(Non) security monitoring systems: Zabbix
Today we will continue to figure out how to behave at the first meeting with the monitoring system during pentest. This time, the old Zabbix came to visit us.
How it all works
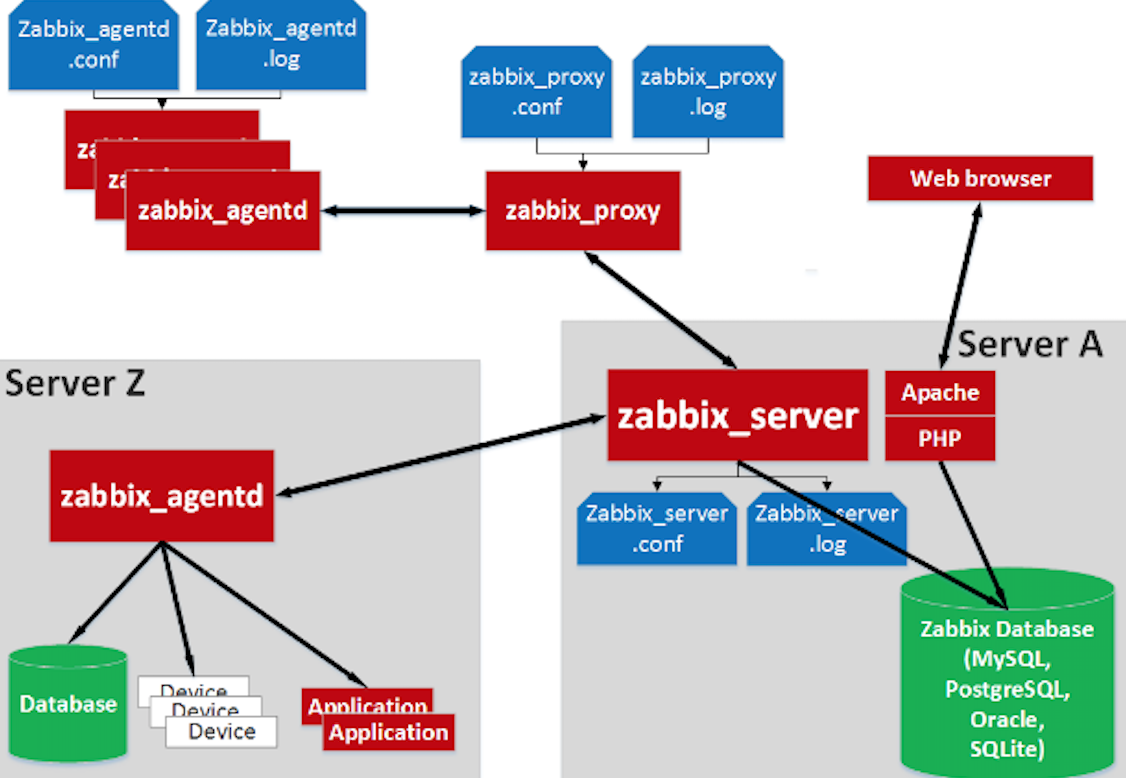
Over time, this monitoring system has acquired a large number of users and numerous forums will gladly help to understand all aspects of the fine-tuning of this software, but the community rarely helps to create a secure system configuration, these weaknesses will be discussed today.
')
Check in light
I do not think that you will be surprised to learn that not all system administrators support the versions of their CMs up to date. So let's start with a simple definition of the system version (you can use one of these scripts 1 or 2 for this ). With a certain probability, you will not need to invent something further and you will be able to use one of the well-proven exploits in order to achieve the goal.

But I think you didn’t look under the cat to read about how to use Metasploit modules, and now, you are inspired by good intentions and research surroundings, come to do your job, connect to the Ethernet outlet and discover a fresh, updated Zabbix. It does not matter, the system developers thought about you and made the transfer of traffic between the host and the server in an unencrypted form, so if the administrator did not bother with setting up encryption - it's time to recall the old arp spoofing. A detailed description of the administrator's session interception and posting on the web interface is described here , as well all the necessary scripts can be studied here .
We need to go deeper
Well, you have already compromised the system, but you know that Zabbix has the functionality of interacting with the observed agents and leaving without trying to capture the subnet would be an unaffordable luxury. Unlike Nagios in Zabbix, many of our capabilities are limited to configuration files that are not in a hurry to give us the opportunity to keep a constant shell on the agent, but only the weak ones surrender and in the updated version of our memo it is easy to explain how to gain a foothold in the compromised system and the necessary configs for successful escalation on the host regardless of whether we are dealing with Unix or Windows.
As you already understood, the purpose of this note was once again to draw the attention of all users of monitoring systems to the problem of their security, as well as to turn their view on our Cheat Sheet on the operation of the SM . The work does not end there, and soon new research in this area will be presented.
Thanks
I would like to thank Shodin for the work done on researching the Zabbix monitoring system (the article of this researcher will be published in our blog soon), without his contribution, our memo would be much leaner. Respect these guys: sabotaged , ro421 .
See you soon!
Source: https://habr.com/ru/post/350026/
All Articles