Malicious software to steal bitcoins spread through Download.com
If you ask an IT professional about basic security measures on the Internet, he will probably advise downloading software only from legitimate sites. It is a pity that this is not a panacea. We found three trojanized applications hosted on download.cnet.com - one of the most popular sites in the world (163 in Alexa ranking).

One of Malvari's victims was Crawsh, a user of subreddit / r / monero, but in his case the story ended well.
')
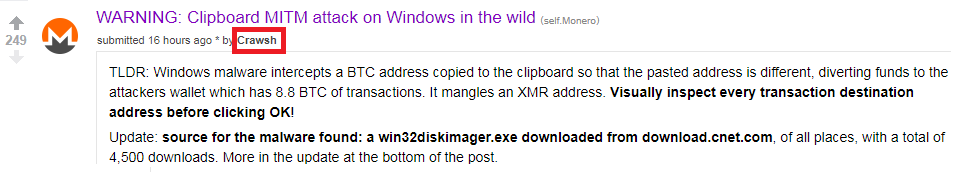
Crawsh suspected something was wrong when he tried to copy and paste the address of his Monero wallet to transfer funds there, and suddenly saw a message that the address was invalid. He decided to figure out what could be the cause of the error, and found out that the problem is in malware. Malvar intercepted the user's wallet address on the clipboard and replaced it with its own bitcoin wallet, which was hard-coded.
Fortunately for Crawsh, the attacker's address was intended for bitcoin transactions. The target application rejected Monero before the user transferred the funds. Unlike other victims working with bitcoins, their transfers were made without failures. To date, the attackers have collected 8.8 military-technical cooperation - about 4 million rubles (at the exchange rate for March 15).
“Almost injured” Crawsh wrote about the incident at Sabreddit / r / Monero. Post noticed in ESET and conducted an investigation to find out the circumstances of the infection and help potential victims.
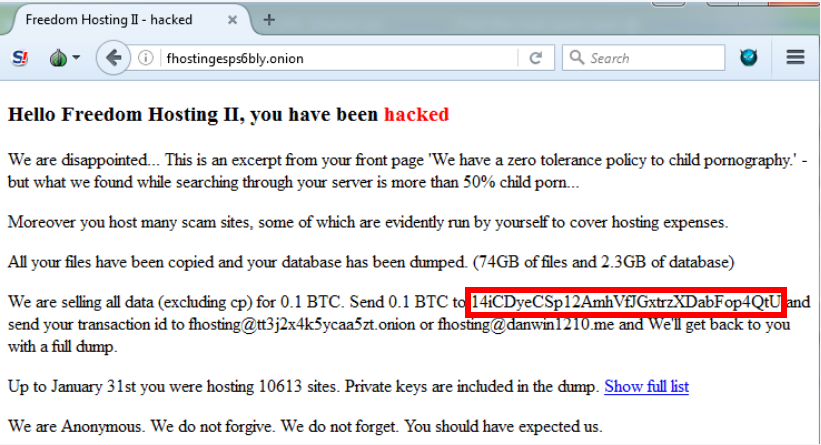
After checking the Google bitcoin address of the attackers, we found several victims. In particular, someone wrote a post about hacking a site (not associated with this malware). But in the text, the original Bitcoin wallet address has been replaced by the already familiar Bitcoin abductor address (see figure below). It is possible that the author of the post is faced with the same malware as Crawsh.
We found out that the Crawsh user’s computer was infected with a Trojanized Win32 Disk Imager application downloaded from download.com, where it was hosted since May 2, 2016.
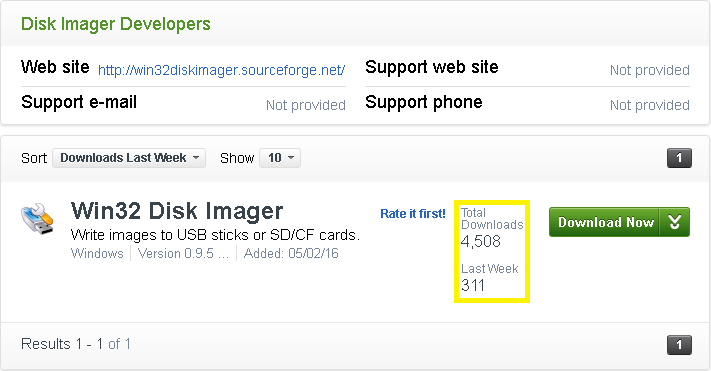
ESET anti-virus products detect this application as MSIL / TrojanDropper.Agent.DQJ. The program was downloaded from CNET 311 times just last week and more than 4500 times in total.
Later we discovered that Win32 Disk Imager is not the only trojanized application on download.com. Found at least two programs of the same authors. The first is CodeBlocks, it contains the same payload (MSIL / CLipBanker.DF) and is already blocked by CNET. CodeBlocks is a popular cross-platform development environment (IDE - Integrated Development Environment) based on open source code, it is used by many C / C ++ developers.

