How does blocking access to pages that distribute prohibited content (now the RKN also checks the search engines)
Before proceeding to the description of the system that is responsible for access filtering by telecom operators, we note that now Roskomnadzor will also control the work of search engines.
At the beginning of the year, an order of control and a list of measures to comply with the requirements of search engine operators to stop issuing information about Internet resources, access to which is restricted in the Russian Federation, was approved.
')
The relevant order of Roskomnadzor dated November 7, 2017 No. 229 is registered with the Ministry of Justice of Russia.
The order was adopted as part of the implementation of the provisions of Article 15.8 of the Federal Law No. 149- dated July 27, 2006 “On Information, Information Technologies and Information Protection”, which defines responsibilities for owners of VPN services, “anonymizers” and search engine operators to restrict access to information , the dissemination of which is prohibited in Russia.
Control measures are held at the location of the control body without interacting with search engine operators.

The information system is understood as the FGIS information resources of information and telecommunication networks, access to which is restricted.
According to the results of the event, an act is drawn up, which indicates, in particular, information about the software used to establish these facts, as well as information confirming that the specific page (s) of the site at the time of control was in the information system for more than a day.
The act is sent to the operator of search engines through the information system. In case of disagreement with the act, the operator has the right to submit his objections to the Roskomnadzor within three working days, which considers the objections also within three working days. Based on the results of consideration of the objections of the operator, the head of the control body or his deputy decides to initiate an administrative offense case.
How the access filtering system is designed for telecom operators
In Russia, there are a number of laws that require telecom operators to filter access to pages that distribute prohibited content:
- FZ 126 “On Communications”, amendment to art. 46 - about the duty of the operator to limit access to information (FESEM).
- “Unified Register” - Resolution of the Government of the Russian Federation of October 26, 2012 N 1101 “On the Unified Automated Information System“ The Unified Register of Domain Names, Website Indexes in the Information and Telecommunication Network “Internet” and Network Addresses, which allow to identify sites in Information and Telecommunications the Internet, containing information whose distribution in the Russian Federation is prohibited »»
- FZ 436 “On the protection of children ...”, categorization of available information.
- Federal Law No. 3 “On Police”, Article 13, Section 12 - on the elimination of the causes and conditions conducive to the realization of threats to the safety of citizens and public safety.
- Federal Law No. 187 “On Amendments to Certain Legislative Acts of the Russian Federation on the Protection of Intellectual Rights in Information and Telecommunication Networks” (“anti-piracy law”).
- Fulfillment of decisions of the courts and instructions of the prosecution authorities.
- Federal Law of 28.07.2012 N 139- “On Amendments to the Federal Law“ On the Protection of Children from Information Harmful to their Health and Development ”and certain legislative acts of the Russian Federation”.
- Federal Law of July 27, 2006 No. 149- “On Information, Information Technologies and Protection of Information”.
Requests from Roskomnadzor for blocking carry an updated list of requirements for the provider, each entry from such a request contains:
- type of registry, according to which the restriction is made;
- the point in time from which the need to restrict access arises;
- type of emergency response (normal urgency - during the day, high urgency - immediate response);
- type of registry entry lock (by URL or domain name);
- registry hash code (changes with any change in the contents of the record);
- details of the decision on the need to restrict access;
- one or more site page indexes, access to which should be restricted (optional);
- one or more domain names (optional);
- one or more network addresses (optional);
- one or more ip-subnets (optional).
To effectively communicate information to the operators, an Information System for Roskomnadzor and Telecom Operators was created. It is located along with regulations, instructions and instructions for operators on a specialized portal:
vigruzki.rkn.gov.ru
For its part, Roskomnadzor began issuing a client of the Auditor “Auditor” to check the operators. Below is a little about the functionality of the agent.
Algorithm for testing the availability of each URL by the Agent. When checking the Agent must:
- determine the IP addresses to which the network name of the checked site (domain) is converted or use the IP addresses provided in the upload ;
- for each IP address received from DNS servers, make an HTTP request for the URL being checked. In the case of receiving a redirect from the checked site HTTP, the Agent must check the URL to which the redirection is performed. At least 5 consecutive HTTP redirects are supported;
- if it is impossible to make an HTTP request (no TCP connection is established), the Agent must conclude that there is a blocking of the IP address entirely;
- in case of a successful HTTP request, the Agent must check the received response of the checked site using the HTTP response code, HTTP header, HTTP content (first received data up to 10 kb in size). If the response received coincides with the stub page templates created in the control center, a conclusion must be made that the URL being checked is blocked ;
- during the verification of the URL, the Agent must verify the installation of the encrypted connection and mark the resource;
- in case there is no coincidence of the data received by the Agent with the templates of the blank pages or trusted pages of the redirect informing about the resource lock, the Agent must conclude that the URL is not blocked on the carrier SPD. In this case, information about the data (HTTP response) received by the Agent is recorded in the report (file of the check log). The system administrator has the ability to form a new page stub template from this entry to prevent subsequent false conclusions about the absence of a lock.
