How to notice DDOS in time: a monitoring service usage scenario for early detection
The first step in the fight against DDOS is to notice it. It is especially important to find out about him in the early stages, when he had not yet turned to full capacity, because then even for an administrator, access to the server can be significantly hampered. Below we offer several methods for early detection of DDOS using the HostTracker site monitoring service .
The reason for writing this article was the real story of a single client who was regularly subjected to DDoS and needed a tool to diagnose it.

So, someone started ddosit you. Or there are prerequisites for this. What to do? The best option, of course, is to buy the services of some kind of “shield”, for example, CloudFlare. But not everyone can afford it, besides ddos are very different in intensity and duration. That is, the task "notice" is still not removed.
')
Rough. It is precisely for the site to stop working. It is very easy to catch using the most common web site monitoring . We check the site with one of the tools available on the market - we get an error message - we react. Simple and reliable. But it may be late. In the same way, you can monitor the availability of a specific port or application (for example, a database).
Thin. DDoS does not start instantly at full capacity. Step by step, connect the new server botnet. Therefore, the site first starts to slow down a bit. Then - a lot. And only then falls. These brakes can be caught using the response time monitoring feature. For this, it is necessary to experimentally find out what the response time is normal (you can still optimize it, but this is another story ), and then set the threshold a little higher.
Even thinner. In addition to the response time, DDoS of course noticeable "from the inside." By installing a simple script on your server, you can very quickly find out that the use of a CPU or some other internal parameter has suddenly increased:
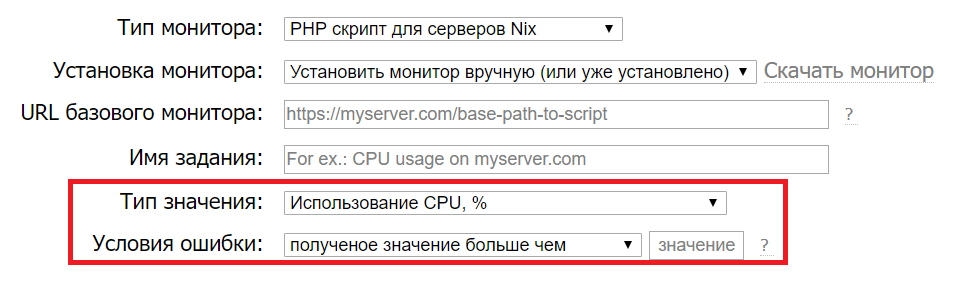
A quick response, while it is still possible to connect to the server remotely, can save the situation.
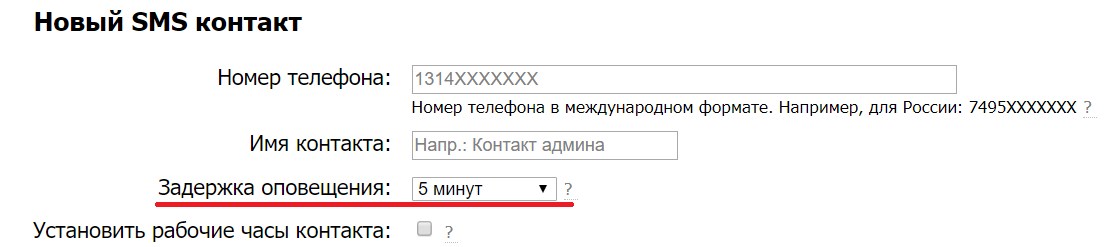
Rejecting transient triggers. There are various ways to automatically suppress DDoS. But, as a rule, they also have their own threshold of sensitivity. The start of a ddos may be missed, but when it is already fully developed, start banning to the left and to the right. So, if you adjust the above-mentioned methods of detecting ddos, you can get an alert, get to understand, and then find out that the automation still worked and the nerves could be saved. To prevent this from happening, in such cases we recommend setting an alert delay. Thus, you will only learn about the problems that do not pass by themselves. This method can also filter out other short-term problems:
If you do everything at the same time, you can get an almost perfect picture of what is happening. Separate network lags from server bugs, site glitches and database brakes. And of course, with almost 100% chance of being sure if it is DDOS or not. Something like this is a comparison of the availability of different monitored resources:

Well, you can always make an additional page with a widget on your site, so that anyone can monitor the system status in real time.
As mentioned above, the reason for writing the article was the correspondence with the client, the problem of which we helped to solve. Most of our functions are designed to respond to requests from customers or well-wishers. Therefore, we will be grateful for the suggestions and constructive criticism.
The reason for writing this article was the real story of a single client who was regularly subjected to DDoS and needed a tool to diagnose it.

So, someone started ddosit you. Or there are prerequisites for this. What to do? The best option, of course, is to buy the services of some kind of “shield”, for example, CloudFlare. But not everyone can afford it, besides ddos are very different in intensity and duration. That is, the task "notice" is still not removed.
')
How to do it?
Rough. It is precisely for the site to stop working. It is very easy to catch using the most common web site monitoring . We check the site with one of the tools available on the market - we get an error message - we react. Simple and reliable. But it may be late. In the same way, you can monitor the availability of a specific port or application (for example, a database).
Thin. DDoS does not start instantly at full capacity. Step by step, connect the new server botnet. Therefore, the site first starts to slow down a bit. Then - a lot. And only then falls. These brakes can be caught using the response time monitoring feature. For this, it is necessary to experimentally find out what the response time is normal (you can still optimize it, but this is another story ), and then set the threshold a little higher.
Even thinner. In addition to the response time, DDoS of course noticeable "from the inside." By installing a simple script on your server, you can very quickly find out that the use of a CPU or some other internal parameter has suddenly increased:

A quick response, while it is still possible to connect to the server remotely, can save the situation.
Rejecting transient triggers. There are various ways to automatically suppress DDoS. But, as a rule, they also have their own threshold of sensitivity. The start of a ddos may be missed, but when it is already fully developed, start banning to the left and to the right. So, if you adjust the above-mentioned methods of detecting ddos, you can get an alert, get to understand, and then find out that the automation still worked and the nerves could be saved. To prevent this from happening, in such cases we recommend setting an alert delay. Thus, you will only learn about the problems that do not pass by themselves. This method can also filter out other short-term problems:

And if all combine?
If you do everything at the same time, you can get an almost perfect picture of what is happening. Separate network lags from server bugs, site glitches and database brakes. And of course, with almost 100% chance of being sure if it is DDOS or not. Something like this is a comparison of the availability of different monitored resources:

Well, you can always make an additional page with a widget on your site, so that anyone can monitor the system status in real time.
As mentioned above, the reason for writing the article was the correspondence with the client, the problem of which we helped to solve. Most of our functions are designed to respond to requests from customers or well-wishers. Therefore, we will be grateful for the suggestions and constructive criticism.
Source: https://habr.com/ru/post/351006/
All Articles