"Do not fit, kill!" Or the whole truth about the security of automated process control systems
Most of our customers are industrial and manufacturing companies. No matter how large and significant the front office and corporate network of such companies are, their main business is the production itself, as well as related tasks and processes. And often, solving the tasks of monitoring and responding to cyber attacks with customers, we start with a corporate network and a perimeter, and as a result we arrive at closed networks and segments of production and technological networks.
We decided to collect our experience in the protection of automated process control systems and talk about the most frequent problems and popular myths about safety in this area.

The automated process control system is a set of hardware and software designed to automate the process equipment control at industrial enterprises.
ACS TP, as a rule, has a multi-level structure:
')
The number of levels of an automated process control system, as well as its composition at each level, of course, depends on its purpose and the performance of its objective functions. At the same time, at each level of the automated control system, according to functional, territorial or other signs, other additional segments may be allocated. However, at the current stage, we limit ourselves to the general representation below.

Problem 1: the myth of the "air gap"
Many process control systems were built for a long time. At that time it was believed that technological networks and systems were completely isolated from the outside world, and therefore, ensuring information security in this area was not recognized as relevant or, at best, was not a priority. However, now the line between technological and corporate networks is more and more erased, and, moreover, Ethernet / IP and, in general, corporate networks are used in technological networks.
These processes are due to the needs of the business and, as a result of the need for network connectivity, we usually see one of the scenarios below at the Customer:
In addition, the effect of the development and mass availability of modern technologies (mobile devices and mobile Internet, USB-modems, etc.), which employees actively use for their own purposes, has an effect. Starting from operators wishing to access the Internet at the workplace, and ending with IT administrators wishing to save travel time to the final facility, located, for example, 20 km from the office.
Let us complete the picture with the problems of using USB modems in the field mentioned above. Phones like USB modems. Home routers, home storage servers and other "possibilities" of modern life. And even if the corporate and technological networks are connected in the best way - the first of the scenarios, unfortunately, in fact, this does not mean that the situation is as it should be and there are no specific places, for example, own Internet access or uncontrolled access to the corporate network. network and back.
The result is a bleak picture of the possibility of easy penetration by an attacker or malware with a connection with C & C inside the automated process control system. In general, we can formulate it as follows: everything that threatens the corporate network, in fact, threatens and technological segments . This does not mean that the technological infrastructure and the protection of the corporate network need to be transferred to the technological infrastructure and the automated process control system, but you should be aware that the risks of the information technology segments of the technology segments are no less than those of the corporate ones.
Problem 2: information security in automated process control systems and information security
Technological networks and segments at the same time are significantly different from corporate networks and systems. So, unlike a typical IT system, a typical process control system:
As a result, we often observe a situation at the end objects at the customer when some in-house development is used (neither the manufacturer nor the support of which is left), with the general shift account, the password from which cannot be changed and which coincides with the login (by analogy with famous admin / admin). If the password can be set at all, in fact, we recall, many process control systems are more than 10-15 years old.
Also, while technological systems for the most part circulate information about technological processes and control actions, the emphasis is usually placed on its availability and integrity, while the issue of confidentiality tends to receive less attention. And this is one of the additional reasons explaining the "delay" with the movement towards ensuring information security in the field of industrial control systems.
So, we have a virtually unprotected system running on outdated and unsupported software with a whole fan of vulnerabilities. Installing updates on such a system, in most cases, is impossible - because of their absence, impossibility of installation, impossibility of rebooting and other numerous reasons. Hence the conclusion: problems and vulnerabilities in technology networks and systems are even higher than in the average corporate network.
At the same time, even in the case of using systems and software supported by the manufacturer, there is usually sustained resistance from the production side to any updates aimed at eliminating security problems. And almost always, this aversion extends to any superimposed security features (by the way, it may well be justified if blocking mechanisms are somehow declared and implemented in such means, even if they are not intended to be used during implementation and future operation).
It is important to note that customers know most of these problems, including possible actions by field staff. The IS risks associated with them are covered by very tough organizational and physical security measures: prohibition of bringing various devices and external media into the territory, physical limitation of the use of equipment ports, etc. measures). However, these measures are not able to fully ensure reliable protection of the process control system.
Summarizing the situations and problems described above, the following main points can be noted: regarding the current situation with information security in the process control systems:
But no matter how limiting factors, it is still necessary to protect the process control system. In the second part of the article, we will describe how, given these problems, to fully monitor and respond to cyber attacks. Again, with live examples and case studies from customers. Do not miss!
We decided to collect our experience in the protection of automated process control systems and talk about the most frequent problems and popular myths about safety in this area.

