Do I need to save data from employees
It is trite to write that company data and customer base are an asset of any business in the 21st century. But they still refer to this asset as a disregard: even a sales manager can easily divert part of the base and profitably sell it, optionally along with them. Corporate security is lame on both legs, and one could blame everything on Russian, but it was not the case - this is happening all over the world, from Moscow to Sydney. Employees and insiders revenge, earn on other people's data, simply harm the company for their own reasons. Of course, not everything and not always, but the frequency of events makes you dwell on the problem and outline a plan B.

Source sokoniafrica.com
Unfortunately, we can’t talk about the numerous security problems with which we have been meeting with our clients for the last 17 years - such information belongs to the NDA, and the possibility of breach of obligations is not even discussed. Our team RegionSoft Developer Studio decided to go the other way: we analyzed numerous sources and studies, summarized our experience without the names of specific companies, processed the information and put it into a post. Because trends, incidents, trends and the direction of threats - this is the basis on which we all need to learn. In the end, the smart learns from the mistakes of others.
How much is your data? “I’m SP, who needs my data!”, “Yes, we have only 2000 clients in the database, what a value!”, “But who needs all this, stop it” - quite common answers to this question. And let's consider the example of 2000 clients of a company selling office supplies for offices. The costs are minimal and rough: 4 sales managers - 50,000 each, online advertising - 20,000 per month (even if customers were attracted for a year), booklets - everyone once received 1 booklet with a production cost of 120 rubles. So, the company spent on 1440 to attract 1 client, that is, 2 880 000 rubles. Almost three million were invested only in the attraction, and in fact there are maintenance and retention. And then the company's manager quit and took away the customer base to competitors - after all, they were looking for a sales person with “business contacts”. Just for the salary received a ready-made warm base, which is enough to make a tiny discount or bonus to get loyalty. Who is guilty? Salesman? Sysadmin? No, the blame is for a manager who has not invested in protecting the most valuable asset of his business - the client base. (Or the second largest asset, because someone will say that the most valuable asset is people. Yes, of course it is, but not those who are willing to sell their boss if they offer acceptable remuneration for it.)
')
Now imagine what happens with large companies, because they are much more vulnerable due to more intense competition, more professional employees and more “tidbit” data. Companies of various sizes spend millions on external security and IT infrastructure protection, but at the same time lose sight of one of the most insidious threats - the danger of theft of internal and valuable commercial information by employees.
Data theft and corruption by corporate insiders is a big problem to be prepared for. Biscom found that 85% of employees are allowed to documents and information that they themselves have created, 30% are allowed to data that they did not directly create. In startups, especially safety-sensitive ideas and first valuable customers, the data show a high degree of connivance: 25% of employees have access to the source code and patent applications, 35% of employees have information about names, phone numbers and e-mail, 85% - have access and retain strategic documents and key business presentations. At the same time, 20% of employees openly stated that they are likely to take data and transfer it to competitors in case of negative circumstances of dismissal, and 90% noted that the main reason for data theft upon dismissal is the lack of information protection policies and technologies. In addition, in almost any company there is a sysadmin (regular or outsourced), which has full access to absolutely all corporate data. And as the peak of turretlessness can be considered maintaining a corporate database in the cloud, when almost no one has the ability to control the territorial distribution of users and the legitimacy of access to data.
So, who are they, robbers of corporate data? In principle, anyone: hackers, intruders, competitors ... But, of course, insiders play a major role in the theft of corporate information. In the comments to one of our articles there was a hot battle, in which it was proved that the system administrators were to blame for all that could be harmful. But there is one thing: yes, the sysadmin can inflict the most severe technical damage and work in the most sophisticated way, but the merchant will sell the data to competitors or in general on the open market. Just because he knows what to sell and to whom, what data is interesting for external agents, and what data is an empty set of numbers. So in the end, the financial damage from the offended admin is not so great (especially if you had protected from all backups made, for example, by another admin, outsourced company, vendor or the manager himself).
Insiders are not necessarily existing employees who came to work today at 9 am These are former employees, relatives of existing ones, partners, branch employees, clients with access to information, contractors, suppliers, consultants, and coaches. And it can be employees of absolutely any level - from the top manager to the junior specialist of those. support In general, the one who indirectly or directly has access to the client base, reports, financial information and personal data is your insider.
