Blockchain: features, structure, EDS and task for a student, part 1
Foreword
I work as an assistant in an institution of higher education (as a hobby), I decided to write several laboratory for students in the discipline "distributed systems". The first part will be told about the blockchain's capabilities, structure and EDS, and the second part about: signature verification, mining and approximate networking. I note that I am not a specialist in distributed systems (network organization may be incorrect).
Structure and capabilities
Blockchain is one of the types of distributed data storage, uses 3 previously known technologies: peer-to-peer networks, encryption and databases. The database is a chain of blocks that is encrypted in a special way and stored on all nodes of the network in the same form (replication is an exact copy). The whole secret lies in the connections between the blocks due to cryptography, as a result it is almost impossible to fake information in the blocks.
Blockchain allows you to securely distribute and / or process data between multiple individuals through an untrusted network. Data can be anything, but the most interesting version of the data is the ability to transfer information, which requires a third trusted party. Examples of such information are money (require the participation of a bank), rights to property (require the participation of a notary), a loan agreement, etc. In essence, the blockchain eliminates the need for the participation of a third trustee.
The most interesting projects where the blockchain is used:
- Monegraph allows authors to secure the rights to their work and establish rules (and payments) for the use of their work;
- La Zooz is a decentralized Uber. Offer your car, find a carrier without payment to Uber;
- Augur is an online bookmaker. Place bets and get a win;
- Storj.io is a P2P data store. Hand over your unused disk space or find the cheapest online storage;
- Muse is a distributed, open and transparent database specifically for the music industry;
- Ripple allows low-cost cross-border payments to banks;
- Golem is a global open source decentralized supercomputer that anyone can access to perform distributed computing (from image processing to conducting research and launching websites). Using Golem, users can buy or sell computing power among themselves;
- Many other cryptocurrencies characterized by high anonymity of work, low cost of transfers, smart contracts, etc.
')
Database
In its simplest form, a database (DB) is a chain of blocks that can be represented as a JSON file.
Block structure
Each block consists of an address, a date and time of creation, a hash, and a list of transactions. As in Figure 1.
- Address - a public key generated by an asymmetric encryption algorithm (for example, RSA), based on a private key invented by a user;
- Date and time - the moment when the block was created (the transaction also has the date and time of creation);
- Hash (binding) - calculated using SHA512 from the address of the previous block and the sum of the hashes of all transactions of the current block, why the binding? Because when calculating it, the address of the previous block is required;
- Information - message, amount of money (cryptocurrency), documents, history of diseases, program code (smart contracts), etc.
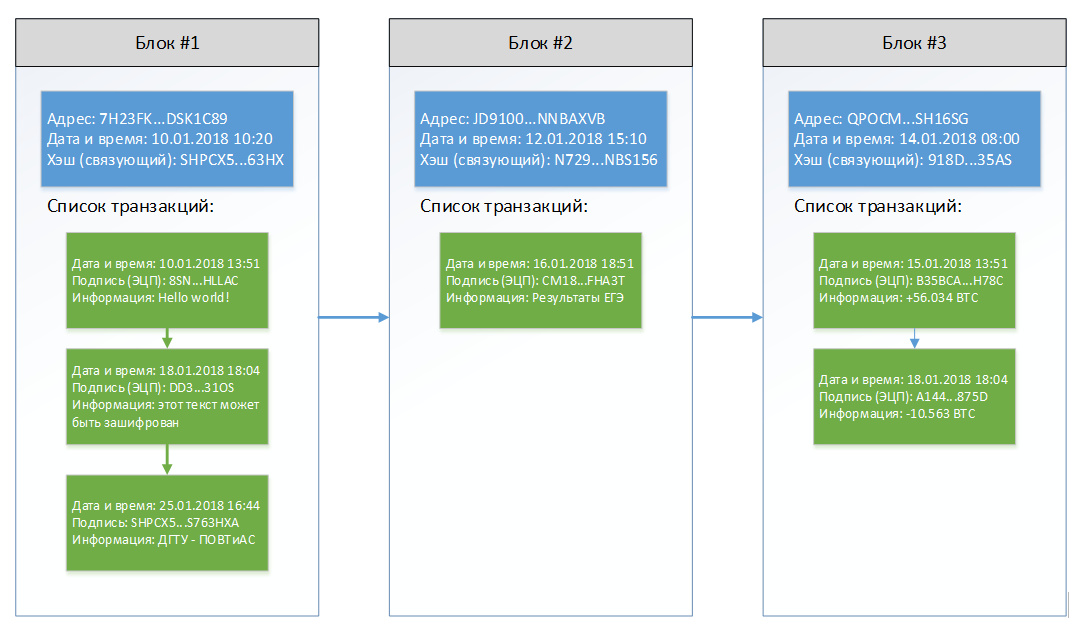
Figure 1 - blockchain of 3 blocks
For a simple understanding of what a block is, it is enough to present it as a chest with a lock, when you want to put something there, then you need to unlock the lock with a key, this key is created by you when you create the block and is called the private key.
