Disruption of a large-scale hacker attack on Windows users in Russia
On March 6, Windows Defender blocked more than 80,000 copies of several sophisticated Trojans that used sophisticated methods of introducing malicious code into the address space of processes and equally sophisticated mechanisms for ensuring stability and evasion of detection. It was possible to reveal a new wave of infection attempts thanks to signals from behavioral analysis systems in combination with cloud models of machine learning.
The second part with a detailed description of the attack and ways of infection.

')
Trojans used in the attack were new versions of Dofoil (also known as Smoke Loader). They tried to infect devices with malware for mining cryptocurrency. In the next 12 hours, more than 400,000 cases of attack were recorded, of which 73% were in Russia, 18% in Turkey, and 4% in Ukraine.
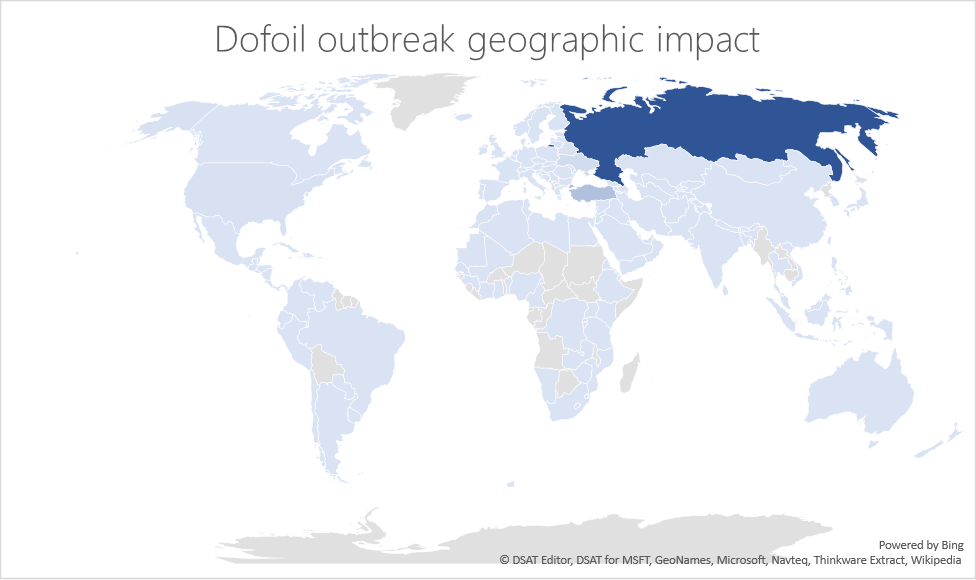
The geographical distribution of the components of the Dofoil attack.
At the very beginning of the attack with the help of behavioral monitoring, Windows Defender antivirus revealed an unusual mechanism of attack resistance and stability. Anti-Virus immediately sent the appropriate signal to our cloud protection service.
Windows 10, Windows 8.1 and Windows 7 users with Windows Defender or Microsoft Security Essentials antivirus software are fully protected from this malware outbreak.
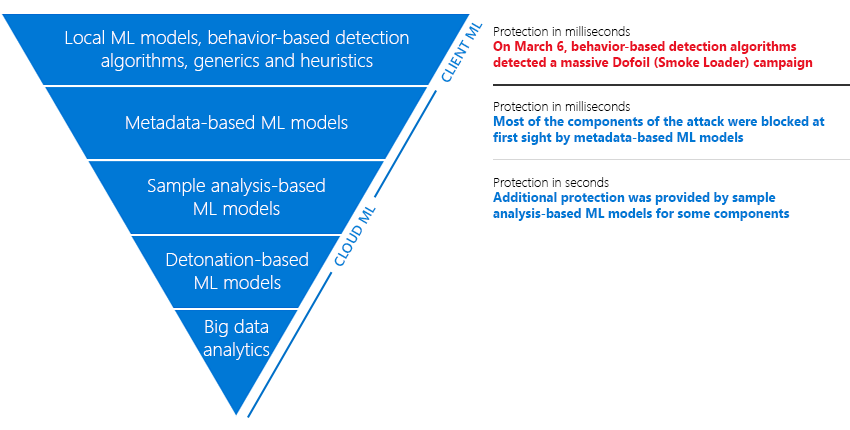
Multi-level protection system based on machine learning in the Windows Defender antivirus program
Artificial intelligence and the detection of threats based on behavioral analysis in Windows Defender form the basis of our protection system. A preemptive defense mechanism based on artificial intelligence was applied against this attack. This approach is similar to multi-level machine-based protection, which stopped the outbreak of an Emotet infection last month.
