Information security of bank non-cash payments. Part 4 - Overview of Threat Modeling Standards

What research
Links to other parts of the study
- Information security of bank non-cash payments. Part 1 - Economic fundamentals.
- Information security of bank non-cash payments. Part 2 - Typical IT infrastructure of the bank.
- Information security of bank non-cash payments. Part 3 - Formation of requirements for the protection system.
- Information security of bank non-cash payments. Part 4 - Overview of threat modeling standards. ( You are here )
- Information security of bank non-cash payments. Part 5 - 100+ thematic links about hacking banks.
- Information security of bank non-cash payments. Part 6 - Analysis of banking crimes.
- Information security of bank non-cash payments. Part 7 - The basic threat model.
- Information security of bank non-cash payments. Part 8 - Typical threat models.
In the previous publication of the cycle, we formed the basic requirements for the system of information security of non-cash payments and said that the specific content of protective measures will depend on the threat model.
To form a qualitative threat model, it is necessary to take into account existing practices and practices on this issue.
')
In this article, we will conduct an express review of about 40 sources describing the processes of modeling threats and managing information security risks. Consider both GOSTs and documents of Russian regulators (FSTEC of Russia, the Federal Security Service of Russia, the Central Bank of the Russian Federation) and international practices.
Brief description of the threat modeling process
The end result of the threat modeling process should be a document - a threat model containing a list of significant (relevant) for the protected object information security threats.
When modeling threats, protected objects are usually considered:
- Information Systems;
- automated systems;
- informatization objects;
- business processes.
By and large, the threat model does not have to be represented in the form of a list. This may be a tree (graph), mayndcard, or some other form of recording, which allows specialists to work with it conveniently.
The specific composition of threats will depend on the properties of the protected object and the business processes implemented with it. Accordingly, one of the initial data for modeling will be the description of the protected object itself.
If a hypothetical object is considered, a typical (basic) threat model is formed . If a real object is considered, then a private threat model is formed.
When modeling threats, in addition to the description of the protected object, specialists must have knowledge of the threats themselves.
In practice, this knowledge can be gleaned from:
- research reports on detected vulnerabilities that can be used to implement threats;
- reports of computer forensic investigations of real computer attacks;
- reports of companies specializing in information security, devoted to the analysis of the current situation in the field of computer security;
- publications in the media on computer crimes;
- data banks or threat catalogs , which list the threats grouped according to one or another principle.
The initial stage of the modeling process will be the identification of threats , that is, the selection of the largest possible list of threats that can at least theoretically affect the protected object.
At the implementation of this stage, nature plays a cruel joke with information security specialists. The problem is that human memory is associative, and we cannot take and extract all content from it, for example, remember all possible threats.
In order to form a list of all possible threats, various tricks are used, allowing specialists to ask themselves certain questions or use the principles according to which threats will be extracted from memory and recorded. Examples of such techniques can be threat classifiers, threat trees or patterns of typical computer attacks . We will discuss these methods below.
After the formation of a list of all possible threats, it begins to be filtered so that, ultimately, only significant (topical) threats to the organization remain. The filtering process, as a rule, is performed in several iterations, at each of which threats on one or another basis are discarded.
Begin with the sign of the availability of opportunities (resources) for violators to implement threats. To determine it, first form a special document - the model of the offender , in which the potential offenders are identified and their capabilities determined. Then, the previously obtained threats are correlated with the model of the offender and discard all threats, the realization of which goes beyond the capabilities of potential violators.
The next sign to filter threats is a sign of insignificance of risk . At first, an organization determines the level of risk that it considers insignificant. Then he assesses the risk from the realization of each threat and, if it is less than or equal to the given level, the threat is discarded.
Thus, after the end of filtering, a threat model will be obtained, containing significant (relevant) for the organization of information security threats.
Threat Identification Technique - “Threat Classifiers”
Most information security threats can be grouped (categorized) by a particular attribute. The resulting classification schemes can be used by experts as questionnaires to their memory from which they will extract threats.
Take, for example, the task of modeling threats to the security of personal data (PD) processed in personal data information systems (ISPD).
In 2008, the FSTEC of Russia issued a methodological document for this purpose - the Basic Model of PD Threats. This document contains many classification schemes, of which we consider the only one - the classification of threats by “source of threat”.
