UPDATED: Amplified memcached 500 Gbps DDoS attacks swept across Europe

A long time ago, in a distant git repository, Brian Aker made a commit that introduces a remarkable feature for listening to UDP traffic in the default memcached installation.
And between February 23 and 27, 2018, a wave of memcached-amplified DDoS attacks swept across Europe.
The security issue of memcached has been known since at least 2014, when Ivan Novikov, the director and founder of Wallarm, spoke about “ memcached injections ” from the Black Hat US scene.
')
And although the injections may allow an attacker to achieve a wide variety of goals, last night we saw a wave of amplified DDoS attacks all over the Internet, including Russia's largest network resources, with port 11211 at the source. All attacks on the past weekend are identified by this attribute as memcached-amplified. In 2017, a group of researchers from the Chinese OKee Team spoke about the possibility of organizing such attacks, pointing out their potentially destructive power.
Over the past few days, many sources have confirmed the fact of an attack by amplified responses from memcached-resources, with small intersperses of DNS and NTP. Intermediaries of these attacks has become a major provider of OVH and a large number of smaller Internet service providers and hosters.
Qrator Labs said many times that in networks, despite the general drop in the number, there are still a lot of amplifiers. Last year, researchers told us, and last weekend demonstrated clearly how such attacks can reach fantastic strength. One of Qrator Labs' clients, the QIWI payment system, confirms the fact of a successfully neutralized attack with a band of 480 Gbit / s of UDP traffic over its own resources from compromised memcached amplifiers.
By default, memcache listens on all UDP traffic on port 11211 in the latest version. Ubuntu 16.04 with default settings runs memcached only on localhost, in contrast to CentOS 7.4, where the memcached configuration listens on UDP requests on all interfaces by default.
Similar, vulnerable, memcached-resources on the Internet a huge amount. In the case of the correct setting, this cannot happen, but the correct setting is still a rare case. Technicians install memcached and forget about its default settings, also forgetting that it listens on all UDP traffic sent to the server and responds, on average, with responses amplified 9000-10000 times.
Neutralization of such an attack can be achieved in several ways, the simplest of which are: installing a firewall on udp traffic from port 11211 (the appearance of legitimate traffic from this port is unlikely) or setting an incoming rate-limit. This implies that you have enough bandwidth to handle such an attack in front of the firewall. For a larger provider, there are two known options:
1. The flowspec filtering;
2. Using extended community.
Take care of port 11211.
UPDATE :
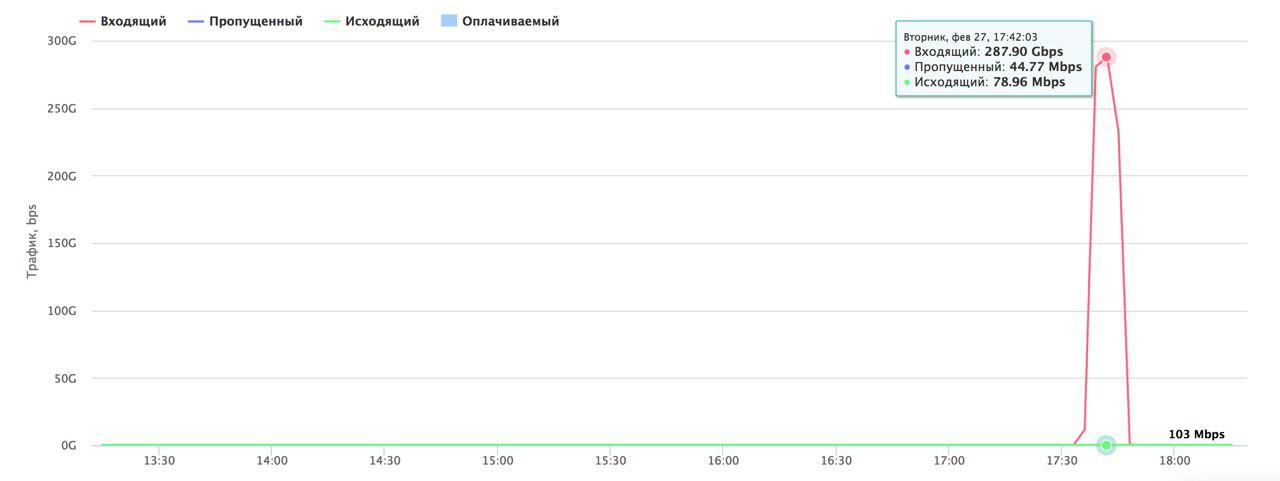
After the publication of this note, Habrahabru tried to pour almost 300 Gbps memcached amplificated UDP.
Source: https://habr.com/ru/post/350074/
All Articles