We receive the list of passengers of flights of the largest air carrier of Ukraine
This article discusses how I discovered a vulnerability that allowed me to get a list of passengers on flights of Ukraine International Airlines, Ukraine’s largest air carrier, and about the company's attitude to the fact that such information is publicly available.
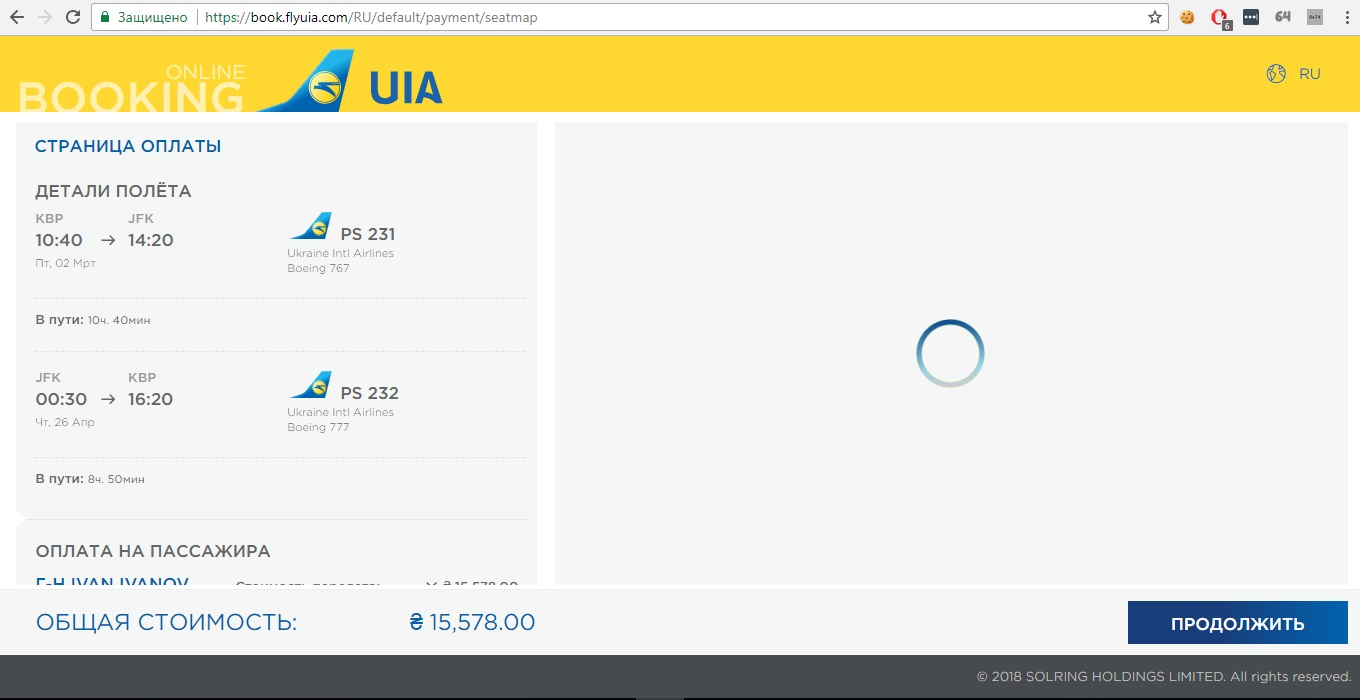
More than a month ago, I began to prepare for a vacation, and it was just time to book airline tickets. So I ended up on the UIA airline website . In the process of selecting seats on the plane, the page that was supposed to display the scheme of seats did not want to load at all.
')
I decided to open a developer tool in Google Chrome to try to understand what the problem is. After examining the requests to the server, I saw that the data about the available places was returned by the server.
Having tried several different browsers, I still did not solve the problem, however I noticed that the request that returns the list of available places was executed in all browsers successfully, despite the fact that session cookies were only available in Google Chrome.
The request was as follows:
where XXXXXX is the PNR, or so-called reservation code.
The answer of the server was the following in all browsers:
This meant that passenger information was available to any user from any device only by PNR code. Consequently, knowing the reservation number, any user could get such passenger data such as last name, first name, adult or child, flight number, departure and arrival airports, departure time.
