Basics of cryptography. Part 0
The purpose of this series of articles I would like to put the creation of the simplest crypto-protected messenger with a focus solely on cryptography, excluding from consideration the technical details of communications, network protocols, graphics and everything else.
Step by step, bypassing the vulnerabilities that our protocol being developed from scratch will have, at the end we will get a self-assembled cryptographic system, opposing the overwhelming number of attack variations.
Most people unfamiliar with cryptography, thinking about encryption, imagine some kind of safe in which the original information is put in its pure form, and in order to get the user to get it back, you need to present the system with a combination that unlocks the safe lock and retrieve information from an abstract box. .
')
However, with this approach, a number of problems arise:
First of all, encryption was developed to hide information in the military sphere, and for it the analogue of the safe is unacceptable. Laws and regulations do not apply during hostilities; therefore, those who gain access to the safe will not try to pick up a code for the lock — they will either use the lock to open the locker by force or contact the safe box manufacturer to bypass the protection.
Therefore, cryptography faces the question of how to preserve the integrity of information, even if the "safe" falls into the hands of the enemy.
A necessary condition for this is to change the structure of the information itself in such a way that its recovery was possible only with the use of a certain key, the size of which is much smaller than the initial data set.

Around this form, encryption leaves your information, with the only difference that it remains recoverable provided that you know the key
Information can only be recovered using the same key that the receiving information on the other side needs to know.
Such an informational mess can be transmitted via open communication channels; it does not represent any value for anyone except people who know the password.
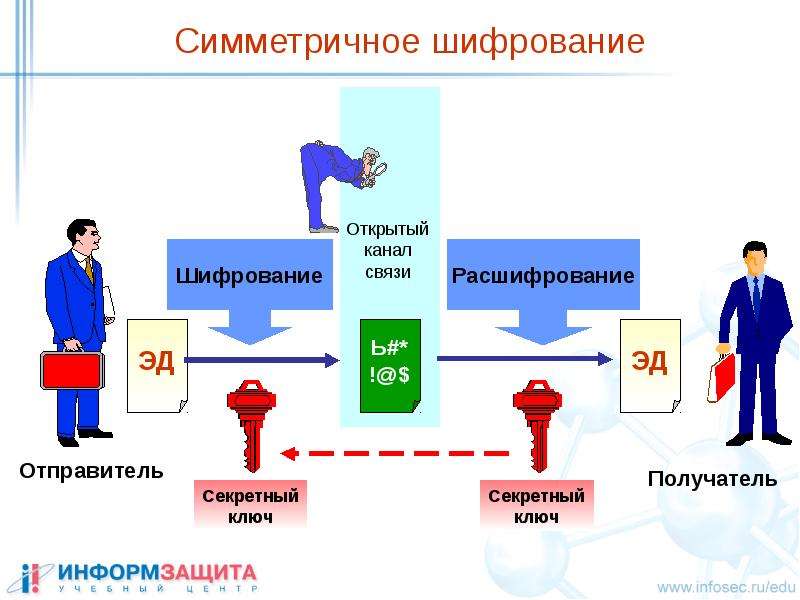
Such encryption is called symmetric, since it uses the exact same cipher as for decryption to encrypt information.
Looking ahead, we can say that this encryption method is not without flaws, so asymmetric encryption methods were invented, but we'll talk about them later.
Symmetric encryption uses the following information transfer protocol:
Considering that the password length is 12 characters for us, and each character is 8 bits, it will take a complete brute force on Alice (2 ^ 8) ^ (12), or 2 ^ 96 operations. Such a search will take the attacker several centuries, and it is unlikely that encrypted information will remain relevant by this time.
Alice has a simple program on her computer
Alice received an encrypted line and sends it to Bob via a telephone line, which Eva listens on around the clock. Having intercepted the encrypted message, Eve cannot do anything with it, but Bob, in turn, having received the message, in the same program will apply the password ddghjfTTfbfs4852, which he knows in advance and will be able to decrypt the message.
The program installed by Bob:
The SymmEncryptor method still remains for us a black box, we do not know how it works, but only rely on its reliability
Conventional encryption algorithms have been tested for tens of years by the cryptographic community of the world, and if there is no evidence of its compromise during this period, then we can safely assume that the algorithm is reliable, it is enough to independently test the old encryption algorithms without being a cryptographer. complicated
You should not trust new encryption algorithms by default until they have passed sufficient strength tests. And even more so, do not try to create your own, naively believing that you will manage to take into account all the nuances that a potential cracker might notice.
Next time we will analyze the black box of the class SymmEncryptor and write the simplest encryption mechanism to figure it out on a personal example - what it is and how it works.
Step by step, bypassing the vulnerabilities that our protocol being developed from scratch will have, at the end we will get a self-assembled cryptographic system, opposing the overwhelming number of attack variations.
Most people unfamiliar with cryptography, thinking about encryption, imagine some kind of safe in which the original information is put in its pure form, and in order to get the user to get it back, you need to present the system with a combination that unlocks the safe lock and retrieve information from an abstract box. .
')
However, with this approach, a number of problems arise:
- The safe can be opened with a grinder or other force method.
- The safe maker can leave a bypass loophole and access content.
First of all, encryption was developed to hide information in the military sphere, and for it the analogue of the safe is unacceptable. Laws and regulations do not apply during hostilities; therefore, those who gain access to the safe will not try to pick up a code for the lock — they will either use the lock to open the locker by force or contact the safe box manufacturer to bypass the protection.
Therefore, cryptography faces the question of how to preserve the integrity of information, even if the "safe" falls into the hands of the enemy.
A necessary condition for this is to change the structure of the information itself in such a way that its recovery was possible only with the use of a certain key, the size of which is much smaller than the initial data set.

