Cybersecurity for drivers: how to avoid cyber attacks on connected cars?
In early January, the most serious global risks of 2018 were voiced at the World Economic Forum in Davos. The four, immediately after the risks associated with extreme weather events, natural disasters and environmental degradation, included cyber attacks. Today they cause the greatest concern among entrepreneurs in countries with developed economies. Cybersecurity concerns stem from people's dependence on digital technology. By 2020, experts expect that humanity will use 20 billion connected devices, which certainly expands the possibilities for cyber attacks. Today, Bright Box CISO by Nikolay Agrinsky talks about how to avoid cyber attacks on your connected car and how to protect customers of automakers and car dealers.
Cars ceased to be physically independent of communications and networks at the end of the 20th century , and as the capabilities of the so-called connected cars expanded, the potential for cyber attacks increased. Today, issues of development of IT technologies are not considered without considering this problem.
')
The Internet has changed the way you work with a computer, as connection today changes the car as a whole and the road environment. When personal computers began to enter our lives, malware was a major information security problem. A computer virus could lead to data corruption, and sometimes damage the computer itself. Nobody thought about data theft or misuse of technology. The communication channels were very slow, and only “favorites” could connect to the Internet or other networks. At that time, the worst thing that could happen was buying a new computer if the old one was damaged. But as soon as the Internet became available, and the cost of equipment decreased, the situation changed. Viruses, of course, remained a very unpleasant event, but we already fear not the purchase of a new computer, but the loss of our data, disruption of the work of critical systems on which our life depends.

