Chrome 68 will mark all HTTP sites as “unsafe”
Google and Mozilla have long agitated for ubiquitous encryption of web traffic and the installation of SSL / TLS certificates. In 2013, at the initiative of Mozilla, the organization Internet Security Research Group was created, which in 2015 launched the Lets's Encrypt service for the automatic issuance of free certificates for TLS encryption. Google is the platinum sponsor of this service.
Today, any site can implement HTTPS without any problems (see "The complete guide to the transition from HTTP to HTTPS" ). Moreover, nowadays, HTTPS is almost mandatory for every website: Chrome and Firefox are already marked as unsafe websites with forms on pages without HTTPS. The absence of HTTPS affects the position in search results and has a serious impact on privacy in general.
')
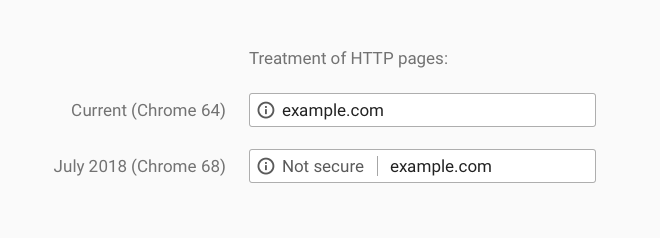
And then HTTP sites will become even more difficult to live. The developers of the Chrome browser announced that from the version of Chrome 68 in July 2018, not only pages with forms, but absolutely all HTTP pages will be marked as unsafe. Users will see the site insecurity message in the address bar next to the site URL (see the screenshot above).
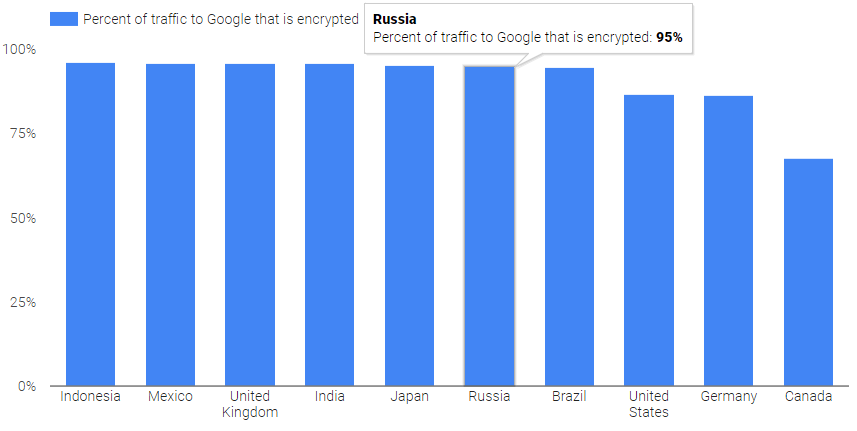
Chrome developers note that over the past year, a very large part of the traffic on the Internet was transferred to HTTPS. Now transmitted in encrypted form:
- Over 68% of Chrome traffic on Android and Windows
- Over 78% of Chrome traffic on Chrome OS and Mac
- 81 of the top 100 Internet sites set HTTPS as default
For example, the jump in popularity of HTTPS last year occurred in Japan. Certificates installed large sites like Rakuten , Cookpad , Ameblo and Yahoo Japan , and the share of HTTPS traffic in Chrome for Windows jumped from 31% to 55%.
In the USA, the share of encrypted traffic increased from 59% to 73% last year.
Google itself has transferred all its services to HTTPS by default .
“The new Chrome interface will help users understand that all HTTP sites are insecure. It contributes to the further movement of the web to use the default secure HTTPS standard, says the official Chromium blog. “Now, installing HTTPS is simpler and cheaper than ever, and it opens up opportunities for improving performance and powerful new features that are too delicate for HTTP.”
Well, Google is true to its word. Back in September 2016, she promised that she would start flagging all HTTP sites as unsafe, and this will happen from July 2018.
The Firefox browser follows the same path. Starting in Firefox 51 (released in January 2017), they are marked as insecure HTTP pages on which to enter passwords. In the address bar for them is an icon with a crossed out lock.

In terms of user perception, this is an important interface change. Studies have shown that users do not perceive the lack of a green icon with a “Protected” lock as a warning. An explicit indication of the danger of the site - right in the address bar - will be a noticeable change.