Dofoil is the latest family of malware that uses crypto-mining software in its attacks. The cost of bitcoin and other cryptocurrencies remains attractive, and attackers take advantage of the opening opportunities and embed mining components into attacks. For example, modern exploit kits contain not extortion programs, but tools for mining cryptocurrency. Mining scripts are being introduced into fraudulent technical support sites, and even mining functions are added to some of the banker Trojans.
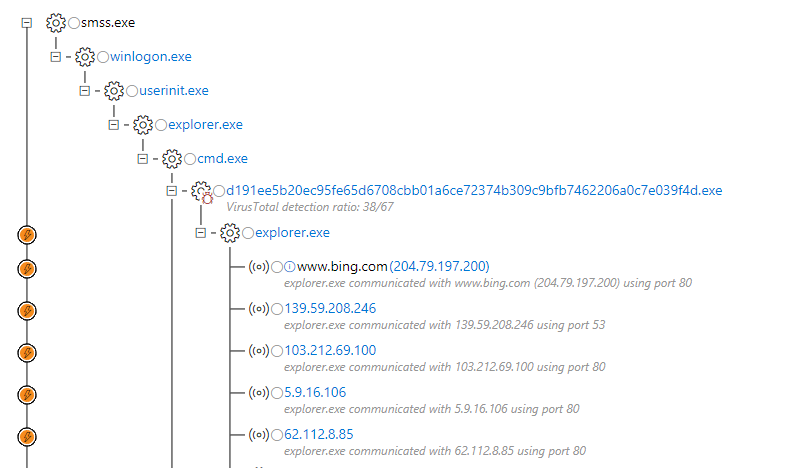
The starting point of the Dofoil campaign, which we discovered on March 6, was a Trojan that replaces the explorer.exe process. Process substitution is a code injection method that creates a new instance of a genuine process (in this case, c: \ windows \ syswow64 \ explorer.exe) and replaces its code with a malicious one.
