Conference DEFCON 16. "Games with bar codes." Felix Lindner, head of Recurity Labs
In this speech, we will focus on bar codes - one-dimensional and two-dimensional bar codes, or matrix codes. Coding, decoding, some tricks, auxiliary things, unresolved issues. Unlike a one-dimensional linear barcode, where information is encoded in the sequence and thickness of vertical stripes, the two-dimensional barcode or 2D code contains information both vertically and horizontally.
My report consists of the following points:
The barcode was invented in 1948 by Silver and Woodland of the Drexel Institute of Technology. The first attempt to use the barcode was made in 1950 - the Association of American Railways decided to use it to identify the cars and it took more than 17 years to mark 95% of the trains and after the system did not work. At this time, people considered the barcodes useless.
')

But already in 1966, the National Association of Foodstuffs offered to apply barcodes to products in order to speed up the process of their identification at the checkout and earn more money. In 1969, the same Association created the industrial standard of the Universal Product Identification Code (later UPC), which has been used since 1970.
In 1981, the US Department of Defense required all products supplied for the army to be labeled Code 39 - a bar code that could encode large Latin letters, numbers and symbols, and you will see later why this was a bad idea.
Bar codes are divided into one-dimensional and two-dimensional. This is how one-dimensional barcodes of different standards look like:

Some of them contain only numbers, some numbers and letters. There are several standards for displaying information on a barcode.

They differ in spacing between stripes, print resolution, and so on. In the next picture you see a special bar code, which is often found on mail envelopes. This is the Postnet code; in the UK, they use similar BPO 4 code. They contain routing information for letters.

This is how two-dimensional codes look like - tell me, which of these codes is printed on your badges? That's right, it's called the Data Matrix. It differs from others in a kind of cross, which divides the label into 4 equal parts. 4 blocks of different information are encoded in them.

MAXICOD and Aztec code are rarely used in the US; I once saw MAXICOD on a package from Cisco. PDF417 is widely used in Europe, for example, for ticketing systems.
In order to decipher the barcode, use 2 ways. You can take a scanner, bring it to the label, the scanner will emit a signal, after which the read information will appear on your computer screen. Handheld scanners are inexpensive and are configured to read barcodes of various types.
The second way is to use decryption software. This is what I use. Some programs are free, others cost a few hundred dollars, although they are easy to crack. I am a lazy person, so as a real capitalist, I use the paid Omniplanar SwiftDecoder program, it is quite expensive, but very good.
Most scanners connect to a computer via USB and contain a decryption module inside. Therefore, you do not need to use special software for the scanner.

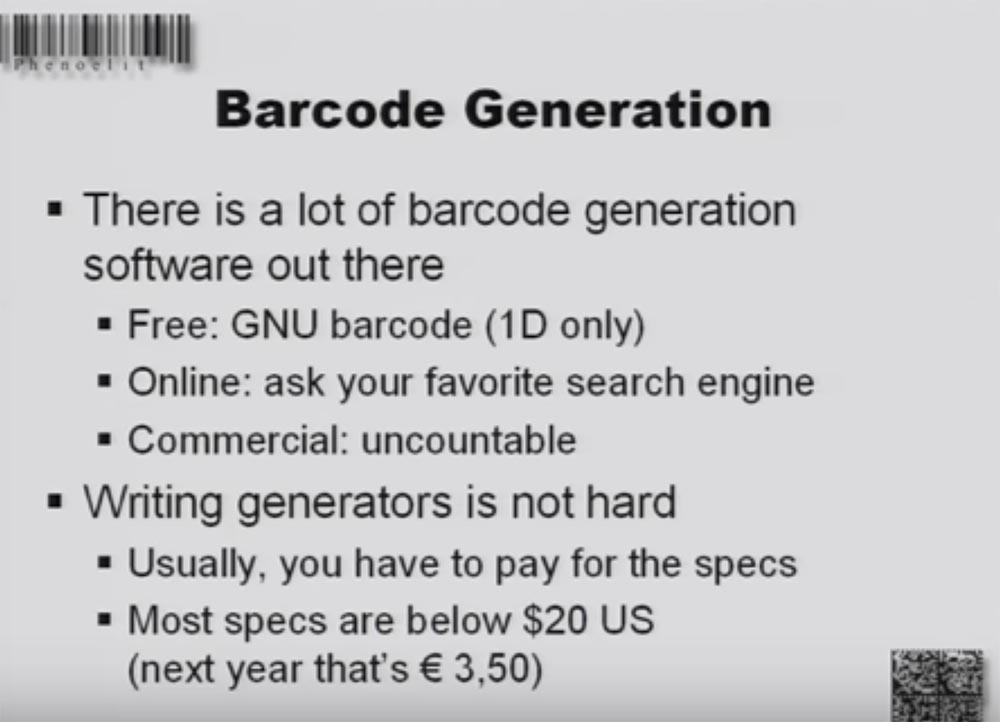
There are also different software for creating bar codes. With the help of free GNU programs you can create only one-dimensional bar codes, and in unlimited quantities. You can use various online barcode generators that create it using PHP scripts, and the number of commercial programs is infinite. Writing barcode generators is not difficult; usually you only have to pay for scripts or specifications, most of which cost less than $ 20. For example, I bought specifications for Aztec code to write my own program.
Barcodes are mainly used for three purposes, and let the Germans forgive me, but I can not give it in a different light, using other words to describe:

Virtually any scanner can be configured to read different bar codes — you need to connect it to your computer, then read the Enter Configuration access code, scan a sample of the desired code, and then scan the Save Configaration save code.
What do you do to configure the scanner? You need to go to the seller’s page of your scanner model, or to the manufacturer’s website, or to the technical support site, or, finally, call them and get a configuration table. In order to reconfigure the scanner to read another code, you need to change the type of compatible barcode, change the CRLF or the nature of the decryption. Most scanners support keyboard codes, such as “Exit” ESC, “page up” PageUp, “page down” PageDown, “delete” DEL and so on, thanks to which you can use the ESC command on the scanner as if you pressed this key on a computer keyboard. Some scanners allow you to update your own firmware by reading the corresponding barcode. Therefore, it can be quite simple to hack the whole shopping center system.

