About the book "Ensuring the safety of automated process control systems in accordance with modern standards"

How to ensure the functional component of security management systems? What is the difference between functional security and information security, and which of them is “more important”? Does it make sense to certify compliance with standards? I tried to share my experience in solving these and other issues with the community when I started publishing a series of articles on Habré a year and a half ago. During this time, something more happened in a series of articles.
The other day the publishing house Infra-Engineering published my book "Securing the safety of automated process control systems in accordance with modern standards . " The format of the annotation on the publisher's site provides only a few lines, so I decided to share with the readers the main ideas and the detailed content of the book.
A look at security in the book is directed from the point of view of the functional component. However, where appropriate, the link between information security (IS) and functional security (FB) is demonstrated. For example, a single structure of requirements for information security and security is considered, as well as a single life cycle of information security and security. In addition, the methods of providing security engines that simultaneously increase the level of information security are considered. As experts in the field of security, it is this focus that is most useful for them.
')
To certify or not to certify? This question often arises at certain stages of product development. Many “against” are understandable, but I will nevertheless dwell on the arguments “for”. Despite the bureaucratic and confusing language of standards, they nevertheless reflect the modern technical level, contain time-tested requirements and best practices. Even a simple analysis of the compliance of products and processes of the company with the requirements of the standards allows us to reflect on the identified inconsistencies, and, possibly, outline ways to improve the quality and maturity, manageability and efficiency of the processes and results of development. In this case, it is not necessarily about obtaining an expensive certificate, which, however, can open the doors to new markets. Many of the work on the assessment of compliance with the requirements of the standards can be carried out at the expense of the company's internal resources. I personally observed several times how such activities brought employees and companies to a new professional level. Therefore, the study of the requirements of the standards and the attempt to meet them, clearly, make sense, and for a number of products related to security, are crucial.
This book is a step-by-step guide describing the complete process of certification of computer control systems (APCS and others) and their components for compliance with the requirements of the International Electrotechnical Commission (IEC) 61508 “Functional safety of electrical / electronic / programmable electronic systems”. In addition to IEC 61508, the book will help in understanding the entire family of derived standards for functional safety, including IEC 61511 "Functional safety - Safety instructed systems for the process industry sector", IEC 62061 "Safety of machinery: Functional safety of electrical, electronic and programmable electronic control systems ", IEC 61513" Nuclear power plants - Instrumentation and control for systems important to safety ", ISO 26262" Road vehicles - Functional safety ", EN 50129" Railway Industry Specific - System Safety in Electronic Systems ", IEC 62304" Medical Device Software ".