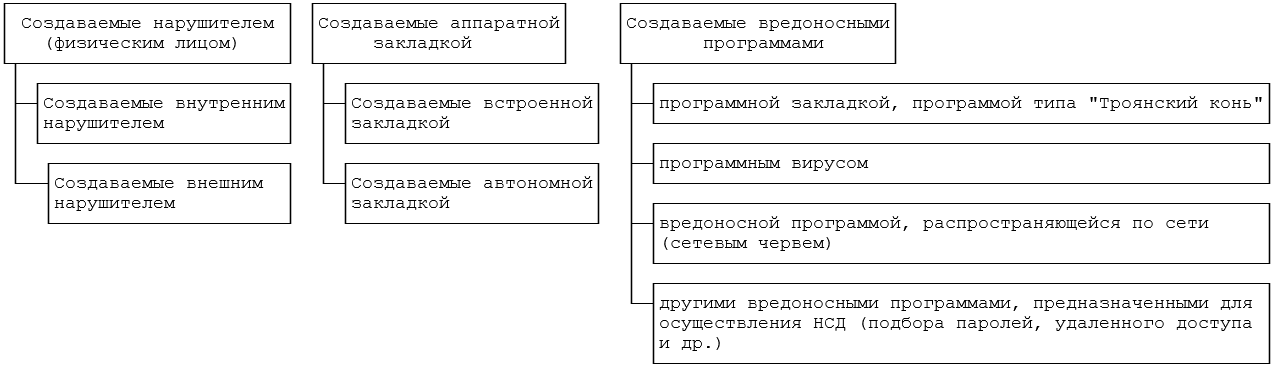
A specialist, building a private model of threats, can use this scheme, ask himself the question: “What threats to personal data will come from the actions of an internal violator?” - and record these threats. Then ask the following question: “How can an external intruder attack personal data?”, Etc. This series of questions allows the specialist to describe all the threats known to him, without forgetting about anything.
Threat Identification Technique - “Threat Tree”
When using this technique, the information security specialist puts himself in the place of the intruder and begins to think about how he would attack the protected object.
In the beginning, a high-level threat is formulated, which will be the root of the future tree.
Then the specialist begins to decompose this threat into low-level ones, the implementation of which can lead to the realization of the threat in question. To do this, he may ask questions, how or by what the investigated threat can be realized.
The resulting threats are affiliated with respect to the one under consideration and are written into the tree as its descendants. Then they, in turn, are also decomposed, and so on until the required level of detail is achieved.
A similar approach has long been known in the art and is used to build fault trees, the formation of which is standardized in GOST R 51901.13-2005 (IEC 61025: 1990) Risk Management. Fault tree analysis .
To illustrate the use of “threat trees”, we consider the formation of a threat model for an information object that is an isolated computer that is not connected to a computer network. Suppose that at this facility important information is being processed, the security of which is required to be ensured.
We define the following as a high-level threat: violation of security properties of protected information.
Common security properties are confidentiality, integrity, availability. Thus, child threats will be:
- privacy violation of protected data;
- violation of the integrity of the protected data;
- violation of the availability of protected data.
Decomposing the threat of “breach of confidentiality of protected data”.
Let us ask ourselves the question: “Due to what can this threat be realized?” - and as a response we will write the following options:
- disclosure of protected data by persons allowed to process them;
- implementation of unauthorized access to protected data by non-authorized persons;
- leakage of protected data through technical channels.
We will do the same with the threat of “violation of the integrity of protected data”. It can be decomposed into:
- damage to protected data due to actions of persons allowed to process them;
- damage to protected data due to malicious code;
- damage to protected data due to failures and failures of the computer on which they are processed.
The decomposition of the threat to “violation of the accessibility of protected data” can be represented by the following threats:
- Destruction of protected data due to the impact of malicious code (crypto-fiber);
- destruction of protected data due to failure of the hard disk of the computer on which they are stored;
- violation of the conditions of operation of the object of information, making it impossible to work with his staff.
As a result, we obtain the following tree:
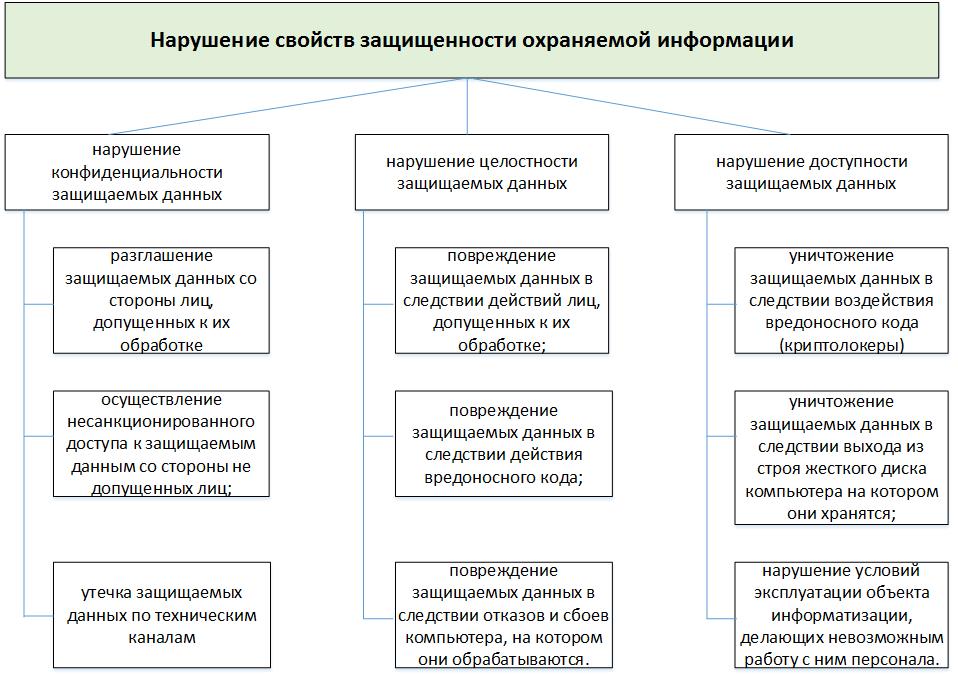
As we can see, even such a primitive model that we have just built is rather cumbersome when it is graphically displayed. Therefore, “threat trees” are mainly documented in hierarchical lists.