You should know that any scanner supports absolutely any barcode, and you do not need to buy separate scanners to read different types of bar codes.
The easiest way to crack a barcode is to copy it. You do not need to decipher the code if you know what it gives you. To copy you will need a good digital camera and printer.

You photograph the barcode on someone else's badge, business card or invitation, print it out on the printer and get a copy. You can use this copy where you need it. For example, the barcode on the badge of one of the hotel guests allows you to enjoy free drinks. You photograph it, print yourself a badge with the same bar code and drink beer free of charge, as if “loaded” money on your badge, which is why chip cards on our conference :) The copied bar code will help you to get to the right place if You do not have access, but someone has it. It is enough to photograph this barcode and assign it to yourself.

Last year in Europe, in Germany, I spent some time in the same hotel in Dresden. So, on the underground parking of the hotel, the machine does not see the difference between the entry and exit tickets. They have the same bar codes. You can use the parking free of charge if you copy such a ticket. In addition, they have a perpetual parking ticket, they give you one when you stay at the hotel. I do not need to recognize the code on such a ticket - I just copy it, type in a bunch of such tickets and distribute them as the right to free parking in the city center, which I did, and you can use free parking forever.

And there are also machines that accept empty containers, for example, plastic bottles, for further processing. Make such a machine was a bad idea. You usually need more time to put the bottles one by one in the acceptance compartment, rather than take to drink a bottle of beer. You put the bottle in it, it disappears inside and it all happens extremely slowly, and in return the machine gives you a voucher with a bar code. This voucher can be exchanged for money or used when buying products in the supermarket. So, just copy one voucher and print a hundred, present them at the box office and get the money.

This became possible due to the fact that the machines are not connected to each other and to cash registers, there is no information exchange, therefore people simply copy vouchers. However, the correct voucher is printed on watermarked paper, and a copy may be noticed.
Consider how you can pay for a beer using a copied barcode. Let's try to decipher the bar code EAN13, which begins with the code of the country of origin of the product, and the number 2 means that the label is used only for internal use.
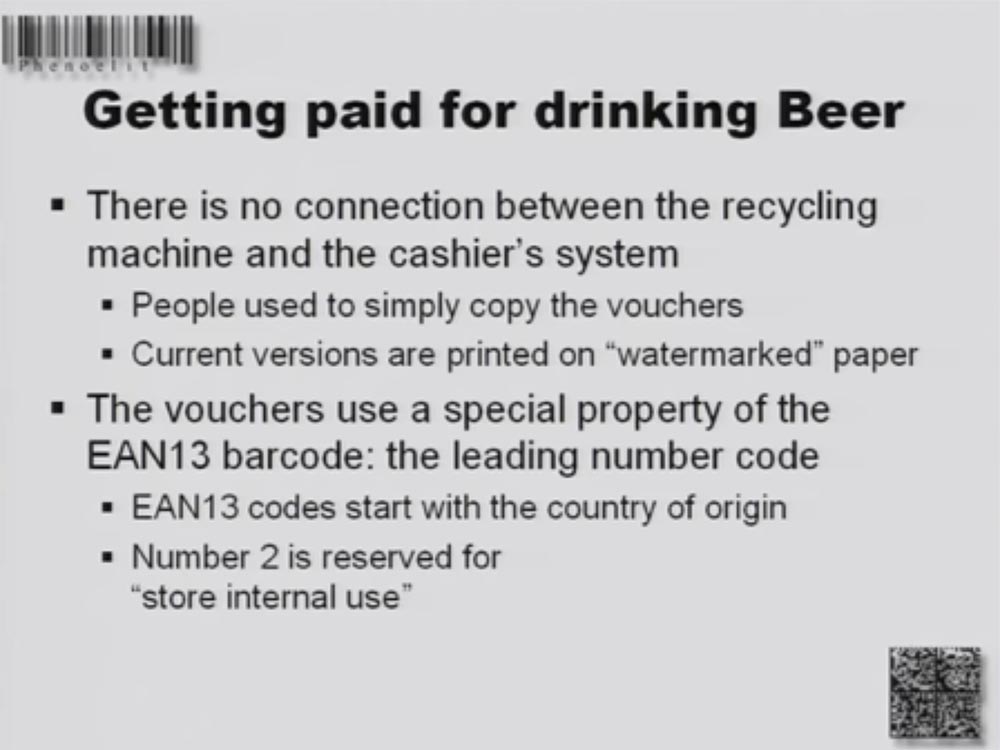
The next 6 digits are the cash register cash return team, another 5 digits indicate the volume or quantity of products. The last digit is the EAN13 verification code (checksum), it is equal to 10 minus the sum of all previous digits. In general, this allows you to return up to 999 euros, which is quite decent.