Electronic digital signature
To prevent information inside transactions from being forged, every transaction inside a block is signed with an electronic digital signature (EDS).
A digital signature is a sequence of bytes formed by converting the signed information using a cryptographic algorithm and intended to verify the authorship of an electronic document.
The digital signature is based on the use of asymmetric encryption and hash functions.
Briefly about encryption methods:
- symmetric encryption uses the same key for both encryption and decryption;
- Asymmetric encryption uses two different keys: one for encryption (also called open), the other for decryption (called closed).
In asymmetric encryption algorithms, encryption is performed using the public key, and decryption is performed using the private one.
But in asymmetric digital signature schemes, signing is performed using the private key, and verification of the signature is done using the public key, that is, encrypted with the closed one, and verified with the public key (“verify” this is not “decrypt”, do not confuse).
RSA can be one of such algorithms. The choice of asymmetric encryption is justified by the fact that other members of the network must make sure that it was the block owner who made the changes and signed the block with his signature (the check is described in the second part ).
Private and public keys
The private (private) key is generated by the user, used to sign transactions. It is kept secret, the one who owns the private key has access to the blockchain cell, which can be represented by a wallet, a container with some data (for example, personal correspondence, important documents, etc.).
A public (public) key must be generated on the basis of a private key, that is, there is a mathematical connection between them (the public key is not invented from the head). It can be published, moreover, it is used in the blockchain as a block address, as well as an authentication of the signature of information in other blocks, by third-party network participants. Knowledge of the public key makes it impossible to determine the private key.
Algorithm for signing information (document)
To create a signature you will need:
- Asymmetric encryption algorithm (for example, RSA);
- Hash function (for example, SHA512);
- Information that we are going to sign.
Since asymmetric algorithms are rather slow compared to symmetric ones, the volume of signed data plays a big role, and if it is large, it usually takes a hash from the signed data, and not the data itself. A hash is obtained using hash functions, for example, SHA512, which accepts certain information as input and returns a hash of a certain length. Hash function as a meat grinder, you can scroll through the meat and get the stuffing, but you will not get the meat back from the stuffing. Thus, the EDS is placed not on the document itself, but on its hash. Hash functions are not part of the EDS algorithm, so any reliable hash function can be used in the scheme.
Stages:
- Using RSA, we generate a pair of public and private keys;
- Subscribed data is substituted into the SHA512 function and we get a hash;
- The resulting hash and private key are substituted into the RSA asymmetric encryption function, that is, RSAEncode (information hash, private key), we will get a line - EDS at the output.
The data signature algorithm is shown in Figure 2.