The second trojanized application is MinGW-w64, available for download at the time of the start of the study. Its payload includes malware to steal bitcoins and a virus. MinGW - compiler, software port GNU Compiler Collection for Microsoft Windows.
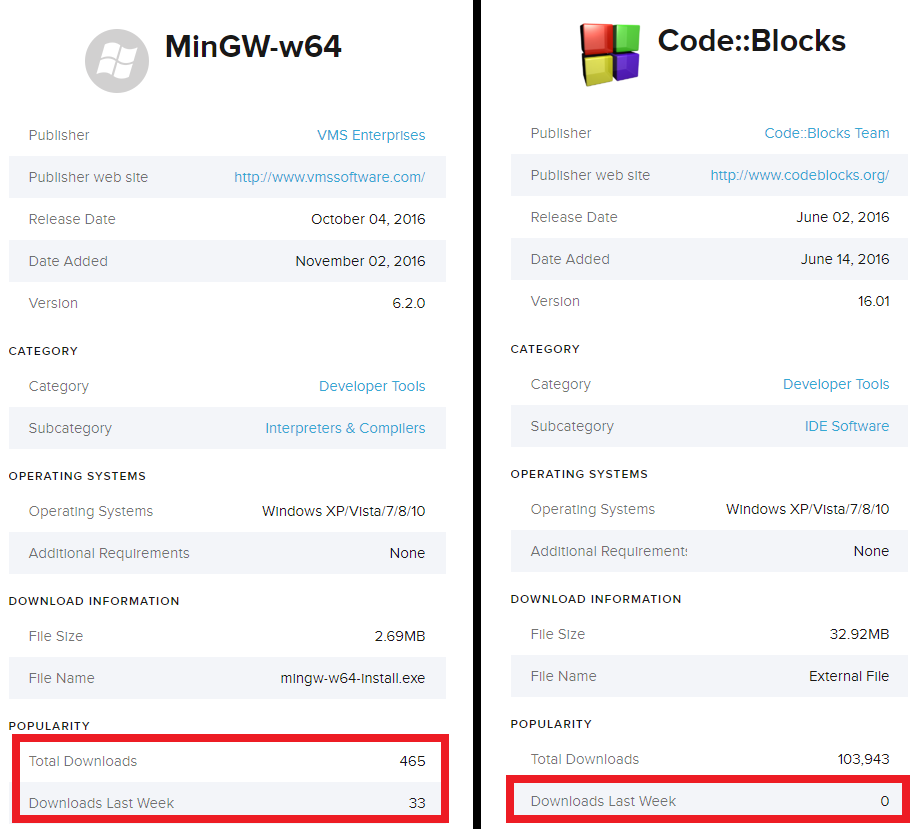
Below is the download statistics for these applications (information from download.com). Please note that the number of recent downloads of CodeBlocks is zero because the program has been removed by CNET. We do not know the exact date of removal, but, according to our telemetry, this could happen in March 2017.
After an ESET warning, CNET promptly removed malicious applications.
Troyanizirovanny dropper (MSIL / TrojanDropper.Agent.DQJ)
At the first stage, a simple dropper extracts the legitimate application installer (Win32DiskImager, CodeBlocks, MinGw) and the payload from the resources, saves both files to the% temp% folder and executes them.
Malicious software that replaces the addresses of the purses in the clipboard
1. MSIL / ClipBanker.DF
The Malvari payload resembles a dropper in terms of simplicity. The program copies itself to the path
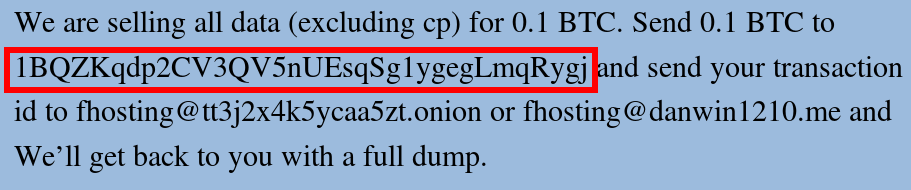
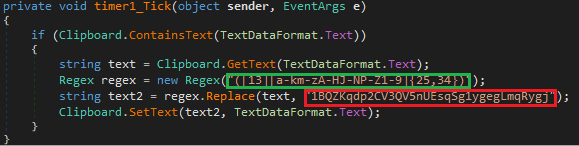
Replacing the address of a Bitcoin wallet is done with a simple code, which can be seen in the figure below. The code searches for a bitcoin address using a regular expression and replaces it with the address of a hard-coded wallets of attackers: 1BQZKqdp2CV3QV5nUEsqSg1ygegLmqRygj.
