APTSimulator - testing countering APT threats
APT Simulator is a framework for checking protective equipment and actions to investigate incidents in a Windows environment that simulates the activity of an infringer of an information system. This is a good platform for training the Blue Team team to counter modern threats.
The main purpose:
- Check for threat detection / compromise assessments.
- Check for detecting security breaches.
- Check SOC / SIEM monitoring tools.
- Environment for exfiltration data for forensic analysis.
APT (Advanced Persistent Threat) These goals usually include establishing and expanding their presence within the information technology infrastructure of the target organization to pursue the intentions of extracting information, disrupting or creating interference to critical aspects of a task, program or service, or to take a position that allows these intentions to be fulfilled in the future. APT, as a “developed sustainable threat”: it has repeatedly achieved its goals for a long time; resistance; has the ability to maintain the level of penetration in the target infrastructure required for the implementation of intentions.
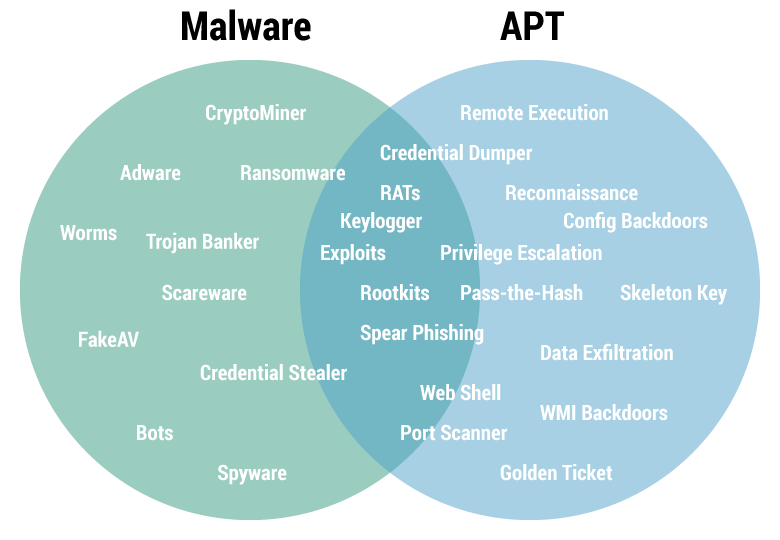
Such attacks are the most "advanced" and, as a rule, technologically complex. In contrast to the usual attacks - consolidation and hidden presence in the system, allowing attackers to interact with the hacked infrastructure and expand their area of concern in a corporate environment.
The following table presents markers of compromise and expected detection results:
- AV = Antivirus
- NIDS = Network Intrusion Detection System
- EDR = Agents on endpoints - AWS, servers (Endpoint Detection and Response)
- SM = Security Monitoring
- CA = Signs of Compromise (Compromise Assessment)
| Test case | AV | NIDS | Edr | SM | CA |
|---|---|---|---|---|---|
| Local file collection | X | ||||
| Connection to C & C servers | X | X | X | X | |
| DNS cache poisoning | X | X | X | X | |
| Malicious User-Agent (droppers, trojans) | X | X | X | ||
| Netcat backconnect | X | X | X | X | |
| WMI backdoor | X | X | X | ||
| LSASS dump | X | X | X | ||
| Mimikatz Employment | X | X | X | X | |
| Using WCE | X | X | X | ||
| Activate Guest Access and Privilege escalation | X | X | X | ||
| Substitute system files | X | X | X | ||
| Hosts modification | X | X | X | ||
| Obfuscated JS Dropper | X | X | X | X | X |
| Obfuscated files (rar> jpg) | X | ||||
| C-class subnet scanning | X | X | X | X | |
| System Information Collection Commands | X | X | X | ||
| Run PsExec | X | X | X | ||
| Malware Delivery | X | X | |||
| At job to collect data | X | X | X | ||
| Adding RUN parameters to the registry | X | X | X | ||
| Creating tasks in the scheduler (can be used as backdoors) | X | X | X | ||
| Stickykey backdoor | X | X | |||
| Using the UserInitMprLogonScript registry key | X | X | X | ||
| Web shells | X | X | X | ||
| WMI backdoors | X | X |
Caution: The framework contains tools and executables that can damage the integrity and stability of your system. Use them only on test or demonstration systems or stands. 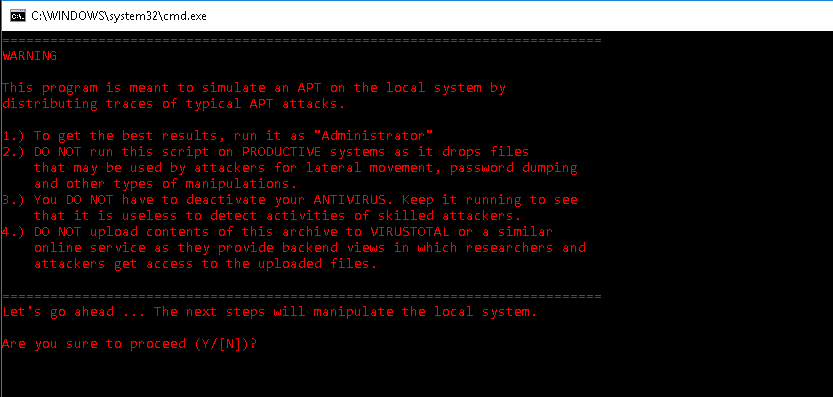
The system interface is a "classic" pseudographic shell, familiar to users of the Metasploit Framework, Empire, SET and many others.
