Eternally Open Sesame, or Several Loopholes in Your IT Landscape

The furious vulnerabilities like EthernalBlue or Heartbleed attract a lot of attention to themselves, fueling the idea that the main thing is timely patching of system software. However, not everyone remembers that critical configuration defects are found no less often and are not always corrected by simply installing updates.
I would like to speak about several of these security flaws, since they are found at every second (if not the first) customer and have not been corrected for years.
Letter from the director
Social engineering is the No. 1 problem, because it is badly curtailed by traditional protection measures. It is possible to teach employees of the company to be wary of unexpected emails, but when it comes to specialists who receive dozens of emails per day from various senders, it is difficult to expect a good result.
Take a look at your SMTP server. With high probability, it processes mail without sender authentication. This is not about mail traffic, through which tons of spam are sent to the outside - this is almost never encountered. Here is another kind of problem: anyone can connect to your mail server from the outside and without authentication send an email to any local user. In this case, the sender's address can be arbitrary - external or internal. Want to send an email on behalf of IT support? There is nothing easier:
')
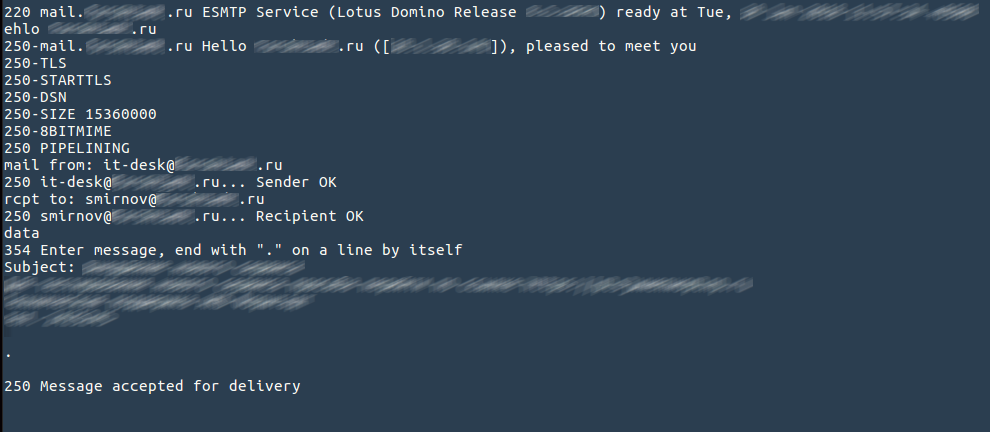
But even if the address of the local sender is unknown, you can try to pick it up, since in most cases the mail server checks whether there is a local user on whose behalf correspondence is sent.
Attack scenario is trivial. By exploiting a deliberately high trust of the victim to the author of the letter: the attacker forces the victim to open the attached file or follow the link. Cheating antivirus software today is a matter of technology. Most antiviruses confidently catch files containing code that exploits known vulnerabilities, and only a few are able to cope with customized code. High secrecy of malicious code can be achieved by using obfuscators and encoders (such as Pyherion), which “hide” suspicious chains of instructions from analytical engines. To overcome sandboxes and other advanced behavioral analyzers, timers are added to the code, which set delays during which the running process shows no activity in the system, and many other tricks. Attackers are often one step ahead of the manufacturers of protective equipment, because they have the opportunity to prepare and test their customized malware without any risk.
In practice, this allows in 8 cases out of 10 to get a valid backdoor at the user's workstation.
Defenseless network
A well-segmented network with strict access lists is often found on internal pen tests. Additional measures to protect administrative accounts (for example, LAPS technology) limit the potential of attacks aimed at extracting account details from OS memory of compromised hosts running Windows. Sometimes hosts are protected so well that an attacker needs to look for attack vectors at the application level or in the network infrastructure. The latter is found frighteningly often. Let us give an example of a common security hole typical of networks built on Cisco equipment.
The essence of the problem is that the Cisco Smart Install (SMI) service in most modern Cisco Catalyst switches allows you to change the device configuration without authentication. The SMI service is designed for the initial configuration of network devices, so it is enabled by default on many switch models. Moreover, in some cases it cannot be disabled (for example, on the Catalyst 6500 Series with IOS version 15.1 (2) SY11, 15.2 (1) SY5, 15.2 (2) SY3), and the only protection measure is the use of ACL.
Check port 4786 / tcp on your Cisco networking equipment. With high probability you will find a working service on it.
It is wrong to consider SMI a rudiment of the past - with time new functions were added to it. Starting with IOS 15.2, the ability to run post-install scripts in enable mode has been added, and this still does not require authentication. The configuration upload / download procedure is available on all versions of IOS.
Due to the possibility of obtaining and modifying the configuration of a network device, there are ample opportunities for attacks on the network: starting with disclosing administrative details and intercepting network traffic, ending with redrawing access lists and including any VLAN present on the remote switch. If the network device is bordered by the protected network segment, its capture will mean an intruder has entered the protected segment.
Manage can not be banned
Group Policy, which is one of the pillars of the AD directory service, allows administrators to implement a number of configuration scripts that require account credentials. The configuration of such policies is stored in XML files in the SYSVOL directory of the domain controller and is available to all participants. The problem is that the passwords of the accounts specified in the policy are stored in the cpassword attribute in an encrypted form, while the encryption key is publicly known and cannot be changed. Thus, any domain member can retrieve and decrypt the password values of user accounts stored in the following files:
- groups.xml
- scheduledtasks.xml
- services.xml
- datasources.xml
Obviously, in most cases, accounts stored in this manner have administrative privileges.
In 2014, Microsoft released security fixes KB2928120 / KB2961899, which prohibit storing user names and passwords in the Group Policy setting. However, forcibly disabling or changing existing policies did not dare. Yes, it is no longer possible to create new Group Policy settings containing user credentials, however, the previously created settings continue to act, warning at every opportunity the domain administrator with a message like:

Microsoft has offered administrators workarounds and alternative ways to implement domain configuration scripts, but in most cases has not been heard.
Summary
Much of the critical security issues cannot be fixed only by installing patches. Standards for configuring information system components are an effective and cheap protective measure that should not be neglected. In their absence, it remains to rely only on expensive detection measures: integrity monitoring, detection of behavioral abnormalities and suspicious traffic.
Andrei Zakharov, Head of Information Security Jet Infosystems Center Group
Source: https://habr.com/ru/post/350622/
All Articles