The attackers did not make any special efforts to conceal the activity, since even the path of the dropper debugging symbol and ClipBanker demonstrate their intentions. We believe that SF to CNET (see below) means SourceForce to CNET, since all three applications have clean instances in the source code repository.
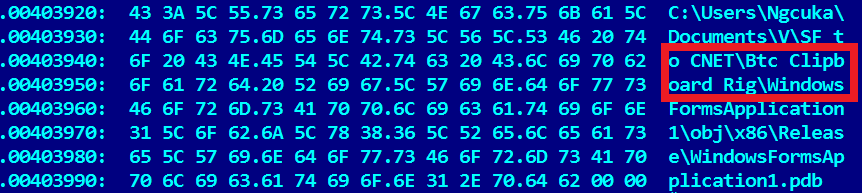
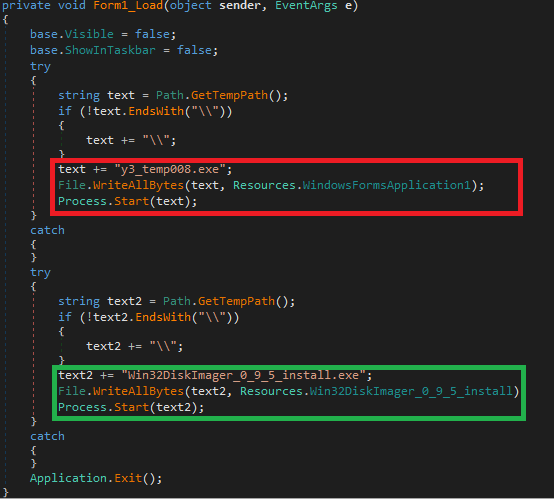
There are several additional infection indicators that victims can check. In particular, the payload and the trojanized packet are reset to% temp% under the names y3_temp008.exe and Win32DiskImage_0_9_5_install.exe, respectively, and are executed.
2. Win32 / ClipBanker.DY
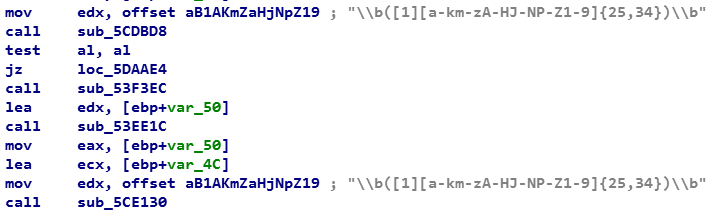
Malvari's payload is reset by the Trojanized MinGW-w64 application. This is a slightly more complicated variant, using a similar regular expression to search for a wallet:
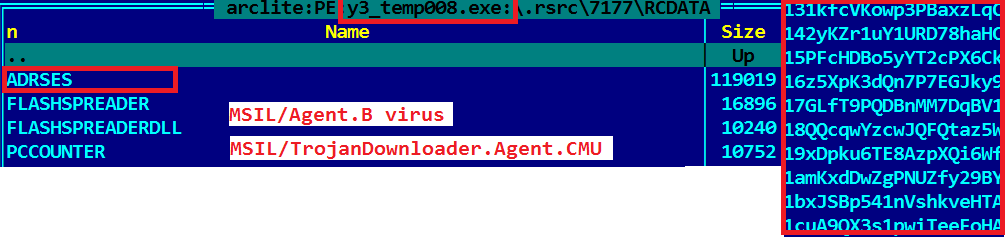
In addition, it contains additional malicious components, encrypted in resources, and about 3,500 addresses of bitcoin wallets (see figure).
The additional payload delivered along with malware to steal bitcoins also has a PDB path. One of them is
The username is identical to the name found in the PDB path of the first Malvari. Thus, we are sure that these malicious programs were developed by the same author.
- Remove the following downloaded installers: win32diskimager.exe (SHA1: 0B1F49656DC5E4097441B04731DDDD02D4617566); codeblocks.exe (SHA1: 7242AE29D2B5678C1429F57176DDEBA2679EF6EB); mingw-w64-install.exe (SHA1: 590D0B13B6C8A7E39558D45DFEC4BDE3BBF24918) from the download folder
- Delete the executable file in the% appdata% \ dibifu_8 \ folder (SHA1: E0BB415E858C379A859B8454BC9BA2370E239266)
