Security of third-party dependencies - check with snyk
Recently there was an excellent publication “A story about how I steal credit card numbers and passwords from visitors to your sites” , to which I translated the answer. The author recently published the second part , but I suspect that there will be no translation - it is proposed to solve the problem in excellent ways, such as translating important input elements “into a separate iframe” or “into special pages without third-party javascript”. At this point, those who led to the first article should have doubted the adequacy of the author - and the low (relative to the previous) rating of the new article shows this.
UPD : translated yet .
Nevertheless, the problem of third-party dependencies is there, and it needs to be solved somehow. And it costs equally in any ecosystem where third-party dependencies are used. In the comments to the previous post, we have already requested some solution, and I want to present one of them - a tool called snyk.
')

Snyk is quite a popular tool, but on Habré I have not yet met his mention. He can check dependencies for many ecosystems (Javascript, Ruby, Python, Scala and Java) on his own base - and the authors claim that their base of vulnerabilities is large. You can look at it with my own eyes. The project code is open, it is on the githaba and it has quite a few stars and forks:
The description is taken from the project site , we make a discount on the marketing bullshit, there are repetitions in the original. Personal impressions will be lower.

You can try this thing very quickly - just do
Yes, as you understand, the tool itself is written in Node.JS, and you need npm. You will also need to log in to the site, it can be done through several services - github, google, bitbucket. In addition, you can test the package without installation, right on the site - and get a clear report like this . And, of course, you can get a beautiful badge like this:

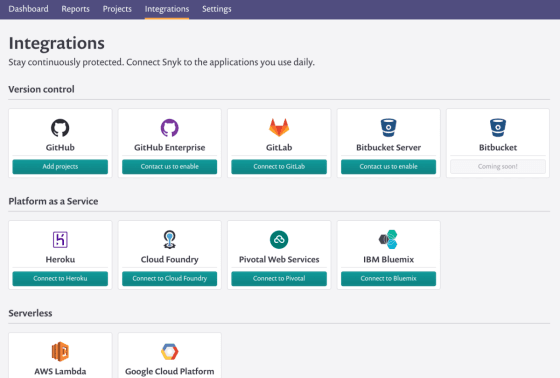
Naturally, you can also integrate it into your CI, but everything is so obvious that you don’t want to write about it.
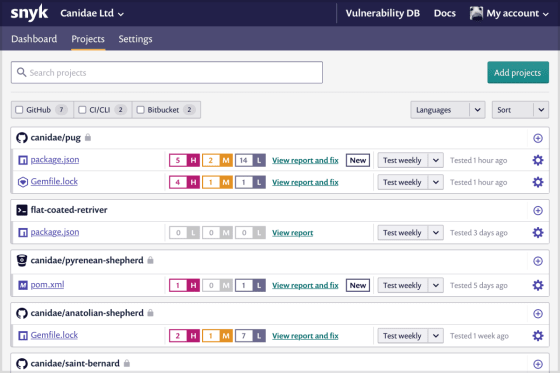
Once you have installed snyk, it just works. So far I have tried it only on Node.JS projects, and some unpleasant aftertaste remains. At a minimum, I noticed that in the absence or in the empty node_modules directory, the check considers that there are no dependencies, and this means that everything is fine in the project. The fact that you could carry them by hand, they could not be fully established, and so on - is not taken into account. But in general, the report turned out to be quite good - although in fact it all comes down to keeping the dependencies up to date. Which is very obvious and without a special tool. However, we all know that it is not always possible to “just pick up and upgrade” to a new major version, and the presence of a critical vulnerability, which the monitoring tool warned about in time, can serve as a good incentive not to postpone it for a long tomorrow.