I wondered what other “surprises” this service keeps.
Having continued issuing tickets, I chose the item for ordering a place for baggage.
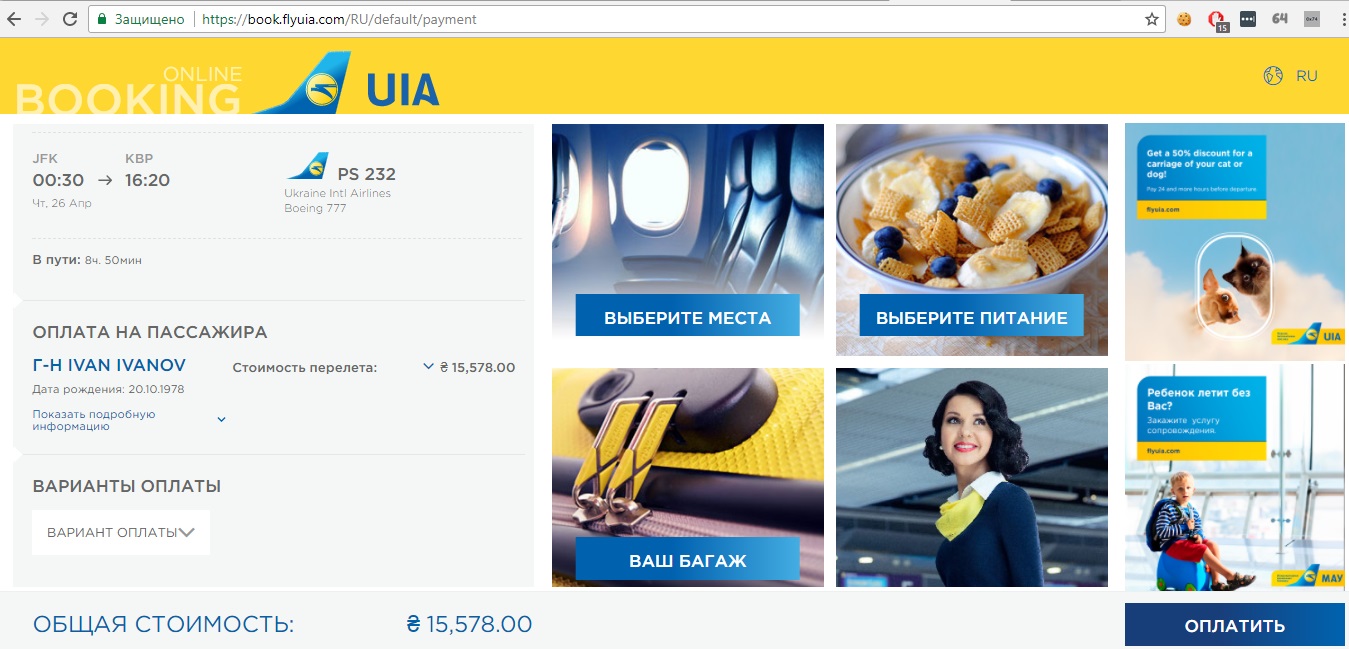
The request had a similar look:
However, the server’s response contained a bit more information about the user:
In this way, such information about the passenger as his date of birth was added.
In fact, we are not talking about one passenger, but about all the passengers included in this booking. For example, I made out tickets for the whole family and in the above requests contained information not only about me, but also about the spouse and children.
Generally speaking, in terms of the law of Ukraine on the protection of personal information, personal
data is information or a collection of information about an individual that is identified or can be specifically identified. The data available in the above requests allow in some cases to uniquely identify a person without even having a date of birth. Such a case is the option if the reservation contains data about several persons. Since such persons are at least familiar, and in many cases relatives, it will not be difficult to identify them using social networks. Thus, in my opinion, already existing data can be considered personal, and the fact of public access to it is a violation of the law on the protection of personal data. But let's not get distracted and continue.
Exploring further "features" of the service, I went to the payment page. Here I was waiting for a new surprise. The request was:
It was also executed in all browsers without session cookies:
The request contains different payment information, but for us the presence of such a parameter as the PNR code is more important. As you can see, the request contains an incremental transaction ID, which means that when going through this value to a greater or lesser side, attackers will be able to get real booking codes and use them in previous requests to get detailed information about the company's customers using the PNR code without using a brute force attack.