The automated process control system is a set of hardware and software designed to automate the process equipment control at industrial enterprises.
ACS TP, as a rule, has a multi-level structure:
')
- Operator / dispatch control level (upper level).
- The level of automatic control (medium level).
- Level of input / output data of executive devices (low / field level).
The number of levels of an automated process control system, as well as its composition at each level, of course, depends on its purpose and the performance of its objective functions. At the same time, at each level of the automated control system, according to functional, territorial or other signs, other additional segments may be allocated. However, at the current stage, we limit ourselves to the general representation below.

Problem 1: the myth of the "air gap"
Many process control systems were built for a long time. At that time it was believed that technological networks and systems were completely isolated from the outside world, and therefore, ensuring information security in this area was not recognized as relevant or, at best, was not a priority. However, now the line between technological and corporate networks is more and more erased, and, moreover, Ethernet / IP and, in general, corporate networks are used in technological networks.
These processes are due to the needs of the business and, as a result of the need for network connectivity, we usually see one of the scenarios below at the Customer:
- The customer has implemented a project of interfacing and segmentation of corporate and technological networks, providing for an integrated approach to ensuring information security with connected segments. At the moment, the rarest option, but we met him at several customers.
- The corporate and technological networks of the customer are connected according to one of the schemes that are available and seem to be fairly secure IT, information security and automated process control systems. This can be as connectivity using a firewall, using a router with ACL (Access Control List), and other options up to AWP / access servers with multiple network cards (by the way, one of the most common cases). A large number of accesses are often superimposed on these schemes, including access from outside the corporate network - for ATMs installed on the territory of production, remote work of vendors of automated process control systems and other involved contractors. As a result, in fact, these schemes over time begin to transform into the following version:
- Just a PCS in a common network. It seems incredible, but unfortunately, this option is also widespread.
In addition, the effect of the development and mass availability of modern technologies (mobile devices and mobile Internet, USB-modems, etc.), which employees actively use for their own purposes, has an effect. Starting from operators wishing to access the Internet at the workplace, and ending with IT administrators wishing to save travel time to the final facility, located, for example, 20 km from the office.
Results of Pentest APCS of company A (excerpt from the report)
In the course of the work, the auditor obtained access to the remote desktop of the user’s automated workplace with the IP address 172.28.XX.YY, on which were found:
The use of VPN connections with saved credentials allowed the auditor to directly access the management of the network equipment of the technological infrastructure, as well as the equipment at the end objects using the control interfaces of the corresponding SCADA systems, directly from the identified workstations.
- Saved settings for VPN connections to segments of the technological infrastructure considered to be isolated (see figure).
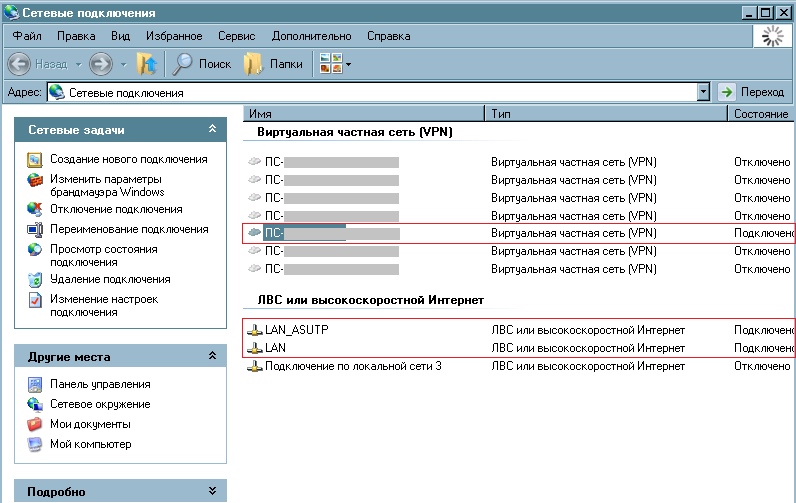
- The file that contained the access details to the technological infrastructure nodes, including the access and control details of the used SCADA systems of various manufacturers. The file was available in the general network directory to all users of the corporate network without authentication (see fig.).