To solve the main practical task of preparing and passing certification, the material is grouped into the following sections, which describe the main stages of this process (see figure). Under the spoilers - a summary of the sections of the book.
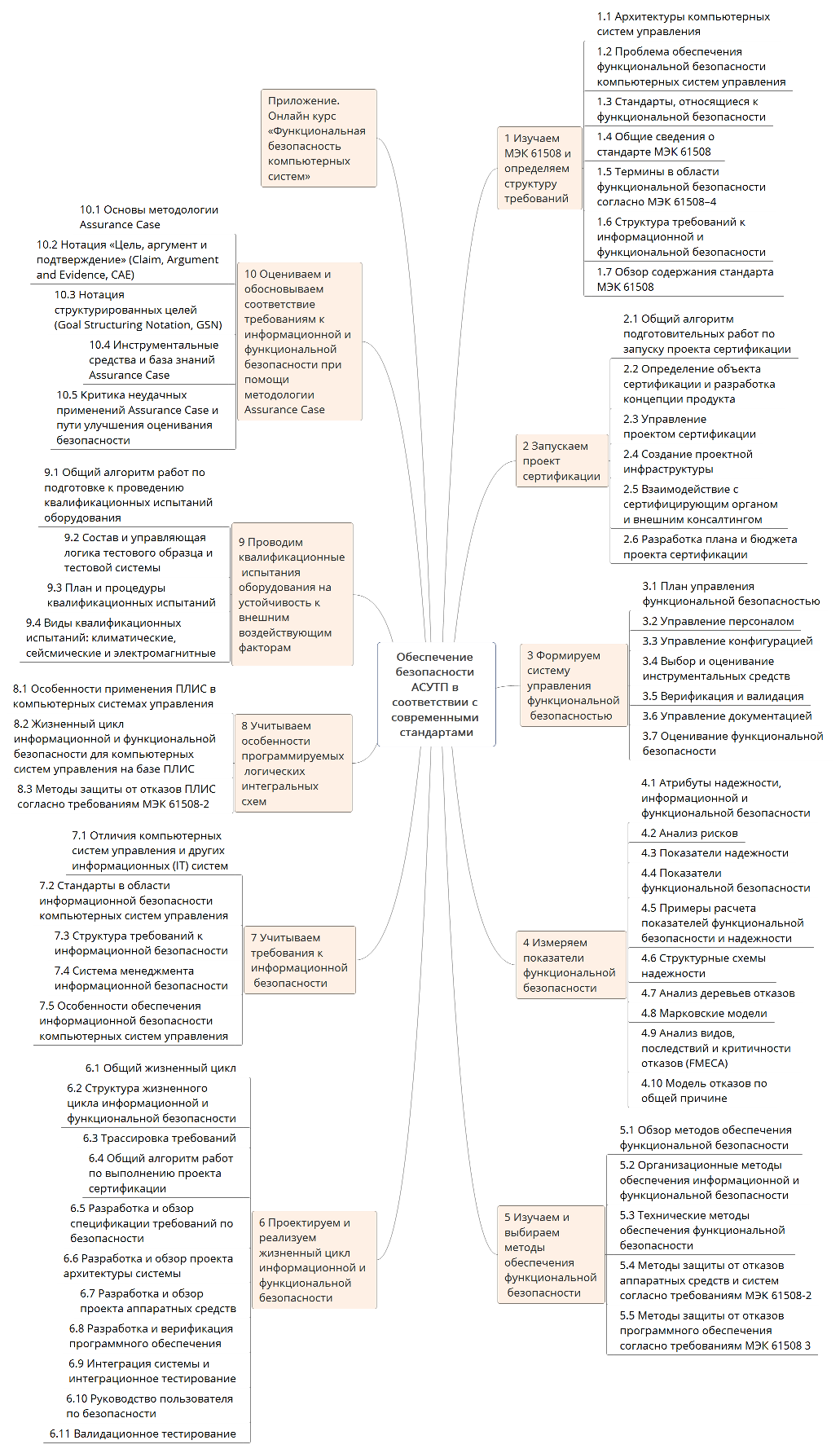
Section 1
Section 1. “Studying IEC 61508 and defining the structure of requirements” contains a brief description of computer control systems architectures (LCP) for which the requirements for the PB are applicable. These architectures include: embedded systems, automated process control systems, systems based on the Internet of Things technology. The risks arising in the course of the KSU functioning, as well as a list of standards containing requirements for FB and aimed at reducing the emerging risks are considered. Next, an analysis of the structure, concept and terminology of the IEC 61508 series of standards was carried out and a harmonized structure of requirements for information security and security technologies was proposed.
Section 2
Section 2 “Launching a Certification Project” is unique because it is dedicated to the organizational component of KSU certification and their software and hardware components for compliance with the requirements of the FB. This topic has not been addressed in well-known publications on the FB, and it is precisely thorough preparation for the project that is the key to its successful completion. The section is based on an algorithm of actions tested in several similar projects in preparation for certification, including determining the object of certification, developing a product concept, creating a project infrastructure, developing a work plan, and establishing contacts with an independent certification organization. Particular attention is paid to the economic model, which allows to determine the cost estimates for the implementation of the certification project.
Section 3
Section 3, “Formulating a Functional Safety Management System,” discusses a group of requirements related to the management of security facilities, including personnel management, selection and evaluation of tools, evaluation of security facilities and other processes.
Section 4
Section 4 “Measuring Functional Safety Indicators” considers aspects of the FB’s quantitative assessment as part of the reliability theory. The attributes of information security and security, types of security indicators and their specified values are considered from the point of view of IEC 61508 requirements. Methods for calculating security indicators, such as structural reliability schemes, fault trees, Markov models, analysis of types, consequences and criticality of failures, are considered. Examples of the calculation of indicators FB are given.
Section 5
Section 5 “Learning and choosing methods for ensuring functional safety” is based on the list of methods given in IEC 61508. The methods are divided into organizational and technical. The requirements of IEC 61508 to the choice of methods for protection against failures of hardware and software components are considered.