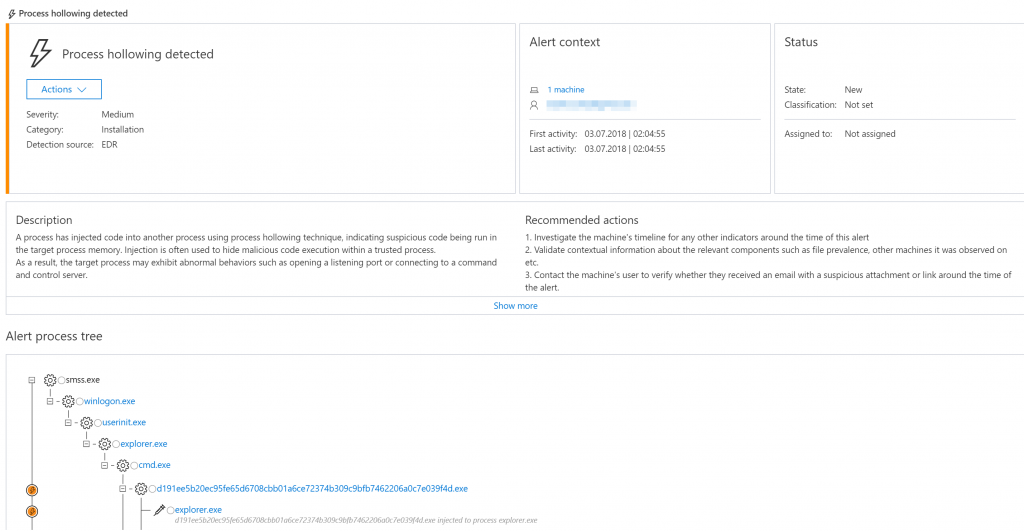
Windows Defender ATP process replacement detection (SHA-256: d191ee5b20ec95fe65d6708cbb01a6ce72374b309c9bfb7462206a0c7e039f4d, found by Windows Defender antivirus under the name TrojanDownloader: Win32 / Dofoil.AB)
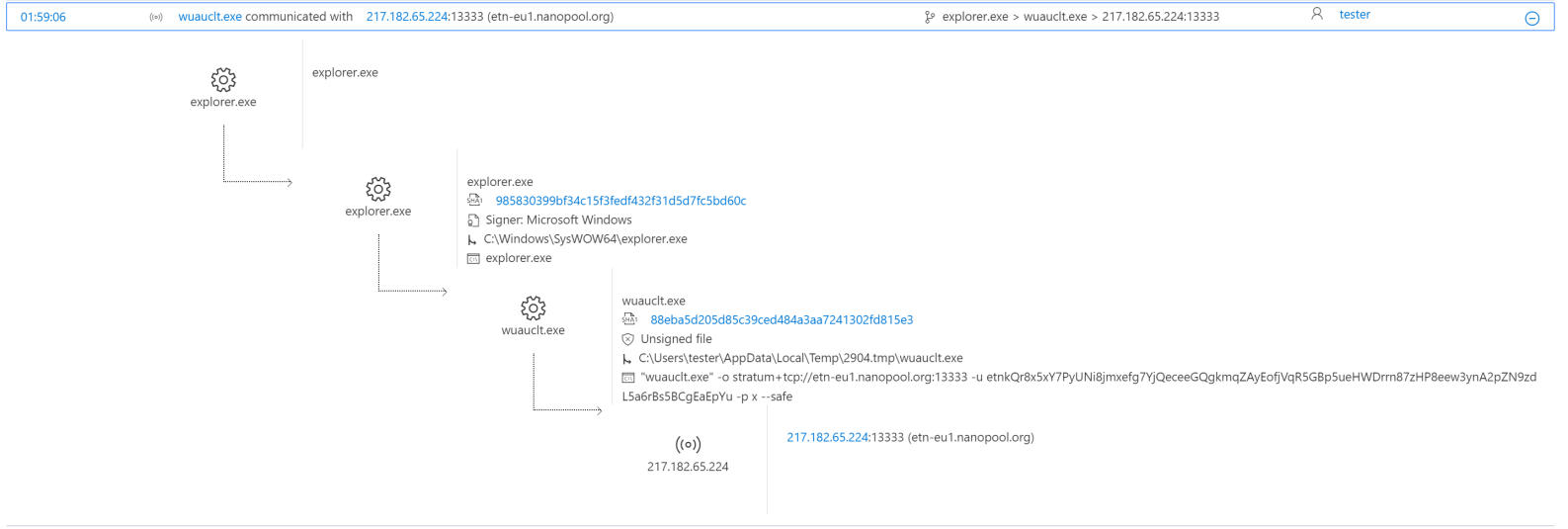
The bogus explorer.exe process then creates a second instance of the malicious code that runs the mining program that disguises as a safe Windows binary file, wuauclt.exe.
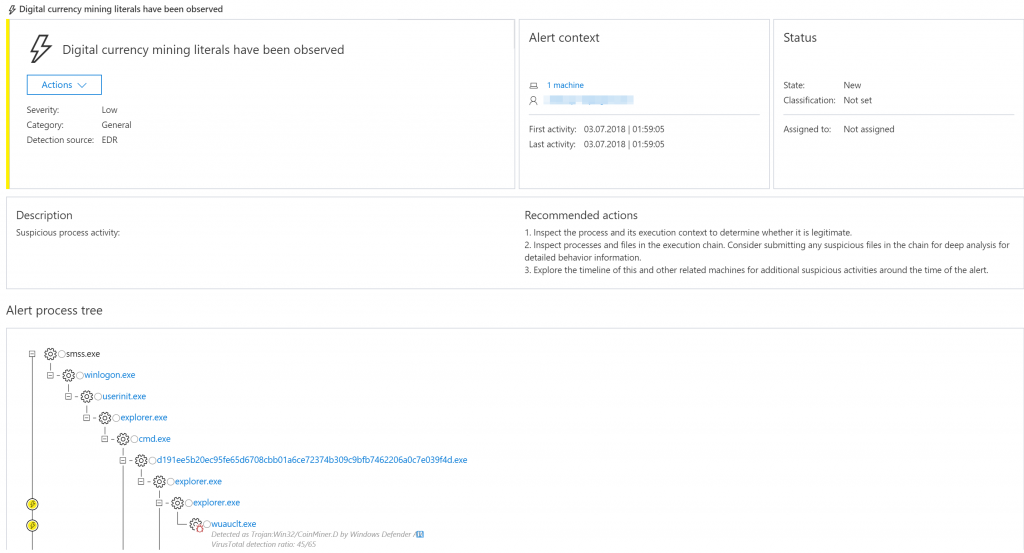
Detection of malware for mining cryptocurrency service Widows Defender ATP (SHA-256: 2b83c69cf32c5f8f43ec2895ec9ac730bf73e1b2f37e44a3cf8ce814fb51f120, detected by Windows Defender antivirus under the name Trojan for a challenge / challenge / challenge profile / wakew /.
