Blockchain: Networking, Signature Verification and Student Assignment, Part 2
Foreword
In the first part, it was told about the blockchain capabilities, structure and EDS, in this part it will be told about: signature verification, mining and approximate networking. I note that I am not a specialist in distributed systems (network organization may be incorrect).
Peer-to-Peer Network (P2P)
A peer-to-peer (peer-to-peer) network is a network based on the equality of participants. Often there are no dedicated servers in such a network, and each node (peer) is both a client and acts as a server. Unlike the client-server architecture, such an organization allows the network to be maintained at any number and any combination of available nodes. Network members are called peers.
Networking
First you need to answer the questions:
- How do customers know that there are other customers?
- How to guarantee optimal interaction between customers, if they can be separated from each other by the continents?
Each client participating in the P2P network application must be able to perform the following operations to overcome these problems:
- detect other customers;
- connect to other customers;
- interact with other customers.
When connecting, a new client contacts the tracker, which contains lists of connected nodes. There can be a lot of such trackers, they are needed for optimal communication between clients, by optimality is meant that downloading a block chain is better from a site that is geographically located nearby than the one that is next. That is, the linking center (tracker) allows you to find out to a new client who is already on the network and provides a list of the most “suitable" nodes. An example of a network is shown in Figure 1.
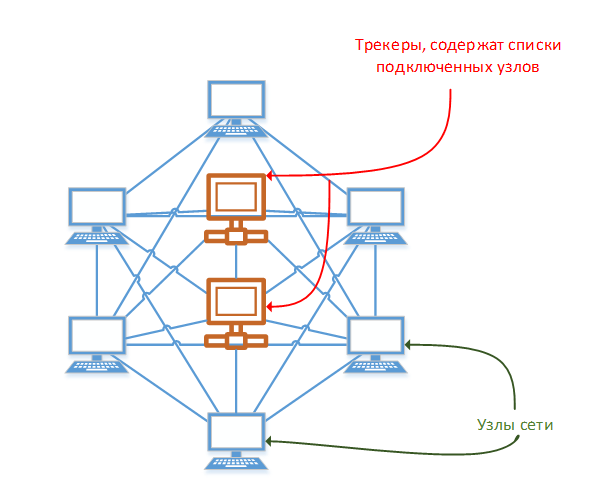
Figure 1 - a decentralized network with trackers containing lists of connected nodes
Mining
Depending on the type of blockchain (decentralized version using proof of operation or centralized with a trusted center), transaction blocks (empty) can be created by miners or the main node (center). Miners are nodes that compute a new block (meaning a transaction block). What does it mean to calculate a new block and why should it be calculated? The thing is that in some types of blockchains it’s not so easy to create a block, you need to solve a difficult task by iterating over numbers (to be exact, to get a hash with 10 zeros at the beginning ~ 0000000000HD83HA653JA ... 83JS) could not quickly replace the block chain, because the calculation of such a hash can take hours, days, weeks (replacing one, you have to recalculate the other blocks). In other types of blockchain, these hashes can already be calculated in advance and, accordingly, there is no need for miners as block getters, here the miner's goal is not to extract the block, but to provide its hard disk for chain storage.
')
Check blockchain data
After adding a new block or inserting a new data into the list of transactions of an already created block, it is necessary that other members of the network check this information.
Transaction Verification Algorithm
The transaction verification algorithm is shown in Figure 2. Transaction verification by other network participants can be divided into steps:
- Data acquisition and signatures from a new transaction;
- Get the SHA512 hash from the data;
- The signature and public key taken from the address of the same block are decrypted using RSADecode (signature, public key);
- Compare the hash obtained in step 2 with the hash obtained from the decoded signature in step 3. If they match, then the data is correct and signed by the owner key, the transaction is added to itself in the block. If they do not match, the data is false and the transaction is rejected and is not added to the block.