Verizon 2017 Data Breach Investigations Report
There are a number of signs that most often indicate that something went wrong. As a rule, the primary markers are completely invisible and understanding comes at a post factum, but several typical behaviors can be distinguished.
Basic hygiene in the field of corporate security - to learn to recognize the danger at the earliest stages. At the same time, it is not necessary to think that small or medium-sized businesses are not threatened - such companies, due to many factors, from salary to legal, are especially susceptible to provocations from within.
Data does not always flow away maliciously, but more often you have to think about the worst. Here are three main data paths outside the company's servers.

This is our CIO. For security reasons, it is encrypted.
So, it smelled of kerosene, outgoing money and Corvalol. It's time to start taking action. So what to do if a leak occurs? The main thing is to be discreet, reasonable and as quick as possible.
In the matter of corporate security, it is better to prevent than to prevent. Honestly, 100% protection will not give anything, there is always an unreliable technology or a corrupt person, there would be a desire to get your information. But this does not mean that you need to give up, decide "whether it will be" and let the security control take its course. The slightest measure of prevention reduces the risks, which means you need to work on ensuring security.
Here is a small checklist of measures that will allow you to protect corporate information.
As you can see, the advice is very simple, but the pathological greed and carelessness of company executives continue to bring tangible trouble to the business.

I’m sure there are better ways to disguise data, but we don’t have a large budget.
In this article, we pay special attention to the CRM system, not only because we are the developer of RegionSoft CRM and are aware of the importance of CRM in security, but also because today every company comes to the introduction of CRM sooner or later. And this means that it is important to use the program correctly so that it does not become a weapon against you.
Modern CRM systems include valuable data: the customer base itself, the sales funnel, product and service names, contract terms, documents, and much more, including financial information. Can you imagine how invaluable a competitor is to get all your customers who are at the decision-making stage? Got a base, made a tune-up, added a discount and collected the proceeds. That is, each customer record in CRM is overvalued, because it contains all relevant confidential information. This means that CRM should be protected as much as possible from insiders, greedy for profit.
CRM-system - safe your corporate information related to customers and transactions. In your power not to leave this safe open wide. Remember: any problem with data leakage from a CRM system is a direct threat not only to you, but also to your partners and customers.

Thus, I am not forced to spend all this money on a whim of cybersecurity
You can talk endlessly about security in the company - each of us has a failure story and a success story. We learn to trust employees, but we have to limit them. Security is associated with many material, financial, moral factors and is not always comfortable for all participants in the process. But if you keep the speed limit behind the wheel, what's the difference how many cameras and radars will take off your car? Probably, it is worth thinking of it all: both heads, and employees.
If you need a reliable powerful CRM, our site is waiting for you
 And we are already actively swinging our channel in the Telegram , in which, without advertising, we write not quite formal things about CRM and business. Come in, sometimes there is a light.
And we are already actively swinging our channel in the Telegram , in which, without advertising, we write not quite formal things about CRM and business. Come in, sometimes there is a light.

Source sokoniafrica.com
Disclaimer
Unfortunately, we can’t talk about the numerous security problems with which we have been meeting with our clients for the last 17 years - such information belongs to the NDA, and the possibility of breach of obligations is not even discussed. Our team RegionSoft Developer Studio decided to go the other way: we analyzed numerous sources and studies, summarized our experience without the names of specific companies, processed the information and put it into a post. Because trends, incidents, trends and the direction of threats - this is the basis on which we all need to learn. In the end, the smart learns from the mistakes of others.
Face of corporate rat
How much is your data? “I’m SP, who needs my data!”, “Yes, we have only 2000 clients in the database, what a value!”, “But who needs all this, stop it” - quite common answers to this question. And let's consider the example of 2000 clients of a company selling office supplies for offices. The costs are minimal and rough: 4 sales managers - 50,000 each, online advertising - 20,000 per month (even if customers were attracted for a year), booklets - everyone once received 1 booklet with a production cost of 120 rubles. So, the company spent on 1440 to attract 1 client, that is, 2 880 000 rubles. Almost three million were invested only in the attraction, and in fact there are maintenance and retention. And then the company's manager quit and took away the customer base to competitors - after all, they were looking for a sales person with “business contacts”. Just for the salary received a ready-made warm base, which is enough to make a tiny discount or bonus to get loyalty. Who is guilty? Salesman? Sysadmin? No, the blame is for a manager who has not invested in protecting the most valuable asset of his business - the client base. (Or the second largest asset, because someone will say that the most valuable asset is people. Yes, of course it is, but not those who are willing to sell their boss if they offer acceptable remuneration for it.)