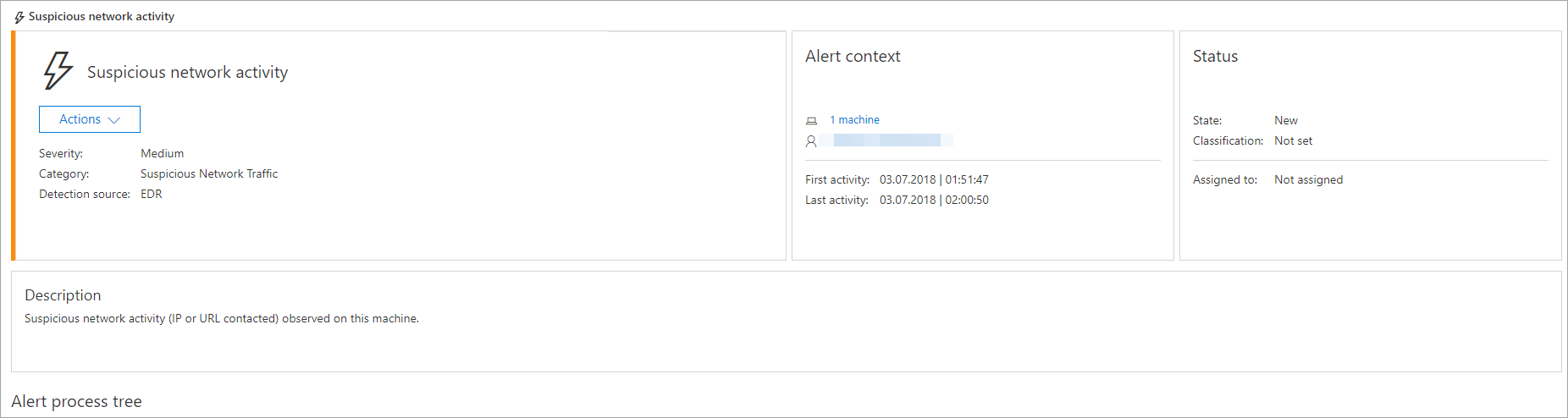
Although the malware uses the name of a trusted Windows binary file, it runs from a different location. The command line does not look the same as the source binary file. In addition, suspicions are caused by network traffic from this binary file.
Windows Defender ATP alert process tree: anomalous IP data exchange
Suspicious network activity displayed in the ATP service in Windows Defender
Windows Defender ATP alert process tree: a bogus explorer.exe process that creates suspicious connections
Dofoil uses a specialized mining application. Judging by the code, this application supports NiceHash, that is, it can conduct mining of different cryptocurrencies. The samples we analyzed were used to mine the Electroneum cryptocurrency.
Sustainability is an important feature of malware mining software. Such programs use a variety of techniques to go unnoticed for a long time and to mine cryptocurrency using stolen computing resources.