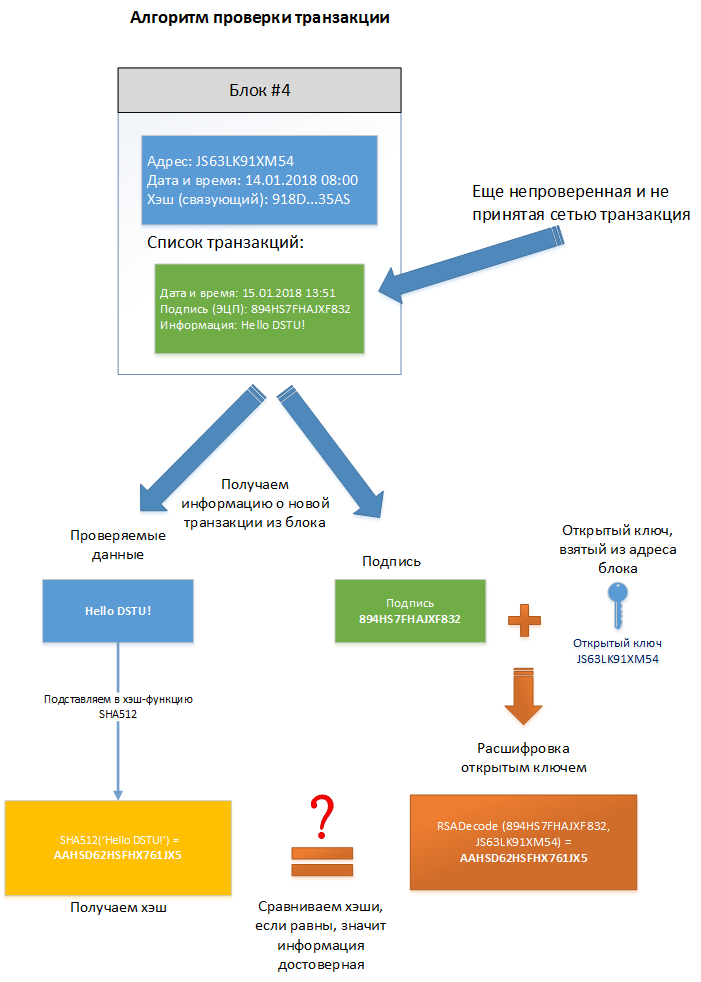
Figure 2 - Transaction Verification Algorithm
Block check algorithm
Checking a new block is divided into stages:
- The address of the last received block is taken (the current block has not yet been received and is not the last) and the list of transactions of the current block. Then the hash is calculated:
= SHA512(block_prev_adress_hash + transaction_hash1 + transaction_hash2 + … + transaction_hashN) - The resulting hash is compared with the hash (binder) of the still not accepted block. If they match, then the block is correct and is added to itself in the chain. Otherwise, the data is incorrect and the block is not accepted.
An example of verifying signatures in C #
Pass to the method obtained from the transaction: data, signature and block address (public key).
private static bool VerifyMessage(string originalData, string signedDataBase64, string publicKey) { // bool verified; // RSA RSACryptoServiceProvider rsa = new RSACryptoServiceProvider(2048); // , ( ) // rsa.FromXmlString(publicKey); // byte[] originalByteData = Encoding.UTF8.GetBytes(originalData); // string Base64 byte[] signedData = Convert.FromBase64String(signedDataBase64); // originalByteDate SHA512, signedData // verified verified = rsa.VerifyData(originalByteData, CryptoConfig.MapNameToOID("SHA512"), signedData); return verified; } The task
It is necessary to expand the PS from the first part by implementing a decentralized network with trackers. Client nodes must be able to communicate with each other (transmit / receive / verify information). Nodes trackers - update / give a list of nodes.
Functions of the tracker node:
- Registration (adding to the list) of the client when connecting to the tracker;
- Return the list of connected nodes.
Client features:
- Connection to the tracker node and network nodes from the list received from the tracker;
- When connecting to network nodes, synchronize the transaction history by accepting it from another participant (if it has a newer or longer chain) with a subsequent check;
- When adding a new block or transaction, announce (transfer) this block to the other participants;
- Getting a new block or transaction from other participants;
- When you receive a new block or transaction from other participants, you need to check them and decide whether to insert into your chain or reject.
Sources
Source: https://habr.com/ru/post/348020/
All Articles