Thus, in the near future we can expect a massive circulation of sites for TLS certificates. After the appearance of free short-term Let's Encrypt certificates designed only for domain protection (DV), the share of HTTPS sites began to grow rapidly, but so far it is not too large. For example, according to statistics for January 2018, only 405 698 have valid TLS certificates in the Runet of 4,016,205 nodes, 32,395 have valid TLS certificates. The number of valid HTTPS nodes is 458,674. That is, the share of valid HTTPS nodes in Runet is only 11.4%.
But this is still significant progress, because as early as July 2015, the number of valid HTTPS nodes in Runet was a modest 34,305 units, that is, 0.9% of the total. After that, a fairly steady increase in the number of valid certificates began.
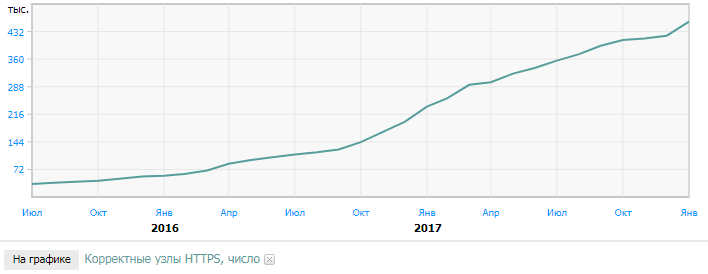
The number of valid HTTPS nodes in RuNet is from July 2015 to January 2018. Source: statdom.ru
Yes, and you need to understand that there are very few “live” web sites on the Runet. There are no statistics here, but Google Analytics codes are found only on 534 thousand web sites, and Yandex.Metrica is on a little over a million. Although it is not recommended to install these tracking trackers, they serve as an indirect indicator of how many approximately active nodes are on the Runet. So among sites with real support, the share of HTTPS can be closer to 40-50%. By the way, this corresponds to Mozilla telemetry data : the share of HTTPS web pages in Firefox browser is now about 49%.
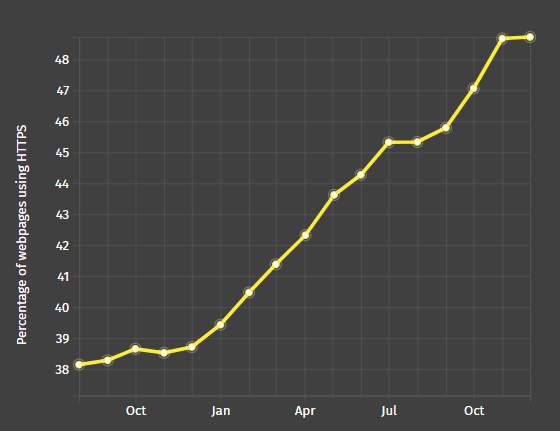
Perhaps the growing popularity of TLS in Russia was also influenced by the tightening of surveillance of citizens on the Internet, including the adoption of the so-called "Spring Law", which requires the preservation of all Internet traffic. True, according to this law, operators and websites are required to provide encryption keys (see the approved procedure for obtaining encryption keys from Internet services ). If the server owner refuses to provide the key needed to decrypt the traffic, a fine of one million rubles can be imposed on it. That is, the special services expect to track and encrypted traffic.
It is not entirely clear how traffic decoding will be implemented in the case of TLS web sites. For example, in Kazakhstan for this site certificates are replaced by a national security certificate issued by the Committee for Communications, Information and Information. Perhaps, something similar will be realized in Russia.
But in the case of using a standard TLS certificate from a trusted Certification Authority , for example GlobalSign, “provide keys” is virtually impossible, because a new session key is generated based on the server certificate, the client's public key, and random numbers generated to encrypt the connection.
Browser developers make it clear that each site needs HTTPS encryption. And there is. Each site has something to lose: this is either information about users, or reputation, or simply protection from introducing third-party banners and crypto miners into pages, for example, from the provider or a WiFi hotspot through which traffic goes . If a user connects to any site via an unprotected HTTP channel, then he actually opens his browser for any third-party code that unauthorized persons will want to run on the computer. And imagine what happens if vulnerabilities like Meltdown and Specter can be exploited through JavaScript?

Source: https://habr.com/ru/post/349428/
All Articles