FastTrack Training. "Network Basics". "Basics of switching or switches." Part two. Eddie Martin December 2012
About a year ago, I noticed an interesting and fascinating series of lectures by Eddie Martin, which, thanks to its history and real-life examples, as well as its tremendous learning experience, is amazingly comprehensible and allows you to gain an understanding of quite complex technologies.

We continue the cycle of 27 articles based on his lectures:
')
01/02: “Understanding the OSI Model” Part 1 / Part 2
03: "Understanding the Cisco Architecture"
04/05: “The Basics of Switching or Switches” Part 1 / Part 2
06: "Switches from Cisco"
07: "Area of use of network switches, the value of Cisco switches"
08/09: "Basics of a Wireless LAN" Part 1 / Part 2
10: "Products in the field of wireless LAN"
11: The Value of Cisco Wireless LANs
12: Routing Basics
13: "The structure of routers, routing platforms from Cisco"
14: The Value of Cisco Routers
15/16: “The Basics of Data Centers” Part 1 / Part 2
17: "Equipment for data centers"
18: "The Value of Cisco in Data Centers"
19/20/21: "The Basics of Telephony" Part 1 / Part 2 / Part 3
22: "Cisco Collaboration Software"
23: The Value of Collaboration Products from Cisco
24: "The Basics of Security"
25: "Cisco Security Software"
26: "The Value of Cisco Security Products"
27: "Understanding Cisco Architectural Games (Review)"
And here is the fifth one.
I think what happens is the natural progress of network development. But there are some things that need a push, you need to apply force to start the process. The first router served as a personal computer, and for this was a special software. But the networks grew so fast that they needed separate processors that could handle the huge traffic. Computers also evolved, multi-core processors appeared. It was even possible to reverse the development process in some way using the SDN (Software Defined Network) - software-defined networks where the management process is separated from the data transfer process. But such an approach can harm Cisco, because there are areas where SDNs are completely inapplicable and the servers will be completely unsuitable, they will hang right away.
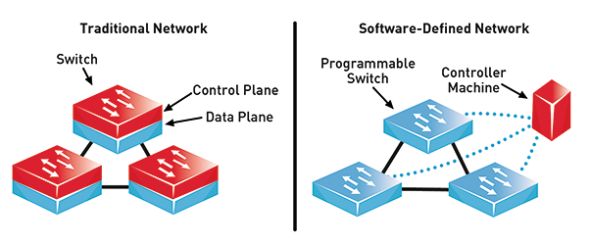
Let's talk about streaming, live video, converting traditional telephony and transcoding video on a huge or regular scale using SDN. We already have our ASIC microchips, which may be useful, or maybe not. Cisco has the necessary base to participate in this, but it will be a slow advance. Cisco always says that we have our own software for our routers, and for future generations of routers, the future generation of ISR (Integrated Service Router). Although it will not be called an ISR, it will still be a software router. But it will have fewer features than our second-generation ISR, so I do not think there will be a server capable of transmitting such a huge amount of information, or local VLANs of such power. But if we are talking about the transfer of small data blocks, this technology is justified and can be applied. You know that there are companies that persist in promoting the SDN idea everywhere, but Cisco does not want to become a suicide and promote it until you have to. We do not want to hurt our current products.
I was in Boston at one such company and spoke in great detail with one of its employees working on SDN. I made sure that they do not leave the ideas of vigorous promotion of such products and I have revealed the whole essence in detail. We cannot stop this process, this is a market trend, and it will develop further, whether Cisco will participate in this or not. Cooperation in this area will cost from 9 to 53 billion dollars and we must make every effort to "be in the game." But is this path valuable? Maybe yes, maybe not. Maybe we can do something with our chips and our capabilities.

I was asked a question about the network address, why it looks like this - 10.10.10.7, why it is needed, how the personal computer recognizes IP and how we can find out who owns this address. This is a very good question! Tell me, who among you made purchases on Amazon or Ebay? I see many. Did anyone make purchases on the Cisco website? Not very much, as I look! And what is the IP address of these resources, you know? Hardly. Remember the three important things you should get from DHCP? What is DNS (Domain Name Services)?
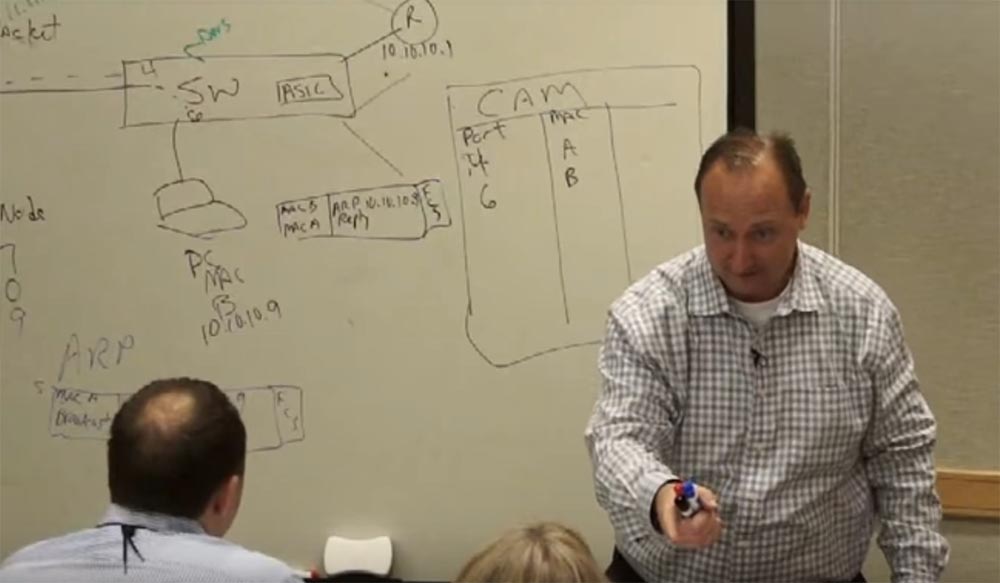
DNS allows you to not remember the numbers and use symbols instead of numbers. You remember the names well, but you don’t remember the number sequences well. I have to admit that I am the opposite. I cannot remember the names of all my cousins and sisters, but I remember their phone numbers. I'm serious. I have two sisters and I do not remember their middle names, but I remember their phone numbers. Each of you remembers what kind your mail server has, for example, mail.cisco.com. So, when you use your mail, you are not interested in its IP-address and the recipient's IP-address. In the switch, we have an internal DNS server located at the application level, which is used for all devices connected to it. So? our mail server mail.cisco.com wants to send mail, but to do this, it must use a transport protocol that does not understand the names, but understands the IP addresses. And because our DNS server accesses the server and says: "I have to convert mail.cisco.com to an IP address." And he does it. But what if we want to access external resources on the Internet? Say to google. In this case, we have a similar interaction with an external DNS server, which is already a DNS server for the entire Internet network. Thus, we have interactions with internal and external DNS servers.
What are the benefits of using domain names, not IP addresses? Think about the network configuration issue. Cisco employs about 70 thousand people. Imagine that we gave each of them a separate IP address for their mail. And soon, for some reason, you would like to change the address to another one, what would we do? We would be forced to change the configuration of all 70 thousand clients. But what if we put a DNS server on this network? Thanks to him, we could change the IP address from 10.10.10.9 to 10.10.10.10 automatically. We would change this entry on the DNS server and the changes would automatically apply to the network. That's cool. This way we can easily deploy our application and the DNS will do all the other work on the network.
The DNS server is a very powerful handler of information coming in via the DHCP protocol, which allows computers to automatically obtain an IP address. At the same time, the switch knows where you are located physically, because it uses this table of MAC addresses.
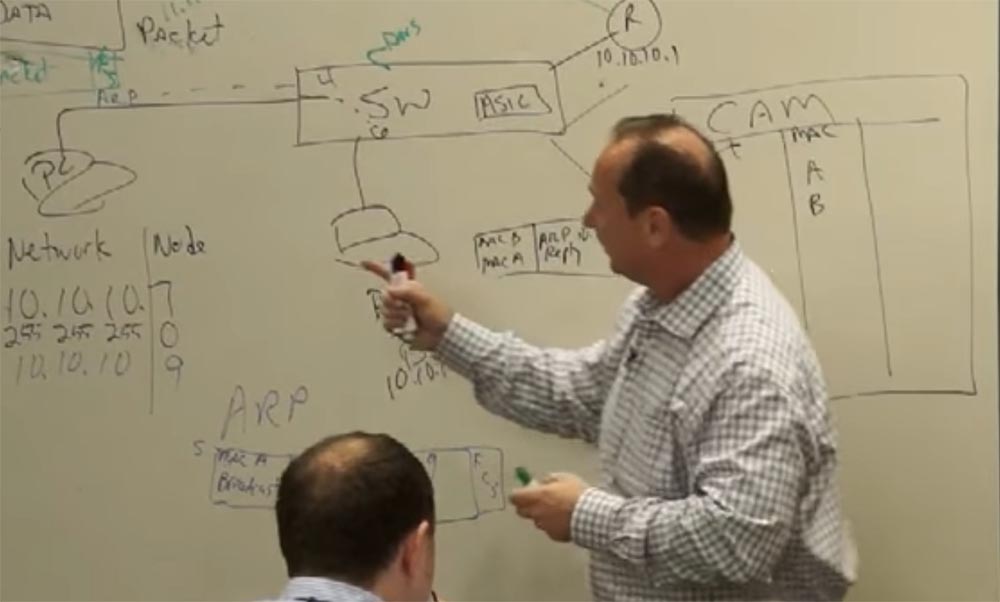
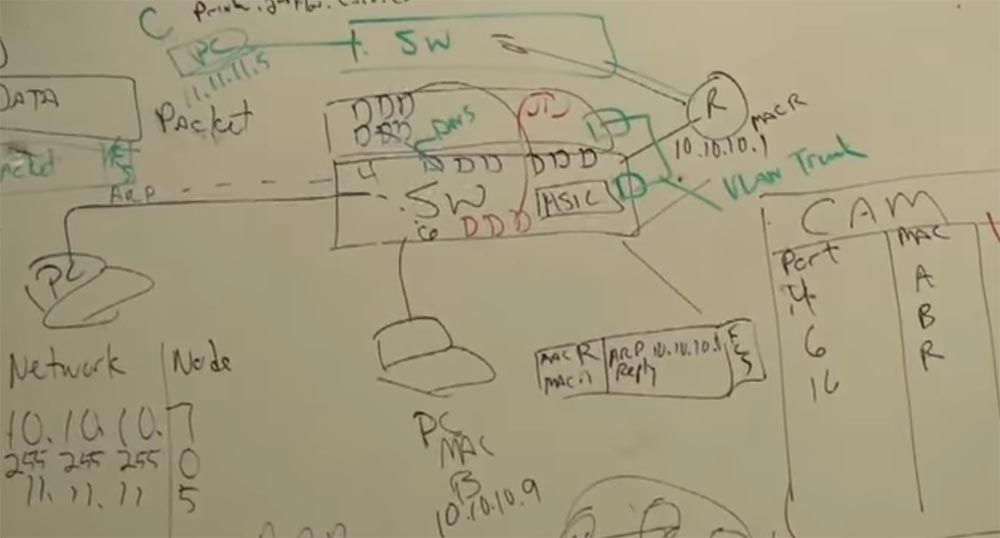
Suppose that I want to connect with IP 11.11.11.5, let's say this is a network printer on which you can print a document — this unit at the top almost in the middle will be our printer.
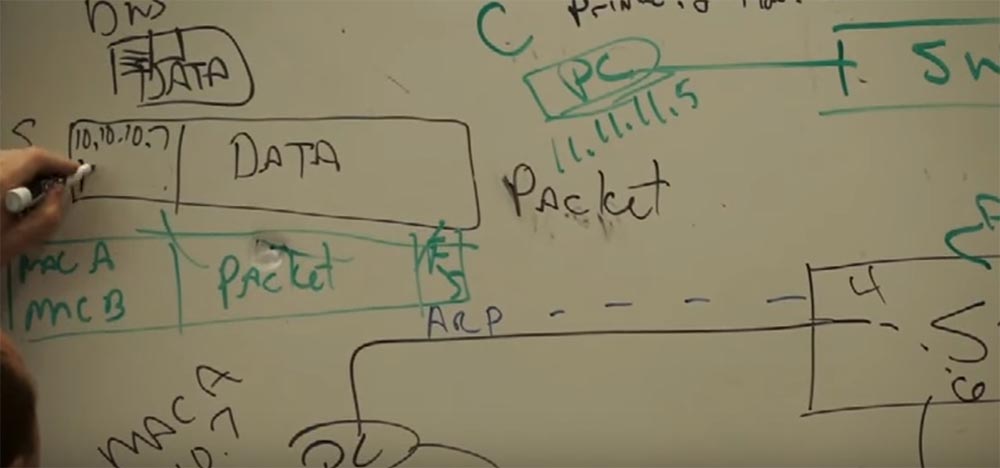
Let's give it the name printer.2floor.cisco.com, this is a well-known printer on the second floor. So, if we want to print, we need to resolve the DNS and get an IP address that matches this name. We will add its IP to the DATA block, where 10.10.10.7 already exists.
Now compare these addresses. Are they on the same network? Of course not!