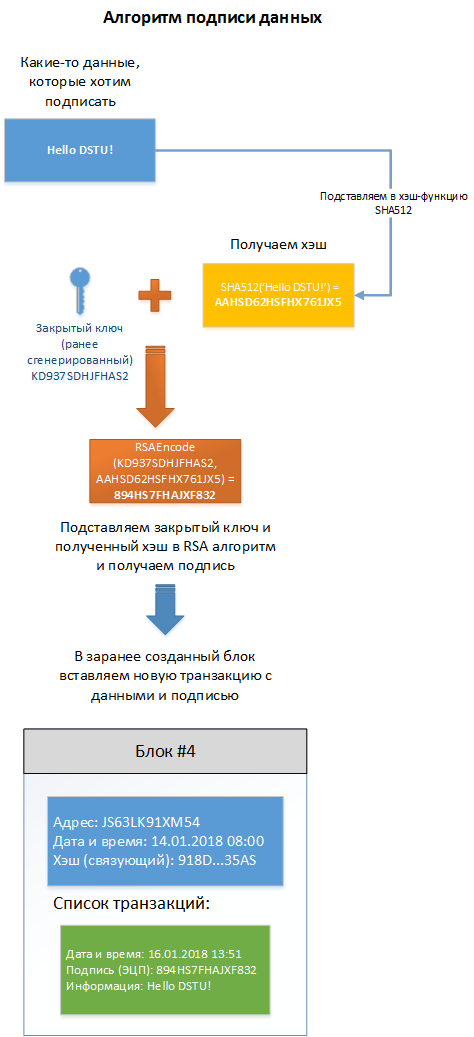
Figure 2 - Data Signing Algorithm
Binder hash block
The binding hash is recalculated every time a new transaction is added. It is considered by summing up all the transaction hashes of the current block and the address of the previous block:
() = SHA512(block_prev_adress_hash + transaction_hash1 + transaction_hash2 + … + transaction_hashN) For example, from Figure 1 it can be seen that the hash of the 3rd block was calculated as the address of the second block and two hashes of two internal transactions:
3 = SHA512(JD9100...NNBAXVB + B35BCA...H78C + A144...875D) It is the binding hash that unites the blocks into a single chain and, most importantly, protects the blockchain from forgery by intruders. Suppose if someone wants to “throw out” or insert his block in the middle of the chain, then the blocks following it will not pass the test, because their hash was based on the address they want to replace or remove. How network members check or monitor the integrity of the network will be discussed in the next section .
Signature example in C #
To generate a key pair, you can use various libraries, for example, the C # language has a built-in package for working with encryption algorithms and digital signature.
// 1024 RSACryptoServiceProvider rsa = new RSACryptoServiceProvider(1024); // , XML string privateKey = rsa.ToXmlString(true); // , XML string publicKey = rsa.ToXmlString(false); The received private key should be stored in a separate file, the public key is the address of the block, so it should not be stored.
Thus, for each user login is the address of the block (public key), and the password is the private key, knowing these two keys you can access the blockchain cell located under this address and dispose of the information in it.
Signing arbitrary data with the RSA encryption algorithm, transferring the data and the private key, we get the signature:
private static string SignData(string data, string privateKey) { // RSA RSACryptoServiceProvider rsa = new RSACryptoServiceProvider(1024); // , ( ) rsa.FromXmlString(privateKey); // byte[] byteData = Encoding.UTF8.GetBytes(data); // SHA512 ( , , ) byte[] signedByteData = rsa.SignData(byteData, CryptoConfig.MapNameToOID("SHA512")); // Base64 string signedData = Convert.ToBase64String(signedByteData); // return signedData; } The task
It is necessary to implement the PS storing the block chain in a separate file in JSON format, each time a new block or transaction is added, the file must be updated.
Client features:
- Registration of a new user (one block = 1 user) - that is, create a new block, return the private key to the user, and use the public key as the block address;
- Authorization - access to the blockchain cell, login is the address of the block, password is the private key;
- After passing authorization - insert a transaction with arbitrary information into the block (not into any, but into the one to which you have access);
- View a list of blocks and transactions in a clear form.
The structure of the block and transactions should correspond to the description in the methodical manual. It is also necessary to store the user's private keys in a separate file (in this blockchain, each user has his own private key, we need this functionality to check the functionality of the program).
Continued - signature verification, mining and approximate networking
Sources
Source: https://habr.com/ru/post/348014/
All Articles