')
Now imagine what happens with large companies, because they are much more vulnerable due to more intense competition, more professional employees and more “tidbit” data. Companies of various sizes spend millions on external security and IT infrastructure protection, but at the same time lose sight of one of the most insidious threats - the danger of theft of internal and valuable commercial information by employees.
Data theft and corruption by corporate insiders is a big problem to be prepared for. Biscom found that 85% of employees are allowed to documents and information that they themselves have created, 30% are allowed to data that they did not directly create. In startups, especially safety-sensitive ideas and first valuable customers, the data show a high degree of connivance: 25% of employees have access to the source code and patent applications, 35% of employees have information about names, phone numbers and e-mail, 85% - have access and retain strategic documents and key business presentations. At the same time, 20% of employees openly stated that they are likely to take data and transfer it to competitors in case of negative circumstances of dismissal, and 90% noted that the main reason for data theft upon dismissal is the lack of information protection policies and technologies. In addition, in almost any company there is a sysadmin (regular or outsourced), which has full access to absolutely all corporate data. And as the peak of turretlessness can be considered maintaining a corporate database in the cloud, when almost no one has the ability to control the territorial distribution of users and the legitimacy of access to data.
Who are they?
So, who are they, robbers of corporate data? In principle, anyone: hackers, intruders, competitors ... But, of course, insiders play a major role in the theft of corporate information. In the comments to one of our articles there was a hot battle, in which it was proved that the system administrators were to blame for all that could be harmful. But there is one thing: yes, the sysadmin can inflict the most severe technical damage and work in the most sophisticated way, but the merchant will sell the data to competitors or in general on the open market. Just because he knows what to sell and to whom, what data is interesting for external agents, and what data is an empty set of numbers. So in the end, the financial damage from the offended admin is not so great (especially if you had protected from all backups made, for example, by another admin, outsourced company, vendor or the manager himself).
Insiders are not necessarily existing employees who came to work today at 9 am These are former employees, relatives of existing ones, partners, branch employees, clients with access to information, contractors, suppliers, consultants, and coaches. And it can be employees of absolutely any level - from the top manager to the junior specialist of those. support In general, the one who indirectly or directly has access to the client base, reports, financial information and personal data is your insider.
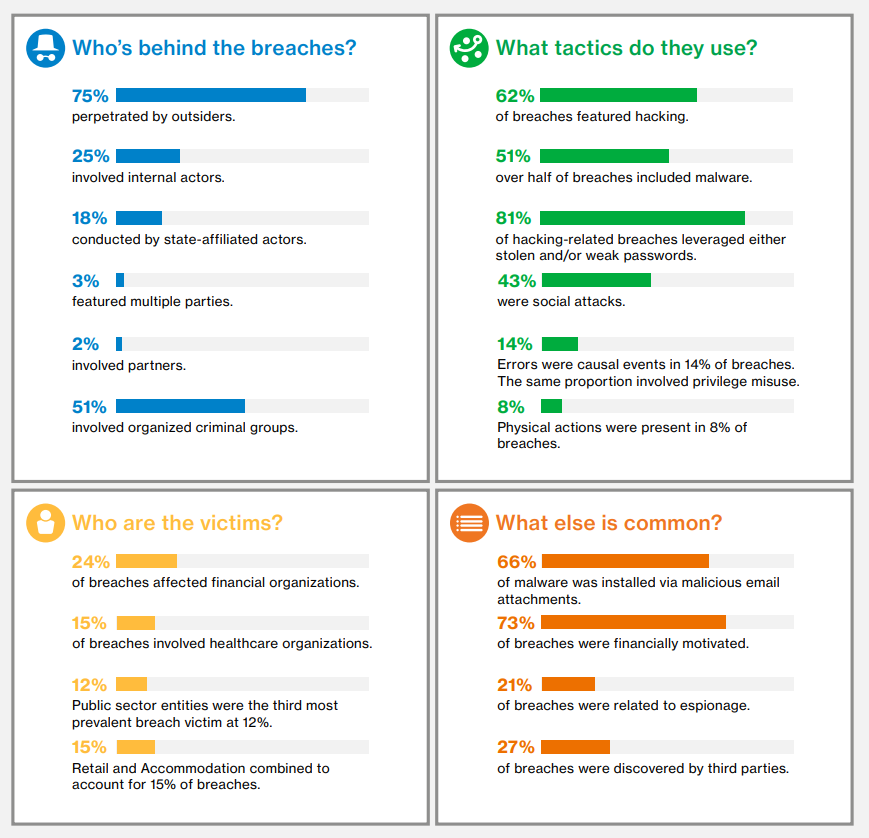
Harold Thomas Martin stole six valuable documents and a computer code from the US National Security Agency (NSA). Martin worked in a consulting firm that accompanies and maintains the NSA infrastructure, Booz Allen Hamilton. By the way, Edward Snowden once worked in it.The Verizon 2017 Data Breach Investigations Report reveals interesting corporate delinquency statistics. The same report showed that, apart from super-cyber-hacker-intrusions and old unkind DDoS attacks, problems with passwords, suspicious attachments in letters, negligence and physical theft did not disappear. By the way, 61% of all recorded violations occurred in companies with up to 1000 employees. Yes, it is logical - to hack or bribe someone from a small business is ten times easier than someone, for example, from a large retail. In this case, the client base can be quite profitable to sell.