Knowing this, you can generate your own barcode and paste it on the desired product. I note that there are many people living in Berlin who do not like to work very much, but they like to drink. If you give this idea to them, they will be very grateful to you and will run to the store to get free money.
To prevent such fraud, stores use their own paper, which is easy to recognize. But if you stick a fake label with a barcode on the bottom of a heavy package of 6 cans or bottles and you are not too greedy (the amount does not attract attention), the girl at the checkout will not want to turn it over to look at the paper on which it is printed. The cashier will simply lift it up and hold the scanner from below to read the information.
The next barcode application is access control. Many companies use a barcode to control physical access. However, not everyone knows that usually the monitoring system simply checks whether the data structure is properly formed. Simply put, it checks whether it is a barcode or just a collection of random graphic elements. A simple test: it is enough to show the system scanner instead of a bar code on the pass bar code on a cigarette pack, and the door will open.

Consider the thing called desynchronization. On the pass, people read the number located above the barcode, and the scanners and identification systems read what is encrypted in the barcode itself, and this data should not be the same. Therefore, you must replace either these numbers or the barcode itself.

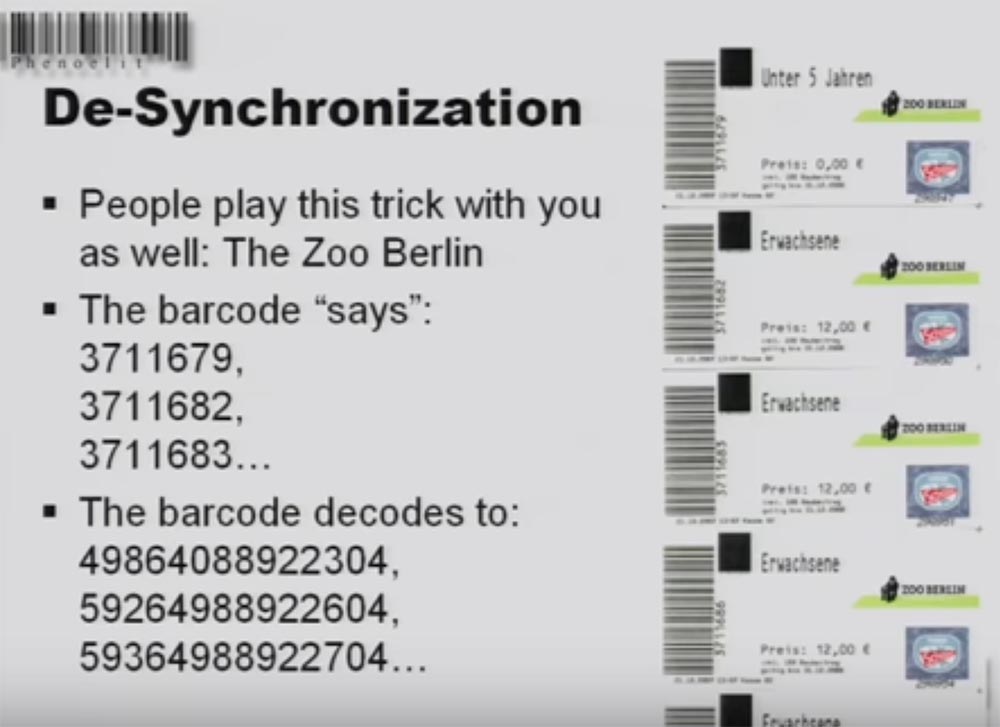
Consider this operation on the example of a ticket to the Berlin Zoo. Under the bar code printed single numbers, for example, 3711679, and decoding the code itself gives such numbers - 49864088922304. Therefore, if you copy such a ticket, remember that these sequences of numbers must be different from each other.
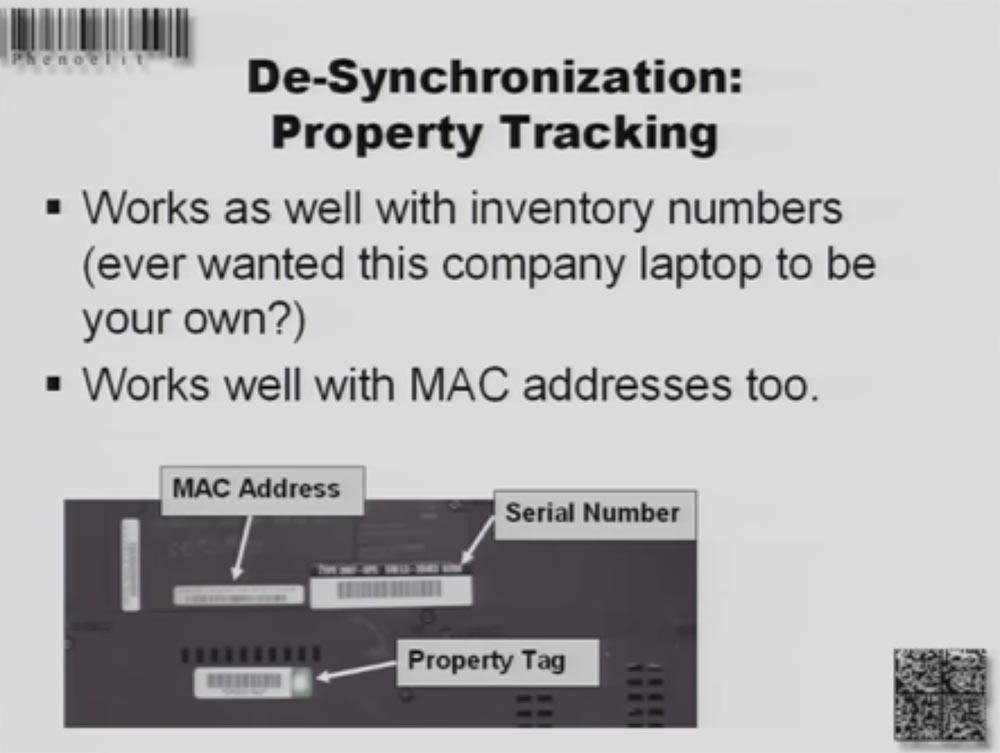
How to use desynchronization to seize someone else's property? Suppose you are working in a company, and next to you is a guy who has a laptop that is much cooler than you, and you want to take his laptop away. The fact is that for the use of state-owned equipment an employee working under a contract receives a bar code. This code is pasted on the laptop, and the same code is available on the pass or badge. If the codes match, you can take and use this technique. The right to use the equipment is checked when the employee enters the office building.