The same thing happens with the car today. Previously, the car owner was puzzled only by saving his own car - no one wants to find under the windows the absence of a recently purchased vehicle. But as soon as the car was connected to the network, everything changed, a number of additional threats, no less weighty than theft, were revealed.
The main and most serious if a cyber attack is committed is the threat to the driver’s life. In 2015, Chrysler recalled 1.4 million vehicles after a couple of hackers demonstrated to WIRED that they could remotely monitor the Jeep system via the Internet. Hackers managed to get at the disposal of turning on and off the air conditioner, audio systems, turning off the brakes and interfering with the steering on the go. In 2016 and 2017, Tesla was attacked. Security researchers from the Keen Security Lab have demonstrated an attack on the Tesla Model S. They were able to activate the brakes, open the doors and fold the mirrors at a distance of 20 km from the cars. Later, one of the hackers broke into the Tesla Model S P85 car power management system and modified it by installing autopilot equipment, software from the twin-engine versions of Tesla. Hacking a car can seriously harm the physical condition of the car owner. But so far, fortunately, the frightening hacker experiments help automakers and developers of connected systems increase the safety level of their products.
The second threat is data. In November 2017, Uber reported data theft of 57 million of its users. Hackers stole the names, email addresses and telephone numbers of 50 million Uber passengers around the world. The hackers also had personal information about 7 million drivers, including about 600,000 US driver license numbers. The history of travel and car use, personal and statistical data - everything can be the object of attack.
And what do you say about the theft of your data? The car has long been an analogue of the office. People spend in the car business negotiations on the speakerphone, not looking up from taxiing, discuss plans for life, talk with their children. Are you ready to share this information with the world? Having connected to the car system without performing physical hacking, you can remotely access everything that happens inside. And the bigger the business, the worse the theft of such corporate and personal data will be. The car itself becomes less valuable than the information that can be read from it. So the hijacking, from which the person is most likely insured, and the first threat we have named, suffers minimal damage today, unlike all other potential incidents.
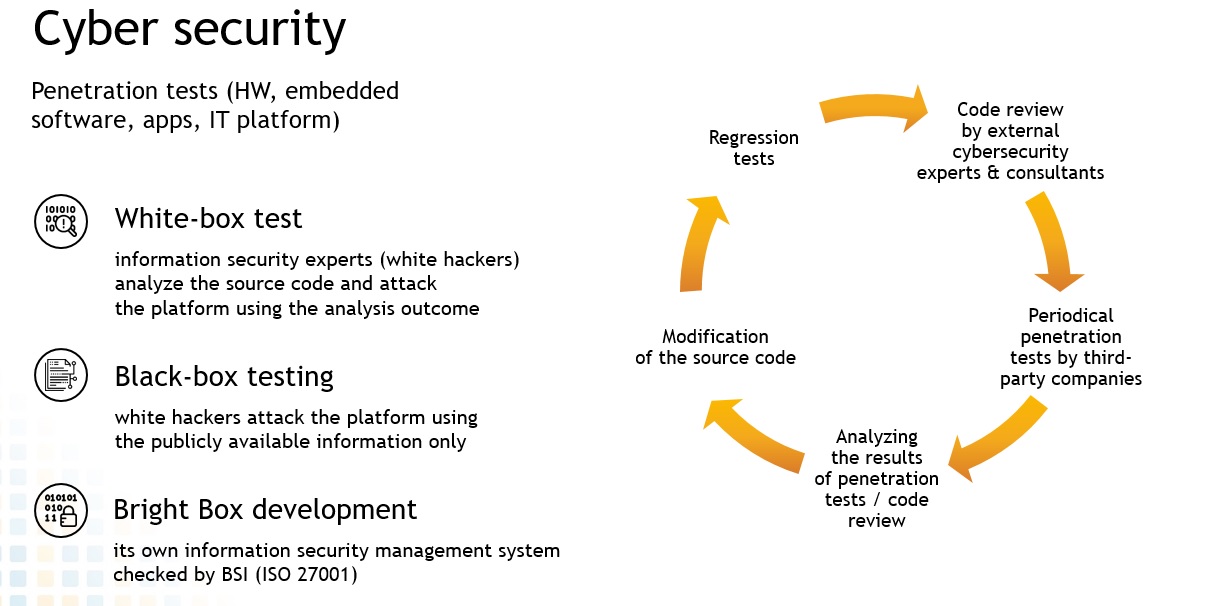
Of course, to avoid the described threats, car and related equipment manufacturers must develop safe systems. In the case of large consortia, standards publications and definition of requirements are needed: OEMs must harmonize requirements and produce new innovative systems that can withstand possible cyber attacks. When developing, it is important to pay attention to the technological and process parts, checking the organization of the development environment, testing environment, conducting mandatory tests, taking care of the product movement issues, the location of the security code and the requirements that make it safe.
Let's now go back to the topic of personal computers. We see that today there are a lot of high-quality security systems that allow you to build serious means of protection, but users do not change their behavior. And now the weakest link in the world of information security is man. Unfortunately, we very often focus on the technical component, forgetting about people. You can put a strong iron door, but if your little son or an old mother will open it to anyone who calls, how much will this increase the level of security?
Car protection should be at a high level, but counteraction is also necessary from the users. The easiest way to steal an unclosed car or a car without an alarm. Cybersecurity is the same. If the driver with the application connected to the car does not follow the safety rules - does not have a password for the phone and the service or uses an identification method that is too simple, does not turn off the bluetooth in the car - this can lead to certain problems.
We, in Bright Box, realizing the importance of safety for end users and possessing expertise in the connected car security, decided to launch a short online course “Cybersecurity for drivers” with practical advice.
From the course you will learn how to protect yourself and your car from intruders when using modern technologies, what you need to pay attention to and what rules you need to follow to ensure that all of the listed threats are not implemented. The course will take no more than 10 minutes. At the end, you will be offered testing and a certificate of successful completion of the course.

Sign up for a course!

Cars ceased to be physically independent of communications and networks at the end of the 20th century , and as the capabilities of the so-called connected cars expanded, the potential for cyber attacks increased. Today, issues of development of IT technologies are not considered without considering this problem.
')
The Internet has changed the way you work with a computer, as connection today changes the car as a whole and the road environment. When personal computers began to enter our lives, malware was a major information security problem. A computer virus could lead to data corruption, and sometimes damage the computer itself. Nobody thought about data theft or misuse of technology. The communication channels were very slow, and only “favorites” could connect to the Internet or other networks. At that time, the worst thing that could happen was buying a new computer if the old one was damaged. But as soon as the Internet became available, and the cost of equipment decreased, the situation changed. Viruses, of course, remained a very unpleasant event, but we already fear not the purchase of a new computer, but the loss of our data, disruption of the work of critical systems on which our life depends.