Methods of identifying threats "patterns of typical attacks"
The basis of this technique is the idea that in carrying out computer attacks, attackers every time make some similar sequence of actions, which can be called a typical attack pattern.
One of the most well-known patterns of computer attacks at the moment is the kill chain pattern described by Lockheed Martin, which includes 7 steps:

Stage 1 . Intelligence (Reconnaissance) - the collection of data about the attacked object.
Stage 2 . Weaponization - the development of tools (malicious code) to conduct an attack.
Stage 3 . Delivery (Delivery) - delivery of malicious code to the attacked object.
Stage 4 . Exploitation - the use of any vulnerability of the attacked object node to launch malicious code.
Stage 5 . Installation (Installation) - installation of hidden remote access on a compromised node.
Stage 6 . Gaining Control (C2) - the organization of a remote access channel of attackers to a compromised node.
Stage 7 . Actions (Actions) - performing actions for which the attack was carried out.
The research organization MITER , having slightly changed the names of the stages, called this template Cyber Attack Lifecycle .
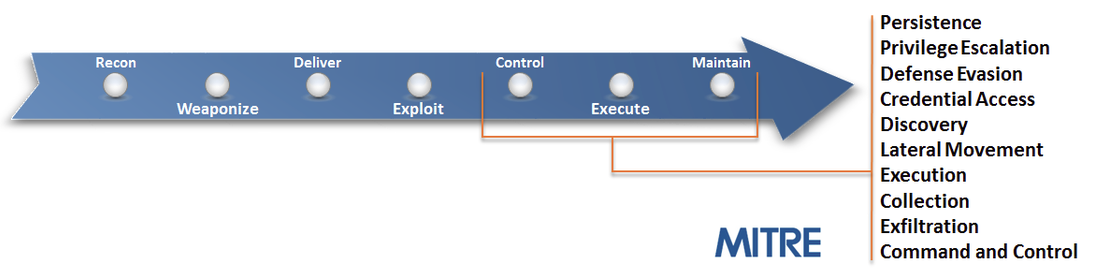
In addition, MITER expanded the description of the various stages and formed a matrix of typical tactics of intruders at each stage. This matrix was named ATT & CK .
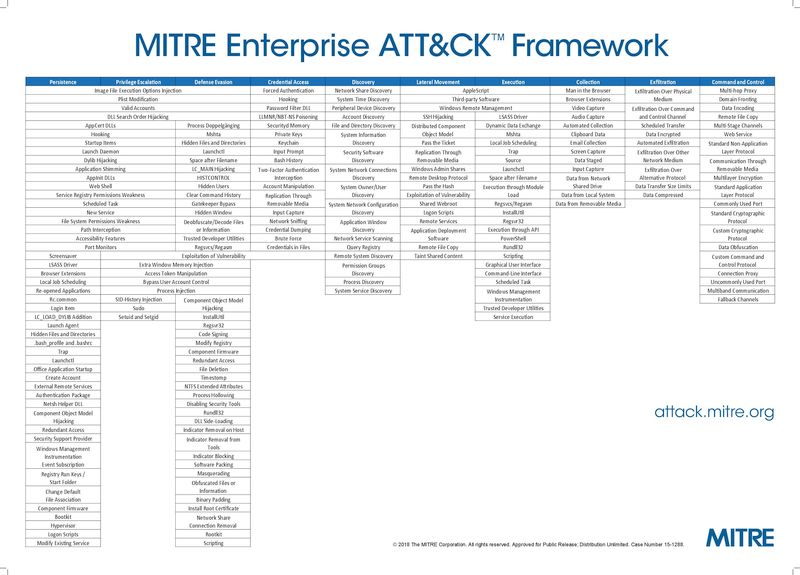
(clickable)
Although the matrix is not universal, it still allows you to describe the actions taken by attackers when making a large number of real attacks.
From the point of view of threat modeling, a typical attack pattern can be considered as a classifier of threats, and a matrix of typical tactics as a significant fragment of the threat model.
Clarifications will require only the last stage of the template - “Actions”, then, for the sake of which the attack was carried out, well, the stages themselves can be supplemented by unaccounted tactics.
Documents of FSTEC of Russia on modeling threats to personal data of 2008.
Both documents are methodical, that is non-binding to use, but reveal how, according to the FSTEC of Russia, the task of modeling threats to personal data security should be addressed.
The basic model of PDD threats, FSTEC, 2008, contains a single source data on PD security threats processed in an ISPD, related to:
- with interception (removal) of PD through technical channels for the purpose of copying or illegal distribution;
- with unauthorized, including accidental, access to ISPDn for the purpose of changing, copying, illegal distribution of PDn or destructive influences on PDPn elements and PDN processed in them using software and hardware and software to destroy or block PDn.