Section 6
Section 6, “Designing and Implementing the Life Cycle of Information and Functional Security,” discusses a group of requirements related to the structure of the life cycle and the content of its stages. A unified life-cycle structure is proposed in terms of compliance with the requirements for both information security and security. For the stages of the life cycle, the actions performed, the composition and structure of the documents produced, the verification and validation methods used, the provision and evaluation of the FB are considered. An approach to performing trace requirements is described. This section is central because it contains an algorithm for work on the implementation of a certification project, linking together all sections of the book.
Section 7
Section 7, “Considering Information Security Requirements,” discusses the specifics of the LCP from the point of view of the interrelationship of the IS and FS processes. The practical focus of this section is to optimize the cost of integrated coordinated security and security services, when the same methods are used simultaneously for both security services and security forces.
Section 8
Section 8 “Considering the features of programmable logic integrated circuits” considers the use of FPGAs as components of the LCP, as well as the associated aspects of certification for compliance with the requirements for the FB.
Section 9
In Section 9 “We conduct qualification tests of equipment for resistance to external influencing factors”, an algorithm is proposed for preparing for this type of testing. The approach to the development of the composition and functions for the test sample KSU, as well as typical functional tests performed to verify the correctness of the functioning are considered.
Section 10
Section 10. “Evaluating and justifying compliance with the requirements for information and functional security using the Assurance Case methodology” is devoted to a methodology that allows collecting all the artifacts of a certification project into a single system and, thus, most effectively confirming compliance with the requirements for the FB.
application
The Appendix “Online course“ Functional safety of computer systems ”contains links to the author’s YouTube channel , which contains video-playlists that are part of a mass open online course (Massive Online Open Course, MOOC).
Each section, in addition to theoretical material, also contains:
- conclusions, briefly summarizing the main provisions of the section;
- A list of recommended literature, supplementing the material of this book in various aspects;
- a list of test questions that should be worked out to verify the assimilation of the material;
- practical tasks for the implementation of measures aimed at ensuring compliance with the requirements of the FB; performing the recommended practices, your organization will move closer to certifying processes and products important to safety.
The book can be used as a tool for a series of trainings in which students learn the requirements of IEC 61508 and then learn how to put processes into practice, develop products and documentation that meet these requirements. In addition, this book can be used in universities as the basis for lecture material and practical work in the study of disciplines related to the security of KSU.
The peculiarity of the book is that the drawings and part of the tables are prepared in English. This is done because the material is based mainly on English-language primary sources, and therefore the translation of terms and illustrations is difficult, and the translation of specific terminology into Russian is still not smooth.
It is assumed that the reader has basic knowledge in such areas as electronics, architecture of the control system and programmable logic controllers (PLC), programming, information security, probability theory and reliability theory.
How was the work on the book? It was based on experience gained in 20 years of work, primarily in the nuclear power industry, as well as for the aerospace industry, the oil and gas and coal industries, railway transport, fire safety, and thermal energy. The result of this activity are dozens of successfully completed certification and licensing projects. Embedded systems continue to operate safely and securely in Argentina, Bulgaria, Brazil, Canada, France, Russia and Ukraine.
In my opinion, the geography of the creation of the book is interesting. After the decision to move to a remote work format, in 2016-2017. I wrote a series of articles on functional safety and a distance course on the same topic, being at this time in Goa, India. The main work on the layout of the book was done in the Indian Himalayas in the summer of 2017. I completed the final edition of the book and the negotiations with the publisher, already in Cambodia.
I want to thank the staff of the publishing house Infra-Engineering and its CEO, Kirill Uvarov, for their fast and high-quality work on publishing.
Infra-Engineering is perhaps the only Russian-language publishing house that publishes technical literature on reliability, security, technical diagnostics, software quality assurance, etc. ( series "Automation" ). It was here that the "Handbook of an Engineer for Industrial Process Control Systems: Design and Development" by Yu.N. Fedorov , who became for many a reference book. In addition, the publishing work professionals who are pleased to deal with.
In conclusion, I wish you all useful books and professional growth!
PS Link to the book on Labyrinth.ru
Source: https://habr.com/ru/post/350664/
All Articles