To do this, you copy the barcode from the badge of the rightful owner, namely the barcode, not the number, and place it on your badge. You wait until the guy finishes his job, take his computer out of the building, then come back, change the code on the badge to your own and calmly go home.
In the same way, you can access the network or data that you do not have. Suppose you use the MAC address of a computer that belongs to another employee, or his accession number, to enter the network. The MAC address is usually put on the device itself, here is the serial number and sticker of the owner with a bar code. By copying the barcode from the badge of the rightful owner, you can get hold of the information of a colleague or apply MAC to the barcode, which contains only F, and put the network.
What other tricks can be done with bar codes? In Germany, you can use the 24-hour automatic DVD rental system Video24, which is located, including in my house, without supervision, for free, and I was interested to deal with it. What does a regular user need to watch a movie on a DVD for money? Barcode membership card, PIN or even fingerprint biometric authentication. The procedure for renting is as follows: You scan the card, enter the PIN, select a movie, exit the session, and then watch the movie on your computer or TV. So you can order a movie through the website.

If you want to rent a movie on a physical medium, rent a DVD from a machine, simply scan the card and pick it up. To return the disk, you need to “roll” the card again, enter the PIN code and put the disk back into the machine. What is the problem? You do not need to enter a pin code.

So, there is a barcode on the card, indicated by a letter and four numbers. The letter matches the first letter of the client's last name. You just need to scan this barcode from your friend, changing only the numbers, and when he orders a movie over the Internet, you will get it! Naturally, a friend of this film will not see, but it will be impossible to prove it, so he will be forced to pay for viewing. So you can watch a DVD and even get it in the machine. The site maintains records of pre-orders, so you can choose the drive that no one has ordered, and be sure to view it.
The next trick is called "Injection and Multi-Decryption." Most barcode scanners come with factory settings. Even if the settings are changed, you can always reconfigure them. Built-in decryption applications in most cases use the type of barcode for which they were written, usually EAN13 or 2o5.

Using the more powerful Code 128 encoding, random data can be entered into a readable barcode, such as SQL scripts, separate encryption, or string formatting. The newer the system application, the better this technology works. Take for example medical research. You can change the software “stuffing” of the scanner so that the real bar code printed on the test tubes with analyzes will be read as completely different data. That is, you can replace the test results, and no one will notice.
The next trick is reading QR codes. These codes work as hyperlinks. Suppose you have a newspaper. A real newspaper, one that we, hackers, haven’t seen for years! You can take a picture of a two-dimensional barcode from its page. Commercial software decoders convert it to an HTTP link, and then the program forces the browser of your mobile device to open the page located at this address.

In fact, this is a very bad idea, and I will explain why.

The fact is that usually this barcode does not lead directly to the site of the newspaper Die Welt, where the article is located, but first sends your browser to a commercial site, as shown in the picture.
When this barcode is decrypted, it turns out that it is possible to imprint random content into the barcode of newspapers, and this is called advertising. However, most business people trust their newspapers, at least they consider them safe.
But the browser of the mobile device, following this link, can pick up viruses or third-party cookies. He automatically, without your will, picks up an advertisement or something worse. That is, reading such a barcode makes your browser vulnerable. As a result, you get:
You need it? Of course not! Therefore, never read the barcode from the pages of newspapers, it is dangerous!
Barcodes have another great ability. This is the density of the one-dimensional barcode strip layout. It depends on the length of the barcode and its readability. You can print a barcode of any length by encoding a lot of information in it. However, scanners and identifiers work with barcodes of a certain length, they are designed to read a limited number of digits. Thus, choosing the density of the strips, you can print much more information within the same physical space. To do this, you must use a laser printer with high print resolution, otherwise the strip of code will merge, and it will become unreadable. By the way, have you noticed that getting the scanner more information than expected is the goal of those people who are called hackers?
So, to read the barcode caused the scanner's buffer overflow and cause problems, choose a high print density. Your favorite barcode code should be Code 128, because it has a full 7-bit ASCII code set and uses the control function code FC4.

Let's return to the barcodes that print in the newspaper and which direct your browser by reference. Using the disassembler, we will see that the QR code can also contain the application number used, the company's phone number, the username and password of the user, and the address of the third-party site that is being logged on.
Consider another thing that is in Germany and which could not be broken. This station packing, or Pack Station. You come here with your mailing envelope or parcel, and this station prints you a sticker with a bar code that you stick on your mailing. And then a UPS employee comes here, who cannot always find the door to pick up your mail.

