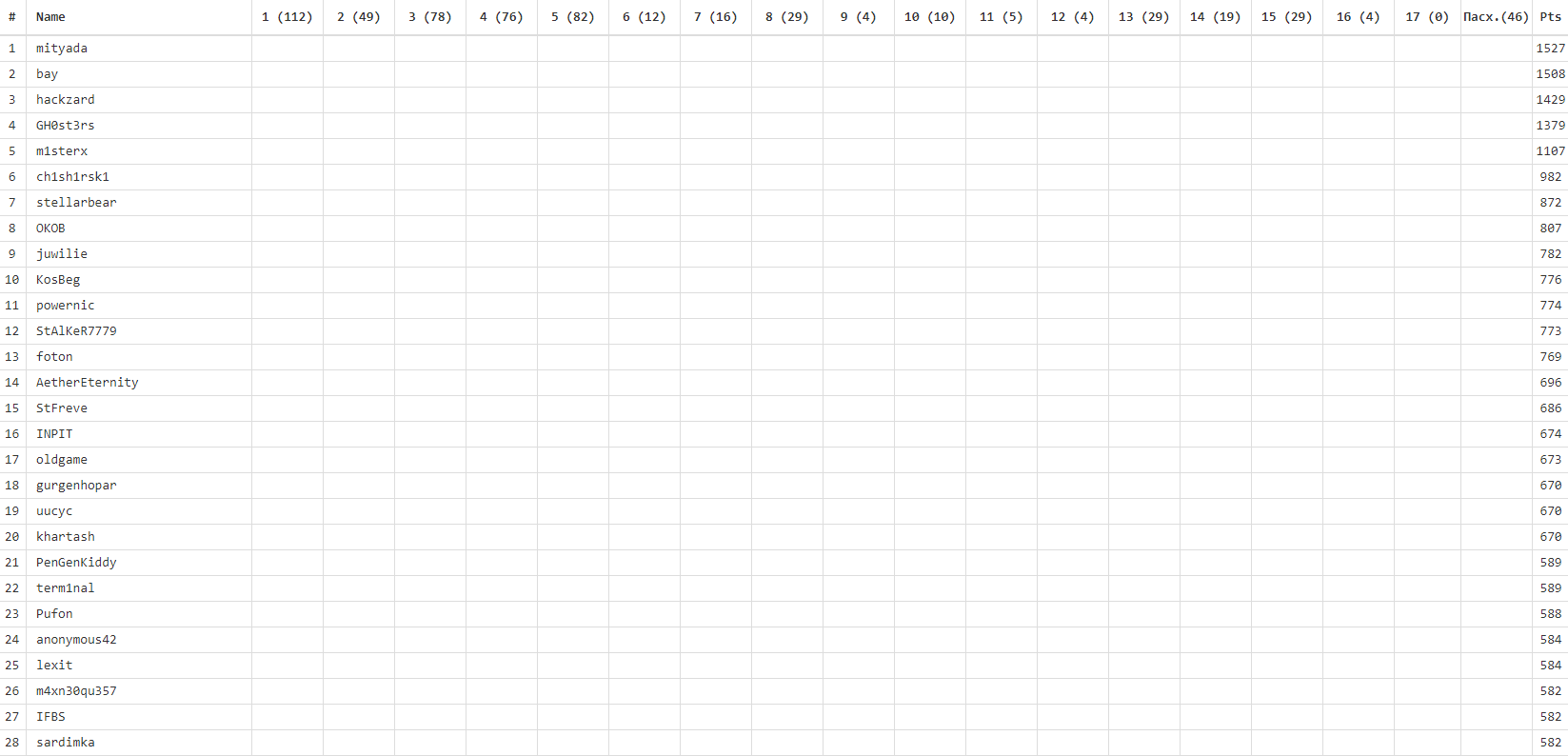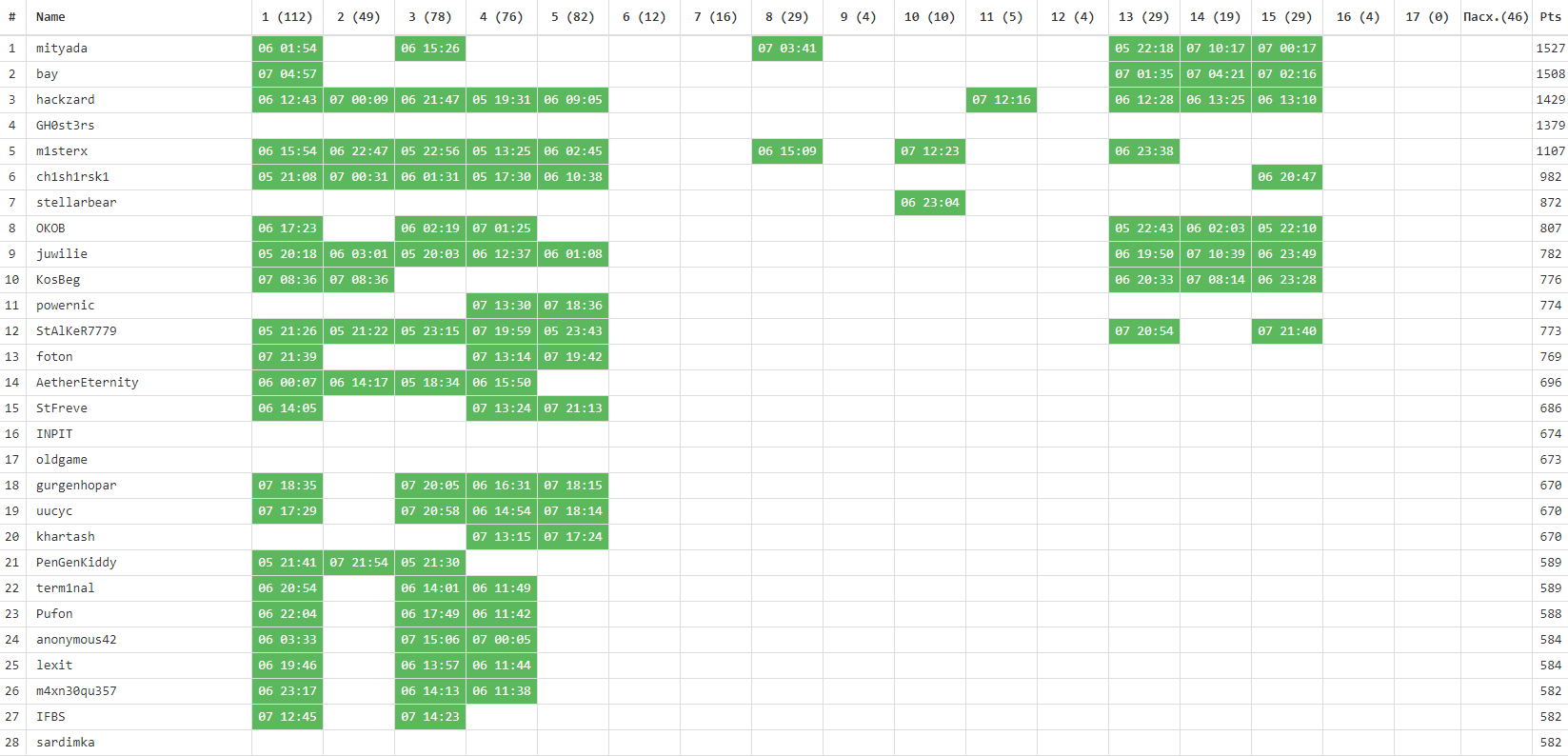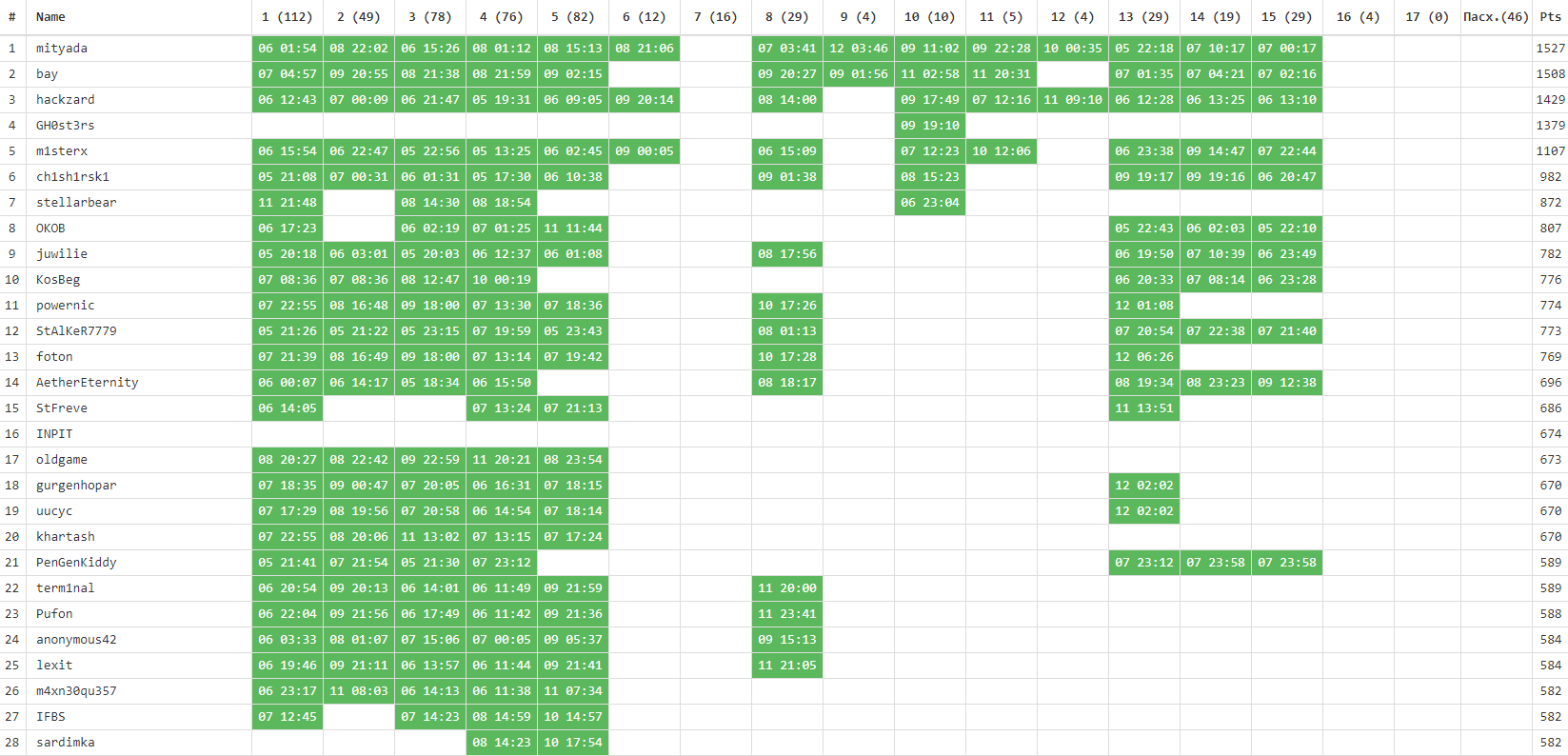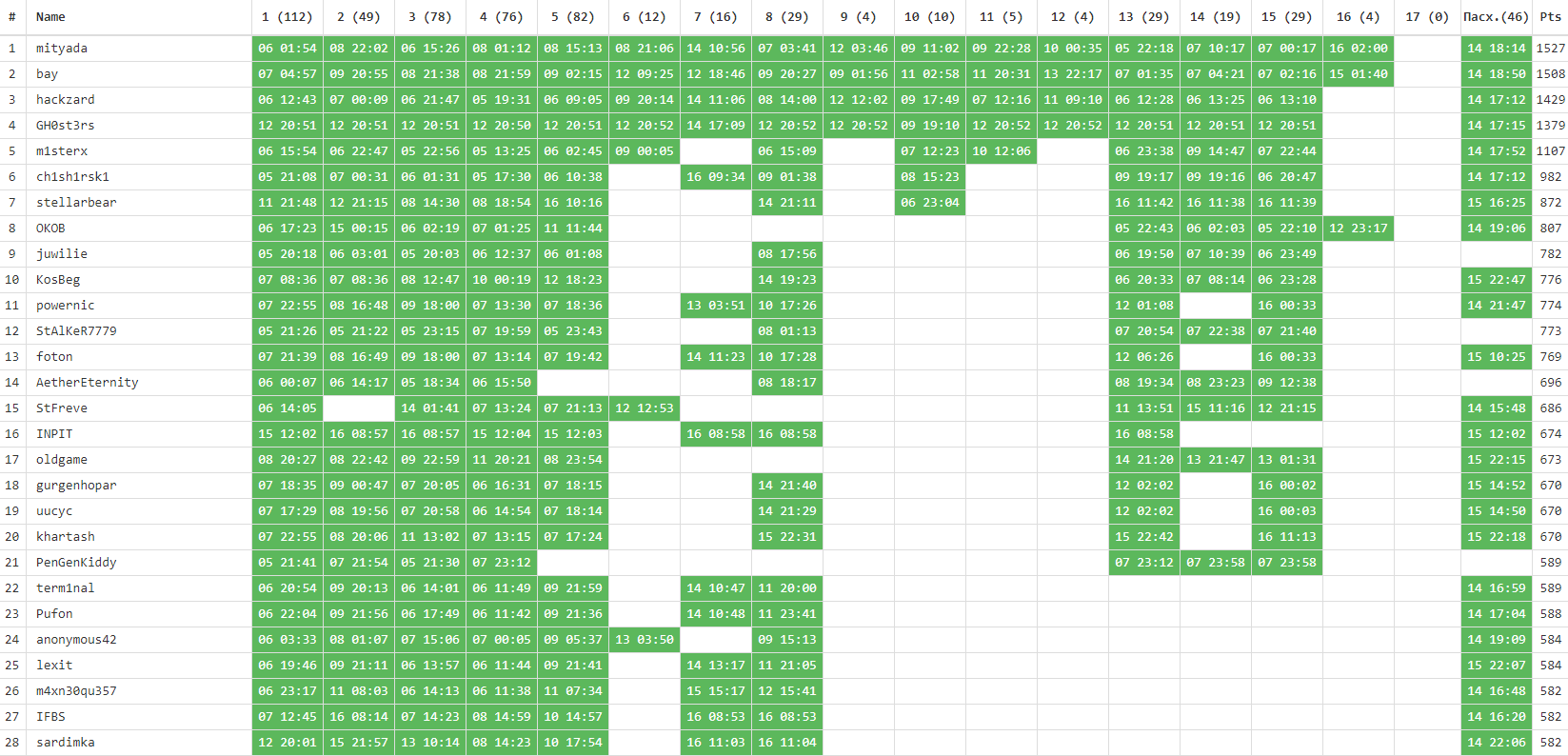
We also collected statistics on the complexity of the tasks (taking into account the number of participants who completed the task completely ):
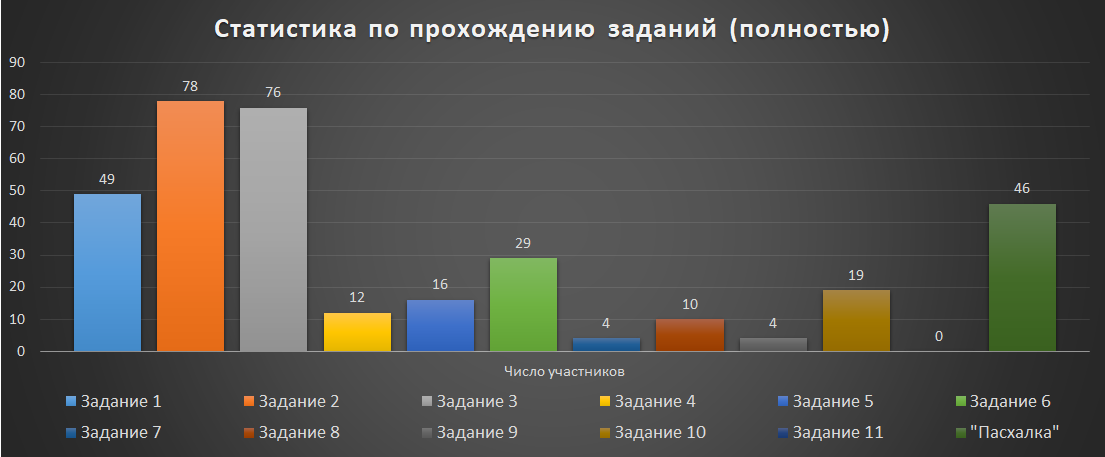
And yet - statistics on tasks with several keys! There were 5 of them in total:
- Task number 1, "Green Association" - 2 keys;