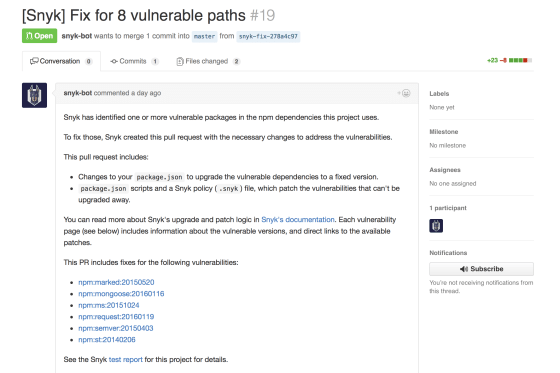
A few more upset the quality of the code of the project itself. It doesn’t bother me that it is written in ES5 (although why then is it Babel’s project?) - but the code itself doesn’t look very nice. It also grieves me that I don’t see active work with pull requests ( for example, mine , where I just corrected the problem described above with node_modules - and in general, it seems, 2 of 23 were taken ). Well, it is strange that the project related to updating and security of the modules itself contains a bunch of obsolete dependencies, and there are a large number of different “bikes” in it.
Again, I am somewhat confused by the amount of marketing in a project. For example, the fact that the verification process itself is called a vulnerability check, and a badge indicates the number of vulnerabilities. This is not true. The maximum that snyk checks are vulnerable dependencies, but not vulnerabilities. These concepts simply can not be replaced. And in the same way it is impossible to show that the project which is not containing dependences, does not possess vulnerabilities. This is a terrible substitution of concepts. Although it is possible that this is just my paranoia - I still consider the awfully hypocritical green lock and the “Secure” sign in the browser when using SSL ...
Anyway, this project has a big plus - it works. It is claimed and developed. So I sincerely wish him to become better, and I hope that we will someday have a good and reliable solution for the global problem of dependency vulnerabilities in our projects.
UPD : translated yet .
Nevertheless, the problem of third-party dependencies is there, and it needs to be solved somehow. And it costs equally in any ecosystem where third-party dependencies are used. In the comments to the previous post, we have already requested some solution, and I want to present one of them - a tool called snyk.
')

Snyk is quite a popular tool, but on Habré I have not yet met his mention. He can check dependencies for many ecosystems (Javascript, Ruby, Python, Scala and Java) on his own base - and the authors claim that their base of vulnerabilities is large. You can look at it with my own eyes. The project code is open, it is on the githaba and it has quite a few stars and forks:

Main features
The description is taken from the project site , we make a discount on the marketing bullshit, there are repetitions in the original. Personal impressions will be lower.
Search
- Search for vulnerabilities in Javascript, Ruby, Python, Scala and Java
- Checking GitHub Repositories
- Checking open source packages before use
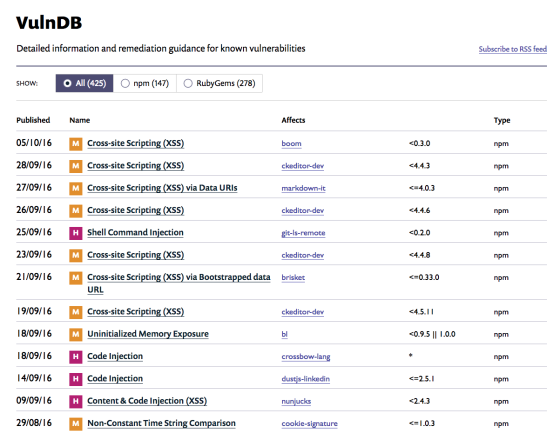
- Uses its own database of vulnerabilities Snyk

Monitoring
- Application dependency checking
- Integration into CI processes
- Warnings about new vulnerabilities in real time
- Application Support on AWS Lambda and Heroku

Correction
- Update or fix vulnerable dependencies
- Automatic pull requests from Snyk in the gihub repository on Node.js and Ruby
- Pull Requests with selected fixes
- Interactive Assistant for quick fixes
- Notification of new vulnerabilities that affect your projects
- Notifications in Slack and by email about vulnerabilities and fixes
- Understandable Uzizymosti
? High severity vuln found in handlebars@3.0.0,
introduced via handlebars@3.0.0
- desc: Content Injection (XSS)
- info: snyk.io/vuln/npm : handlebars: 20151207
Remediation options
> Upgrade to handlebars@4.0.0 (potentially breaking change)
Patch (no patch available, there is one)
Set to ignore for 30 days (updates policy)
Skip
Prevention
- Snyk can check pull requests that can make your applications on Node.js, Ruby, Python, Scala and Java vulnerable
- You can use Snyk in CI for automated tests.
- You can customize the desired security level for your needs and priorities.

