How is the advanced protection against DDoS in Selectel

More than two years have passed since the launch of the Selectel DDoS Protection service. Since then, more than 100 clients of the company have taken advantage of it, more than 200 single IP addresses have been defended, and some clients immediately protect the / 24 subnets. During this time, the system has repelled more than 200 large attacks with a volume of more than 10 Gbit / s each, and the volume of traffic through the cleaning system has grown 5 times. There were also attacks such as TCP SYN of the famous Mirai bot, which crossed the power mark of 70 Gbit / s at 17 million packets per second.
Taking into account the experience gained in protecting against DDoS attacks, additional protection measures were introduced and unique cleaning algorithms were developed, working up to the L7 level of the OSI model , which are based on behavioral traffic analysis, recreating the algorithms of a real user.
')
This article describes the features of the organization of enhanced protection against DDoS in Selectel.
All DDoS attacks, classifying them according to targets, can be divided into the following groups:
- Attacks that aim to overload bandwidth . Examples of attacks of this type are the above-mentioned UDP flood, ICMP flood (also known as ping flood), and other packet distribution practices that have not been requested. The strength of such attacks is measured in gigabits per second. It is constantly increasing and can now be up to 100 gigabits or more per second.
- Attacks at the protocol level . As the name implies, attacks of this type exploit the limitations and vulnerabilities of various network protocols. They "bombard" the server with parasitic packets, and it becomes unable to process requests from legitimate users. As an example, SYN-flood, teardrop and other attacks that disrupt the normal movement of packets within the protocol at different stages.
- Attacks at the application level that disrupt the normal functioning of the system, exploiting the vulnerabilities and weaknesses of applications and operating systems. These attacks are invisible to standard analyzers, as they sometimes make up to 1 Kpps. Standard protection measures cannot detect such a small surge of traffic; therefore, protection always requires constant filtering and the cleaning complex must always know the algorithms of the application itself.
The existing protection system works well with bandwidth overload attacks and is acceptable at the protocol level. Extended protection against DDoS attacks adds another step to the traffic cleaning complex - a special proxy server for protection against attacks at the protocol level and at the application level.
The route of the traffic cleared by the usual protection against DDoS attacks is shown in the diagram:

For enhanced protection against DDoS attacks, it is necessary that the responses to requests from the server also go through the DDoS (traffic cleaning) protection complex:
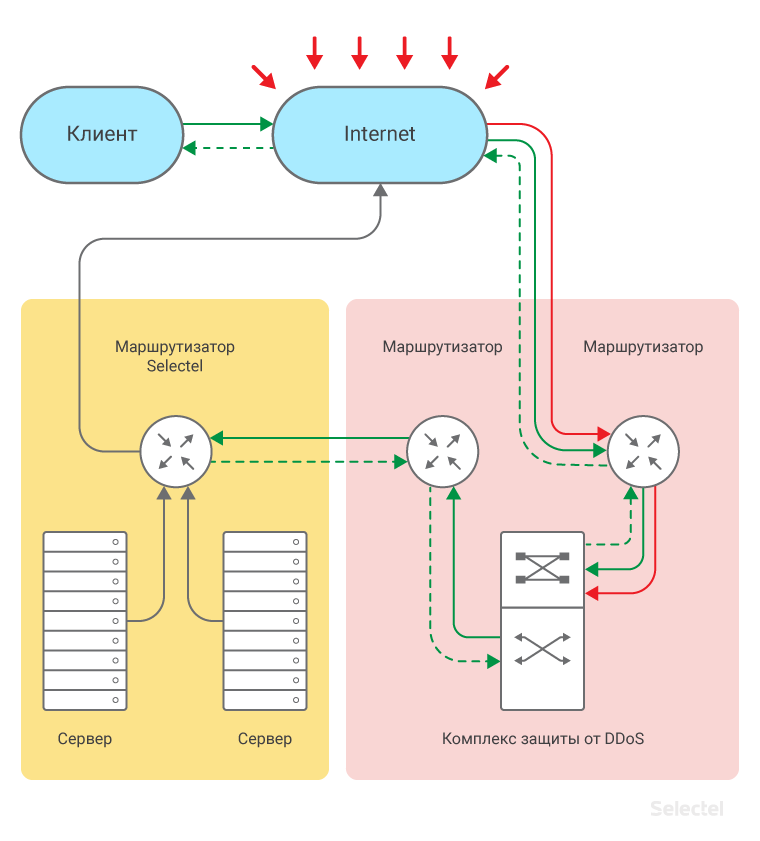
In the simplest case, on the side of the DDoS protection complex, a software and hardware solution based on the proxy server principle is individually configured. This solution passes all data through to the protected resource and back.
If we talk about HTTP, the client's address is added by the proxy server to the HTTP header (for example, X-Forwarded-For or X-Real-IP). But it only works for HTTP-like protocols (HTTP, HTTP / 2, HTTPS, Speedy). For other protocols, both TCP and UDP based, no headers are added.
Scheme of work
Suppose the client IP address is 192.0.2.55.
The real IP address of the protected server is 198.51.100.15.
In order to put the server on advanced protection against DDoS, you need to fill out a special questionnaire, indicating which applications on the server you want to protect against attacks.
How many applications - so many objects to be protected:
- if there are two such applications, we are talking about two protected objects;
- if one - about one;
- if the application works with multiple TCP / UDP ports (for example, if it is SIP-proxy, then the application works with both TCP and UDP traffic) - this is one application;
- if we add a web server, we get another protected object. For example, we protect SIP-proxy, which should be available from the Internet as sip.example.com.
Based on the questionnaire Selectel allocates a pair of IP addresses:
- 203.0.113.34 - for installation on a protected server;
- 95.213.255.45 - for a proxy service on the side of the DDoS protection complex.
- In DNS records, the A record value for sip.example.com is set to 95.213.255.45.
- The client 192.0.2.55 contacts the service by the DNS name, the service by IP address 95.213.255.45.
This address is accessible by routing through the partner's network and thus all incoming traffic from clients to the server goes to the cleaning complex:

The proxy service processes the traffic as follows:
There was: (src-ip 192.0.2.55, dst-ip 95.213.255.45).
Steel: (src-ip 192.168.0.45, dst-ip 203.0.113.34) - 192.168.0.45 - the address that the DDoS protection partner uses for NAT pools.

The secure IP address of the server 203.0.113.34 is known only to the server administrator, Selectel and the DDoS protection partner. The real server address 198.51.100.15 is known only to the server administrator and Selectel.
This server address 95.213.254.15 is used to make connections from the server side, for example, for apt-get update and for server administration and monitoring, say, via ssh.
Protected (203.0.113.34 in the example) and real (198.51.100.15 in the example) addresses must be kept secret, and their declassification may lead to a DDoS attack past the cleaning complex.
The address 203.0.113.34 is used to connect the server with the traffic clearing complex and is unavailable from the Internet. To match the server’s connection address with the traffic clearing complex of the current address of the protected address, Selectel uses static routing of the form:
route 203.0.113.34/32 via 198.51.100.15/
The reverse traffic from the server to the Internet to the client is as follows:
- The server sends IP packets (src-ip 203.0.113.34, dst-ip 192.168.0.45).
- The Selectel router isolates traffic from the incoming server to the following addresses: 192.168.0.45 (addresses of the NAT pools of the traffic clearing complex) and sends traffic back to the traffic clearing complex:

The packet passes through the reverse cleaning complex, where the SRC-IP and DST-IP addresses are replaced in the IP packet. The client eventually leaves the IP packet (src-ip 95.213.255.45, dst-ip 192.0.2.55):

Address conversion is transparent for both the client and the server. If device addresses are transmitted within packets (in particular, SIP packets contain within the addresses of the parties), then these packets change inside due to ALG processing inside the DDoS protection complex. Today the complex supports ALG profiles for FTP, TFTP, SIP, RTSP, PPTP, IPSec.
Supported Applications
For advanced protection against DDoS requires fine-tuning of the cleaning complex. Today we at Selectel can offer extended protection for the following applications:
- Web server (HTTP)
- Encrypted web server (https).
- Teamspeak
- Counter strike
- Minecraft
- Microsoft RDP
- DNS
For applications that process secure traffic (HTTPS, other protocols with TLS support), it is necessary to transfer the private key to the DDoS protection complex in order to organize proper proxying. Without key transfer, application-level protection becomes impossible, and the possibilities are limited by the protocol level.
Extended protection against DDoS attacks is designed for both HTTP resources and others: TeamSpeak, CounterStrike, DNS. Over HTTP traffic - the complex is focused on full L7 analysis of passing packets and copes well with various HTTP attacks: XSS, SQL-injection and so on.
Source: https://habr.com/ru/post/348454/
All Articles