- Task number 4, "Airship? Aha! ”- 2 keys;
- Task number 9, "QEMU + eCos = QECOS" - 2 keys;
- Task number 10, "Specter" - 3 keys;
- Task number 11, "Cat Fur Grows" - 2 keys;
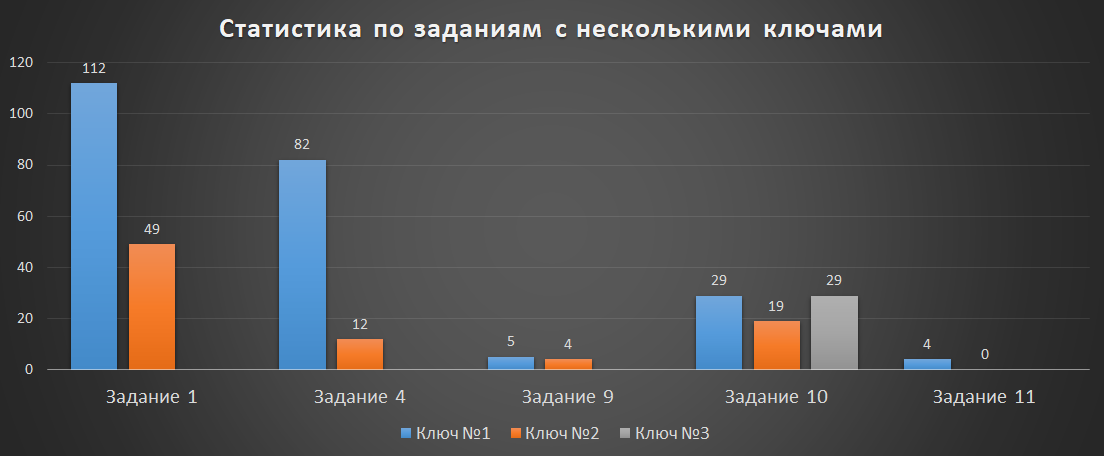
Over the entire period of the online stage NeoQUEST-2018, 594 keys were received! The easiest was the first key to the task with Android (№1, "Green Association").
Ahead - "confrontation"!
This year's "confrontation" will be held in St. Petersburg not in summer, but in autumn - at the end of September. However, this is not all the changes that await guests and participants!
We will leave the coolest and favorite: reports, workshops and demonstrations of attacks and add new! For the first time NeoQUEST will be held together with the scientific and technical conference "Methods and technical means of ensuring information security" ! The guests of NeoQUEST-2018 will learn a lot about the interrelation of science and cybersecurity practice, the importance of scientific research for the information security specialist and how modern information security mechanisms work from a scientific point of view!
At the same time, those who wish can take part not only in NeoQUEST, but also in the scientific sections of the conference! To learn more about participation with a report or a workshop at NeoQUEST, write to support@neoquest.ru, and learn more about the conference “Methods and technical means of information security” on the joint site , for all questions please contact mitsobi@neobit.ru.
Ahead - write-ups of several tasks and active preparation for the "confrontation rate"! By the way, the participants who have passed entirely at least one task - check your mail, we will soon start sending out!
Source: https://habr.com/ru/post/351524/
All Articles