So, I copied a lot of barcodes into my notebook and tried to crack the packing station scanner with them, to deceive him, but I couldn’t do anything with it. This is probably because this scanner reads any one-dimensional barcodes, using only 2o5 digital coding and its software as a whole “no”.
Another useful note: if we can solve the purpose of the barcode, we can create our own code. It is quite simple.
Our next goal is postal codes. Postal services are increasingly using a two-dimensional matrix barcode instead of the usual stamps. They do not need to glue stamps anymore, they simply print the barcodes on envelopes and save themselves time. The advantage of this solution is the automatic creation of such a code and its automatic recognition. Some emails use their own barcode types, which not all scanners work with.

What exactly do email scanners check, what data do they verify? It depends on the purpose of the barcode. Consider the envelope of the letter that I received from an Australian company. There is an ASCII code consisting of all zeros. The cost of the letter is zero, because the company did not pay for sending it, it sends letters for free. If I print the same code on the envelope and send a letter to Australia, I will not have to pay for it either.
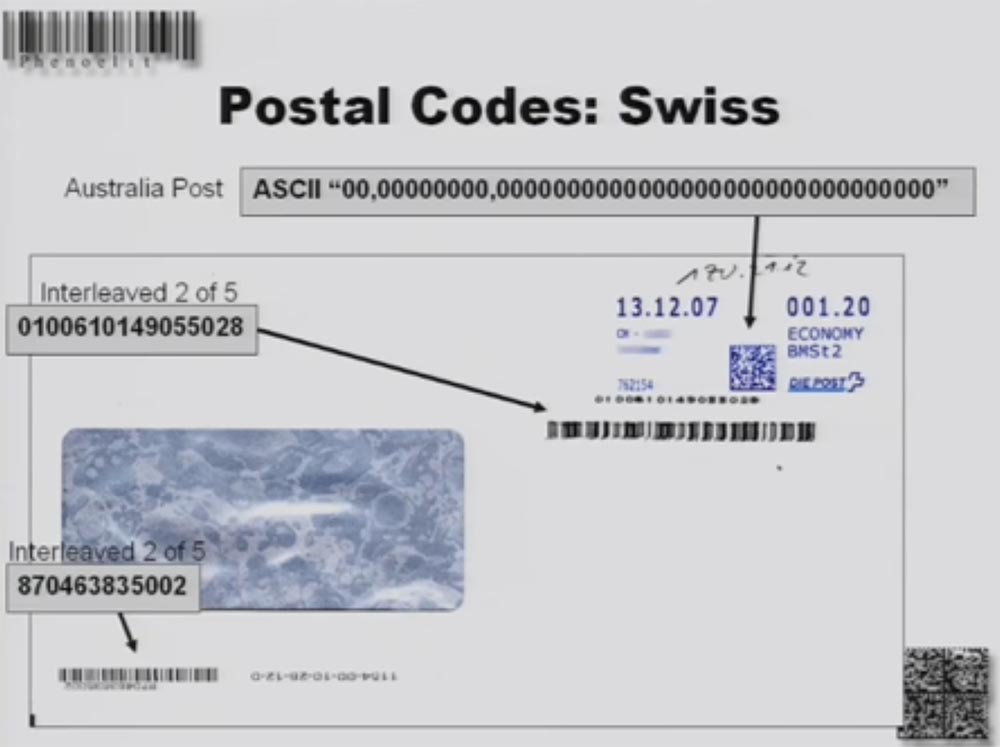
Two more digital codes in the encoding 25 indicate postal information and have nothing to do with the cost of sending.
Postal codes in the USA are different. The system of applying barcodes is called "Intellectual Mail." It uses Code 128 encoding, and its scripts, or specifications, can be easily found on the Internet as a .doc file. That is, all barcode information is easily decoded.

However, this information does not contain any indication that you are the recipient of this letter, that is, that it is addressed to you. It only indicates that the sender of the letter is assigned a unique code. And it can be found on this code within 30-45 days, because after this period the information about the person who sent you the letter is deleted from the mail service database. This uniqueness is not protected in any way, because it is in the general barcode. That is, the numbers from 10 to 18 can be changed so that the sender cannot be traced. Let's look at the Pentagon’s recommendations, which describe how to recognize dangerous mailings, or how to protect yourself from a bomb in a letter. It says that dangerous emails include:
In this case, the credibility of the identification number of the sender is not subject to doubt. If the letter's barcode contains the sender's ID, then everything is fine with it. It turns out that you can send anything, to anyone, anywhere, completely free of charge, if you indicate in the barcode ID that the sender is the Pentagon, the US Department of Defense, because they trust him.
Consider now the plane tickets. Now the fashion trend is to order tickets online and print on a home printer. Frankfurt / Main Airport security requires that all tickets ordered via the Internet or purchased at the box office must have a bar code. I often fly, so I want to show you my tickets with barcodes.

This is what my program for decoding barcodes on tickets looks like. It is made in different colors for better perception. Here I found all the information: passenger's name, number, reservation code, departure date, where it is flying, flight number, class, place, ticket number. The last digit is a security code that serves to identify the passenger. However, it is static, that is, does not change. Thus, we can print our own ticket with our own barcode, sticking everything we need, including the security code. , .

, . , , . , , , . , , , , , .