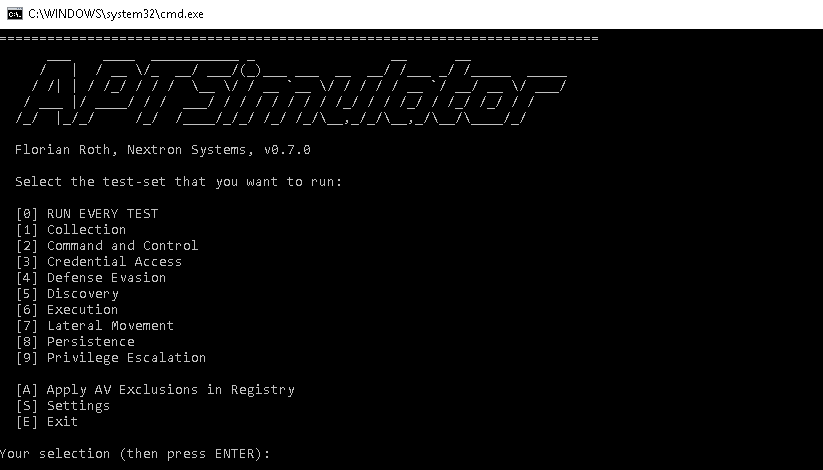
The main tools are available from the program context menu. There is a possibility of launching the toolkit from the context menu, as well as individual utilities.
→ Project page on github .
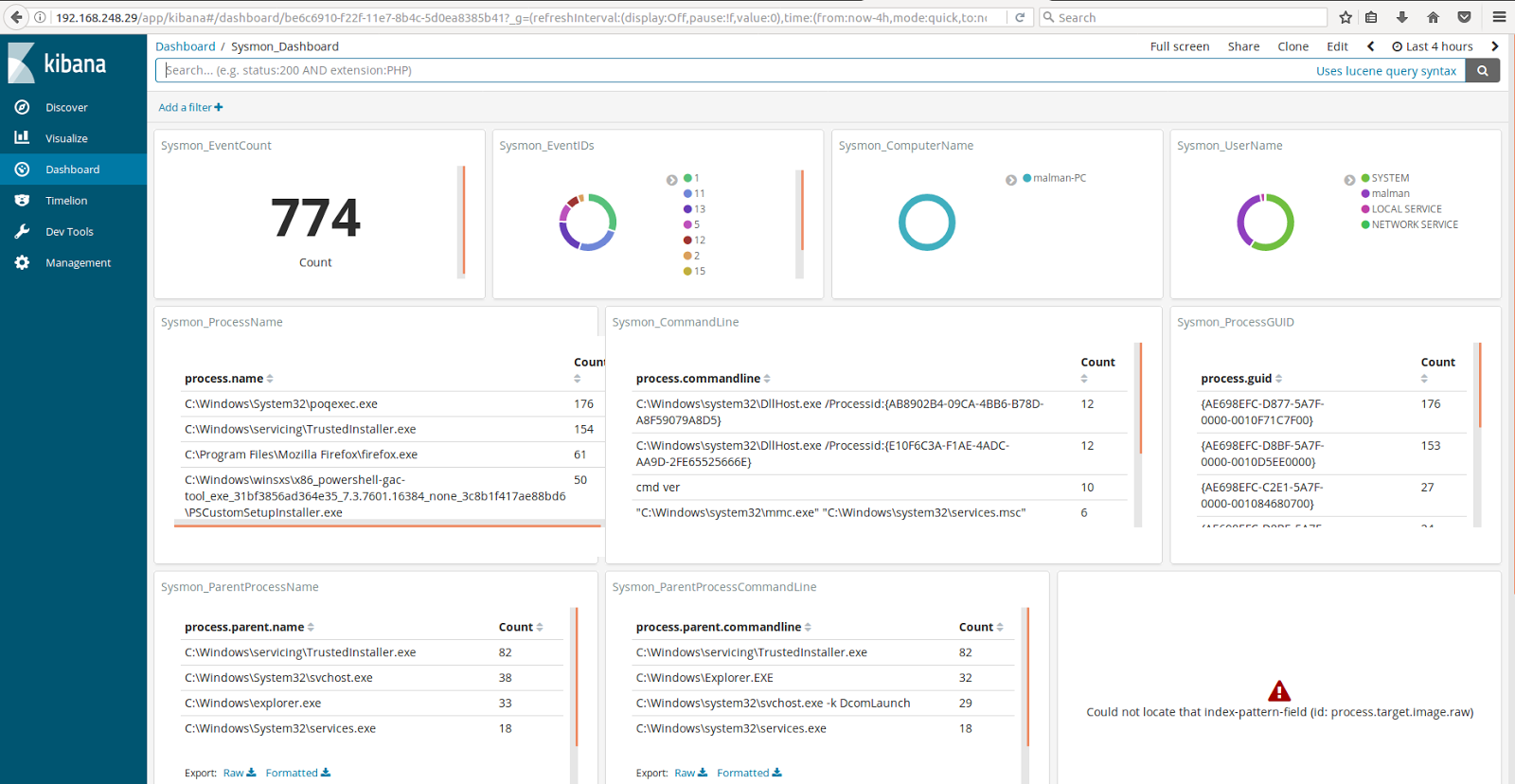
For those who do not have their own monitoring environment of malicious activity, I suggest using HELK-Hunting ELK (Elasticsearch, Logstash, Kibana) - a monitoring environment for checking and visualizing data from compromised hosts.