Specifies a formal description of the threats:
- threat of leakage through technical channels: = <source of threat>, <medium of PD propagation and influences / receiver of informative signal / transmitter of an acting signal>, <PD carrier>
- unauthorized access threat: = <threat source>, <software or hardware vulnerability>, <threat realization method>, <target object>, <unauthorized access>.
- threat of unauthorized access in ISPDn: = <source of threat>, <vulnerability of ISPDn>, <method of threat realization>, <object of influence (program, protocol, data, etc.)>, <destructive action>.
- threat of “Denial of service”: = <source of threat>, <vulnerability of ISPDn>, <method of threat realization>, <object of influence (carrier of PDN)>, <direct result of threat realization (buffer overflow, blocking the processing procedure, “looping” processing and so on.)>;
- threat of primary health insurance in ISPDn: = <class of malicious program (with indication of habitat)>, <source of threat (carrier of malicious program)>, <method of infection>, <object of influence (boot sector, file, etc.)>, < description of possible destructive actions>, <additional information about the threat (residency, speed of propagation, polymorphicity, etc.)>.
Formal description of threats used the following abbreviations:
ISPDn - personal data information system.
NSD - unauthorized access.
WWW - software and mathematical influence (the introduction of malware).
The document provides classification signs of threats and vulnerabilities, and malicious programs. A small catalog of typical threats associated with technical channel leaks and unauthorized access is provided. A typical model of offenders is given and their capabilities are determined.
The method for determining actual PD threats in 2008 defines an algorithm by which it is possible to filter threats based on the insignificance of risk. To this end, the methodology presents methods for determining the feasibility of a threat (probability), a hazard (damage) hazard indicator and the rules for classifying a security threat as not relevant (with little risk).
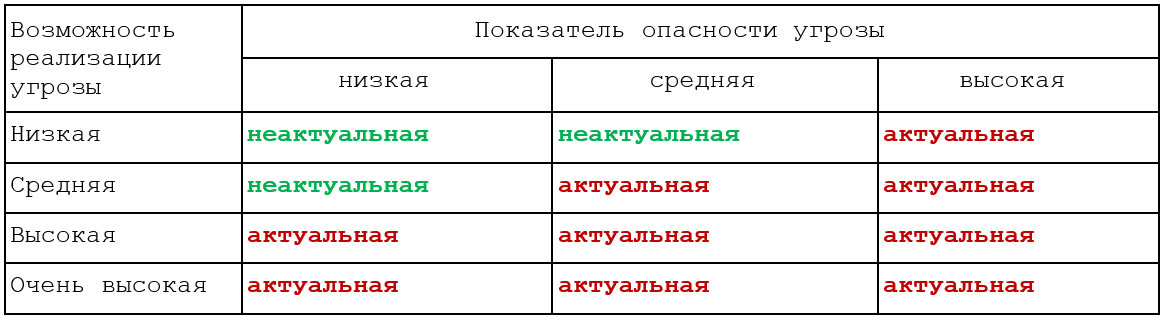
Documents of the FSTEC of Russia on modeling threats in state information systems (GIS) and the database of threats to the FSTEC of Russia.
- Methodical document FSTEC of Russia. Measures to protect information in the state information systems (approved by the FSTEC of Russia on February 11, 2014)
- Draft methodological document of FSTEC of Russia. Methods for determining information security threats in information systems
- FSTEC of Russia Threats Data Bank (bdu.fstec.ru) .
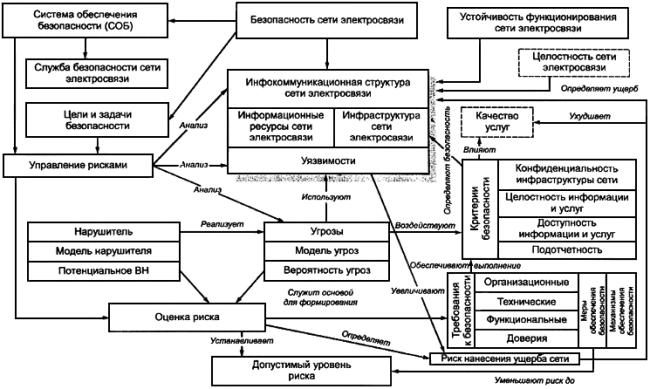
Methodical document FSTEC of Russia. Measures to protect information in the state information systems (approved by the FSTEC of Russia on February 11, 2014) . Information security threats (UMI) are determined based on the results of assessing the capabilities (potential, equipment and motivation) of external and internal violators, analyzing possible information system vulnerabilities, possible ways to implement information security threats and the consequences of violation of information security properties (confidentiality, integrity, availability).
Formal description of information security threats:
Ubi: = [the possibility of the offender; information system vulnerabilities; method of threat realization; consequences from the realization of the threat].
Opportunities (potential) of violators are divided into three groups:
- Intruder with basic potential.
- Infiltrator with Basic Enhanced Potential
- High potential offender
The interpretation of the capabilities of violators is given in the draft methodological document of the FSTEC of Russia. The method for determining information security threats in information systems .