. - , . , , . , , , . .
. , , , , . . , , , , , . , , , . — , , . , . . $1, . $5 – , .
-, . , , – .

, . , .
, - :
, .
«» -, , , lagune.cyphertext.de/twiki .
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The Truth About VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
My report consists of the following points:
- quick introduction to the essence of barcodes;
- coding and reading bar codes;
- scanners;
- simple tricks with barcodes;
- hidden attacks;
- reading selected samples;
- unsolved problems and challenges;
- principles of safe use of barcode.
The barcode was invented in 1948 by Silver and Woodland of the Drexel Institute of Technology. The first attempt to use the barcode was made in 1950 - the Association of American Railways decided to use it to identify the cars and it took more than 17 years to mark 95% of the trains and after the system did not work. At this time, people considered the barcodes useless.
')

But already in 1966, the National Association of Foodstuffs offered to apply barcodes to products in order to speed up the process of their identification at the checkout and earn more money. In 1969, the same Association created the industrial standard of the Universal Product Identification Code (later UPC), which has been used since 1970.
In 1981, the US Department of Defense required all products supplied for the army to be labeled Code 39 - a bar code that could encode large Latin letters, numbers and symbols, and you will see later why this was a bad idea.
Bar codes are divided into one-dimensional and two-dimensional. This is how one-dimensional barcodes of different standards look like:

Some of them contain only numbers, some numbers and letters. There are several standards for displaying information on a barcode.

They differ in spacing between stripes, print resolution, and so on. In the next picture you see a special bar code, which is often found on mail envelopes. This is the Postnet code; in the UK, they use similar BPO 4 code. They contain routing information for letters.

This is how two-dimensional codes look like - tell me, which of these codes is printed on your badges? That's right, it's called the Data Matrix. It differs from others in a kind of cross, which divides the label into 4 equal parts. 4 blocks of different information are encoded in them.

MAXICOD and Aztec code are rarely used in the US; I once saw MAXICOD on a package from Cisco. PDF417 is widely used in Europe, for example, for ticketing systems.
In order to decipher the barcode, use 2 ways. You can take a scanner, bring it to the label, the scanner will emit a signal, after which the read information will appear on your computer screen. Handheld scanners are inexpensive and are configured to read barcodes of various types.
The second way is to use decryption software. This is what I use. Some programs are free, others cost a few hundred dollars, although they are easy to crack. I am a lazy person, so as a real capitalist, I use the paid Omniplanar SwiftDecoder program, it is quite expensive, but very good.
Most scanners connect to a computer via USB and contain a decryption module inside. Therefore, you do not need to use special software for the scanner.

There are also different software for creating bar codes. With the help of free GNU programs you can create only one-dimensional bar codes, and in unlimited quantities. You can use various online barcode generators that create it using PHP scripts, and the number of commercial programs is infinite. Writing barcode generators is not difficult; usually you only have to pay for scripts or specifications, most of which cost less than $ 20. For example, I bought specifications for Aztec code to write my own program.

Barcodes are mainly used for three purposes, and let the Germans forgive me, but I can not give it in a different light, using other words to describe:
- for identification, as a label;
- for fast data transfer from a visual carrier (business card) to a physical device, for example, to a smartphone;
- for all sorts of hooliganism, for example, for the exchange of encrypted curses, I call it GGU, Ganz Grober Unfug, which, translated from German, means “a very rough trick”.

Virtually any scanner can be configured to read different bar codes — you need to connect it to your computer, then read the Enter Configuration access code, scan a sample of the desired code, and then scan the Save Configaration save code.
What do you do to configure the scanner? You need to go to the seller’s page of your scanner model, or to the manufacturer’s website, or to the technical support site, or, finally, call them and get a configuration table. In order to reconfigure the scanner to read another code, you need to change the type of compatible barcode, change the CRLF or the nature of the decryption. Most scanners support keyboard codes, such as “Exit” ESC, “page up” PageUp, “page down” PageDown, “delete” DEL and so on, thanks to which you can use the ESC command on the scanner as if you pressed this key on a computer keyboard. Some scanners allow you to update your own firmware by reading the corresponding barcode. Therefore, it can be quite simple to hack the whole shopping center system.

You should know that any scanner supports absolutely any barcode, and you do not need to buy separate scanners to read different types of bar codes.
The easiest way to crack a barcode is to copy it. You do not need to decipher the code if you know what it gives you. To copy you will need a good digital camera and printer.

You photograph the barcode on someone else's badge, business card or invitation, print it out on the printer and get a copy. You can use this copy where you need it. For example, the barcode on the badge of one of the hotel guests allows you to enjoy free drinks. You photograph it, print yourself a badge with the same bar code and drink beer free of charge, as if “loaded” money on your badge, which is why chip cards on our conference :) The copied bar code will help you to get to the right place if You do not have access, but someone has it. It is enough to photograph this barcode and assign it to yourself.

Last year in Europe, in Germany, I spent some time in the same hotel in Dresden. So, on the underground parking of the hotel, the machine does not see the difference between the entry and exit tickets. They have the same bar codes. You can use the parking free of charge if you copy such a ticket. In addition, they have a perpetual parking ticket, they give you one when you stay at the hotel. I do not need to recognize the code on such a ticket - I just copy it, type in a bunch of such tickets and distribute them as the right to free parking in the city center, which I did, and you can use free parking forever.