Integration
- Automatic monitoring of your github repositories
- Adding Snyk to CI Processes
- Flexible policies customizable to your team

Teamwork
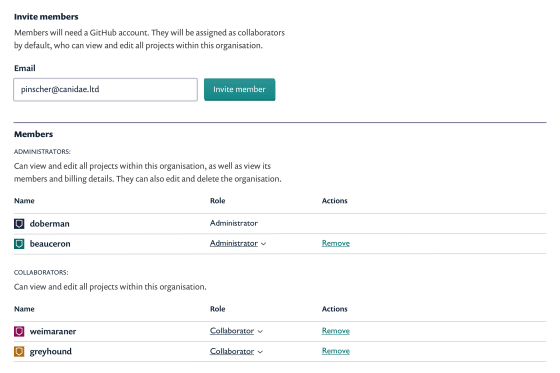
- Use Snyk Organizations for teamwork.
- Administrator and Member Roles
- Anyone on the team can search and fix vulnerabilities.
- Only the right people will be notified of new vulnerabilities.

Training
- Subscribe to the vulnerability base to learn about them in time.
- Learn about how to exploit vulnerabilities and how to fix them.

Personal impressions
Installation
You can try this thing very quickly - just do
npm install -g snyk cd ~/projects/myproj/ snyk test Yes, as you understand, the tool itself is written in Node.JS, and you need npm. You will also need to log in to the site, it can be done through several services - github, google, bitbucket. In addition, you can test the package without installation, right on the site - and get a clear report like this . And, of course, you can get a beautiful badge like this:
Naturally, you can also integrate it into your CI, but everything is so obvious that you don’t want to write about it.
Using
Once you have installed snyk, it just works. So far I have tried it only on Node.JS projects, and some unpleasant aftertaste remains. At a minimum, I noticed that in the absence or in the empty node_modules directory, the check considers that there are no dependencies, and this means that everything is fine in the project. The fact that you could carry them by hand, they could not be fully established, and so on - is not taken into account. But in general, the report turned out to be quite good - although in fact it all comes down to keeping the dependencies up to date. Which is very obvious and without a special tool. However, we all know that it is not always possible to “just pick up and upgrade” to a new major version, and the presence of a critical vulnerability, which the monitoring tool warned about in time, can serve as a good incentive not to postpone it for a long tomorrow.

A few more upset the quality of the code of the project itself. It doesn’t bother me that it is written in ES5 (although why then is it Babel’s project?) - but the code itself doesn’t look very nice. It also grieves me that I don’t see active work with pull requests ( for example, mine , where I just corrected the problem described above with node_modules - and in general, it seems, 2 of 23 were taken ). Well, it is strange that the project related to updating and security of the modules itself contains a bunch of obsolete dependencies, and there are a large number of different “bikes” in it.
Again, I am somewhat confused by the amount of marketing in a project. For example, the fact that the verification process itself is called a vulnerability check, and a badge indicates the number of vulnerabilities. This is not true. The maximum that snyk checks are vulnerable dependencies, but not vulnerabilities. These concepts simply can not be replaced. And in the same way it is impossible to show that the project which is not containing dependences, does not possess vulnerabilities. This is a terrible substitution of concepts. Although it is possible that this is just my paranoia - I still consider the awfully hypocritical green lock and the “Secure” sign in the browser when using SSL ...
Anyway, this project has a big plus - it works. It is claimed and developed. So I sincerely wish him to become better, and I hope that we will someday have a good and reliable solution for the global problem of dependency vulnerabilities in our projects.
Source: https://habr.com/ru/post/347934/
All Articles