Attention, update Firefox to version 58.0.1 to close the critical vulnerability

Mozilla has released an important update to the Firefox web browser to fix a critical vulnerability that allows attackers to remotely execute malicious code on computers that have an vulnerable version of the browser installed.
A critical vulnerability (CVE-2018-5124) can lead to code execution in the system when opening in a certain way prepared HTML fragments, which use additional interface control attributes. The essence of the vulnerability is in the possibility of inline-substitution of JavaScript-code through these elements, which will be performed at a privileged level, responsible for the formation of the browser interface (chrome-privileged).
“Successful exploitation of the vulnerability could allow an attacker to execute arbitrary code with the privileges of the user. If a user has elevated privileges, an attacker could completely compromise the system, ”says a security advisory from Cisco .An attacker may be able to install programs, create new accounts with full user rights, view, change or delete data.
')
However, if the browser is configured with fewer user rights on the system, exploiting this vulnerability may have a less negative effect on the user's security.
The most vulnerable versions of the browser include Firefox 56 (.0, .0.1, .0.2), 57 (.0, .0.1, .0.2, .0.3, .0.4) and 58 (.0). The vulnerability has been fixed in Firefox 58.0.1, and it can be downloaded from the company's official website .
CVE-2018-5124, discovered by the developer Mozilla Johann Hofmann, does not affect the Firefox browser versions for Android and Firefox 52 ESR.
Users are advised to apply a software update before hackers start using this feature, and not to open links, in emails or messages, if they come from suspicious sources.
System administrators are also advised to use an unprivileged account when browsing the Internet.
Firefox quantum
The update was prepared a week after the company released its new browser, Firefox Quantum (Firefox 58). Firefox 58.0 has been developed over the past two months. During this time, Mozilla engineers added a streaming compilation and a new two-tier compiler designed to improve WebAssembly performance. In addition, Firefox has now learned how to automatically fill out bank card details, and for MacOS users added support for WebVR.
Among other improvements are optimization of page loading speed due to the implementation of the caching technique for internal representation of JavaScript and acceleration of web page rendering in Windows due to the integration of Off-Main-Thread Painting technology.
Firefox 58 was the first browser release that comes with security fixes by default to reduce the risk of Meltdown and Specter attacks. However, problems with older processors may occur.
PS
Since we are talking about the vulnerabilities of processors, it is worth noting that researchers from the company AV-TEST today found at least 139 samples of malicious programs that are associated with attempts to operate Meltdown and Specter. The increase in the number of detected viruses is shown below in the graph and indicates that the attackers are actively working in this direction.
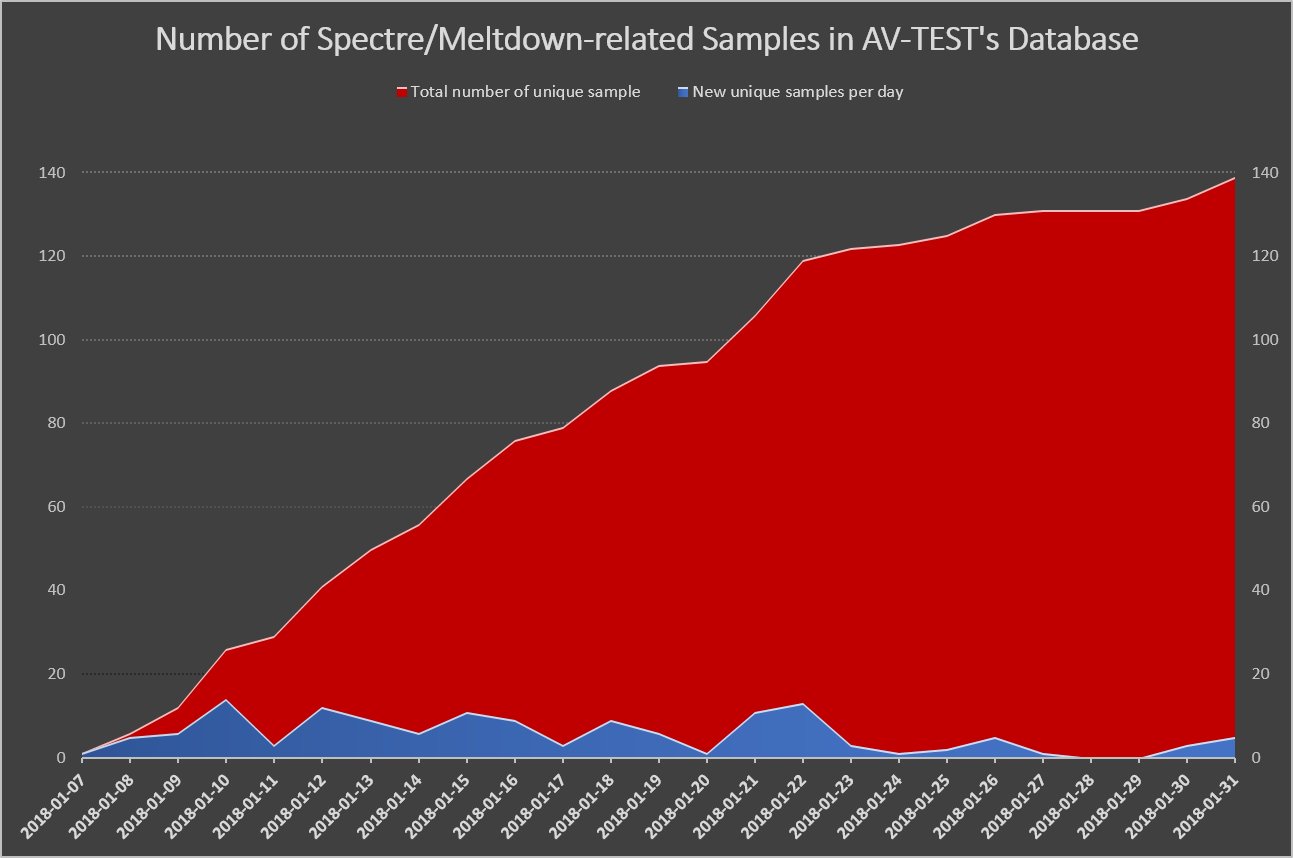
Under the link you can find SHA256 hashes for all malware samples.
Source: https://habr.com/ru/post/348080/
All Articles