The network number does not match, so a router is needed here, because if a computer is from another network, then it is connected to it via a router. This is the gateway, the gateway to the rest of the Internet world outside our network. One router (router), one entry point opens the gate to a world where there are millions, millions and millions of recipients, but among them there is one that you want to communicate with. So, if the device is with you on the same network, then you can communicate directly, via a switch, and if in different networks, then you get in touch via a router.
So, I'm going to send data to my 10.10.10.1 router, but what should I do if I don't know its MAC address? I know that it is in my network, but I do not remember the address, but the router remembers it! It has an ARP cache that stores IP addresses and MAC addresses that you “talked to” for 5 minutes. The duration of the “memory” of the router, depending on the operating system, is approximately 300 seconds, and if you have not accessed it again during this time, it will be disabled. And if you are going to send the data again, you say - I have to contact my default gateway again, and the whole cycle of device recognition within the network is repeated.
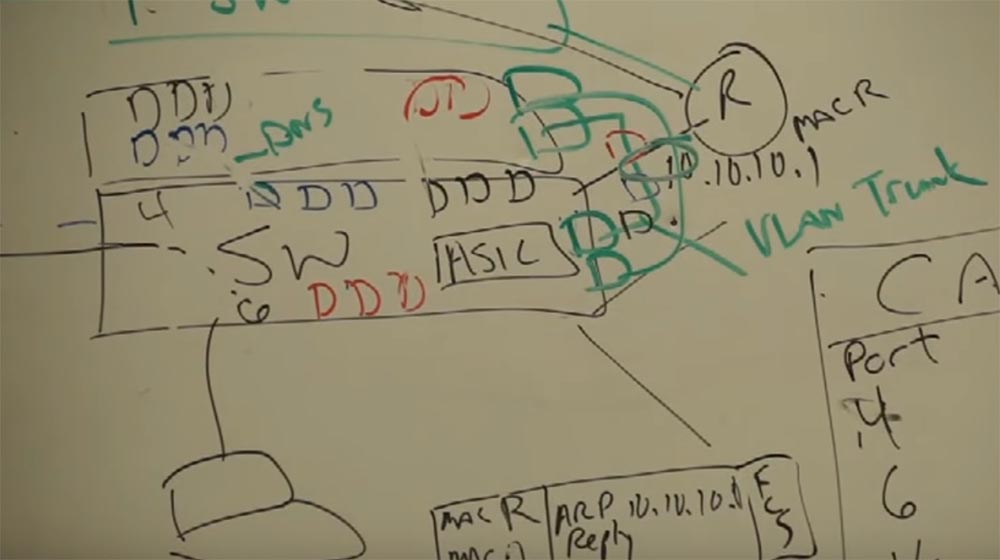
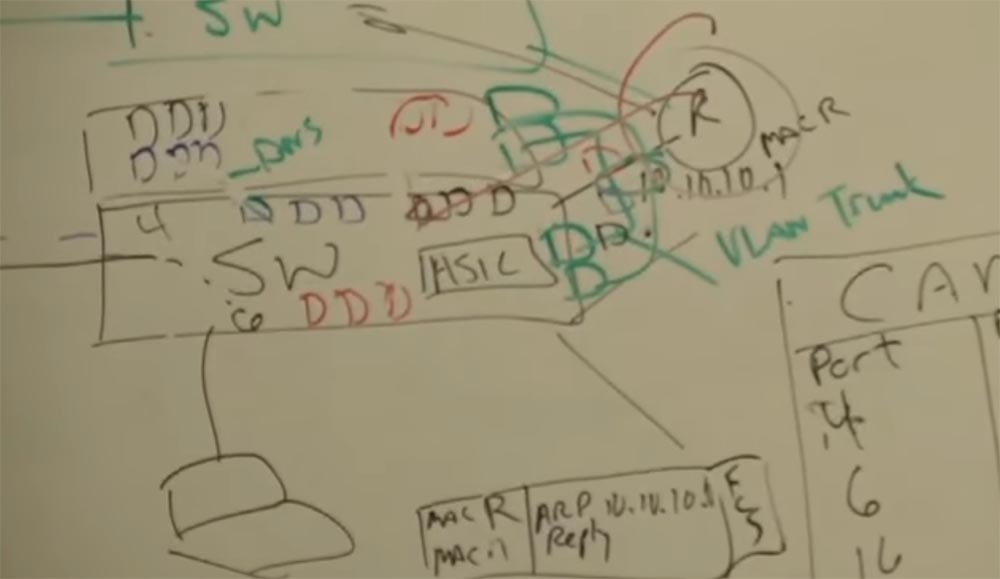
Let our router have a MAC address R, and it is connected to port 16 of our switch.
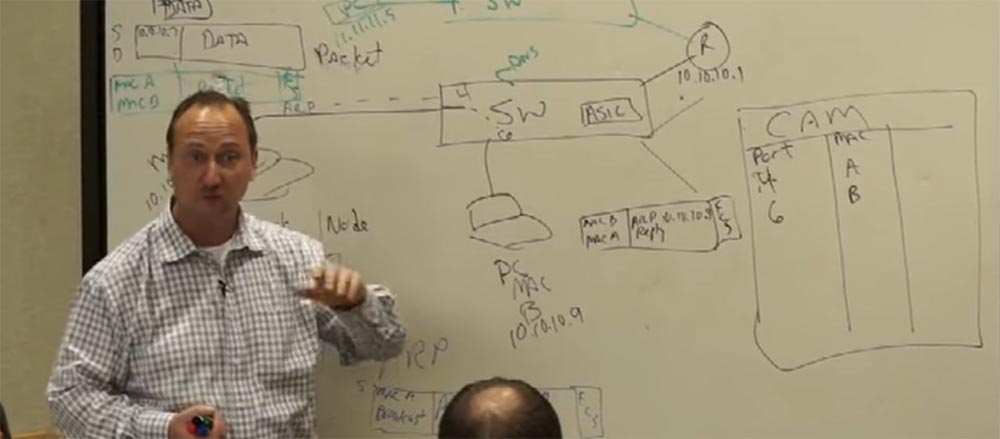
And when we access the printer, everything repeats according to the scheme - request, response, address check, and this happens an infinite number of times. And when I send my data packet to the printer, it gets on the switch, and the switch asks: “Oh, are you still here, number 4? Do you want to another network? Then I send you to that guy whose name is the router! ” And the router forwards your packet to the printer. It does not matter if it is the smallest or largest router in the world - they all work on the same principle.
Consider the case when the router connects two networks, on the one hand it has the address 11.11.11.x, and on the other 10.10.10.x. Of course, the router can connect at least 2 million networks. The router has 2 types of workers. Each network that is connected to the router will have its own “boyfriend” located on the second level of the OSI model (L2), which will determine the MAC address of the device for the network.
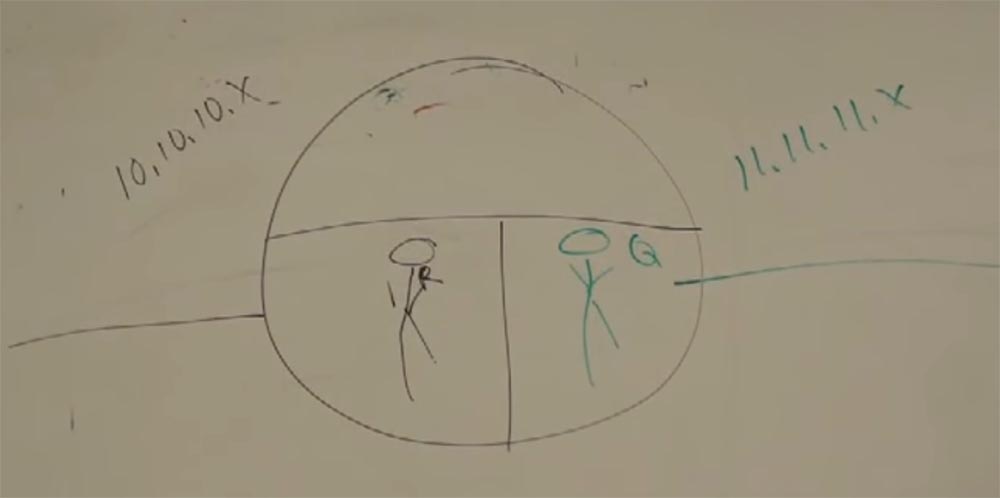
Let for 10.10.10.x the MAC address will be R, and for 11.11.11.x Q. These workers interact at the physical (L2) level. These two "guys", R and Q, each work in their own sector, but they both work together on the same task. And they are controlled by the third guy, the smartest, let's call him L3 - this is the third level.
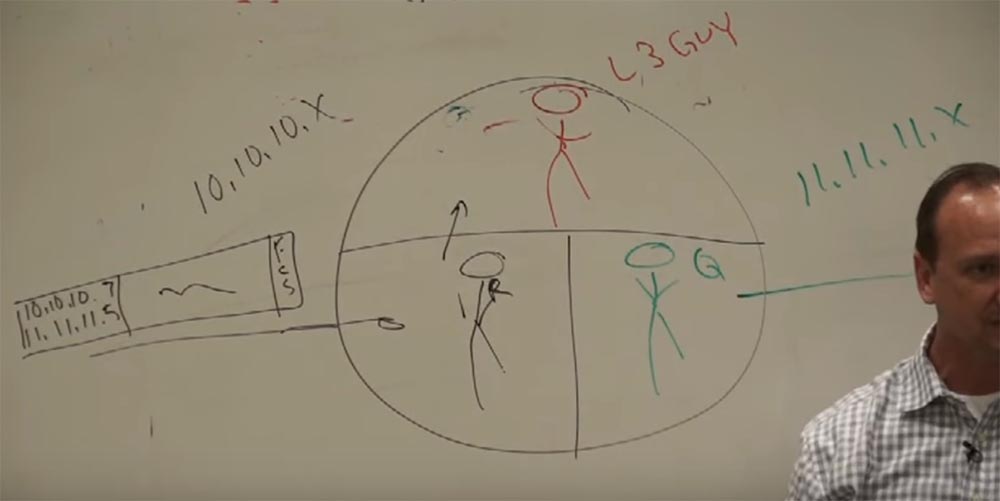
So, we have a frame transmission from the MAC address A (sender) to the MAC address R (router). The frame is successfully delivered to the worker who is on the second level of the 10.10.10.x network. He performs a checksum check (FCS), receives a packet from the frame and does not know what to do with it, since the second level can work only with MAC addresses, and the packet indicates that we want to send it from the device with the address 10.10. 10.7 to the device with the address 11.11.11.5 (printer). A worker “understands” that he does not have enough data to successfully transmit a packet, and addresses “upward” to the worker L3.
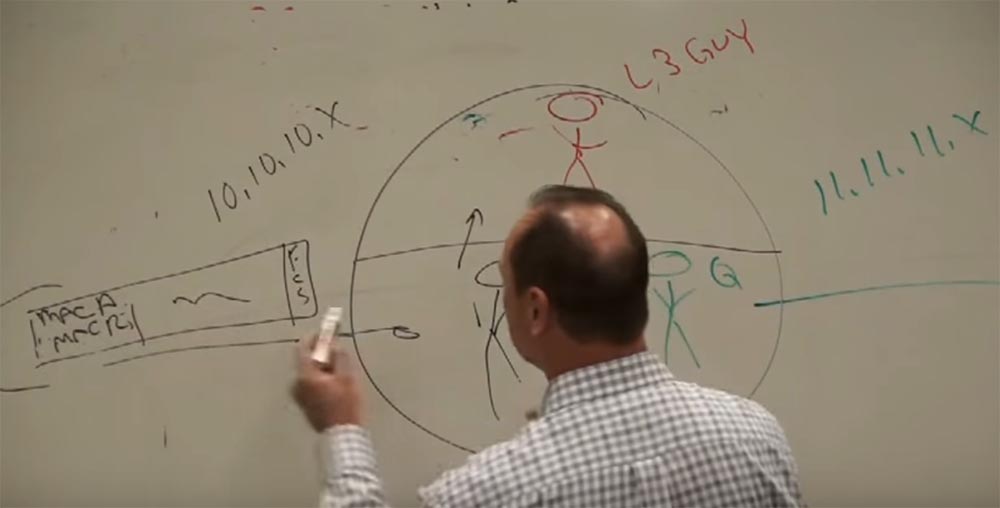
It's like in school - you don't know how to do the task, but you know a classmate who knows how to do it. And our router refers to such a knowledgeable “classmate” whose name is L3.
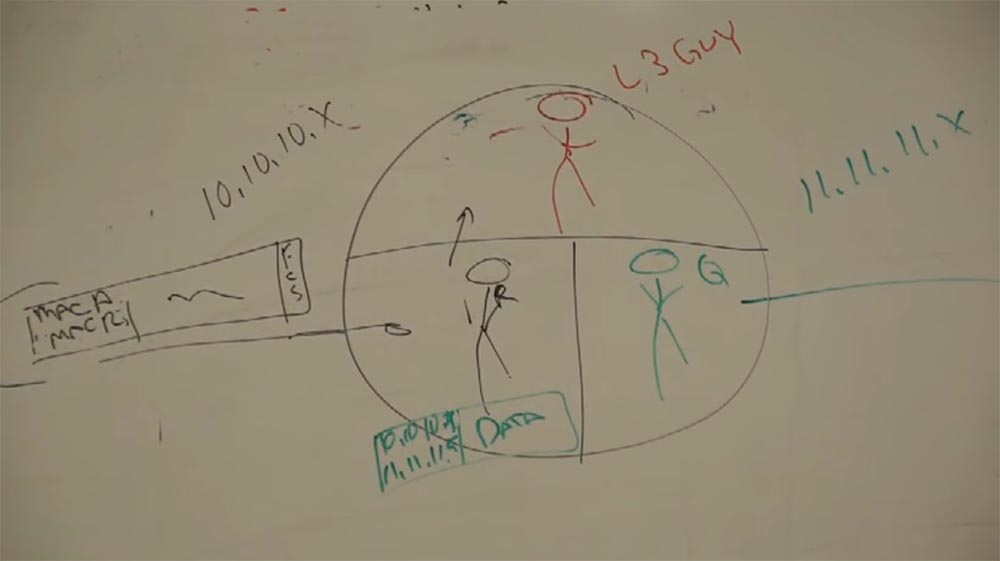
R tells him “Hey, level 3, do you know all the IP addresses? I have a package that needs to be delivered 11.11.11.5, delivered to the address - I have a drink ”! Well, you know how it happens! You transmit a packet to level 3, because level 3 is the packet level. It has tables in which there are all addresses of all networks, routing tables. And this serious guy from above, who knows what to do with the package, takes it and gives it to the guy named Q, in accordance with the routing table, which shows the routes and that this guy is responsible for the network we need, saying, " are you kind enough to deliver this to 11.11.11.5? ”and Q takes the packet, puts it in a solid frame, and what does he see? He sees the recipient’s address, but he hasn’t communicated with the device for which the IP address ends with 5 , he already forgot his MAC address! And now he shouts to his whole network: “Hey, is there anyone here who VUT 5 "? He uses the ARP protocol to determine the network address.
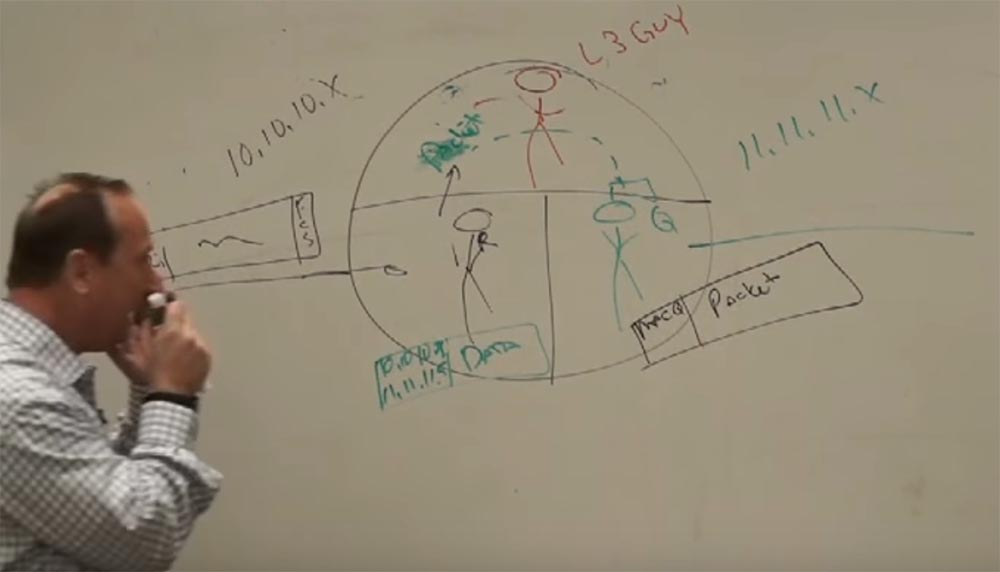
Suppose that it is answered by a device that has a MAC address of C. And now it marks the package “From MAC Q to MAC C” and sends it to the recipient with IP 11.11.11.5. No matter how big the network is, these processes repeat all the time.
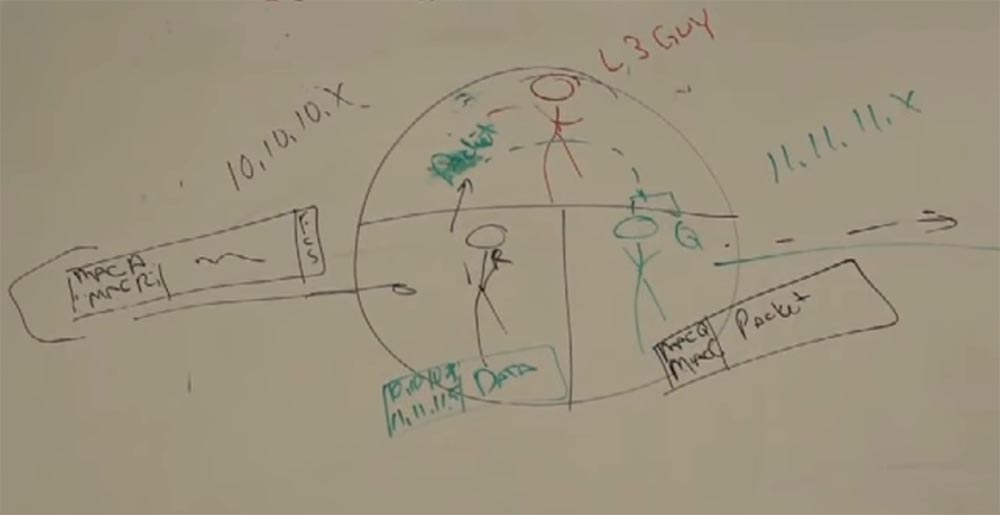
Each router has routes by default, and if the router does not have a direct connection to the 11.11.11.x network, it will send it along the route where the router can be located, which will be connected to this network. However, if there is no opportunity to enter this network and the required router is missing, the packet will be thrown out and we will receive a timeout waiting for a response from the application we need.
The main thing here is to correctly configure the network, for which address tables are used. For example, a network as large as Cisco consists of many users. When we add a new user, no matter how far he is, we attach him to one of the network nodes (router) and correctly configure his workplace, configure the network again, but this is a very simple process due to the structure of IP addresses.