- Delete the file y3_temp008.exe from the folder% temp% \ (SHA1: 3AF17CDEBFE52B7064A0D8337CAE91ABE9B7E4E3; C758F832935A30A865274AA683957B8CBC65DFDE)
- Delete the registry entry ScdBcd from HKEY_CURRENT_USER \ Software \ Microsoft \ Windows \ CurrentVersion \ Run
During the study, we reported a problem to CNET, and they promptly removed trojnized applications from the site, preventing the further spread of malware.
If you suspect your computer has been infected, install a modern anti-virus solution that automatically deletes files. The most effective measure of protection against spoofing the contents of the clipboard is double-checking addresses when performing transactions.
Triple applications:
win32diskimager.exe 0B1F49656DC5E4097441B04731DDDD02D4617566 MSIL / TrojanDropper.Agent.DQJ trojan
codeblocks.exe 7242AE29D2B5678C1429F57176DDEBA2679EF6EB MSIL / ClipBanker.EY trojan
mingw-w64-install.exe 590D0B13B6C8A7E39558D45DFEC4BDE3BBF24918 MSIL / TrojanDropper.Agent.DQJ trojan
ClipBankers:
mingw-w64 payload # 1 BE33BDFD9151D0BC897EE0739F1137A32E4437D9 Win32 / ClipBanker.DY trojan
mingw-w64 payload # 1 2EABFFA385080A231156420F9F663DC237A9843B Win32 / ClipBanker.DY trojan
mingw-w64 payload # 1 7B1E9A6E8AF6D24D13F6C561399584BFBAF6A2B5 Win32 / ClipBanker.DY trojan
codeblocks.exe payload E65AE5D0CE1F675962031F16A978F582CC67D3D5 MSIL / ClipBanker.AB trojan
win32diskimager.exe payload E0BB415E858C379A859B8454BC9BA2370E239266 MSIL / ClipBanker.DF trojan
URLs:
MinGW-w64: download.cnet.com/MinGW-w64/3000-2069_4-77411782.html
Win32 Disk imager: download.cnet.com/Win32-Disk-Imager/3000-2242_4-76554991.html
CodeBlocks: download.cnet.com/Code-Blocks/3000-2212_4-10516243.html