A list of what the Agent must provide
- communication with the control center for a complete list of URLs and blocking modes that need to be tested;
- communication with the control center to obtain data on verification modes. Supported modes: full one-time check, full periodic with a given interval, selective one-time with a user-defined list of URLs, periodic with a specified interval check of a list of URLs (of a certain type of EP records);
- continuation of the implementation of specified verification procedures on the existing URL list, in case it is impossible to obtain a list of URLs from the control center, and storing the obtained results of the checks with subsequent transfer to the control center;
- full implementation of specified verification procedures on the existing URL lists, in case of impossibility to obtain information on verification modes from the control center, and storing the obtained test results with the subsequent transfer to the control center;
- checking the results of blocking in accordance with the established mode;
- Sending an audit report to the control center (verification log file);
- the ability to test the performance of the SPD operator, i.e. check the availability of a list of known sites;
- the ability to verify the results of blocking using a proxy server;
- the possibility of remote software updates;
- the ability to conduct diagnostic procedures on the PDS (response time, packet flow path, file download speed from an external resource, determination of IP addresses for domain names, value of the speed of receiving information in the reverse communication channel in wired access networks, packet loss rate, average transmission delay time packages);
- scanning performance of at least 10 URLs per second, provided that the communication channel band is sufficient;
- the ability of the agent to repeatedly access the resource (up to 20 times), with a variable frequency from 1 time per second to 1 time per minute;
- the ability to create a random order of list entries transmitted for testing and setting the priority for a specific page of the site on the Internet.
In general, the structure looks like this:
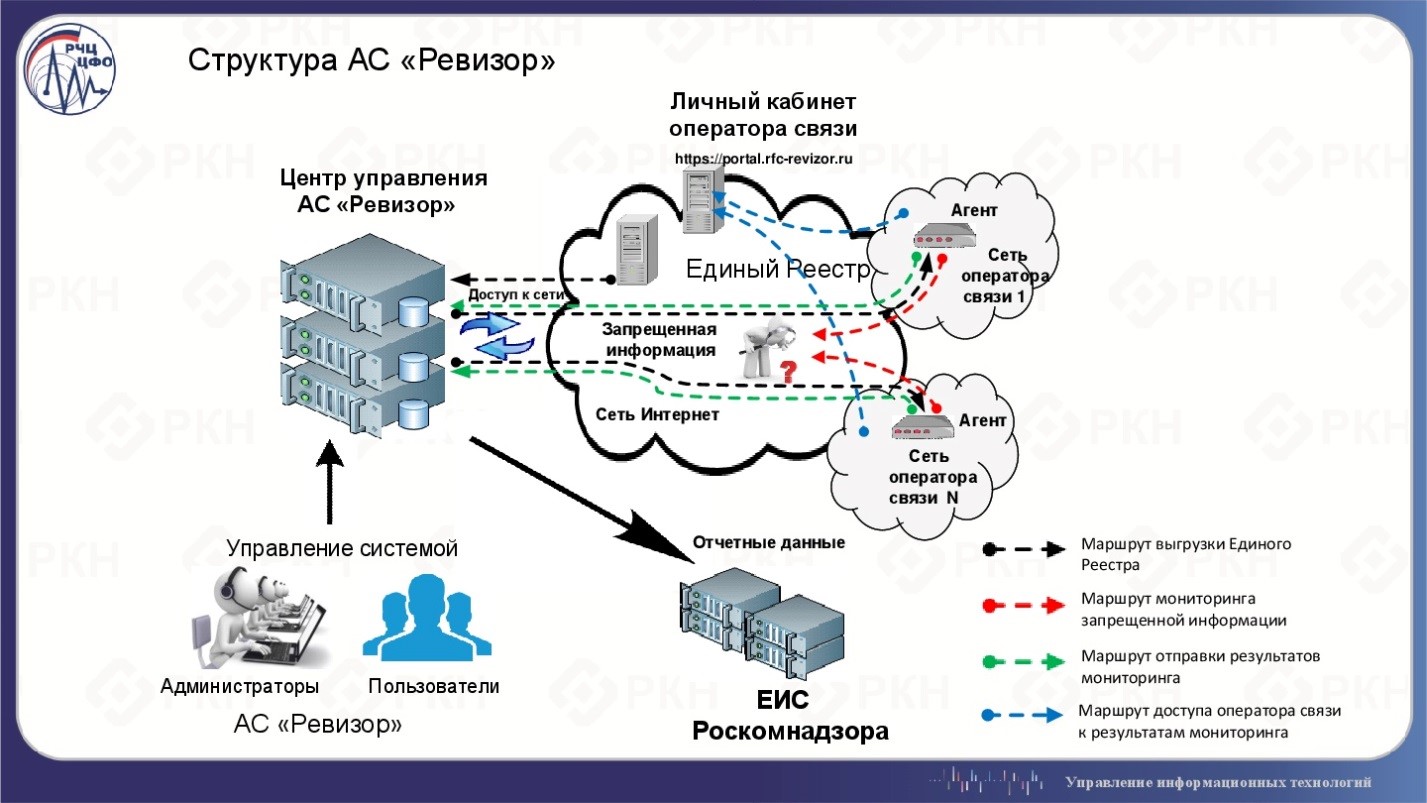
Software and hardware-software solutions for filtering Internet traffic (DPI-solutions) allow operators to block traffic from users to sites from the RKN list. Block them or not, it checks the client AC Examiner. It is a list of RKN automatically checks the availability of the site.