But it always happens that when the time elapses, during which the router remembers the address of the subscriber, it “loses” it. The device “drops out” of the network, and in order to interact with it, you need to repeat the entire cycle of protocols anew. There is nothing difficult in this, it is not rocket science. And if you are preparing to receive a CCIE expert certificate, and I don’t know how many of those present already have such a certificate, you will indeed one day become a “cool” specialist, because testing is really difficult. But there is nothing not possible.
From my point of view, you should know what routing is, but you don’t have to know EIGRP, which is proprietary (that is, proprietary software owned by the company) for Cisco. This is a kind of “cold” type of BGP protocol, which is used on the Internet, there are millions of routes, it is really client-oriented server software. But all the other routers and protocols do almost the same around the world, they work on the same general principle.
So we discussed this principle of data transfer. Let me remind you - we have two different switches. Suppose these two people or two devices are on the same floor. I will give an example from life, so that you understand the meaning.
In 1995, in Cary, North Carolina, the Catholic Church wanted to build a Catholic school. My bride was a Catholic, and I was a Baptist, and I still remain. So, she told me: “So that we could be married without any problems, it would be nice if you would help in the construction of this school, because I want my children to grow up as Catholics”! I replied: "Fine, even though I am not a Catholic, but I will help them, because in any case you will become my wife."
It was a new construction, they wanted to introduce computer training there, so it was necessary to create a network, connect all the classes into one. It was necessary to literally connect each desk to the switch, and it was quite expensive. I went there and met the team leader networkers, who said that they want to create a separate network for each of the 3 floors in each building.
At the same time on each floor there will be one switch for students, one switch for teachers and another switch to control these two. They wanted to manage networks from the outside, connect all devices to it and share them with routers. Because, in their opinion, the students will be very cunning with these networks, if the network is one. To prevent this from happening, you need to isolate these networks from each other as much as possible. I just got there from Blue Cross Blue Shield, a large North Carolina health care organization, and I had experience working with large networks. Therefore, I knew that the proposed option would be too expensive. I contacted the second person in their team and explained this by offering a cheaper option. I said: “What will happen if we make one device, in which there will be ports for students, and ports for teachers, and ports for management - and all this in one device”!
They asked me, would it be safe - all in one device? And I answered them - is it less safe than three separate physical switches, each of which can be simply broken? What I suggested is a VLAN technology — a virtual local area network that is more secure than a network of physical devices and is much cheaper.
Today we use such networks, we use VLAN every day. We use them, for example, for voice transmission, we use such networks in IP-telephony. By default, the voice in the Cicso switches is separated in VLAN 200, you can change this in the settings. We share voice and data, due to this, QoS prioritization is possible. What else can VLAN be useful for? For wireless networks. We use VLAN to separate voice networks, video networks, data networks, guest networks within our one wireless access point. Different VLANs satisfy different needs, have different capabilities and limitations.
That is why they are used to separate, for example, the accounting department from others. What about security? When you first connect to the network as a new user, we need to know who you are, whether to let you in or block you. What if your system has one of the wonderful little ailments, which is called a virus? We check who you are and if you are infected. All this is done using the 802.1X protocol. He determines that each device that connects to the network must have a login, which Cisco uses to control access to the network. We look at your device and see if you updated your antivirus program, in particular. And if you have not done this, or have disabled your antivirus, then your device is placed on a special virtual network called the "corrective VLAN". We put you in quarantine, but you will not be there forever, because we will try to rectify the situation. A window will pop up on your monitor, where it will be said that you have disabled the antivirus, but will get access as soon as you turn it on. However, if the reason is different, and you are really infected or do not want to enable antivirus, then you will be placed in a special virtual network. We simply add a column to the table that we just made, and assign you a VLAN tag, and we will see how you enter the switch with this tag and how you leave it. Regardless of whether it is a network of engineering workers, or accountants, or a marketing department, or IP telephony, we can isolate you by MAC address or login, separate from the healthy segment of the network, isolate you by port.

