Let's Encrypt postponed issuance of wildcard certificates due to security issues.

Statistics Let's Encrypt
On January 4, 2018, the Certificate Authority Let's Encrypt began testing endpoints of software interfaces for the automatic issuance of wildcard certificates. These certificates are issued only in the new version of the automated certificate management environment - ACME v2. The public launch of ACME v2 was scheduled for February 27 , but at the last moment it was decided to postpone it for some time. This is not Let's Encrypt's fault. It was just that on January 8, 2018, it was unexpectedly discovered that one of the methods for validating domains TLS-SNI-01 can be used to obtain a certificate for other people's subdomains . The Certificate Authority Let's Encrypt turned off support for TLS-SNI-01 and postponed the introduction of the ACME v2 protocol, where they were going to use the new TLS-SNI-02 check that was subject to the same vulnerability.
The IETF ACME working group is now working on the TLS-SNI-03 standard. There must solve the problem.
')
Wildcard certificates are one of the most frequently requested features among users. Such a certificate is distributed to several sub-domains at once, so it is not necessary to separately register each sub-domain separately.
Differences between ACME v2 and ACME v1
The ACME v2 protocol has a number of differences from the first version of the API. Here are some of the major high-level changes :
- The procedure for authorization / issuance of certificates has changed.
- JWS authorization request has changed.
- Instead of the
resourcefield, a newurlheader appeared in the JWS request body. - Another endpoint / resource address.
- Creating an account and signing a ToS agreement is now done in one step, not two.
- A new type of domain ownership verification TLS-SNI-02 instead of TLS-SNI-01 (not yet implemented, see above for vulnerability with subdomain validation).
Like DV, wildcard certificates from Let's Encrypt are planned to be issued free of charge and automatically to everyone, but only through the ACME v2 point. To obtain a certificate, you must install one of the clients that support this protocol.
Clients with ACME v2 support
- ACME4J (acme4j> = 2.0)
- GetSSL ( APIv2 branch)
- acme.sh
- Net :: ACME2
- EasyHTTPs * (automatically selects v2 or v1)
- Hiawatha
- leclient php library
- dehydrated
URL of the ACME v2 test environment:
https://acme-staging-v02.api.letsencrypt.org/directoryNow these certificates cannot be used in production, because the intermediate certificate Fake LE Intermediate X1 is not in the trust stores of browsers and clients.
The delay in the implementation of ACME v2 is associated with an interesting vulnerability in the subdomain validation mechanism, which has recently become well known . The bottom line is that in some cases through Let's Encrypt you can get an HTTPS certificate for a subdomain of a foreign domain after its hijacking through a cloud service (DNS hijacking). For more on this hack, see the speech of security consultant Frans Rosen at the OWASP AppSec EU Belfast conference.
Let's Encrypt have nothing to blame for this vulnerability. Automated issuance of certificates is carried out in full compliance with the ACME standard approved by the ISRG. However, the lack of verification and the automated issuance of certificates makes it possible for intruders to operate - this focus only takes place with Let's Encrypt. Like some other magic tricks.
Weaknesses of Let's Encrypt Certificates
Automated certification center operation is both a strength and a disadvantage. Of course, it is very convenient to do everything through the API (see step-by-step instructions for installing HTTPS ). This approach is quite logical contributed to the mass distribution of HTTPS - it is good for everyone: for site owners, and for users, and for the general system of the ecosystem of security on the Internet. But there are also disadvantages, due to which Let's Encrypt certificates are not suitable for everyone. In addition to some inconvenience with the renewal of certificates every three months and the lack of guarantees, it is also a problem of trust.
First, Let's Encrypt does not issue the most reliable OV (organization validation) and EV (extended validation) certificates at all.