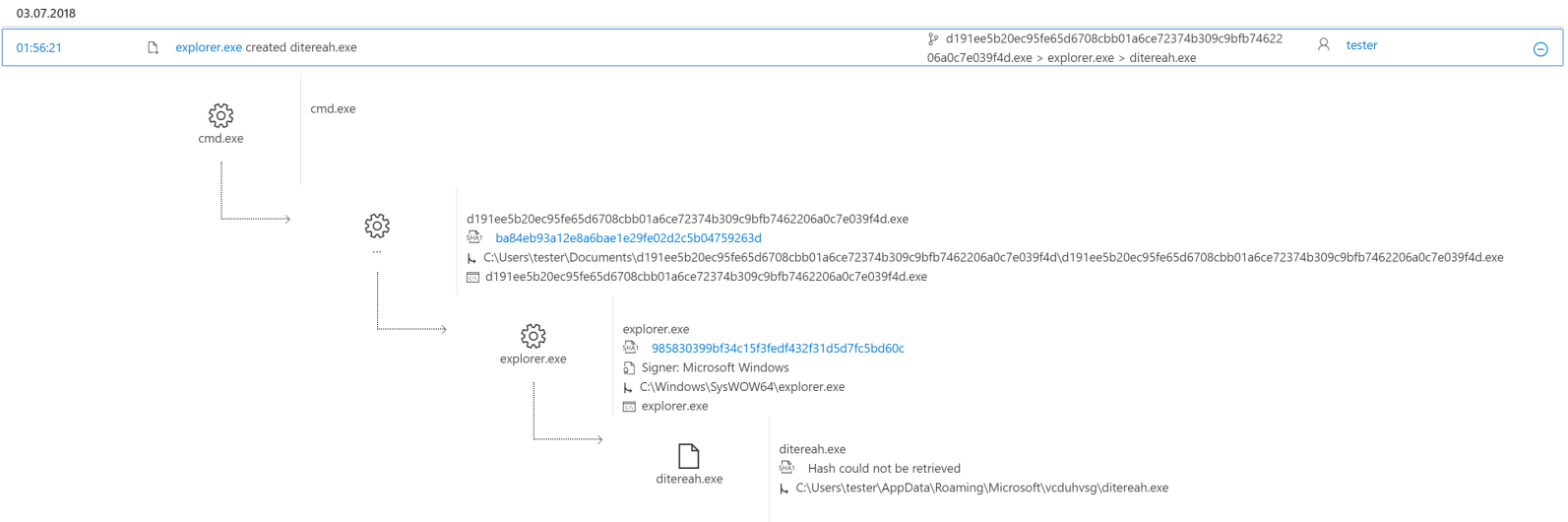
To avoid detection, Dofoil modifies the registry. The mock explorer.exe process creates a copy of the original malware in the Roaming AppData folder and renames it to ditereah.exe. It then creates a registry key or modifies an existing one to point to the newly created copy of the malware. In the sample we analyzed, the OneDrive Run section was changed.
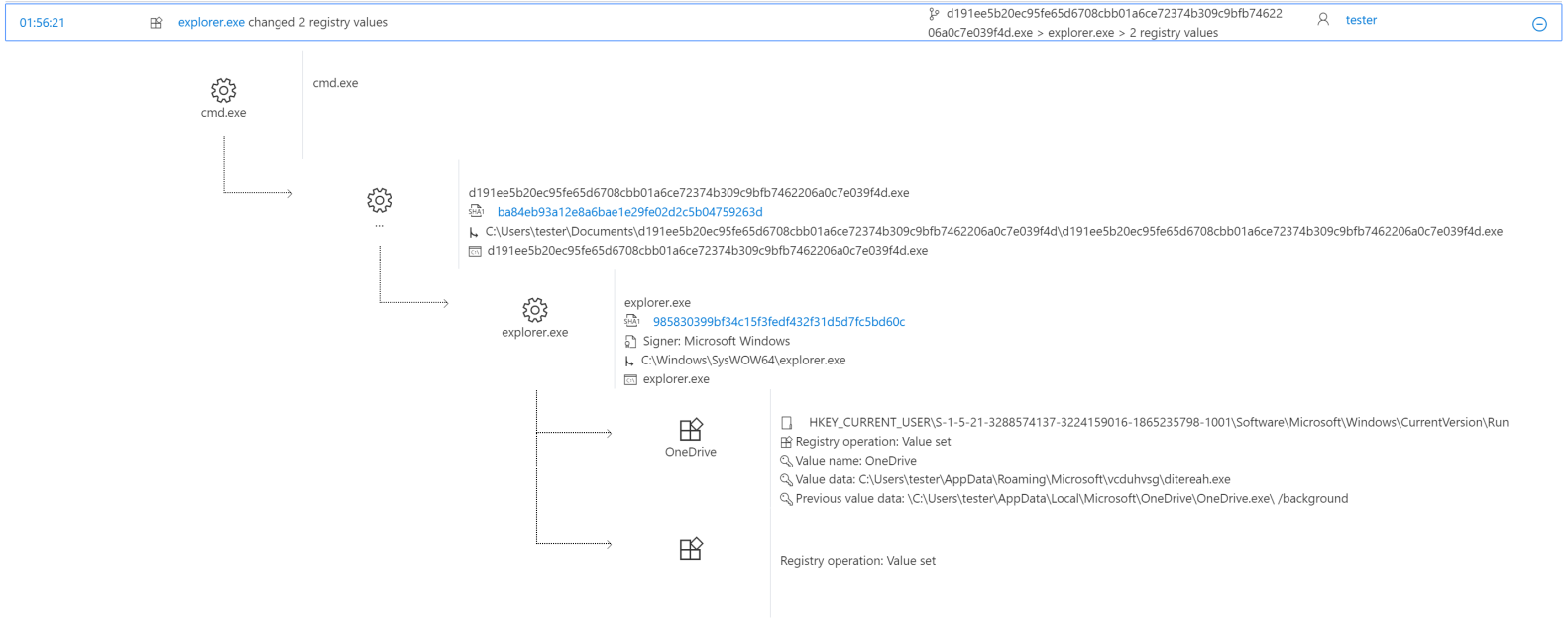
Windows Defender ATP alert process tree: creating a new malicious process (SHA-256: d191ee5b20ec95fe65d6708cbb01a6ce72374b309c9bfb7462206a0c7e039f4d) and changing the registry
Dofoil is a stable family of Trojan downloaders. They connect to management and control servers (C & C), from which they receive commands to download and install malware. In a March 6 campaign, Dofoil Trojans used Namecoin's decentralized network infrastructure to exchange information with management and control servers.