Verizon 2017 Data Breach Investigations Report
Signs that should alert you
There are a number of signs that most often indicate that something went wrong. As a rule, the primary markers are completely invisible and understanding comes at a post factum, but several typical behaviors can be distinguished.
- Bulk export of customer and lead information in any form. These can be abnormal copying to external media, printouts, sending large volumes of letters and letters of large volumes, copying to cloud storages. Typically, this behavior can be detected in the CRM-system logs, as well as in IT infrastructure monitoring systems.
- The decline in labor activity. An employee who knows that he will soon leave the organization and will be able to immediately find a job or money will relax before leaving, because he knows that all deadlines and reports for the current month will pass without him. As a rule, this is very noticeable both at the level of ordinary colleagues and the head of the department.
- “Tidying up” in a working PC and network folders - if an employee who had not shown any zeal in cyber-cleaning suddenly starts cleaning files, copying the work he has done, removing important documents and disabling access to his shared folders, then most likely he preparing to disappear from the company. Of course, with the documents that he considers to belong to him, and not to the company - he worked so much on them (the fact that he received a salary for this work, he no longer remembers, because the memory is selective). This behavior is especially fatal when a programmer, analyst, or engineer leaves.
- Sudden, unusual and unmotivated processing and the appearance at work on weekends. If an employee almost never worked outside the office hours and suddenly began to linger or ask for access to the office for the weekend, he should look at it anyway. Even if he does not have malicious intent regarding the data, he may be overloaded with work or working on several personal projects (which may also lead to a “bad” dismissal, depending on the company's policy).
Basic hygiene in the field of corporate security - to learn to recognize the danger at the earliest stages. At the same time, it is not necessary to think that small or medium-sized businesses are not threatened - such companies, due to many factors, from salary to legal, are especially susceptible to provocations from within.
How can the data go?
Data does not always flow away maliciously, but more often you have to think about the worst. Here are three main data paths outside the company's servers.
- By chance. Today, each employee in the work process is faced with a dozen, if not one, of resources and sources: network storage, devices, clouds, corporate systems. It is impossible to track where a file donkey and stayed. Such leaks are almost safe - the data is either lost or ignored by a respectable former employee.
- False understanding of ownership - the employee thinks that everything he did belongs to him. This is a very common proposition that lies at the root of most problems. The employee faithfully believes that all his own needs to be taken with him, because it is done by his work. The fact that it was for this job he was hired for work, and for this work the wages were charged, usually forgotten.
