Why most people do not use two-factor authentication?
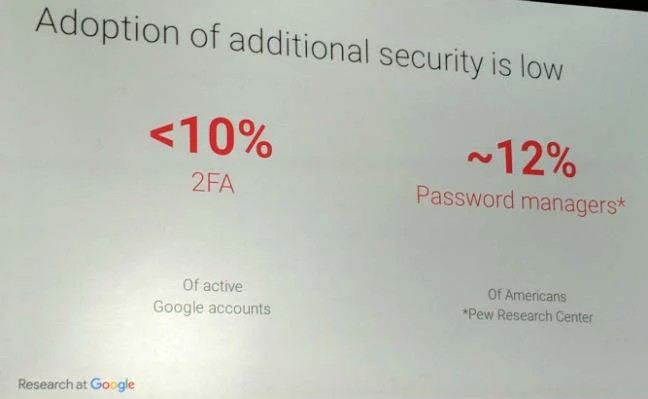
Less than 10% of accounts use two-factor authentication, about 12% use password managers.
It has been almost seven years since Google introduced two-factor authentication (2FA), but so far almost no one uses it.
At the Usenix's Enigma 2018 Information Security Conference in January, Google Software Engineer Grzegorz Milka made a presentation. He published sad statistics on how ordinary users relate to their security: less than 10% of active Google accounts use 2FA and only about 12% of Americans use password managers (Pew Research Center statistics). Recently this subject was discussed on Geektimes.
')
Leaving aside the fact that Google, when activated, requires 2FA to indicate the phone number - this does not suit those who are not ready to share personal data with the corporation. Quite a reasonable position. But most users prefer to ignore 2FA for other reasons. Why?
Google is one of the pioneers in the implementation of 2FA among major Internet services. In addition, the company actively promotes this method and distributes the Google Authentificator App to link your account to a specific device. Two-factor authentication works and simply by SMS.
Insecurity 2FA by SMS
It should be noted that 2FA via SMS has already been officially recognized as an insecure method of authentication due to unrecoverable vulnerabilities in the Signaling System 7 (SS7) signaling system, which is used by cellular networks to interact with each other.
Experts of the company Positive Technologies a few years ago showed how the interception of SMS. In short, the attack is a procedure for registering a subscriber in the range of a “fake” MSC / VLR. The source data is the subscriber's IMSI and the address of the current MSC / VLR, which can be obtained using the corresponding request on the SS7 network. After the subscriber is registered in the “fake” MSC / VLR zone, he will stop receiving incoming calls and SMS, and all his SMS messages will be sent to the attacker's node.
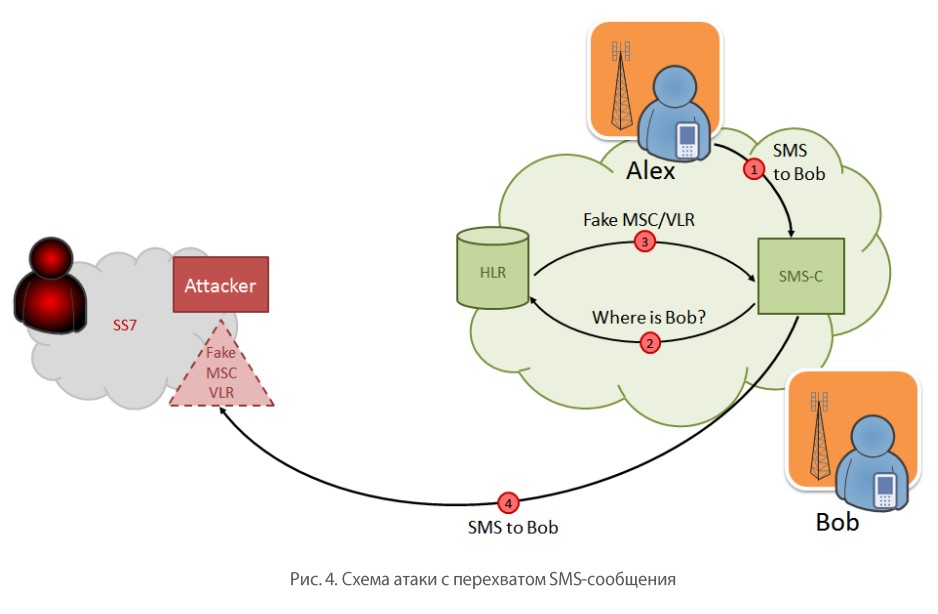
The specific case of the attack with all the necessary commands and screenshots published in the corporate blog Positive Technologies on Habré.