All this is possible thanks to virtualization technology, since if there are two different physical switches, they can be combined into one. Nowadays, all modern switches support VLAN technology and the number of possible VLANs is often associated with the number of ports. For example, the smallest switch, Cisco 2900 Series Router supports the ability to create up to 1000 virtual networks, while the most advanced one - up to 4000. If more than 50 VLANs are created on one switch, then this is really a large network.
Let's return to the example with the Catholic school, they would have only 4 VLANs. But the technology has just emerged, and as we remember, the full implementation of the standard takes up to 18-23 months. Recall the integrated circuits (ASIC) installed inside the switches. CISCO — , , , ASIC . , . , . , iOS, .
-, , Cisco Nexus 5000, . - – , . VLAN' , 90- , , .
, , , . 95-97 ? VLAN Trunking — , (VLAN), . Cisco.
, , . , , .

, 48 , 62, VLAN 2 , 48 . 14 , , $400 . Cisco? , , VLAN Trunk. , . , , VLAN.
$1000 . , ? , 2. , EtherChannel, , .
, Cisco 95-97 . 12% . , ASIC , . ? , . , .
: Cisco . , , . , Cisco , . ? , - , . , , . , - . , - .
, : PoE QoS. , , .
, , , ? Cisco , ? . . , . - , , Cisco. , , . , Cisco , . , . – . , , . , , , AT&T, 2 .
, , Cisco. . 3- .
Cisco 1996 . , . « VLAN». 1 , 70 . , 3750, 12 , . , , , . . L2 , VLAN', . L3 , VLAN', , (). , , , 48 . , 3516 3750, , L2 , , L3. , — . , , .
() – Cisco, , . . ? , , , , .
, , 2 3 , . , — . ? , . Cisco 4510R, 3 . , 4506 , , , mp3 .