As a result, a set of all vulnerable requests allows attackers to organize a service that will be able to compile a list of passengers of airline flights in real time unnoticed by resource managers. However, the passenger list is not public information and is protected for security purposes by airlines and, in some countries, by laws. Access to such data is usually only employees of companies and certain government agencies. The more my surprise was when, when contacting UIA's client support and informing them about the presence of these vulnerabilities, in the process of correspondence and clarifying the status of my application I received the following answer:
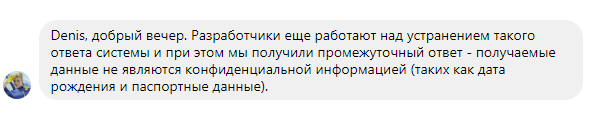
However, when asked if they provide a list of passengers at the request of clients, they answered me negatively.
Despite this strange response from the company, the developers eliminated all the above vulnerabilities within a month, which reassured me as a client.
As a separate point, I would like to draw attention to the fact that, again, as is the case with other large companies, there is no separate communication channel in MAU for reporting vulnerabilities. When I was asked to contact me with the security service or responsible developers, I was refused:

Summing up, I want to say the following.
Airlines should take care of the safety of their passengers not only at airports and on board the aircraft, but also online. After all, passenger data is very sensitive information. Owning it, thieves can rob the victim's apartment while she is away. An ex-spouse may pursue his ex-wife, knowing about her movements. An attacker, having received the booking codes, can through the airline’s website cancel the passenger check in bulk, which could potentially result in flight delays. Public information about the movements of business competitors may be detrimental to their companies. There are many ways to use such information with malicious intent and it should be protected accordingly.
More than a month ago, I began to prepare for a vacation, and it was just time to book airline tickets. So I ended up on the UIA airline website . In the process of selecting seats on the plane, the page that was supposed to display the scheme of seats did not want to load at all.

')
I decided to open a developer tool in Google Chrome to try to understand what the problem is. After examining the requests to the server, I saw that the data about the available places was returned by the server.
Having tried several different browsers, I still did not solve the problem, however I noticed that the request that returns the list of available places was executed in all browsers successfully, despite the fact that session cookies were only available in Google Chrome.
The request was as follows:
https://bookapi.flyuia.com/ancillary/seatmap?pnr=XXXXXX¤cy=USD&flyuiacountrycode=uk&flyuialanguagecode=ru&locale=RU where XXXXXX is the PNR, or so-called reservation code.
The answer of the server was the following in all browsers:
[ { "paxDetails" : { "uniqueId" : "2", "firstName" : "IVANOV", "title" : "- (Ms.)", "lastName" : "IVAN", "paxType" : "Adult", "cartPaxId" : "b1da2ebf-4525-35bd-afc1-b1f448132ad3" }, "segmentDetails" : [ { "company" : "PS", "bookingClass" : "B", "flightNumber" : "1234", "departureAirport" : "KBP", "arrivalAirport" : "JFK", "departureDateTime" : "2018-02-01T00:05", "operatingAirline" : "PS" } ], "segmentId" : "1", "isAvailableForCheckIn" : true, "seat_rows" : [ { "seats" : [ { "id" : "aab4ca38-2c28-1f13-359d-4ad264d53a0e_1e80aae3-a68b-44de-ae14-aff839563612", "occupation" : "AVAILABLE", "letter" : "A", "rowNumber" : 4, "seatCharacteristics" : [ "W", "CH", "EK", "H", "for_infant" ], "price" : { "amount" : "16.00", "currency" : "USD" }, "class" : "ECONOMY", "seat_type" : "SEAT", "ticket_value" : "FD3A" },...] This meant that passenger information was available to any user from any device only by PNR code. Consequently, knowing the reservation number, any user could get such passenger data such as last name, first name, adult or child, flight number, departure and arrival airports, departure time.
I wondered what other “surprises” this service keeps.
Having continued issuing tickets, I chose the item for ordering a place for baggage.