The description and classification of vulnerabilities is carried out using national standards:
- GOST R 56545-2015 Information security. Vulnerabilities of information systems. Vulnerability Guidelines
- GOST R 56546-2015 Information security. Vulnerabilities of information systems. Classification of Information System Vulnerabilities
Vulnerabilities themselves, ways of realizing threats and possible damage are listed in the FSTEC of Russia threat database .
Methodical recommendations of the Federal Security Service of Russia on modeling threats to the security of personal data
Guidelines identify the main threats to PD, which can be neutralized only with the help of SKZI. These include:
- transfer of personal data via communication channels that are not protected from interception by the violator of information transmitted through it or from unauthorized impacts on this information (for example, when transmitting personal data over public information and telecommunication networks);
- storage of personal data on storage media, unauthorized access to which by the offender cannot be excluded using non-cryptographic methods and techniques.
The document also defines the classification of opportunities for violators:
| N | Generalized opportunities for attack sources |
|---|---|
| one | The ability to independently carry out the creation of methods of attack, preparation and conduct of attacks only outside the controlled area |
| 2 | Opportunity to independently create methods of attack, prepare and conduct attacks within the controlled area, but without physical access to hardware (hereinafter - AS), on which the SKZI and the environment of their functioning are implemented |
| 3 | The ability to independently create methods of attack, preparation and conduct of attacks within the controlled area with physical access to the AU, which are implemented SKZI and the environment of their operation |
| four | The ability to attract professionals with experience in the development and analysis of SKZI (including experts in the field of analysis of linear transmission signals and signals of side electromagnetic radiation and interference SKZI) |
| five | Opportunity to attract specialists with experience in the development and analysis of CIPF (including specialists in the field of use for implementing the attacks of undocumented capabilities of application software) |
| 6 | Opportunity to attract specialists with experience in the development and analysis of SKZI (including specialists in the field of using for implementing the attacks undocumented capabilities of hardware and software components of the environment of functioning of SKZI) |
Bank of Russia Documents on Information Security Risks
- Letter No. 197-T of the Central Bank of the Russian Federation of December 7, 2007 “On Risks in Remote Banking Services”
- Bank of Russia Ordinance No. 3889-U, dated December 10, 2015, “On the Identification of Threats to the Security of Personal Data Actual in the Processing of Personal Data in Personal Data Information Systems”
- Recommendations in the field of standardization of the Bank of Russia RS BR IB IBBS-2.2-2009. "Methodology for risk assessment of information security breaches"
The letter of the Central Bank of the Russian Federation dated December 7, 2007 No. 197-T “On the risks of remote banking services” contains a list of typical threats to remote banking services and their customers, including:
- Implementing DoS / DDoS attacks against RBS servers.
- Theft of personal information of bank customers by phishing via e-mail.
- Theft of payment card details using skimming attacks and fake ATMs.
- Theft of client access details to the RBS systems using social engineering and telephone fraud.
Bank of Russia Ordinance No. 3889-U dated December 10, 2015 “On the Identification of Threats to the Security of Personal Data Actual in the Processing of Personal Data in Personal Data Information Systems” contains a sectoral list of security threats to personal data, including the following threats:
- the threat of unauthorized access to personal data by persons authorized in the information system of personal data, including during the creation, operation, maintenance and / or repair, modernization, decommissioning of the information system of personal data;
- the threat of exposure to malicious code external to the personal data information system;
- the threat of the use of social engineering methods to persons who have authority in the personal data information system;
- the threat of unauthorized access to alienable personal data carriers;
- the threat of loss (loss) of personal data carriers, including portable personal computers of users of the personal data information system;
- the threat of unauthorized access to personal data by persons who do not have authority in the personal data information system, using vulnerabilities in the organization of personal data protection;
- the threat of unauthorized access to personal data by persons who do not have authority in the personal data information system using vulnerabilities in the personal data information system software;
- the threat of unauthorized access to personal data by persons who do not have authority in the personal data information system using vulnerabilities in ensuring the protection of network interaction and data transmission channels;
- the threat of unauthorized access to personal data by persons who do not have authority in the personal data information system, using vulnerabilities in ensuring the protection of computer networks of the personal data information system;
- the threat of unauthorized access to personal data by persons who do not have authority in the personal data information system using vulnerabilities caused by non-compliance with the requirements for the use of cryptographic information protection tools.
Recommendations in the field of standardization of the Bank of Russia RS BR IB IBBS-2.2-2009. "Methodology for risk assessment of information security breaches"
The document proposes the following risk assessment procedures:
Procedure 1. Determining the list of types of information assets for which procedures for assessing the risks of information security violations are performed (hereinafter referred to as the area of information security risks assessment).
Procedure 2. Determining the list of types of environment objects corresponding to each of the types of information assets in the area of information security risk assessment.
Procedure 3. Identification of sources of threats for each of the types of environment objects defined as part of procedure 2.
Procedure 4. Determination of the IS of IS threats in relation to the types of environment objects determined under the procedure 2.3.