An example of a monitoring protocol is available here .
Last year, Roskomnadzor began testing solutions for blocking, which the operator can use to implement this scheme by the operator. I will quote from the results of such testing:
“The positive conclusions of Roskomnadzor were received by specialized software solutions“ UBIC ”,“ EcoFilter ”,“ SCAT DPI ”,“ Tiksen-Blocking ”,“ SkyDNS Zapret ISP ”and“ Carbon Reductor DPI ”.I will add that up to 27 telecom operators with different numbers of subscribers from different federal districts of the Russian Federation took part in testing each software product.
The conclusion of Roskomnadzor was also obtained, confirming the possibility of using by operators of the ZapretService software as a means of restricting access to prohibited resources on the Internet. The test results showed that when installed according to the “broken” connection scheme recommended by the manufacturer and the network operator’s network was correctly configured, the number of violations detected according to the Unified Register of Prohibited Information does not exceed 0.02%.
Thus, telecom operators are given the opportunity to choose the most appropriate solution for them to restrict access to prohibited resources, including from the list of software products that have received a positive conclusion from Roskomnadzor.
At the same time, during testing of the software product IdecoSelecta ISP, due to the lengthy procedure of its deployment and configuration, some operators were unable to proceed to the tests on time. More than half of the telecom operators participating in the testing did not exceed a week for the test operation of Ideco Selecta ISP. Considering the small amount of statistical data obtained and a small number of participants in the testing, Roskomnadzor in its official opinion indicated that it was impossible to obtain unambiguous conclusions about the effectiveness of the Ideco Selecta ISP product as a means of restricting access to prohibited resources on the Internet. ”
The official conclusions on the results of testing can be found here . In these conclusions almost zero technical information. You can read about the product “Ideco Selecta ISP” to know how not to do it.
This year, testing will continue and at the moment, judging by the news of Roskomnadzor, one product has already been taken and another 2 in the near future.
What if a lock occurred by mistake?
In conclusion, I would like to remind you that Roskomnadzor is “not mistaken,” which is confirmed by the Constitutional Court.
The resolution, which effectively removes responsibility from Roskomnadzor for the erroneous blocking of sites, was made as part of the consideration of the complaint to the Constitutional Court by the director of the Internet Publishers Association Vladimir Kharitonov. It said that in December 2012, Roskomnadzor mistakenly blocked its online library digital-books.ru. As Mr. Kharitonov explained, his resource was located on the same IP address as the rastamantales (.) Ru portal (now rastamantales (.) Com), which was the original object of blocking. Vladimir Kharitonov tried to challenge the decision of Roskomnadzor in court, but in June 2013 the Tagansky District Court recognized the blockage as legal, and in September 2013, the decision was upheld by the Moscow City Court.
From the same place:
In Roskomnadzor "b" said that the decision of the COP are satisfied. “The Constitutional Court confirmed that Roskomnadzor is implementing the law. If the operator does not have the technical ability to restrict access to a separate page of the site, and not to its network address, then it is the responsibility of the operator, ”the spokesman said.
This question is also relevant for cloud providers and hosting companies, as similar incidents happened to them. In June 2016, Amazon S3 cloud service was blocked in Russia, although only the 888poker poker room page located on its platform was added to the registry at the request of the Federal Tax Service. Blocking the entire resource was linked to the fact that Amazon S3 uses the secure https protocol, which does not allow to block individual pages. Only after Amazon itself deleted the page to which claims had arisen from the Russian authorities, the resource was excluded from the registry.
Source: https://habr.com/ru/post/347964/
All Articles