The Browser Exploitation Framework Project: from XSS to full control

BeEF (short for Browser Exploitation Framework) is a platform for exploiting client-side vulnerabilities, such as XSS (cross-site scripting).
The exploitation of XSS vulnerabilities is often given little attention, because attack vectors are aimed at users of the web application, and not at the web application or web server. BeEF allows you to implement attacking vectors that use a web browser as an entry point. Such attacks can be used in the context of watering hole and spear phishing attacks, as well as in the context of APT .
Principle of operation
After identifying the XSS vulnerability, the attacker injects a generated or generated script on the vulnerable site to control the victim’s browser. If the XSS is stored, and is applicable to all site visitors, it may allow attackers to attack multiple targets simultaneously.
')
A minimum of effort is required from the BeEF administrator; it is enough to simply run beef-xss and open the control panel in the browser.
After executing the hook (js-payload) BeEF, the victim's browser will appear in the “online” tab.

BeEF is cross-platform and can be installed on a Linux, MacOS or Windows system, and is also included with Kali Linux.
To become a victim, it is enough to execute hook.js in your browser. As a result of the script execution, the victim's browser becomes a “bot”, which can be used to send various commands, malicious executable files, intercept keystrokes (keylogging) and so on.
Post operation
The image below shows the interception of keystrokes in the victim's browser. This may allow to intercept the user's password (with the XSS vector, only the session is usually intercepted, not the credentials themselves).

After the javascript code has been executed in the victim's browser, multiple post-exploitation modules are available to the BeEF administrator:

Modules are divided into the following categories:
- collection of information;
- socio-technical vectors;
- network discovery;
- metasploit;
- tunneling;
- XSS-rays (search XSS);
- hold module;
- geo-location
Using these modules, you can explore and analyze network devices using the victim's browser as a springboard for attack.
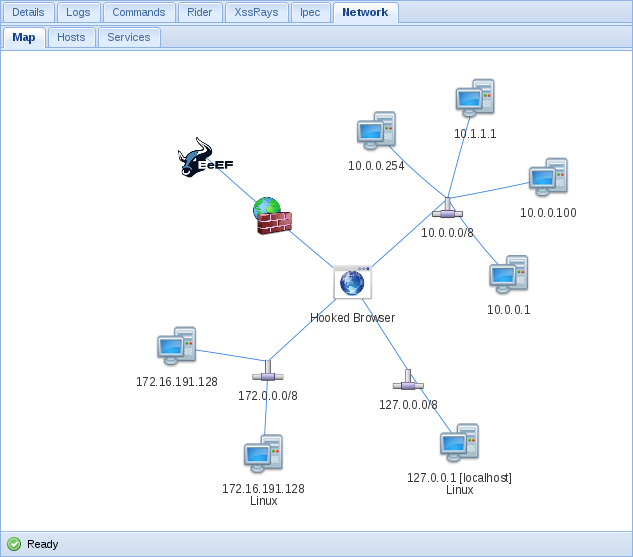
Source: https://habr.com/ru/post/348928/
All Articles