Procedure 5. Determination of an ITF violation of information security for information types of information about risk assessment of information security violations.
Procedure 6. Risk assessment of information security breaches.
The degree of risk acceptability is proposed to be assessed using a “classical” table of risk assessment, taking into account the likelihood and possible damage.
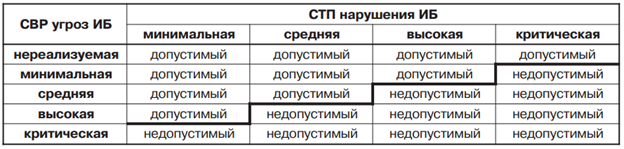
Here SVR - the degree of possibility of realization of the threat, STP - the severity of the consequences
The recommendations also contain a small catalog of threats, broken down by classes.
Class 1. Sources of information security threats associated with adverse events of a natural, man-made and social nature.
Class 2. Sources of information security threats related to the activities of terrorists and persons committing crimes and offenses
Class 3. Sources of information security threats associated with the activities of suppliers / providers / partners
Class 4. Sources of information security threats associated with failures, failures, destruction / damage of software and hardware
Class 5. Sources of IS threats associated with the activities of internal violators of IS
Class 6. Sources of IS threats associated with the activities of external violators of IS
Class 7. Sources of information security threats associated with non-compliance with the requirements of supervisory and regulatory authorities and current legislation.
National standards of the Russian Federation (GOST)
- GOST R 51275-2006. Protection of information. The object of informatization. Factors affecting information. General provisions
- GOST R ISO / TO 13569-2007. Financial services. Information Security Recommendations
- GOST R 56545-2015 Information security. Vulnerabilities of information systems. Vulnerability Guidelines
- GOST R 56546-2015 Information security. Vulnerabilities of information systems. Classification of Information System Vulnerabilities
- GOST R 53113.1-2008 Information Technology (IT). Protection of information technologies and automated systems from information security threats implemented using hidden channels. Part 1. General Provisions
- GOST R 52448-2005 Information Security. Securing telecommunication networks. General provisions
- GOST R ISO / IEC 27005-2010. Information technology. Methods and means of security. Information Security Risk Management
GOST R 51275-2006. Protection of information. The object of informatization. , . General provisions
50922-2006 . , « (-)» () . , , .
/ 13569-2007. .
«C» - . , , , , , . , , .
56545-2015 . . 56546-2015 . . . GOST R 50922-2006 Information Security. Basic terms and definitions .
The standards provide a classification of information systems vulnerabilities, containing three classification characteristics:
- by area of origin;
- by types of IP deficiencies;
- at the place of occurrence (manifestation).
The vulnerabilities themselves are proposed to be described in the form of a passport containing the following sections:
- The name of the vulnerability.
- Vulnerability ID.
- Identifiers of other vulnerability description systems.
- Brief description of the vulnerability.
- Vulnerability class.
- The name of the software and its version.
- Service (port), which (which) is used for software operation.
- Software programming language.
- Type of fault.
- Place of occurrence (manifestation) of vulnerability.
- Fault type identifier.
- The name of the operating system and the type of hardware platform.
- .
- , .
- () .
OVAL .
53113.1-2008 (). , . 1.
, , , .
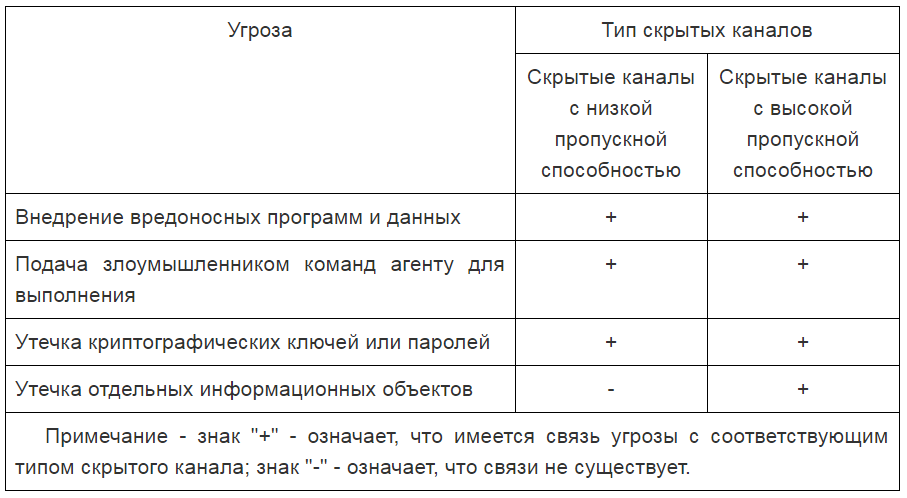
52448-2005 . . General provisions
, :
51275-2006. . . , . . .
, , , , , .
, . — (, ) (, , ).
/ 27005-2010. . .
, ISO 27K . .

Appendix C provides examples of typical threats, and Appendix D presents typical vulnerabilities.