, , . 2? , . ? Power Supply. . . , , . , . , , . – , , , iOS. , . , Super 7, , , 860 iOS, Linux. . 2 , , , , , . IP- . . , – , .

, , (Line Card), Gigabit Ethernet. (SFP) , , 5 . Line Card, .
Catalist 4500, . , - . , 2 , , .
- Cisco 6500? 90- , 2 $ 25% . – 2 . . , 2 $, .
, 2 , Cisco Nexus -, 15 . . Nexus 2002 «» MDS 9500, (Fabric Director Switches), .

Cisco Catalist 6500 – , 6500 , 720. 4500 19 . $, 720 6500, , , ( ), 35 . $. . 2 3 , , Cisco. , . , , , 1, 10 40 Ethernet, 48- (Line Card) 100- Ethernet , . ASIC. , ASIC.

Continued:
FastTrack Training. "Network Basics". "Switches from Cisco". Eddie Martin December 2012
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The Truth About VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?

We continue the cycle of 27 articles based on his lectures:
')
01/02: “Understanding the OSI Model” Part 1 / Part 2
03: "Understanding the Cisco Architecture"
04/05: “The Basics of Switching or Switches” Part 1 / Part 2
06: "Switches from Cisco"
07: "Area of use of network switches, the value of Cisco switches"
08/09: "Basics of a Wireless LAN" Part 1 / Part 2
10: "Products in the field of wireless LAN"
11: The Value of Cisco Wireless LANs
12: Routing Basics
13: "The structure of routers, routing platforms from Cisco"
14: The Value of Cisco Routers
15/16: “The Basics of Data Centers” Part 1 / Part 2
17: "Equipment for data centers"
18: "The Value of Cisco in Data Centers"
19/20/21: "The Basics of Telephony" Part 1 / Part 2 / Part 3
22: "Cisco Collaboration Software"
23: The Value of Collaboration Products from Cisco
24: "The Basics of Security"
25: "Cisco Security Software"
26: "The Value of Cisco Security Products"
27: "Understanding Cisco Architectural Games (Review)"
And here is the fifth one.
FastTrack Training. "Network Basics". "Basics of switching or switches." Part two. Eddie Martin December 2012
I think what happens is the natural progress of network development. But there are some things that need a push, you need to apply force to start the process. The first router served as a personal computer, and for this was a special software. But the networks grew so fast that they needed separate processors that could handle the huge traffic. Computers also evolved, multi-core processors appeared. It was even possible to reverse the development process in some way using the SDN (Software Defined Network) - software-defined networks where the management process is separated from the data transfer process. But such an approach can harm Cisco, because there are areas where SDNs are completely inapplicable and the servers will be completely unsuitable, they will hang right away.

Let's talk about streaming, live video, converting traditional telephony and transcoding video on a huge or regular scale using SDN. We already have our ASIC microchips, which may be useful, or maybe not. Cisco has the necessary base to participate in this, but it will be a slow advance. Cisco always says that we have our own software for our routers, and for future generations of routers, the future generation of ISR (Integrated Service Router). Although it will not be called an ISR, it will still be a software router. But it will have fewer features than our second-generation ISR, so I do not think there will be a server capable of transmitting such a huge amount of information, or local VLANs of such power. But if we are talking about the transfer of small data blocks, this technology is justified and can be applied. You know that there are companies that persist in promoting the SDN idea everywhere, but Cisco does not want to become a suicide and promote it until you have to. We do not want to hurt our current products.
I was in Boston at one such company and spoke in great detail with one of its employees working on SDN. I made sure that they do not leave the ideas of vigorous promotion of such products and I have revealed the whole essence in detail. We cannot stop this process, this is a market trend, and it will develop further, whether Cisco will participate in this or not. Cooperation in this area will cost from 9 to 53 billion dollars and we must make every effort to "be in the game." But is this path valuable? Maybe yes, maybe not. Maybe we can do something with our chips and our capabilities.

I was asked a question about the network address, why it looks like this - 10.10.10.7, why it is needed, how the personal computer recognizes IP and how we can find out who owns this address. This is a very good question! Tell me, who among you made purchases on Amazon or Ebay? I see many. Did anyone make purchases on the Cisco website? Not very much, as I look! And what is the IP address of these resources, you know? Hardly. Remember the three important things you should get from DHCP? What is DNS (Domain Name Services)?

DNS allows you to not remember the numbers and use symbols instead of numbers. You remember the names well, but you don’t remember the number sequences well. I have to admit that I am the opposite. I cannot remember the names of all my cousins and sisters, but I remember their phone numbers. I'm serious. I have two sisters and I do not remember their middle names, but I remember their phone numbers. Each of you remembers what kind your mail server has, for example, mail.cisco.com. So, when you use your mail, you are not interested in its IP-address and the recipient's IP-address. In the switch, we have an internal DNS server located at the application level, which is used for all devices connected to it. So? our mail server mail.cisco.com wants to send mail, but to do this, it must use a transport protocol that does not understand the names, but understands the IP addresses. And because our DNS server accesses the server and says: "I have to convert mail.cisco.com to an IP address." And he does it. But what if we want to access external resources on the Internet? Say to google. In this case, we have a similar interaction with an external DNS server, which is already a DNS server for the entire Internet network. Thus, we have interactions with internal and external DNS servers.