And there are also machines that accept empty containers, for example, plastic bottles, for further processing. Make such a machine was a bad idea. You usually need more time to put the bottles one by one in the acceptance compartment, rather than take to drink a bottle of beer. You put the bottle in it, it disappears inside and it all happens extremely slowly, and in return the machine gives you a voucher with a bar code. This voucher can be exchanged for money or used when buying products in the supermarket. So, just copy one voucher and print a hundred, present them at the box office and get the money.

This became possible due to the fact that the machines are not connected to each other and to cash registers, there is no information exchange, therefore people simply copy vouchers. However, the correct voucher is printed on watermarked paper, and a copy may be noticed.
Consider how you can pay for a beer using a copied barcode. Let's try to decipher the bar code EAN13, which begins with the code of the country of origin of the product, and the number 2 means that the label is used only for internal use.

The next 6 digits are the cash register cash return team, another 5 digits indicate the volume or quantity of products. The last digit is the EAN13 verification code (checksum), it is equal to 10 minus the sum of all previous digits. In general, this allows you to return up to 999 euros, which is quite decent.

Knowing this, you can generate your own barcode and paste it on the desired product. I note that there are many people living in Berlin who do not like to work very much, but they like to drink. If you give this idea to them, they will be very grateful to you and will run to the store to get free money.
To prevent such fraud, stores use their own paper, which is easy to recognize. But if you stick a fake label with a barcode on the bottom of a heavy package of 6 cans or bottles and you are not too greedy (the amount does not attract attention), the girl at the checkout will not want to turn it over to look at the paper on which it is printed. The cashier will simply lift it up and hold the scanner from below to read the information.
The next barcode application is access control. Many companies use a barcode to control physical access. However, not everyone knows that usually the monitoring system simply checks whether the data structure is properly formed. Simply put, it checks whether it is a barcode or just a collection of random graphic elements. A simple test: it is enough to show the system scanner instead of a bar code on the pass bar code on a cigarette pack, and the door will open.

Consider the thing called desynchronization. On the pass, people read the number located above the barcode, and the scanners and identification systems read what is encrypted in the barcode itself, and this data should not be the same. Therefore, you must replace either these numbers or the barcode itself.

Consider this operation on the example of a ticket to the Berlin Zoo. Under the bar code printed single numbers, for example, 3711679, and decoding the code itself gives such numbers - 49864088922304. Therefore, if you copy such a ticket, remember that these sequences of numbers must be different from each other.

How to use desynchronization to seize someone else's property? Suppose you are working in a company, and next to you is a guy who has a laptop that is much cooler than you, and you want to take his laptop away. The fact is that for the use of state-owned equipment an employee working under a contract receives a bar code. This code is pasted on the laptop, and the same code is available on the pass or badge. If the codes match, you can take and use this technique. The right to use the equipment is checked when the employee enters the office building.

To do this, you copy the barcode from the badge of the rightful owner, namely the barcode, not the number, and place it on your badge. You wait until the guy finishes his job, take his computer out of the building, then come back, change the code on the badge to your own and calmly go home.
In the same way, you can access the network or data that you do not have. Suppose you use the MAC address of a computer that belongs to another employee, or his accession number, to enter the network. The MAC address is usually put on the device itself, here is the serial number and sticker of the owner with a bar code. By copying the barcode from the badge of the rightful owner, you can get hold of the information of a colleague or apply MAC to the barcode, which contains only F, and put the network.

What other tricks can be done with bar codes? In Germany, you can use the 24-hour automatic DVD rental system Video24, which is located, including in my house, without supervision, for free, and I was interested to deal with it. What does a regular user need to watch a movie on a DVD for money? Barcode membership card, PIN or even fingerprint biometric authentication. The procedure for renting is as follows: You scan the card, enter the PIN, select a movie, exit the session, and then watch the movie on your computer or TV. So you can order a movie through the website.

If you want to rent a movie on a physical medium, rent a DVD from a machine, simply scan the card and pick it up. To return the disk, you need to “roll” the card again, enter the PIN code and put the disk back into the machine. What is the problem? You do not need to enter a pin code.

So, there is a barcode on the card, indicated by a letter and four numbers. The letter matches the first letter of the client's last name. You just need to scan this barcode from your friend, changing only the numbers, and when he orders a movie over the Internet, you will get it! Naturally, a friend of this film will not see, but it will be impossible to prove it, so he will be forced to pay for viewing. So you can watch a DVD and even get it in the machine. The site maintains records of pre-orders, so you can choose the drive that no one has ordered, and be sure to view it.
The next trick is called "Injection and Multi-Decryption." Most barcode scanners come with factory settings. Even if the settings are changed, you can always reconfigure them. Built-in decryption applications in most cases use the type of barcode for which they were written, usually EAN13 or 2o5.

Using the more powerful Code 128 encoding, random data can be entered into a readable barcode, such as SQL scripts, separate encryption, or string formatting. The newer the system application, the better this technology works. Take for example medical research. You can change the software “stuffing” of the scanner so that the real bar code printed on the test tubes with analyzes will be read as completely different data. That is, you can replace the test results, and no one will notice.
The next trick is reading QR codes. These codes work as hyperlinks. Suppose you have a newspaper. A real newspaper, one that we, hackers, haven’t seen for years! You can take a picture of a two-dimensional barcode from its page. Commercial software decoders convert it to an HTTP link, and then the program forces the browser of your mobile device to open the page located at this address.

In fact, this is a very bad idea, and I will explain why.