Interception of someone else's SMS is not at all theoretical delights; such attacks have already been carried out repeatedly by hackers and special services of different countries (see the article “The intelligence services began to intercept SMS telegram authorization codes ”). Although in the Russian case it could not be the security services at all, after all, the attack through SS7 is available to anyone who wanted to: anyone could intercept these SMS, it was not necessarily the security services.
Anyway, 2FA via SMS is no longer a safe two-factor authentication method. This was officially recognized by NIST (National Institute of Standards and Technology), which in 2016 published a new version of the Digital Authentication Guide . It says that SMS authentication is no longer supported and will not be included as the recommended authentication method in future versions of the Guide.
In other words, in some cases, two-factor authentication is not secure, but rather gives users a sense of false security . They think that their account cannot be compromised without a mobile phone - and therefore, for example, set a weaker password for the account. That is, in this case, 2FA even worsens the user 's security.
Google did not implement other methods of 2FA, for example, sending a code to another email address - perhaps it was also considered that they were not too secure, like 2FA via SMS. But whatever method 2FA we use - in any case, this is an additional gesture for the user. That is, people trite uncomfortable. It seems that many are willing to sacrifice security for convenience.
Uncomfortable?
Actually, the assumption of inconvenience was confirmed by Grzegorz Milka, the same speaker from Google. The Register journalists asked him why Google won't turn on two-factor authentication by default for all accounts? The answer was: usability. “It's about how many users will leave if we force them to use additional security.”
Google how can trying to simplify the process. For example, in July 2017, the company launched a quick login using notifications on the phone (Google Prompt). Here verification codes are not used, but instead simply click on the notification from Google on your phone and confirm the entry.
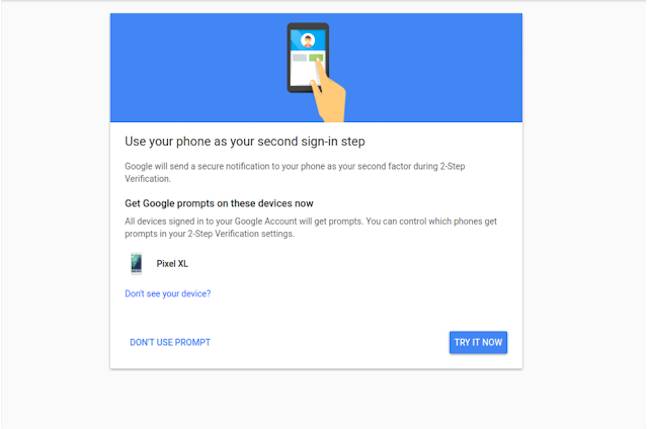
But judging by the statistics, even this 2FA method seems unnecessarily complicated to users. Any extra keystroke, any additional screen - this is a difficulty, a deterioration in usability. Even the simplest action on the Internet can cause difficulties for a part of the audience. Google says that when trying to install this defense mechanism, more than 10% of users could not enter code sent by SMS into the window.
It turns out that most users are simply not willing to sacrifice convenience for the sake of security. Someone believes that he "has nothing to hide." Or that his account is of no value to intruders, and therefore he will never become a victim of hacking. In order to protect such people, Google is trying to improve heuristics and detect hacking facts by user actions. The problem is that you need to react in such cases very quickly: within a few minutes, until the attacker carried out all his plans.

Anatomy of a typical hack. From the presentation of Google. As you can see, the attacker manages to carry out all actions in 15 minutes
Google says that activity in hacked accounts has a number of similar signs. Once logged in, the attacker disables notifications, searches for valuable assets in the archive of letters (Bitcoin wallets, intimate photos, files with passwords, etc.), copies the contact list and sets a filter to hide their actions from the owner.
Google tries to struggle with such activity as it can, notifying the account holder in various ways and pushing him to activate 2FA. But as Masha Sedova, co-founder of Elevate Security, said, the trivial methods do not work because of the general lack of interest in user security .
Source: https://habr.com/ru/post/348124/
All Articles