What are the benefits of using domain names, not IP addresses? Think about the network configuration issue. Cisco employs about 70 thousand people. Imagine that we gave each of them a separate IP address for their mail. And soon, for some reason, you would like to change the address to another one, what would we do? We would be forced to change the configuration of all 70 thousand clients. But what if we put a DNS server on this network? Thanks to him, we could change the IP address from 10.10.10.9 to 10.10.10.10 automatically. We would change this entry on the DNS server and the changes would automatically apply to the network. That's cool. This way we can easily deploy our application and the DNS will do all the other work on the network.
The DNS server is a very powerful handler of information coming in via the DHCP protocol, which allows computers to automatically obtain an IP address. At the same time, the switch knows where you are located physically, because it uses this table of MAC addresses.

Suppose that I want to connect with IP 11.11.11.5, let's say this is a network printer on which you can print a document — this unit at the top almost in the middle will be our printer.

Let's give it the name printer.2floor.cisco.com, this is a well-known printer on the second floor. So, if we want to print, we need to resolve the DNS and get an IP address that matches this name. We will add its IP to the DATA block, where 10.10.10.7 already exists.
Now compare these addresses. Are they on the same network? Of course not!

The network number does not match, so a router is needed here, because if a computer is from another network, then it is connected to it via a router. This is the gateway, the gateway to the rest of the Internet world outside our network. One router (router), one entry point opens the gate to a world where there are millions, millions and millions of recipients, but among them there is one that you want to communicate with. So, if the device is with you on the same network, then you can communicate directly, via a switch, and if in different networks, then you get in touch via a router.
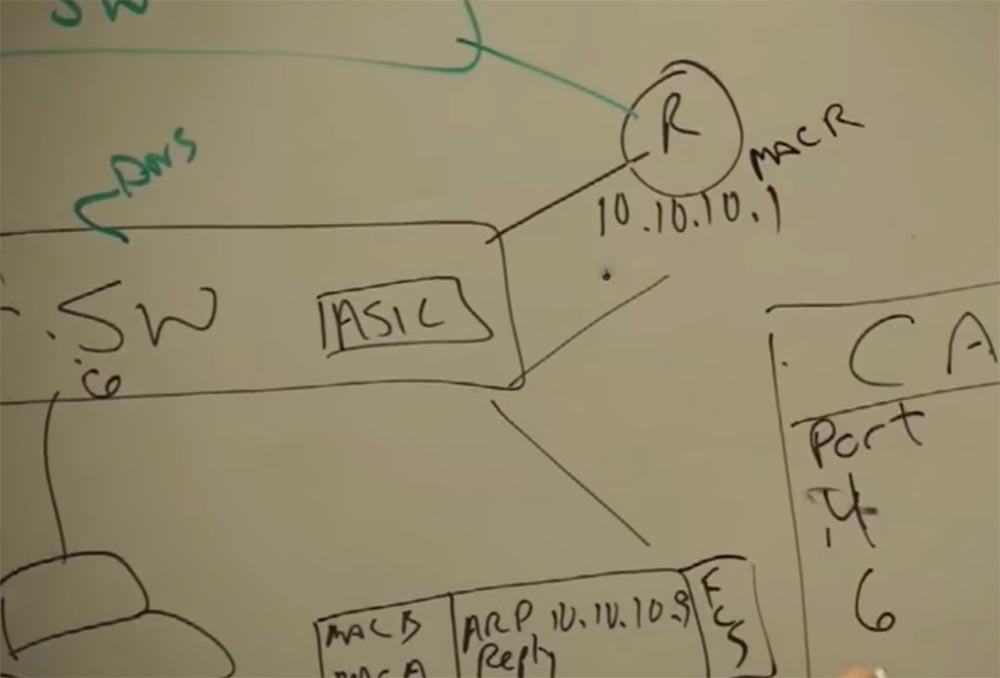
So, I'm going to send data to my 10.10.10.1 router, but what should I do if I don't know its MAC address? I know that it is in my network, but I do not remember the address, but the router remembers it! It has an ARP cache that stores IP addresses and MAC addresses that you “talked to” for 5 minutes. The duration of the “memory” of the router, depending on the operating system, is approximately 300 seconds, and if you have not accessed it again during this time, it will be disabled. And if you are going to send the data again, you say - I have to contact my default gateway again, and the whole cycle of device recognition within the network is repeated.

Let our router have a MAC address R, and it is connected to port 16 of our switch.

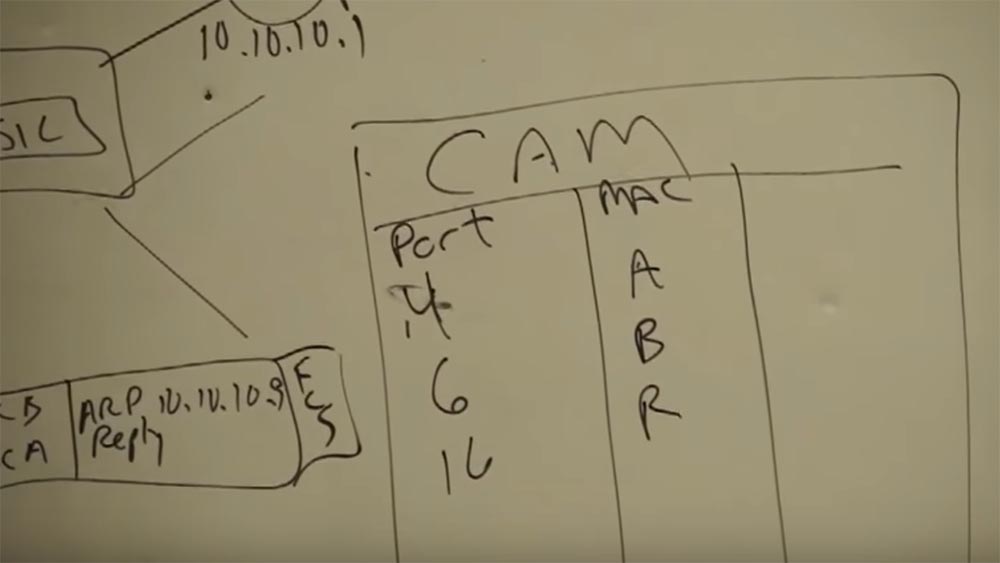
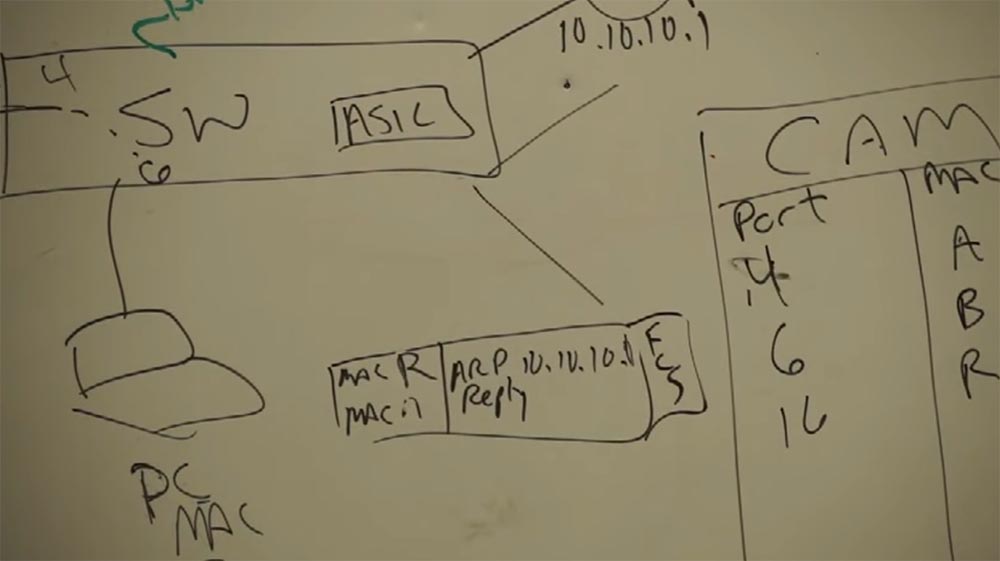
And when we access the printer, everything repeats according to the scheme - request, response, address check, and this happens an infinite number of times. And when I send my data packet to the printer, it gets on the switch, and the switch asks: “Oh, are you still here, number 4? Do you want to another network? Then I send you to that guy whose name is the router! ” And the router forwards your packet to the printer. It does not matter if it is the smallest or largest router in the world - they all work on the same principle.