The use of VPN connections with saved credentials allowed the auditor to directly access the management of the network equipment of the technological infrastructure, as well as the equipment at the end objects using the control interfaces of the corresponding SCADA systems, directly from the identified workstations.
Let us complete the picture with the problems of using USB modems in the field mentioned above. Phones like USB modems. Home routers, home storage servers and other "possibilities" of modern life. And even if the corporate and technological networks are connected in the best way - the first of the scenarios, unfortunately, in fact, this does not mean that the situation is as it should be and there are no specific places, for example, own Internet access or uncontrolled access to the corporate network. network and back.
The result is a bleak picture of the possibility of easy penetration by an attacker or malware with a connection with C & C inside the automated process control system. In general, we can formulate it as follows: everything that threatens the corporate network, in fact, threatens and technological segments . This does not mean that the technological infrastructure and the protection of the corporate network need to be transferred to the technological infrastructure and the automated process control system, but you should be aware that the risks of the information technology segments of the technology segments are no less than those of the corporate ones.
Problem 2: information security in automated process control systems and information security
Technological networks and segments at the same time are significantly different from corporate networks and systems. So, unlike a typical IT system, a typical process control system:
- It is a real-time system in which response time is critical, and delays and data loss are unacceptable.
- Along with widely used operating systems and protocols, it widely uses specialized and specially designed (proprietary).
- The duration of the life cycle is 10-15-20 years, and for some objects - up to 30 years.
- Components can be isolated, geographically remote, and physically difficult to access.
- A reset in the process control system may be unacceptable, incl. it is often impossible to install any updates, etc.
As a result, we often observe a situation at the end objects at the customer when some in-house development is used (neither the manufacturer nor the support of which is left), with the general shift account, the password from which cannot be changed and which coincides with the login (by analogy with famous admin / admin). If the password can be set at all, in fact, we recall, many process control systems are more than 10-15 years old.
Results of Pentest APCS of company B (excerpt from the report)
A study of the technological network diagrams identified by the auditor and the ways of their interfacing with user segments showed that the nodes with IP addresses 10.65.XX.YY, 10.65.XX.ZZ function as a router between the user and technology networks. Access to these devices is possible via SSH using the credentials of the root user account with an easy-to-use root password. Nodes with the above IP addresses after gaining access to them were identified and turned out to be PSI system controllers (see fig.).

Working on these SSH service devices with the ability to transfer graphical sessions and support for SSH tunnels allowed the auditor to organize traffic tunneling and conduct selective scanning of technological network nodes through the PSI system controllers, a subsequent attack on the technological network password protection subsystem and access to the devices isolated from the user network. segment.
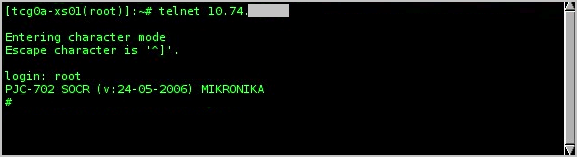
In particular, the auditor obtained access to the technological network based on MIKRONIKA equipment, for which access was made via Telnet using the credentials of a root account that does not have a password set up for remote privileged access to devices (see the figure).

Working on these SSH service devices with the ability to transfer graphical sessions and support for SSH tunnels allowed the auditor to organize traffic tunneling and conduct selective scanning of technological network nodes through the PSI system controllers, a subsequent attack on the technological network password protection subsystem and access to the devices isolated from the user network. segment.
In particular, the auditor obtained access to the technological network based on MIKRONIKA equipment, for which access was made via Telnet using the credentials of a root account that does not have a password set up for remote privileged access to devices (see the figure).

Also, while technological systems for the most part circulate information about technological processes and control actions, the emphasis is usually placed on its availability and integrity, while the issue of confidentiality tends to receive less attention. And this is one of the additional reasons explaining the "delay" with the movement towards ensuring information security in the field of industrial control systems.
So, we have a virtually unprotected system running on outdated and unsupported software with a whole fan of vulnerabilities. Installing updates on such a system, in most cases, is impossible - because of their absence, impossibility of installation, impossibility of rebooting and other numerous reasons. Hence the conclusion: problems and vulnerabilities in technology networks and systems are even higher than in the average corporate network.
At the same time, even in the case of using systems and software supported by the manufacturer, there is usually sustained resistance from the production side to any updates aimed at eliminating security problems. And almost always, this aversion extends to any superimposed security features (by the way, it may well be justified if blocking mechanisms are somehow declared and implemented in such means, even if they are not intended to be used during implementation and future operation).
It is important to note that customers know most of these problems, including possible actions by field staff. The IS risks associated with them are covered by very tough organizational and physical security measures: prohibition of bringing various devices and external media into the territory, physical limitation of the use of equipment ports, etc. measures). However, these measures are not able to fully ensure reliable protection of the process control system.
Summarizing the situations and problems described above, the following main points can be noted: regarding the current situation with information security in the process control systems:
- “Everything can be broken” in the process control system without complex attacks on systems, protocols and controllers.
- The initial risks of information security in a technological network are not only not less, but also significantly higher than in a corporate network.
- These risks require their own range of actions and measures, at least taking into account:
- colossal criticality and continuity of business processes;
- the practical impossibility of updates;
- practical inapplicability or inapplicability of traditional IS systems and, in particular, blocking mechanisms.
But no matter how limiting factors, it is still necessary to protect the process control system. In the second part of the article, we will describe how, given these problems, to fully monitor and respond to cyber attacks. Again, with live examples and case studies from customers. Do not miss!
Source: https://habr.com/ru/post/349444/
All Articles