A study of cyber attacks in 2017: 47% of attacks are directed at the infrastructure of companies
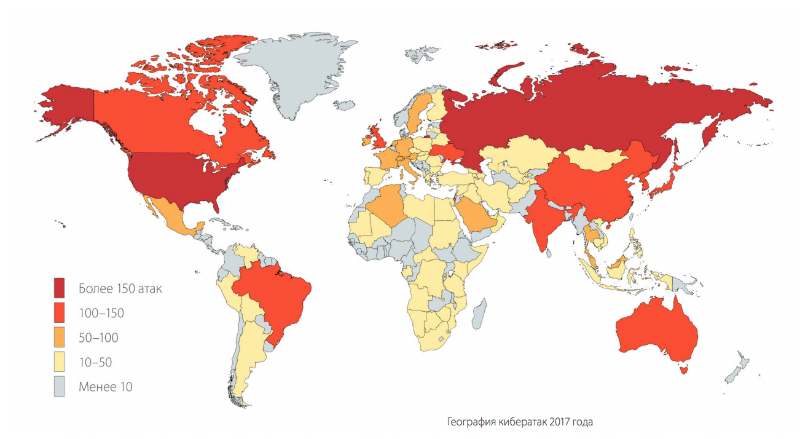
According to statistics collected by experts from Positive Technologies, infrastructure and web resources of companies became the most frequent targets of attacks in 2017, and among the main trends of the year experts call encryption Trojans, the development of the cyberservice market, attacks on banks, cryptocurrency exchanges and ICO.
The main trend of 2017 has undoubtedly become Trojan encryption. Moreover, as the analysis of the behavior of intruders showed throughout the year, the problem is not so much extortionists as the viruses that irrevocably encrypt data, thereby causing great damage to the infrastructure of companies.
')
While some are infected with “malware”, others are setting up their production. Due to the active promotion of the ransomware as a service, the same Trojans have been used repeatedly by different people, and the threshold for entering a cybercrime business is reduced, because anyone can now buy malware through the Internet. This means that the number of malicious campaigns will only increase.
Throughout 2017, the number of casualties among regular users also grew: if in the first quarter, analysts at Positive Technologies counted 21 unique incidents that resulted in private individuals, by the end of the year their number approached 100. Experts of the company also associate this fact with popularity ransomware as a service, since newcomers in cybercrime who are looking for quick money most often send purchased Trojans to private individuals. It is also worth noting that in 2017, ordinary users, in principle, were of the greatest interest to attackers: it’s 26% of all attacks.
The main motives of the attackers in 2017 were obtaining direct financial benefits (70%) and data theft (26%). The most stolen data were medical information and payment card data. At the same time, as experts note, although personal data continue to interest intruders, on the darknet they are no longer as valuable as they used to be.
The rush around cryptocurrency that had risen in 2017 and the significant increase in ICO’s popularity attracted intruders who launched attacks on cryptocurrency exchanges, private purses and ICOs. And while some registered cryptocars and transferred money to them, others devastated these wallets, for example, by selecting credentials.
The cybercriminals and the rapidly growing market of “smart things” did not go unnoticed. The compromise of credentials from IoT devices led to the fact that millions of routers, IP cameras, vacuum cleaners and other utensils were in botnets and are used for mining cryptocurrency, spying on people, DDoS attacks and other things.
During 2017, we witnessed an increase in the popularity of large-scale malicious attacks: while in the first half of the year, the proportions of mass and targeted attacks were approximately equal, by the end of the year, the majority were mass cyber attacks (57%). According to analysts of Positive Technologies, in the future such attacks will continue and evolve. At the same time, they will be aimed not only at making a profit, but also at a destructive impact. Malicious software turns into a real weapon that can lead to devastating consequences. If companies do not take the necessary measures to protect, then we can not exclude new loud targeted attacks using specialized malware.
Active Directory (AD) - the main goal of attackers during any attack on corporate information systems. Despite the increased proactive protection systems, professional pentesters and intruders are finding new attack vectors for AD. Now is just another round of the game: security vendors have learned how to detect brute-force and pass-the-hash attacks, and security researchers have developed a technique for creating a golden ticket based on NTLM hash. The appearance in January 2018 of DCShadow, a new attack technique on AD, and the statement of the authors of the attack “SIEM will not help you” became a challenge for every Blue Team.
During free webinar, which will be held on Thursday, March 15 at 14:00, Anton Tyurin, head of the team at the research of attack detection methods at Positive Technologies, will tell you how modern attacks on Active Directory work, how they can be detected in logs and network traffic and what can be done to reduce the number of vectors. Target audience of the performance: employees of SOC, Blue Team and IT-divisions.
To participate in the webinar you need to register .
Source: https://habr.com/ru/post/351228/
All Articles