The same thing happens with the car today. Previously, the car owner was puzzled only by saving his own car - no one wants to find under the windows the absence of a recently purchased vehicle. But as soon as the car was connected to the network, everything changed, a number of additional threats, no less weighty than theft, were revealed.
The main and most serious if a cyber attack is committed is the threat to the driver’s life. In 2015, Chrysler recalled 1.4 million vehicles after a couple of hackers demonstrated to WIRED that they could remotely monitor the Jeep system via the Internet. Hackers managed to get at the disposal of turning on and off the air conditioner, audio systems, turning off the brakes and interfering with the steering on the go. In 2016 and 2017, Tesla was attacked. Security researchers from the Keen Security Lab have demonstrated an attack on the Tesla Model S. They were able to activate the brakes, open the doors and fold the mirrors at a distance of 20 km from the cars. Later, one of the hackers broke into the Tesla Model S P85 car power management system and modified it by installing autopilot equipment, software from the twin-engine versions of Tesla. Hacking a car can seriously harm the physical condition of the car owner. But so far, fortunately, the frightening hacker experiments help automakers and developers of connected systems increase the safety level of their products.
The second threat is data. In November 2017, Uber reported data theft of 57 million of its users. Hackers stole the names, email addresses and telephone numbers of 50 million Uber passengers around the world. The hackers also had personal information about 7 million drivers, including about 600,000 US driver license numbers. The history of travel and car use, personal and statistical data - everything can be the object of attack.
And what do you say about the theft of your data? The car has long been an analogue of the office. People spend in the car business negotiations on the speakerphone, not looking up from taxiing, discuss plans for life, talk with their children. Are you ready to share this information with the world? Having connected to the car system without performing physical hacking, you can remotely access everything that happens inside. And the bigger the business, the worse the theft of such corporate and personal data will be. The car itself becomes less valuable than the information that can be read from it. So the hijacking, from which the person is most likely insured, and the first threat we have named, suffers minimal damage today, unlike all other potential incidents.
Of course, to avoid the described threats, car and related equipment manufacturers must develop safe systems. In the case of large consortia, standards publications and definition of requirements are needed: OEMs must harmonize requirements and produce new innovative systems that can withstand possible cyber attacks. When developing, it is important to pay attention to the technological and process parts, checking the organization of the development environment, testing environment, conducting mandatory tests, taking care of the product movement issues, the location of the security code and the requirements that make it safe.
Let's now go back to the topic of personal computers. We see that today there are a lot of high-quality security systems that allow you to build serious means of protection, but users do not change their behavior. And now the weakest link in the world of information security is man. Unfortunately, we very often focus on the technical component, forgetting about people. You can put a strong iron door, but if your little son or an old mother will open it to anyone who calls, how much will this increase the level of security?
Car protection should be at a high level, but counteraction is also necessary from the users. The easiest way to steal an unclosed car or a car without an alarm. Cybersecurity is the same. If the driver with the application connected to the car does not follow the safety rules - does not have a password for the phone and the service or uses an identification method that is too simple, does not turn off the bluetooth in the car - this can lead to certain problems.
We, in Bright Box, realizing the importance of safety for end users and possessing expertise in the connected car security, decided to launch a short online course “Cybersecurity for drivers” with practical advice.
From the course you will learn how to protect yourself and your car from intruders when using modern technologies, what you need to pay attention to and what rules you need to follow to ensure that all of the listed threats are not implemented. The course will take no more than 10 minutes. At the end, you will be offered testing and a certificate of successful completion of the course.

Sign up for a course!
Source: https://habr.com/ru/post/350268/
All Articles