The dummy process explorer.exe records and runs another binary file, D1C6.tmp.exe (SHA256: 5f3efdc65551edb0122ab2c40738c48b677b1058f7dfcdb86b05af42a2d8299c) in the Temp folder. This file then creates and runs its copy under the name lyk.exe. The running lyk.exe file connects to IP addresses that act as DNS proxy servers for the Namecoin network. Then the file tries to contact the vinik.bit management and control server in the NameCoin infrastructure. The management and control server instructs the malware to connect to the IP address or disconnect from it, download the file from a specific link, launch a specific file or interrupt its execution, or go into sleep mode for a while.
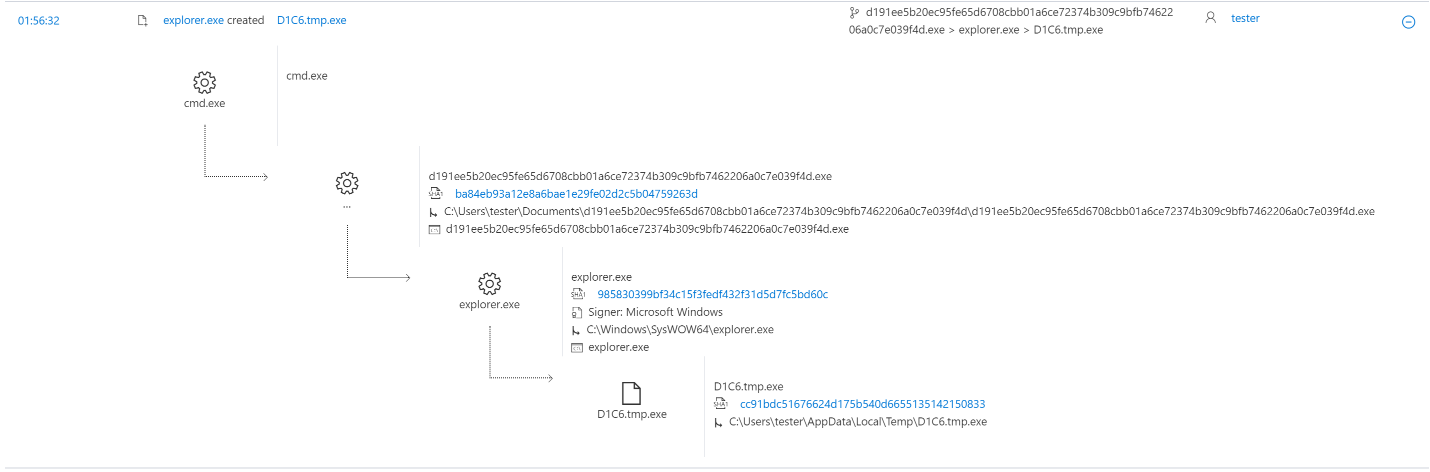
Windows Defender ATP alert process tree: creating a temporary file D1C6.tmp.exe (SHA256: 5f3efdc65551edb0122ab2c40738c48b677b1058f7dfcdb86b05af42a2d8299c)
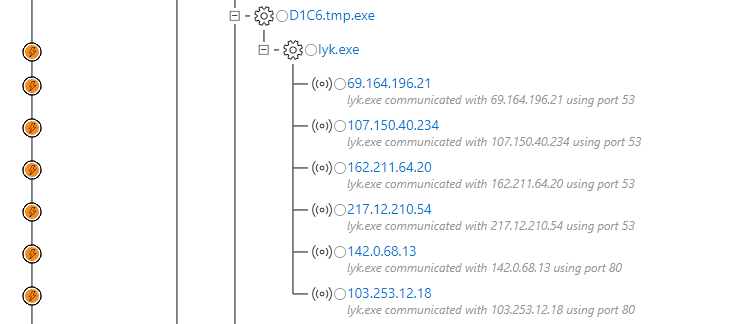
Alert process tree in Windows Defender ATP: connecting the lyk.exe file to IP addresses
As the cost of cryptocurrency grows, groups of cybercriminals make more and more attacks in order to penetrate the network and imperceptible mining.