The fact is that usually this barcode does not lead directly to the site of the newspaper Die Welt, where the article is located, but first sends your browser to a commercial site, as shown in the picture.
When this barcode is decrypted, it turns out that it is possible to imprint random content into the barcode of newspapers, and this is called advertising. However, most business people trust their newspapers, at least they consider them safe.
But the browser of the mobile device, following this link, can pick up viruses or third-party cookies. He automatically, without your will, picks up an advertisement or something worse. That is, reading such a barcode makes your browser vulnerable. As a result, you get:
- XSS threat, or cross-site scripting, that is, when you open this page, a malicious script can be executed on your device;
- the link can take control of your mailbox;
- the link may direct you to the site with viruses;
- clicking on a link can download binary codes to your phone from a malicious website.
You need it? Of course not! Therefore, never read the barcode from the pages of newspapers, it is dangerous!
Barcodes have another great ability. This is the density of the one-dimensional barcode strip layout. It depends on the length of the barcode and its readability. You can print a barcode of any length by encoding a lot of information in it. However, scanners and identifiers work with barcodes of a certain length, they are designed to read a limited number of digits. Thus, choosing the density of the strips, you can print much more information within the same physical space. To do this, you must use a laser printer with high print resolution, otherwise the strip of code will merge, and it will become unreadable. By the way, have you noticed that getting the scanner more information than expected is the goal of those people who are called hackers?
So, to read the barcode caused the scanner's buffer overflow and cause problems, choose a high print density. Your favorite barcode code should be Code 128, because it has a full 7-bit ASCII code set and uses the control function code FC4.

Let's return to the barcodes that print in the newspaper and which direct your browser by reference. Using the disassembler, we will see that the QR code can also contain the application number used, the company's phone number, the username and password of the user, and the address of the third-party site that is being logged on.
Consider another thing that is in Germany and which could not be broken. This station packing, or Pack Station. You come here with your mailing envelope or parcel, and this station prints you a sticker with a bar code that you stick on your mailing. And then a UPS employee comes here, who cannot always find the door to pick up your mail.

So, I copied a lot of barcodes into my notebook and tried to crack the packing station scanner with them, to deceive him, but I couldn’t do anything with it. This is probably because this scanner reads any one-dimensional barcodes, using only 2o5 digital coding and its software as a whole “no”.
Another useful note: if we can solve the purpose of the barcode, we can create our own code. It is quite simple.
Our next goal is postal codes. Postal services are increasingly using a two-dimensional matrix barcode instead of the usual stamps. They do not need to glue stamps anymore, they simply print the barcodes on envelopes and save themselves time. The advantage of this solution is the automatic creation of such a code and its automatic recognition. Some emails use their own barcode types, which not all scanners work with.

What exactly do email scanners check, what data do they verify? It depends on the purpose of the barcode. Consider the envelope of the letter that I received from an Australian company. There is an ASCII code consisting of all zeros. The cost of the letter is zero, because the company did not pay for sending it, it sends letters for free. If I print the same code on the envelope and send a letter to Australia, I will not have to pay for it either.

Two more digital codes in the encoding 25 indicate postal information and have nothing to do with the cost of sending.
Postal codes in the USA are different. The system of applying barcodes is called "Intellectual Mail." It uses Code 128 encoding, and its scripts, or specifications, can be easily found on the Internet as a .doc file. That is, all barcode information is easily decoded.

However, this information does not contain any indication that you are the recipient of this letter, that is, that it is addressed to you. It only indicates that the sender of the letter is assigned a unique code. And it can be found on this code within 30-45 days, because after this period the information about the person who sent you the letter is deleted from the mail service database. This uniqueness is not protected in any way, because it is in the general barcode. That is, the numbers from 10 to 18 can be changed so that the sender cannot be traced. Let's look at the Pentagon’s recommendations, which describe how to recognize dangerous mailings, or how to protect yourself from a bomb in a letter. It says that dangerous emails include:
- departures from abroad;
- special notes like "confidential", "personally for ...";
- handwritten or poorly typed address;
- no sender address;
- letter weight is more than specified;
- visible wiring or metal foil, etc.
In this case, the credibility of the identification number of the sender is not subject to doubt. If the letter's barcode contains the sender's ID, then everything is fine with it. It turns out that you can send anything, to anyone, anywhere, completely free of charge, if you indicate in the barcode ID that the sender is the Pentagon, the US Department of Defense, because they trust him.
Consider now the plane tickets. Now the fashion trend is to order tickets online and print on a home printer. Frankfurt / Main Airport security requires that all tickets ordered via the Internet or purchased at the box office must have a bar code. I often fly, so I want to show you my tickets with barcodes.

This is what my program for decoding barcodes on tickets looks like. It is made in different colors for better perception. Here I found all the information: passenger's name, number, reservation code, departure date, where it is flying, flight number, class, place, ticket number. The last digit is a security code that serves to identify the passenger. However, it is static, that is, does not change. Thus, we can print our own ticket with our own barcode, sticking everything we need, including the security code. , .

, . , , . , , , . , , , , , .

. - , . , , . , , , . .
. , , , , . . , , , , , . , , , . — , , . , . . $1, . $5 – , .
-, . , , – .

, . , .
, - :
- , : , , , ..
- -, , ID-, «» ;
- , – , ;
- : , ! , . , .
- !
, .
«» -, , , lagune.cyphertext.de/twiki .
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The Truth About VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
Source: https://habr.com/ru/post/351344/
All Articles