Around this form, encryption leaves your information, with the only difference that it remains recoverable provided that you know the key
Information can only be recovered using the same key that the receiving information on the other side needs to know.
Such an informational mess can be transmitted via open communication channels; it does not represent any value for anyone except people who know the password.
Such encryption is called symmetric, since it uses the exact same cipher as for decryption to encrypt information.
Looking ahead, we can say that this encryption method is not without flaws, so asymmetric encryption methods were invented, but we'll talk about them later.
Symmetric encryption uses the following information transfer protocol:
- Suppose the symmetric key is: password
- Alice encrypts the message and receives an encrypted set of bits in a form very similar to informational garbage and transmits it over an open communication channel.
- Eve, having overheard the encrypted message, cannot come up with anything better than how to start sorting through the password in order to get the original message, since, with an ideal or close to ideal symmetric algorithm, password selection is the most acceptable way of obtaining access to information.

Considering that the password length is 12 characters for us, and each character is 8 bits, it will take a complete brute force on Alice (2 ^ 8) ^ (12), or 2 ^ 96 operations. Such a search will take the attacker several centuries, and it is unlikely that encrypted information will remain relevant by this time.
Alice has a simple program on her computer
public class User { private String password = "qdghjfTTfbfs4852"; // SymmEncrypor - , private SymmEncryptor SE = new SymmEncryptor(); // private String encryptMessage(String message) { String encMessage = SE.encrypt(message, password); System.out.print(" : " + encMessage); return encMessage; } // private String decryptMessage(String EncryptedMessage) { String encMessage = SE.decrypt(EncryptedMessage, password); System.out.print(" : " + decMessage); return decMessage; } public static void main(String[] args) { String message = encryptMessage("Hello, Bob!"); } } Alice received an encrypted line and sends it to Bob via a telephone line, which Eva listens on around the clock. Having intercepted the encrypted message, Eve cannot do anything with it, but Bob, in turn, having received the message, in the same program will apply the password ddghjfTTfbfs4852, which he knows in advance and will be able to decrypt the message.
The program installed by Bob:
public class User { private String password = "qdghjfTTfbfs4852"; private SymmEncryptor SE = new SymmEncryptor(); private String encryptMessage(String message) { SymmEncryptor SE = new SymmEncryptor(); String encMessage = SE.encrypt(message, password); System.out.print(" : " + encMessage); return encMessage; } private String decryptMessage(String message) { String encMessage = SE.decrypt(message, password); System.out.print(" : " + decMessage); return decMessage; } public static void main(String[] args) { // , String message = "FJekjfisdf7f33fFFDf788dsfvUHVUDIUSiusdyf&D&F^8" // , , qdghjfTTfbfs4852 String DecryptedMessage = decryptMessage(message); * : : Hello, Bob! } } The SymmEncryptor method still remains for us a black box, we do not know how it works, but only rely on its reliability
Conventional encryption algorithms have been tested for tens of years by the cryptographic community of the world, and if there is no evidence of its compromise during this period, then we can safely assume that the algorithm is reliable, it is enough to independently test the old encryption algorithms without being a cryptographer. complicated
You should not trust new encryption algorithms by default until they have passed sufficient strength tests. And even more so, do not try to create your own, naively believing that you will manage to take into account all the nuances that a potential cracker might notice.
Next time we will analyze the black box of the class SymmEncryptor and write the simplest encryption mechanism to figure it out on a personal example - what it is and how it works.
Source: https://habr.com/ru/post/350198/
All Articles