NIST Special Publications
- NIST SP 800-30. Guide for Conducting Risk Assessments
- NIST SP 800-39. Managing Information Security Risk
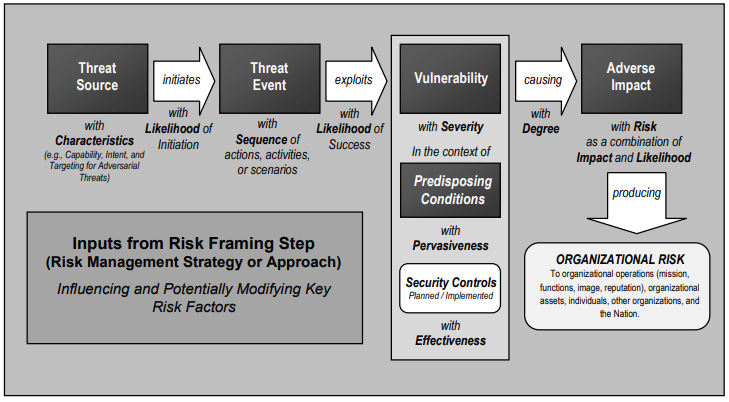
NIST SP 800-30. Guide for Conducting Risk Assessments The
document focuses on risk management at the level of an organization’s management.
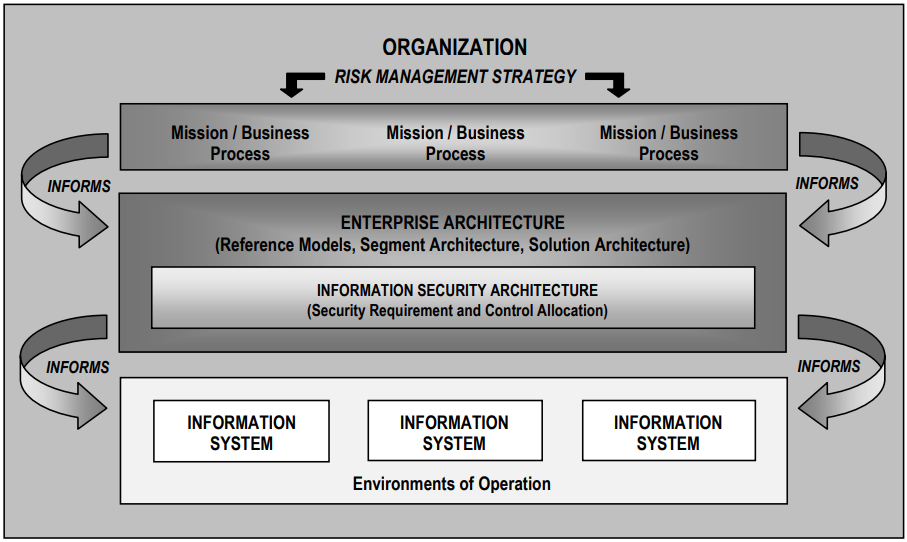
NIST SP 800-39. Managing Information Security Risk The
document describes an enterprise-level information security risk management methodology. The main goal of the methodology is to connect the information security system with the mission and objectives of the organization
OCTAVE (Operationally Critical Threat, Asset, and Vulnerability Evaluation)
OCTAVE , , . 8 :
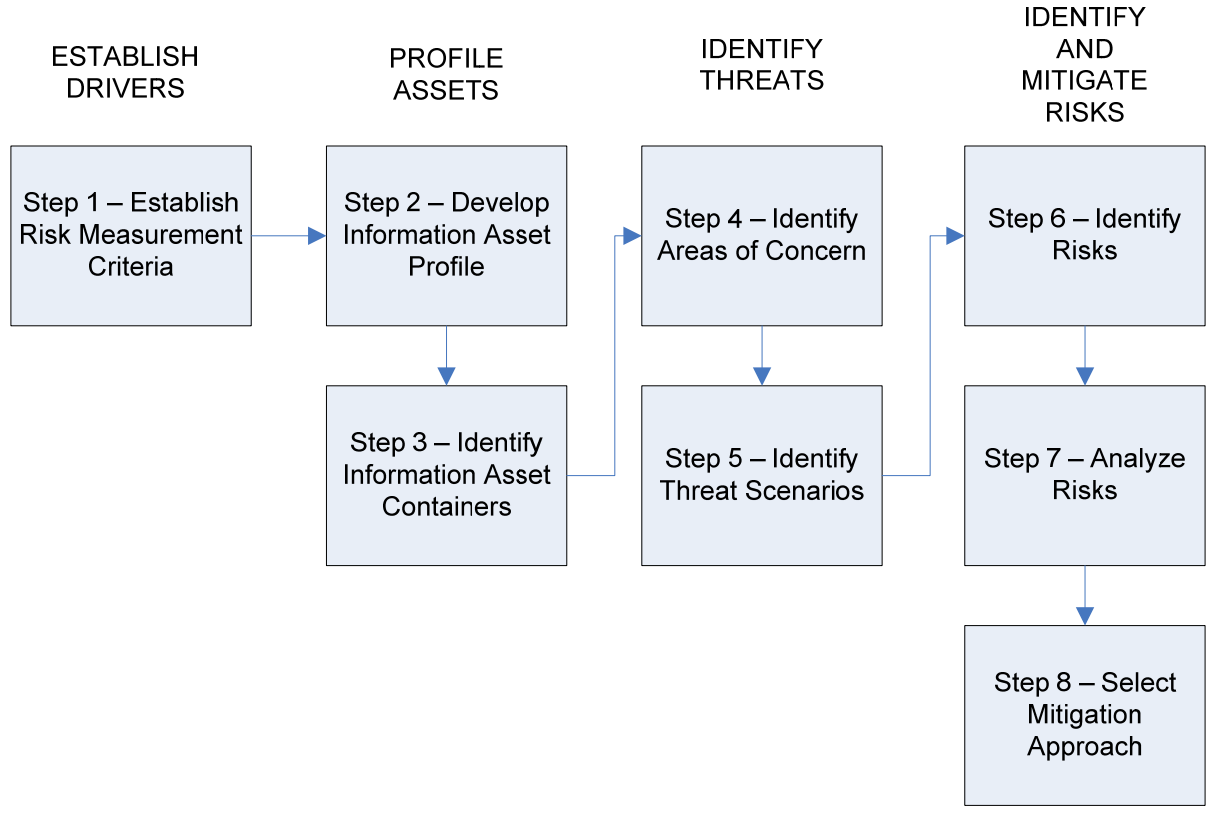
- (Establish Risk Measurement Criteria).