- Malice - an insider finds a way to harm the company and steal data for reasons of revenge, care for competitors, desire to blackmail a manager, etc. As a rule, such actions always end in court. By the way, dear employers, remember - if you have taken a manager with data from previous work, expect that he will substitute you in the same way.

This is our CIO. For security reasons, it is encrypted.
It happened, what to do first?
So, it smelled of kerosene, outgoing money and Corvalol. It's time to start taking action. So what to do if a leak occurs? The main thing is to be discreet, reasonable and as quick as possible.
- Do not show it and prepare a plan for how you will investigate the incident. Consult with lawyers or security guards (if you have them), find out what documents and how you need to get and arrange to initiate a lawsuit. Try to do everything so that information about the discovery of an offense does not flow to the people - gossip instantly flies around the company, and the offender will have time to cover his tracks, disappear, or even “return as it was and become in no way”.
- Determine the location of the leak, find out what information, in what volume and through what channels could be transmitted. Change the security system, passwords, change account rights, make backups.
- Determine the purpose of the theft to minimize negative consequences. Find out who was the customer and accepted the information, build a chain of participants in the offense. If the data has not been transferred, start approaching the employee so that he does not have time to transfer it to the destination.
- Quickly collect all possible evidence: emails, browser history, call recordings, CRM system logs, ITSM system logs, employee activity records on a PC. Do all this as secretly as possible so that the employee does not suspect your intentions.
- If the information related to external partners, suppliers and other interested parties, immediately inform them about the discovery of the offense, so that they, for their part, can also minimize the risks, and may even help with the investigation (it’s like a thing - if the guys were in collusion, they can and prevent).
- As soon as you understand that you have a bag of evidence and the necessary information has been gathered, immediately cut off all the accesses to the employee and call him on the carpet. Even if it is your biggest pet, do not come from afar - the more you attack and charge, the more the insider realizes his level of responsibility and the faster the cards will be revealed.
- Next, discuss ways to return the data and correct the situation - perhaps the employee himself will tell you what to do in the framework of the motives that moved them. Encourage the employee to cooperate in the pretrial order, enter into a pretrial agreement with him, in which you clearly negotiate substantial penalties for possible insider activity after his dismissal from the company, notarize this agreement.
- Simultaneously with the start of negotiations, initiate the dismissal process.
- After the story is over, make the process public (but not humiliating!), Examine the causes, find the gaps, draw conclusions and finally fix the security holes.
Prevention decides
In the matter of corporate security, it is better to prevent than to prevent. Honestly, 100% protection will not give anything, there is always an unreliable technology or a corrupt person, there would be a desire to get your information. But this does not mean that you need to give up, decide "whether it will be" and let the security control take its course. The slightest measure of prevention reduces the risks, which means you need to work on ensuring security.
Here is a small checklist of measures that will allow you to protect corporate information.
- List policies with a clear delineation of access rights on the list of employees. Employees must clearly and unambiguously understand what information and with what rights can be used by them. Exactly the same as the fact that the work done and executed by them is the property of the company (roughly speaking, bought for wages).
- At the stage of recruitment, register separate agreements on trade secrets, access to information, NDA. The employee must become familiar with the documents and sign them simultaneously with the employment contract. Of course, a wolf and a few sheep steal, but possible legal consequences will significantly reduce negative aspirations.
Uber company for the development of business unmanned vehicles acquired startup Otto with the founder Anthony Lewandowski headed. By the end of 2017, Uber began to break into the lead of unmanned development, but at the same time, Uber's competitor, Waymo, sued the company for stealing corporate secrets. It turned out that the developer of Lewandowski, a former employee of Waymo, stole more than 14,000 confidential technical documents, drawings and other files before being fired from the company in order to use them in the very same startup that Uber had acquired. The company was faced with legal prosecution for using someone else's technology in the development of unmanned vehicles and for actively covering up the theft of trade secrets. The court was postponed several times while public hearings were being held, but it says a lot that the struggle is far from over 14,000 files, but for the right to develop a technology that, according to experts, will be as relevant to the global automotive industry as the invention of the car itself.
- When applying for a job, discuss the terms of use of equipment, especially portable. Differentiate the rights for business and personal gadgets (for example, prohibit the rolling CRM mobile application on a personal smartphone).