One of Malvari's victims was Crawsh, a user of subreddit / r / monero, but in his case the story ended well.
')

Crawsh suspected something was wrong when he tried to copy and paste the address of his Monero wallet to transfer funds there, and suddenly saw a message that the address was invalid. He decided to figure out what could be the cause of the error, and found out that the problem is in malware. Malvar intercepted the user's wallet address on the clipboard and replaced it with its own bitcoin wallet, which was hard-coded.
Fortunately for Crawsh, the attacker's address was intended for bitcoin transactions. The target application rejected Monero before the user transferred the funds. Unlike other victims working with bitcoins, their transfers were made without failures. To date, the attackers have collected 8.8 military-technical cooperation - about 4 million rubles (at the exchange rate for March 15).
“Almost injured” Crawsh wrote about the incident at Sabreddit / r / Monero. Post noticed in ESET and conducted an investigation to find out the circumstances of the infection and help potential victims.
After checking the Google bitcoin address of the attackers, we found several victims. In particular, someone wrote a post about hacking a site (not associated with this malware). But in the text, the original Bitcoin wallet address has been replaced by the already familiar Bitcoin abductor address (see figure below). It is possible that the author of the post is faced with the same malware as Crawsh.


Spread
We found out that the Crawsh user’s computer was infected with a Trojanized Win32 Disk Imager application downloaded from download.com, where it was hosted since May 2, 2016.
ESET anti-virus products detect this application as MSIL / TrojanDropper.Agent.DQJ. The program was downloaded from CNET 311 times just last week and more than 4500 times in total.

Later we discovered that Win32 Disk Imager is not the only trojanized application on download.com. Found at least two programs of the same authors. The first is CodeBlocks, it contains the same payload (MSIL / CLipBanker.DF) and is already blocked by CNET. CodeBlocks is a popular cross-platform development environment (IDE - Integrated Development Environment) based on open source code, it is used by many C / C ++ developers.

The second trojanized application is MinGW-w64, available for download at the time of the start of the study. Its payload includes malware to steal bitcoins and a virus. MinGW - compiler, software port GNU Compiler Collection for Microsoft Windows.

Below is the download statistics for these applications (information from download.com). Please note that the number of recent downloads of CodeBlocks is zero because the program has been removed by CNET. We do not know the exact date of removal, but, according to our telemetry, this could happen in March 2017.

After an ESET warning, CNET promptly removed malicious applications.
Analysis
Troyanizirovanny dropper (MSIL / TrojanDropper.Agent.DQJ)
At the first stage, a simple dropper extracts the legitimate application installer (Win32DiskImager, CodeBlocks, MinGw) and the payload from the resources, saves both files to the% temp% folder and executes them.

Malicious software that replaces the addresses of the purses in the clipboard
1. MSIL / ClipBanker.DF
The Malvari payload resembles a dropper in terms of simplicity. The program copies itself to the path
%appdata%\Dibifu_8\go.exe and adds an autorun key to the registry to ensure persistence.Replacing the address of a Bitcoin wallet is done with a simple code, which can be seen in the figure below. The code searches for a bitcoin address using a regular expression and replaces it with the address of a hard-coded wallets of attackers: 1BQZKqdp2CV3QV5nUEsqSg1ygegLmqRygj.