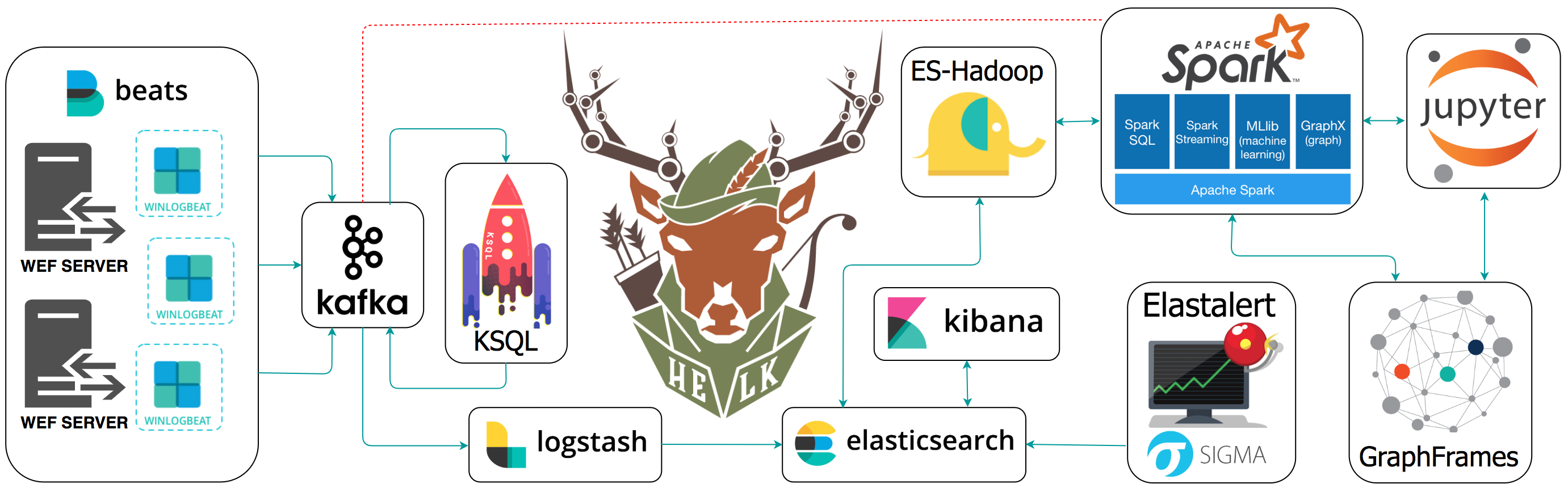
This system is a platform for detecting threats, a set of tools and utilities for analysis and visualization in the form of a docker container.
→ Project page on github .
The use of these two tools will allow you to improve your skills in identifying modern threats, investigating incidents and developing means and measures to respond quickly.
')
Source: https://habr.com/ru/post/350066/
All Articles