Secondly, security experts have long noticed that Let's Encrypt issue a lot of certificates to harmful sites that are used for phishing. For example, between January 1, 2016 and March 6, 2017, Let's Encrypt issued certificates for 15,720 domains with the word “PayPal” in the title, and the number of such certificates is growing exponentially, increasing every month by 1.5-2 times.
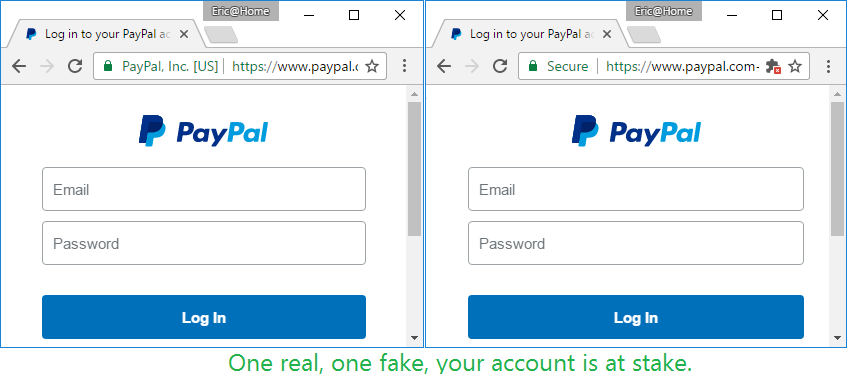
Since then, the problem has only worsened, and in fact Let's Encrypt becomes a permanent working tool for fraudsters.
The use of SSL certificates by fraudsters was one of the main concerns regarding the launch of Let's Encrypt at the end of 2015. In the old days with paid certificates, attackers could hardly afford to purchase thousands of certificates, especially the issuance of each of them was accompanied by a certain verification procedure. Now certificates have become free, and their receipt and renewal can be automated.
And no one thinks to fix this problem. The creators of Let's Encrypt think logically that it is not their business to monitor cybercrime and catch fraudsters. Therefore, they are not engaged in the moderation of sites. And browser developers continue to consider phishing sites that have received a DV-certificate as “safe”.
One of the partners of GlobalSign in August 2017 published a short article listing the advantages and disadvantages of Let's Encrypt. Here are some points to consider when choosing a free certificate:
1. Free Let's Encrypt certificate is short-term and designed for a period not exceeding 90 days, as opposed to a paid one, which can be issued for a period of up to 3 years. You can, of course, reissue the certificate every 3 months, but be sure to follow the deadlines. A certificate can be reissued in three ways: manually, by setting up a cron task scheduler or automatically.
If you chose the manual update method, then follow the deadlines clearly and reissue the certificate in time. Otherwise, you risk getting an influx of dissatisfied users of the site and their subsequent outflow.
The cron task scheduler is a way to configure automatic updates. The method is good for those who have Linux administration skills and can work with kroner. It is also necessary to take into account that the work of the krone does not exclude errors that may prevent the re-issue of the certificate. Conclusion: you will still have to follow the update.
Automatic update. This method assumes that you accept the automatic settings provided by the Certificate Authority. And here you need to understand that you thus give your consent to the fact that the CA can make changes at its discretion in the software and settings of your server.
2. Not all domains can be protected with free Let's Encrypt. This certificate is designed only to protect one domain without company verification, the so-called DV SSL (Domain Validation).
So, using Let's Encrypt, you cannot create the following types of certificates:
- Wildcard certificate to protect subdomains of a specific domain;
- Certificates OV SSL (organization validation) , involving verification of not only the domain, but also the company;
- EV certificates SSL (extended validation) . Certificate with the maximum degree of protection and the green address bar of the browser;
- Multi-Domain certificate type UCC;
The important point is that there are no financial guarantees of using Let'sEncrypt.
3. If suddenly a free certificate is hacked, no one will provide you with money compensation.
To date, Let's Encrypt has provided certificates for 67.6 million domains . All of them received free DV (Domain Validation) certificates through an automated procedure and API. Since the start of the full-service operation in December 2015, the share of HTTPS traffic on the Internet has increased from 39% to approximately 70%, that is, almost doubled (by the number of page views in Firefox, 14-day moving average).

The desire of Let's Encrypt to transfer 100% of the web to total encryption is great. But the automated approach somewhat “devalues” the status of DV certificates. Therefore, it might make sense for commercial companies, e-commerce sites, banks and other serious customers to look towards a managed PKI infrastructure or OV and EV certificates from such well-known global certification centers, such as GlobalSign . Although most of the usual sites will suit the free Let's Encrypt certificates: this is better than nothing.

Source: https://habr.com/ru/post/350048/
All Articles