- Use specialized workflow software. So, the client base is best accumulated and stored in the CRM system (preferably hosted on your server and with the functionality of logging user actions, events, and the ability to set access rights).
- Monitor employee actions. No, it should not be paranoia in the form of a camera behind your back or a total keylogger, but it is imperative to monitor changes in IT infrastructure and extraordinary, anomalous events. For example, the suspicion of a system administrator (or security service) should cause copying or downloading large amounts of data, active copying or sending files at lunchtime or during before or after the working day interval.
- Make backups. This advice can be safely written in every article on Habré, and still they will be done either “already” or “not yet”. Backups are not some whim of a vendor or the head of a company, it is a saving on the consequences of negligence: the extortioner will not receive a single ruble, because there is a copy of all the data; vengeful admin quit with nothing - backups were protected; The salesman is in vain glad that he erased the entire customer base - it is securely reserved. Especially pay attention to the creation of backups, if you work with a cloud-based CRM system or another service - backups can be made under special conditions or only for a fee, this can be a surprise.
- Pay attention to the cloud technologies that you use in business. Working with them, the easiest way to forget is who has access to it and who has access to which accounts. Be sure to continuously monitor current access. The cloud generally relaxes - for example, many save passwords in the browser and do not log in with each login, but keep the application on a fixed tab. In addition, if your employee transfers his login from cloud CRM to competitors, you can find out about it only when you realize that all your customers have already closed deals with your competitors.
- Pay attention to what applications and services an employee uses on a working PC. Particular attention should be paid to cloud services with shared access (for example, Google Docs). It was repeatedly noted that employees continue to access files even after being fired. Moreover, if there are a lot of files (commercial offers, contracts, agreements, prices), it is almost impossible to cut off all access at once. Choose corporate equivalents with permissions and roles (for example, in RegionSoft CRM we have provided the ability to attach contracts, KPs and other files to the client card so that all documentation is stored in the central database on the company's server, and not rummaged in vain).
- Strictly prohibit employees from using personal email for login in business services, be it CRM or Google AdWords. An employee may not follow basic safety hygiene and compromise his e-mail, and there’s close to corporate systems.
- Develop a BYOD (Bring Your Own Device) policy for using personal devices and gadgets for business purposes and within the company. There was a case that one very large food company forced employees to put mobile phones in a drawer for the whole working day. This, of course, bend, reducing employee loyalty. But certain restrictive measures for developers, testers, sales managers, technical support specialists should be.
Another story is related to the elite plastic surgery clinic in Beverly Hills. The famous surgeon Zain Kadri hired an employee who first worked as a driver and translator, and then went on to work with data and phone calls. The girl was engaged in shooting medical patient records and information on their credit cards on a corporate smartphone (do you still remember that we are talking about Beverly Hills?). In addition, she took unethical photographs of patients before and during operations. The case is at the stage of investigation, the former employee already claims that she was driven by revenge, but there is a version that the case is in paid unfair competition.
- Make employees invent normal passwords, write masks for entering complex combinations, check if the password is hanging on the monitor and is not under the keyboard. This may seem very funny from the outside, but it is a significant security step.
A moment of beauty - the top worst passwords of 2017 from the report SplashData Worst Passwords of 2017
1 - 123456 (rank unchanged since 2016 list)
2 - password (unchanged)
3 - 12345678 (up 1)
4 - qwerty (Up 2)
5 - 12345 (Down 2)
6 - 123456789 (New)
7 - letmein (New)
8 - 1234567 (unchanged)
9 - football (Down 4)
10 - iloveyou (New)
11 - admin (Up 4)
12 - welcome (Unchanged)
13 - monkey (New)
14 - login (Down 3)
15 - abc123 (Down 1)
16 - starwars (New)
17 - 123123 (New)
18 - dragon (Up 1)
19 - passw0rd (Down 1)
20 - master (Up 1)
21 - hello (New)
22 - freedom (New)
23 - whatever (New)
24 - qazwsx (New)
25 - trustno1 (New)
Our personal favorites are trustno1, starwars and dragon. As you can see from the data in brackets, passwords are roaming by rating from year to year. And rightly we think that some employees of Russian companies are not far from this list.