The attackers did not make any special efforts to conceal the activity, since even the path of the dropper debugging symbol and ClipBanker demonstrate their intentions. We believe that SF to CNET (see below) means SourceForce to CNET, since all three applications have clean instances in the source code repository.
C:\Users\Ngcuka\Documents\V\SF to CNET\Btc Clipboard Rig\WindowsFormsApplication1\obj\x86\Release\WindowsFormsApplication1.pdb
There are several additional infection indicators that victims can check. In particular, the payload and the trojanized packet are reset to% temp% under the names y3_temp008.exe and Win32DiskImage_0_9_5_install.exe, respectively, and are executed.
2. Win32 / ClipBanker.DY
Malvari's payload is reset by the Trojanized MinGW-w64 application. This is a slightly more complicated variant, using a similar regular expression to search for a wallet:

In addition, it contains additional malicious components, encrypted in resources, and about 3,500 addresses of bitcoin wallets (see figure).

The additional payload delivered along with malware to steal bitcoins also has a PDB path. One of them is
C:\Users\Ngcuka\Documents\V\Flash Spreader\obj\x86\Release\MainV.pdb .The username is identical to the name found in the PDB path of the first Malvari. Thus, we are sure that these malicious programs were developed by the same author.
How to clean the infected system
- Remove the following downloaded installers: win32diskimager.exe (SHA1: 0B1F49656DC5E4097441B04731DDDD02D4617566); codeblocks.exe (SHA1: 7242AE29D2B5678C1429F57176DDEBA2679EF6EB); mingw-w64-install.exe (SHA1: 590D0B13B6C8A7E39558D45DFEC4BDE3BBF24918) from the download folder
- Delete the executable file in the% appdata% \ dibifu_8 \ folder (SHA1: E0BB415E858C379A859B8454BC9BA2370E239266)
- Delete the file y3_temp008.exe from the folder% temp% \ (SHA1: 3AF17CDEBFE52B7064A0D8337CAE91ABE9B7E4E3; C758F832935A30A865274AA683957B8CBC65DFDE)
- Delete the registry entry ScdBcd from HKEY_CURRENT_USER \ Software \ Microsoft \ Windows \ CurrentVersion \ Run
During the study, we reported a problem to CNET, and they promptly removed trojnized applications from the site, preventing the further spread of malware.
If you suspect your computer has been infected, install a modern anti-virus solution that automatically deletes files. The most effective measure of protection against spoofing the contents of the clipboard is double-checking addresses when performing transactions.
Indicators of compromise
Triple applications:
win32diskimager.exe 0B1F49656DC5E4097441B04731DDDD02D4617566 MSIL / TrojanDropper.Agent.DQJ trojan
codeblocks.exe 7242AE29D2B5678C1429F57176DDEBA2679EF6EB MSIL / ClipBanker.EY trojan
mingw-w64-install.exe 590D0B13B6C8A7E39558D45DFEC4BDE3BBF24918 MSIL / TrojanDropper.Agent.DQJ trojan
ClipBankers:
mingw-w64 payload # 1 BE33BDFD9151D0BC897EE0739F1137A32E4437D9 Win32 / ClipBanker.DY trojan
mingw-w64 payload # 1 2EABFFA385080A231156420F9F663DC237A9843B Win32 / ClipBanker.DY trojan
mingw-w64 payload # 1 7B1E9A6E8AF6D24D13F6C561399584BFBAF6A2B5 Win32 / ClipBanker.DY trojan
codeblocks.exe payload E65AE5D0CE1F675962031F16A978F582CC67D3D5 MSIL / ClipBanker.AB trojan
win32diskimager.exe payload E0BB415E858C379A859B8454BC9BA2370E239266 MSIL / ClipBanker.DF trojan
URLs:
MinGW-w64: download.cnet.com/MinGW-w64/3000-2069_4-77411782.html
Win32 Disk imager: download.cnet.com/Win32-Disk-Imager/3000-2242_4-76554991.html
CodeBlocks: download.cnet.com/Code-Blocks/3000-2212_4-10516243.html
Source: https://habr.com/ru/post/351262/
All Articles