The request had a similar look:
https://bookapi.flyuia.com/ancillary/luggage?pnr=XXXXXX¤cy=USD&locale=RU However, the server’s response contained a bit more information about the user:
[ { "paxDetails" : { "uniqueId" : "2", "firstName" : "ivan", "title" : "-", "lastName" : "ivanov", "paxType" : "Adult", "dateOfBirth" : "1978-10-20", "cartPaxId" : "a30928c1-219b-8d15-8345-b517f0fda360" },...] In this way, such information about the passenger as his date of birth was added.
In fact, we are not talking about one passenger, but about all the passengers included in this booking. For example, I made out tickets for the whole family and in the above requests contained information not only about me, but also about the spouse and children.
Generally speaking, in terms of the law of Ukraine on the protection of personal information, personal
data is information or a collection of information about an individual that is identified or can be specifically identified. The data available in the above requests allow in some cases to uniquely identify a person without even having a date of birth. Such a case is the option if the reservation contains data about several persons. Since such persons are at least familiar, and in many cases relatives, it will not be difficult to identify them using social networks. Thus, in my opinion, already existing data can be considered personal, and the fact of public access to it is a violation of the law on the protection of personal data. But let's not get distracted and continue.
Exploring further "features" of the service, I went to the payment page. Here I was waiting for a new surprise. The request was:
https://bookapi.flyuia.com/payportal/transaction/123456?flyuiacountrycode=ua&flyuialanguagecode=ru&locale=RU It was also executed in all browsers without session cookies:
{ "id" : 211334, "payportal" : "UkrEximBank", "creationTime" : "2017-12-25 14:32:13", "status" : "INIT", "amount" : 15578.00, "currency" : "UAH", "errorCode" : 0, "errorCategory" : "UNDEFINED", "data" : "{\"Locale\":\"ru_RU\",\"ORDER\":\"000000450187\",\"PosId\":\"12e66438b256e10f74424133\",\"Pnr\":\"XXXXXX\",\"fopType\":\"CREDIT_CARD\",\"Country\":\"492ac4aae7f43c6e6a4336f9\",\"Passenger\":\"ivanov ivan\",\"PayerEmail\":\"ivanov.ivan@gmail.com\",\"BackReference\":\"https://book.flyuia.com/RU/default/paymentstatus\",\"OaDRoute\":\"01Feb18JFKKBP-10Feb18KBPJFK\",\"LANG\":\"UKR\",\"DESC\":\"XXXXXX, ivanov ivan, 01Feb18JFKKBP-10Feb18KBPJFK\"}",...} The request contains different payment information, but for us the presence of such a parameter as the PNR code is more important. As you can see, the request contains an incremental transaction ID, which means that when going through this value to a greater or lesser side, attackers will be able to get real booking codes and use them in previous requests to get detailed information about the company's customers using the PNR code without using a brute force attack.
As a result, a set of all vulnerable requests allows attackers to organize a service that will be able to compile a list of passengers of airline flights in real time unnoticed by resource managers. However, the passenger list is not public information and is protected for security purposes by airlines and, in some countries, by laws. Access to such data is usually only employees of companies and certain government agencies. The more my surprise was when, when contacting UIA's client support and informing them about the presence of these vulnerabilities, in the process of correspondence and clarifying the status of my application I received the following answer:

However, when asked if they provide a list of passengers at the request of clients, they answered me negatively.
Despite this strange response from the company, the developers eliminated all the above vulnerabilities within a month, which reassured me as a client.
As a separate point, I would like to draw attention to the fact that, again, as is the case with other large companies, there is no separate communication channel in MAU for reporting vulnerabilities. When I was asked to contact me with the security service or responsible developers, I was refused:

Summing up, I want to say the following.
Airlines should take care of the safety of their passengers not only at airports and on board the aircraft, but also online. After all, passenger data is very sensitive information. Owning it, thieves can rob the victim's apartment while she is away. An ex-spouse may pursue his ex-wife, knowing about her movements. An attacker, having received the booking codes, can through the airline’s website cancel the passenger check in bulk, which could potentially result in flight delays. Public information about the movements of business competitors may be detrimental to their companies. There are many ways to use such information with malicious intent and it should be protected accordingly.
Source: https://habr.com/ru/post/349890/
All Articles