Consider the case when the router connects two networks, on the one hand it has the address 11.11.11.x, and on the other 10.10.10.x. Of course, the router can connect at least 2 million networks. The router has 2 types of workers. Each network that is connected to the router will have its own “boyfriend” located on the second level of the OSI model (L2), which will determine the MAC address of the device for the network.

Let for 10.10.10.x the MAC address will be R, and for 11.11.11.x Q. These workers interact at the physical (L2) level. These two "guys", R and Q, each work in their own sector, but they both work together on the same task. And they are controlled by the third guy, the smartest, let's call him L3 - this is the third level.

So, we have a frame transmission from the MAC address A (sender) to the MAC address R (router). The frame is successfully delivered to the worker who is on the second level of the 10.10.10.x network. He performs a checksum check (FCS), receives a packet from the frame and does not know what to do with it, since the second level can work only with MAC addresses, and the packet indicates that we want to send it from the device with the address 10.10. 10.7 to the device with the address 11.11.11.5 (printer). A worker “understands” that he does not have enough data to successfully transmit a packet, and addresses “upward” to the worker L3.
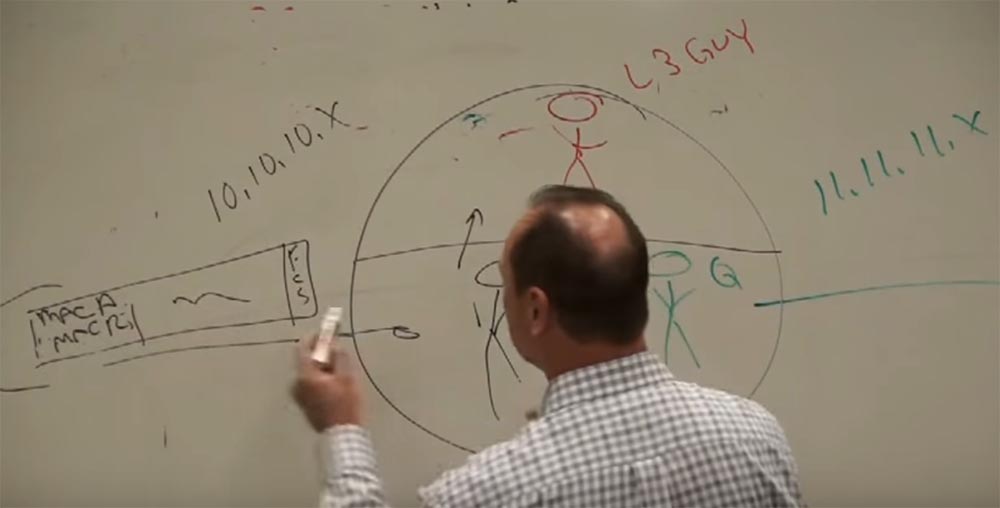
It's like in school - you don't know how to do the task, but you know a classmate who knows how to do it. And our router refers to such a knowledgeable “classmate” whose name is L3.

R tells him “Hey, level 3, do you know all the IP addresses? I have a package that needs to be delivered 11.11.11.5, delivered to the address - I have a drink ”! Well, you know how it happens! You transmit a packet to level 3, because level 3 is the packet level. It has tables in which there are all addresses of all networks, routing tables. And this serious guy from above, who knows what to do with the package, takes it and gives it to the guy named Q, in accordance with the routing table, which shows the routes and that this guy is responsible for the network we need, saying, " are you kind enough to deliver this to 11.11.11.5? ”and Q takes the packet, puts it in a solid frame, and what does he see? He sees the recipient’s address, but he hasn’t communicated with the device for which the IP address ends with 5 , he already forgot his MAC address! And now he shouts to his whole network: “Hey, is there anyone here who VUT 5 "? He uses the ARP protocol to determine the network address.

Suppose that it is answered by a device that has a MAC address of C. And now it marks the package “From MAC Q to MAC C” and sends it to the recipient with IP 11.11.11.5. No matter how big the network is, these processes repeat all the time.

Each router has routes by default, and if the router does not have a direct connection to the 11.11.11.x network, it will send it along the route where the router can be located, which will be connected to this network. However, if there is no opportunity to enter this network and the required router is missing, the packet will be thrown out and we will receive a timeout waiting for a response from the application we need.
The main thing here is to correctly configure the network, for which address tables are used. For example, a network as large as Cisco consists of many users. When we add a new user, no matter how far he is, we attach him to one of the network nodes (router) and correctly configure his workplace, configure the network again, but this is a very simple process due to the structure of IP addresses.
But it always happens that when the time elapses, during which the router remembers the address of the subscriber, it “loses” it. The device “drops out” of the network, and in order to interact with it, you need to repeat the entire cycle of protocols anew. There is nothing difficult in this, it is not rocket science. And if you are preparing to receive a CCIE expert certificate, and I don’t know how many of those present already have such a certificate, you will indeed one day become a “cool” specialist, because testing is really difficult. But there is nothing not possible.
From my point of view, you should know what routing is, but you don’t have to know EIGRP, which is proprietary (that is, proprietary software owned by the company) for Cisco. This is a kind of “cold” type of BGP protocol, which is used on the Internet, there are millions of routes, it is really client-oriented server software. But all the other routers and protocols do almost the same around the world, they work on the same general principle.
So we discussed this principle of data transfer. Let me remind you - we have two different switches. Suppose these two people or two devices are on the same floor. I will give an example from life, so that you understand the meaning.
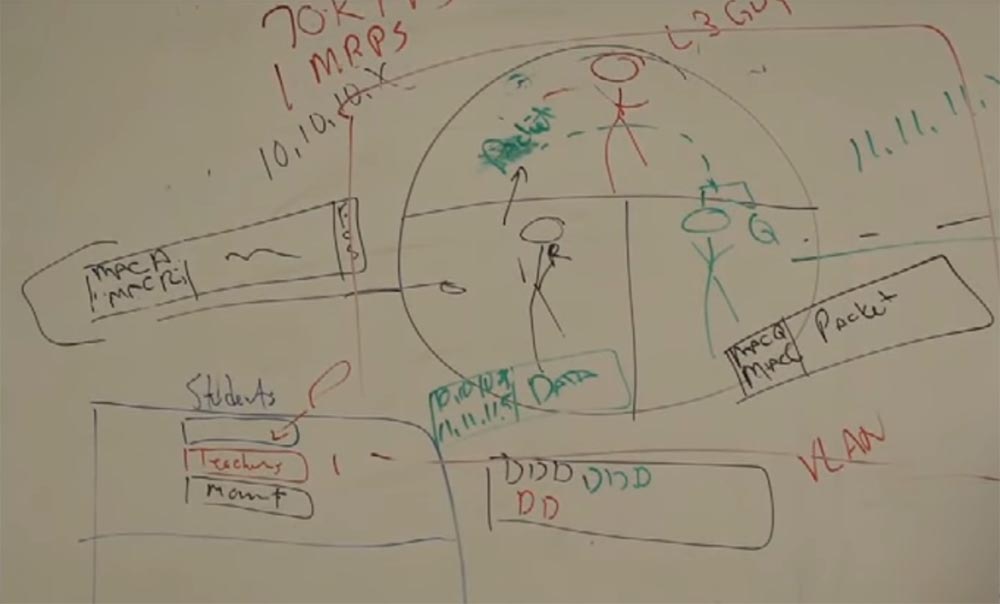
In 1995, in Cary, North Carolina, the Catholic Church wanted to build a Catholic school. My bride was a Catholic, and I was a Baptist, and I still remain. So, she told me: “So that we could be married without any problems, it would be nice if you would help in the construction of this school, because I want my children to grow up as Catholics”! I replied: "Fine, even though I am not a Catholic, but I will help them, because in any case you will become my wife."
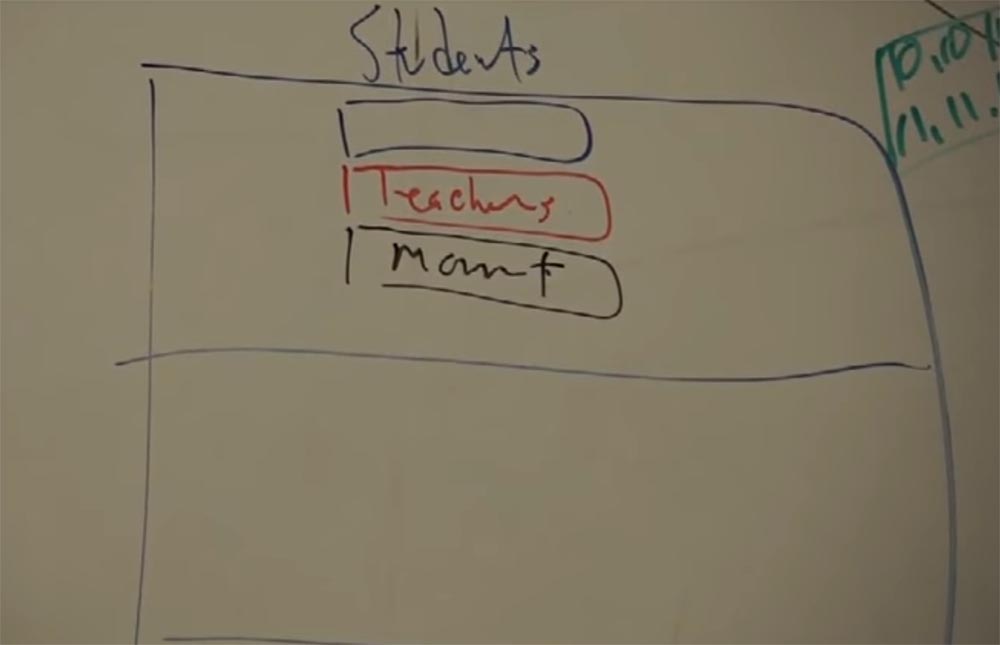
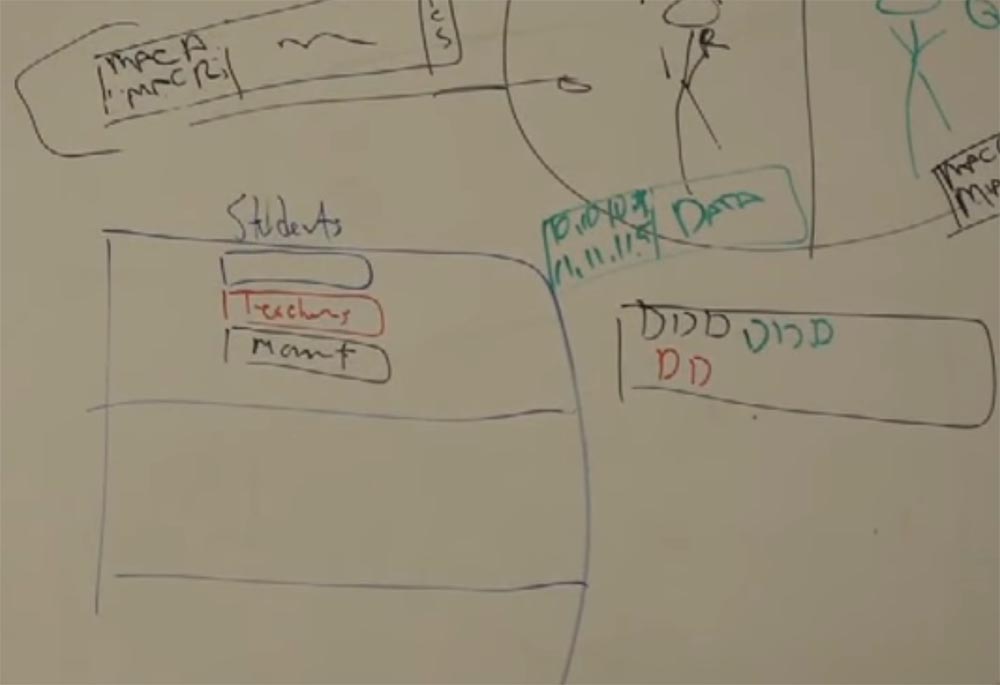
It was a new construction, they wanted to introduce computer training there, so it was necessary to create a network, connect all the classes into one. It was necessary to literally connect each desk to the switch, and it was quite expensive. I went there and met the team leader networkers, who said that they want to create a separate network for each of the 3 floors in each building.