- (Develop an Information Asset Profile).
- / / (Identify Information Asset Containers).
- (Identify Areas of Concern)
- (Identify Threat Scenarios)
- (Identify Risks)
- (Analyze Risks)
- Select Information Security Risk Handling Measures (Select Mitigation Approach)
The threat tree methodology is used to identify the threats carried out in step 5.
Trike Methodology
Trike is based on a risk-based approach to building information security and is intended for conducting information security audits and building threat models.
Distinctive features of this methodology are:
- its initial focus on the use of specialized software for building threat models;
- use of attack trees to describe security threats;
- use of typical attack libraries.
Microsoft threat modeling techniques and publications
Microsoft Security Development Lifecycle . «» – («waterfall») , , . « (design)» .
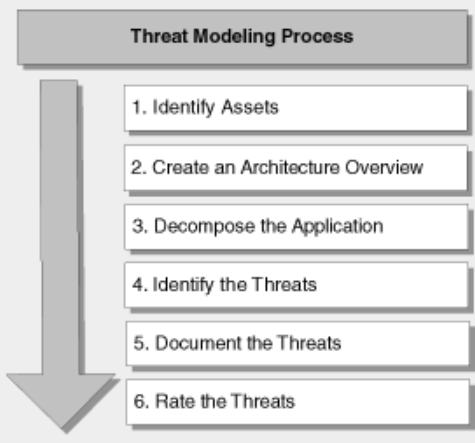
:
- STRIDE;
- ;
- .
The STRIDE methodology is a classification scheme for describing attacks depending on the type of exploits used for their implementation or the motivation of the intruder.
STRIDE is an acronym for first letters:
- S poofing Identity - "personality substitution." The intruder impersonates himself as a legitimate user (for example, stole a login / password) and performs malicious actions on his behalf.
- T ampering with Data - "fake data." The intruder forges the data that is available to him when the Web application is running. These can be cookies, HTTP request elements, etc.
- R epudiation - “rejection of transactions”. The intruder can refuse transactions when there is not sufficient audit of user actions on the Web application side.
- I of nformation Disclosure - «disclosure of sensitive information." The intruder tries to disclose the personal data of other users, authentication information, etc.
- D enial of Service - “Denial of Service”.
- E levation of Privilege - “privilege escalation”.
After identifying the threats, the SDL suggests assessing the risks they engender. For this, the DREAD technique can be used .
The name of the DREAD methodology is also an acronym for the first letters of the categories for which the risk is assessed:
- D amage Potential - what damage will be done if the threat is realized?
- R eproducibility - how easy is it to implement a threat?
- E xploitability – , ?
- A ffected Users – ?
- D iscoverability – ?
:
Risk_DREAD = (DAMAGE + REPRODUCIBILITY + EXPLOITABILITY + AFFECTED USERS + DISCOVERABILITY) / 5 ,
0 10. , Damage Potential :
- 0 = ;
- 5 = ;
- 10 = .
- OWASP Top10
Web-. - OWASP Testing project
Web-. - WASC Threat Classification
, Web-. - Bluetooth Threat Taxonomy
Bluetooth. - ENISA Threat Landscape
, . - ENISA Threat Taxonomy
, . - BSI Threat catalogue
, (, , . .). - Open Threat Taxonomy
, JSON , . - US DoD Comprehensive Military Unmanned Aerial Vehicle smart device ground control station threat model
, . - VoIP Security and Privacy Threat Taxonomy
, VoIP. - Mobile Threat Catalogue
NIST, , . - ATT&CK
, . - -2.2-2009. « »
, .
. .- 51275-2006. . . , . General provisions
, . , . - , 2008 .
, , .
Source: https://habr.com/ru/post/351326/
All Articles