Antivirus Windows Defender uses a multi-level approach to security. The use of threat detection algorithms based on behavior analysis, universal patterns and heuristic analysis, as well as machine learning models on client devices and in the cloud provides protection against real-time threats and epidemics.
As seen in this case, the Windows Defender Advanced Threat Protection ( WDATP ) service signals malicious behavior associated with software installation, code injection, resiliency mechanisms, and cryptocurrency mining operations. Security services can use the extensive WDATP libraries to detect abnormal network activity and take necessary action. WDATP also includes protection from the Windows Defender Antivirus, Windows Defender Exploit Guard, and Windows Defender Application Guard, simplifying security management.
The second part with a detailed description of the attack and ways of infection.

')
Trojans used in the attack were new versions of Dofoil (also known as Smoke Loader). They tried to infect devices with malware for mining cryptocurrency. In the next 12 hours, more than 400,000 cases of attack were recorded, of which 73% were in Russia, 18% in Turkey, and 4% in Ukraine.

The geographical distribution of the components of the Dofoil attack.
At the very beginning of the attack with the help of behavioral monitoring, Windows Defender antivirus revealed an unusual mechanism of attack resistance and stability. Anti-Virus immediately sent the appropriate signal to our cloud protection service.
- Within a few milliseconds, numerous cloud-based metadata-based machine learning models already blocked the detected threat when it appeared.
- After another couple of seconds, our machine learning models based on sample and detonation analysis confirmed that the program was reasonably classified as malicious. A few minutes later, models based on detonation were connected and additionally confirmed the conclusions of the previous mechanisms.
- A few minutes after the start of the attack, the anomaly detection service notified our specialists about a new potential outbreak of infection.
- After analyzing, the Microsoft incident response team assigned to the threats of this new wave a name that corresponds to the classification of malware families. Thus, at the very beginning of the company, users received a warning about blocking this threat, in which it appeared under the names assigned by machine learning systems (for example, Fuery, Fuerboos, Cloxer or Azden). Those who were blocked later saw the threat under the name of the malware family to which it belongs, that is, Dofoil or Coinminer.
Windows 10, Windows 8.1 and Windows 7 users with Windows Defender or Microsoft Security Essentials antivirus software are fully protected from this malware outbreak.

Multi-level protection system based on machine learning in the Windows Defender antivirus program
Artificial intelligence and the detection of threats based on behavioral analysis in Windows Defender form the basis of our protection system. A preemptive defense mechanism based on artificial intelligence was applied against this attack. This approach is similar to multi-level machine-based protection, which stopped the outbreak of an Emotet infection last month.
Code implementation and mining cryptocurrencies
Dofoil is the latest family of malware that uses crypto-mining software in its attacks. The cost of bitcoin and other cryptocurrencies remains attractive, and attackers take advantage of the opening opportunities and embed mining components into attacks. For example, modern exploit kits contain not extortion programs, but tools for mining cryptocurrency. Mining scripts are being introduced into fraudulent technical support sites, and even mining functions are added to some of the banker Trojans.