At the same time on each floor there will be one switch for students, one switch for teachers and another switch to control these two. They wanted to manage networks from the outside, connect all devices to it and share them with routers. Because, in their opinion, the students will be very cunning with these networks, if the network is one. To prevent this from happening, you need to isolate these networks from each other as much as possible. I just got there from Blue Cross Blue Shield, a large North Carolina health care organization, and I had experience working with large networks. Therefore, I knew that the proposed option would be too expensive. I contacted the second person in their team and explained this by offering a cheaper option. I said: “What will happen if we make one device, in which there will be ports for students, and ports for teachers, and ports for management - and all this in one device”!

They asked me, would it be safe - all in one device? And I answered them - is it less safe than three separate physical switches, each of which can be simply broken? What I suggested is a VLAN technology — a virtual local area network that is more secure than a network of physical devices and is much cheaper.
Today we use such networks, we use VLAN every day. We use them, for example, for voice transmission, we use such networks in IP-telephony. By default, the voice in the Cicso switches is separated in VLAN 200, you can change this in the settings. We share voice and data, due to this, QoS prioritization is possible. What else can VLAN be useful for? For wireless networks. We use VLAN to separate voice networks, video networks, data networks, guest networks within our one wireless access point. Different VLANs satisfy different needs, have different capabilities and limitations.
That is why they are used to separate, for example, the accounting department from others. What about security? When you first connect to the network as a new user, we need to know who you are, whether to let you in or block you. What if your system has one of the wonderful little ailments, which is called a virus? We check who you are and if you are infected. All this is done using the 802.1X protocol. He determines that each device that connects to the network must have a login, which Cisco uses to control access to the network. We look at your device and see if you updated your antivirus program, in particular. And if you have not done this, or have disabled your antivirus, then your device is placed on a special virtual network called the "corrective VLAN". We put you in quarantine, but you will not be there forever, because we will try to rectify the situation. A window will pop up on your monitor, where it will be said that you have disabled the antivirus, but will get access as soon as you turn it on. However, if the reason is different, and you are really infected or do not want to enable antivirus, then you will be placed in a special virtual network. We simply add a column to the table that we just made, and assign you a VLAN tag, and we will see how you enter the switch with this tag and how you leave it. Regardless of whether it is a network of engineering workers, or accountants, or a marketing department, or IP telephony, we can isolate you by MAC address or login, separate from the healthy segment of the network, isolate you by port.

All this is possible thanks to virtualization technology, since if there are two different physical switches, they can be combined into one. Nowadays, all modern switches support VLAN technology and the number of possible VLANs is often associated with the number of ports. For example, the smallest switch, Cisco 2900 Series Router supports the ability to create up to 1000 virtual networks, while the most advanced one - up to 4000. If more than 50 VLANs are created on one switch, then this is really a large network.
Let's return to the example with the Catholic school, they would have only 4 VLANs. But the technology has just emerged, and as we remember, the full implementation of the standard takes up to 18-23 months. Recall the integrated circuits (ASIC) installed inside the switches. CISCO — , , , ASIC . , . , . , iOS, .
-, , Cisco Nexus 5000, . - – , . VLAN' , 90- , , .
, , , . 95-97 ? VLAN Trunking — , (VLAN), . Cisco.
, , . , , .

, 48 , 62, VLAN 2 , 48 . 14 , , $400 . Cisco? , , VLAN Trunk. , . , , VLAN.

$1000 . , ? , 2. , EtherChannel, , .

, Cisco 95-97 . 12% . , ASIC , . ? , . , .
: Cisco . , , . , Cisco , . ? , - , . , , . , - . , - .
, : PoE QoS. , , .
, , , ? Cisco , ? . . , . - , , Cisco. , , . , Cisco , . , . – . , , . , , , AT&T, 2 .
, , Cisco. . 3- .

Cisco 1996 . , . « VLAN». 1 , 70 . , 3750, 12 , . , , , . . L2 , VLAN', . L3 , VLAN', , (). , , , 48 . , 3516 3750, , L2 , , L3. , — . , , .

() – Cisco, , . . ? , , , , .
, , 2 3 , . , — . ? , . Cisco 4510R, 3 . , 4506 , , , mp3 .

, , . 2? , . ? Power Supply. . . , , . , . , , . – , , , iOS. , . , Super 7, , , 860 iOS, Linux. . 2 , , , , , . IP- . . , – , .

, , (Line Card), Gigabit Ethernet. (SFP) , , 5 . Line Card, .
Catalist 4500, . , - . , 2 , , .
- Cisco 6500? 90- , 2 $ 25% . – 2 . . , 2 $, .
, 2 , Cisco Nexus -, 15 . . Nexus 2002 «» MDS 9500, (Fabric Director Switches), .

Cisco Catalist 6500 – , 6500 , 720. 4500 19 . $, 720 6500, , , ( ), 35 . $. . 2 3 , , Cisco. , . , , , 1, 10 40 Ethernet, 48- (Line Card) 100- Ethernet , . ASIC. , ASIC.

Continued:
FastTrack Training. "Network Basics". "Switches from Cisco". Eddie Martin December 2012
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The Truth About VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
Source: https://habr.com/ru/post/350022/
All Articles