After the dismissal of employees, delete their accounts, archive mail (do not delete - it can be useful both for business purposes and in possible proceedings), disconnect from instant messengers and group chats. There are examples where even after 3 years after leaving a company, employees retain access to the corporate portal, to CRM, and to numerous work services.
Banal and simple advice - inform employees about the possibility of leaks and burglary. Alas, due to ignorance of leaks, there is no less than due to malicious intent.
2 - password (unchanged)
3 - 12345678 (up 1)
4 - qwerty (Up 2)
5 - 12345 (Down 2)
6 - 123456789 (New)
7 - letmein (New)
8 - 1234567 (unchanged)
9 - football (Down 4)
10 - iloveyou (New)
11 - admin (Up 4)
12 - welcome (Unchanged)
13 - monkey (New)
14 - login (Down 3)
15 - abc123 (Down 1)
16 - starwars (New)
17 - 123123 (New)
18 - dragon (Up 1)
19 - passw0rd (Down 1)
20 - master (Up 1)
21 - hello (New)
22 - freedom (New)
23 - whatever (New)
24 - qazwsx (New)
25 - trustno1 (New)
Our personal favorites are trustno1, starwars and dragon. As you can see from the data in brackets, passwords are roaming by rating from year to year. And rightly we think that some employees of Russian companies are not far from this list.
After the dismissal of employees, delete their accounts, archive mail (do not delete - it can be useful both for business purposes and in possible proceedings), disconnect from instant messengers and group chats. There are examples where even after 3 years after leaving a company, employees retain access to the corporate portal, to CRM, and to numerous work services.
Banal and simple advice - inform employees about the possibility of leaks and burglary. Alas, due to ignorance of leaks, there is no less than due to malicious intent.
As you can see, the advice is very simple, but the pathological greed and carelessness of company executives continue to bring tangible trouble to the business.

I’m sure there are better ways to disguise data, but we don’t have a large budget.
How to secure in CRM
In this article, we pay special attention to the CRM system, not only because we are the developer of RegionSoft CRM and are aware of the importance of CRM in security, but also because today every company comes to the introduction of CRM sooner or later. And this means that it is important to use the program correctly so that it does not become a weapon against you.
Modern CRM systems include valuable data: the customer base itself, the sales funnel, product and service names, contract terms, documents, and much more, including financial information. Can you imagine how invaluable a competitor is to get all your customers who are at the decision-making stage? Got a base, made a tune-up, added a discount and collected the proceeds. That is, each customer record in CRM is overvalued, because it contains all relevant confidential information. This means that CRM should be protected as much as possible from insiders, greedy for profit.
- Choose a CRM system with built-in security mechanisms - at a minimum, it should be possible to differentiate user access rights.
- Try to choose a desktop solution - stealing data from CRM with a central repository on your server is much more difficult than in the cloud. In addition, your server is easier to protect with additional funds and control access to it.
- Monitor employee actions in the CRM system: the program should be able to log actions, log processes and events, etc. You can always determine who downloaded the reports, uploaded the lists of clients, performed certain actions.
- Give access to the CRM system only to those employees who really need it to work. Do not allow employees to freely and without the need of business to view the lists of clients of other employees.
- New employees are granted access gradually, it is not necessary to immediately open all the functionality - let us give full rights in accordance with official duties only after the completion of the trial period.
- Whenever possible, use data encryption. Even an elementary transfer of important files in archived form with a simple password will ensure minimal security.
CRM-system - safe your corporate information related to customers and transactions. In your power not to leave this safe open wide. Remember: any problem with data leakage from a CRM system is a direct threat not only to you, but also to your partners and customers.

Thus, I am not forced to spend all this money on a whim of cybersecurity
You can talk endlessly about security in the company - each of us has a failure story and a success story. We learn to trust employees, but we have to limit them. Security is associated with many material, financial, moral factors and is not always comfortable for all participants in the process. But if you keep the speed limit behind the wheel, what's the difference how many cameras and radars will take off your car? Probably, it is worth thinking of it all: both heads, and employees.
If you need a reliable powerful CRM, our site is waiting for you
Source: https://habr.com/ru/post/351196/
All Articles