The starting point of the Dofoil campaign, which we discovered on March 6, was a Trojan that replaces the explorer.exe process. Process substitution is a code injection method that creates a new instance of a genuine process (in this case, c: \ windows \ syswow64 \ explorer.exe) and replaces its code with a malicious one.

Windows Defender ATP process replacement detection (SHA-256: d191ee5b20ec95fe65d6708cbb01a6ce72374b309c9bfb7462206a0c7e039f4d, found by Windows Defender antivirus under the name TrojanDownloader: Win32 / Dofoil.AB)
The bogus explorer.exe process then creates a second instance of the malicious code that runs the mining program that disguises as a safe Windows binary file, wuauclt.exe.

Detection of malware for mining cryptocurrency service Widows Defender ATP (SHA-256: 2b83c69cf32c5f8f43ec2895ec9ac730bf73e1b2f37e44a3cf8ce814fb51f120, detected by Windows Defender antivirus under the name Trojan for a challenge / challenge / challenge profile / wakew /.
Although the malware uses the name of a trusted Windows binary file, it runs from a different location. The command line does not look the same as the source binary file. In addition, suspicions are caused by network traffic from this binary file.

Windows Defender ATP alert process tree: anomalous IP data exchange

Suspicious network activity displayed in the ATP service in Windows Defender

Windows Defender ATP alert process tree: a bogus explorer.exe process that creates suspicious connections
Dofoil uses a specialized mining application. Judging by the code, this application supports NiceHash, that is, it can conduct mining of different cryptocurrencies. The samples we analyzed were used to mine the Electroneum cryptocurrency.
Resilience
Sustainability is an important feature of malware mining software. Such programs use a variety of techniques to go unnoticed for a long time and to mine cryptocurrency using stolen computing resources.
To avoid detection, Dofoil modifies the registry. The mock explorer.exe process creates a copy of the original malware in the Roaming AppData folder and renames it to ditereah.exe. It then creates a registry key or modifies an existing one to point to the newly created copy of the malware. In the sample we analyzed, the OneDrive Run section was changed.


Windows Defender ATP alert process tree: creating a new malicious process (SHA-256: d191ee5b20ec95fe65d6708cbb01a6ce72374b309c9bfb7462206a0c7e039f4d) and changing the registry
Information exchange with management and control servers
Dofoil is a stable family of Trojan downloaders. They connect to management and control servers (C & C), from which they receive commands to download and install malware. In a March 6 campaign, Dofoil Trojans used Namecoin's decentralized network infrastructure to exchange information with management and control servers.
The dummy process explorer.exe records and runs another binary file, D1C6.tmp.exe (SHA256: 5f3efdc65551edb0122ab2c40738c48b677b1058f7dfcdb86b05af42a2d8299c) in the Temp folder. This file then creates and runs its copy under the name lyk.exe. The running lyk.exe file connects to IP addresses that act as DNS proxy servers for the Namecoin network. Then the file tries to contact the vinik.bit management and control server in the NameCoin infrastructure. The management and control server instructs the malware to connect to the IP address or disconnect from it, download the file from a specific link, launch a specific file or interrupt its execution, or go into sleep mode for a while.

Windows Defender ATP alert process tree: creating a temporary file D1C6.tmp.exe (SHA256: 5f3efdc65551edb0122ab2c40738c48b677b1058f7dfcdb86b05af42a2d8299c)

Alert process tree in Windows Defender ATP: connecting the lyk.exe file to IP addresses
Real-time protection in Windows 10
As the cost of cryptocurrency grows, groups of cybercriminals make more and more attacks in order to penetrate the network and imperceptible mining.
Antivirus Windows Defender uses a multi-level approach to security. The use of threat detection algorithms based on behavior analysis, universal patterns and heuristic analysis, as well as machine learning models on client devices and in the cloud provides protection against real-time threats and epidemics.
As seen in this case, the Windows Defender Advanced Threat Protection ( WDATP ) service signals malicious behavior associated with software installation, code injection, resiliency mechanisms, and cryptocurrency mining operations. Security services can use the extensive WDATP libraries to detect abnormal network activity and take necessary action. WDATP also includes protection from the Windows Defender Antivirus, Windows Defender Exploit Guard, and Windows Defender Application Guard, simplifying security management.
Source: https://habr.com/ru/post/351356/
All Articles