DCShadow - Active Directory Attack Technique

On January 24, 2018, Benjamin Delpy and Vincent Le Toux demonstrated a new attack technology against the Active Directory infrastructure at the Microsoft BlueHat security conference.
The name of the new attack technique is DCShadow. Such an attack allows an attacker to create a fake domain controller in an Active Directory environment to replicate malicious objects into the Active Directory working infrastructure.
First of all, the attack is noteworthy because its author is the author of the utility mimikatz , one of the most popular tools for exfiltration of passwords in a Windows environment. Based on it, many utilities and frameworks for post-operation in a Windows environment work. At the time, she made a lot of noise, allowing you to get Windows passwords of users in the clear.
')
The DCShadow attack uses the DrsReplicaAdd trigger ( DRSR 4.11.19.2) to start replication. This allows you to change the replTo attribute of the domain controller and perform immediate replication.
The main attack vector DCShadow is to create a new server and nTDSDSA objects in the Configuration section. The attack technique is well represented in the following diagram:
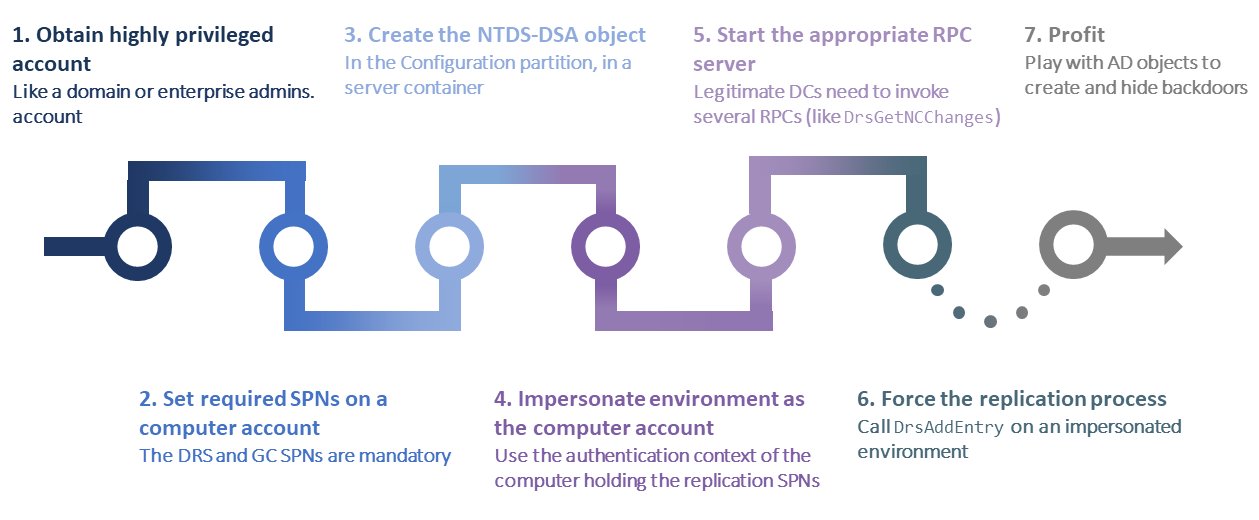
With DCShadow, you no longer need to try to replicate data; you need to register new domain controllers in the target infrastructure in order to deploy Active Directory objects or modify existing ones (by replacing the contents of attributes). The idea of a fake domain controller is not new and has already been used for attacks, but it required invasive methods (for example, installing a Windows Server virtual machine).
In order for a server to be a domain controller, it must perform the following functions:
- use a data warehouse capable of replicating its information over LDAP protocols, conforming to MS-DRSR and MS-ADTS specifications;
- be a source of authentication available via the Kerberos, NTLM, Netlogon or WDigest protocols;
- use the group policy management system;
- DNS provider (optional role).
In addition to hosting these services, the domain controller in the creation process must be registered in the directory infrastructure, which must be accepted by another domain controller as a replication source. Data replication is organized using the built-in NTD service process, called Knowledge Consistency Checker (KCC). The main function of KCC is to create and maintain replication topology. By default, the KCC initiates replication every 15 minutes to ensure consistent and regular updates.
The DCShadow authors defined the minimum set of changes necessary to introduce a new server into the replication topology. To achieve this goal, the DCShadow attack must modify the target Active Directory infrastructure database to allow the spoofed server to be part of the replication process.
According to the MS-ADTS specification, a domain controller is represented in an Active Directory database by an object of the nTDSDSA class, which is always in the context of a domain configuration naming convention. NTDS-DSA objects can only be created as child objects of the server, which, in turn, can only be part of an organization or server object. Thus, the purpose of the DCShadow attack is to create a new server and nTDSDSA objects in the “Configuration” section of the scheme.
However, it is not enough to simply add an object to allow a fake server to initiate replication. To be part of the replication process, two requirements must be met:
- trust other servers;
- Provide authentication support for connecting other servers to a counterfeit server to replicate data.
Using a valid account, a fake server can be considered as a reliable Active Directory server. The Kerberos SPN attributes will provide authentication support for other domain controllers.
This requirement is fulfilled using Kerberos (SPN). SPNs are used by the Kerberos service (KDC) to encrypt a Kerberos ticket with a computer account associated with an SPN. The DCShadow technique allows you to add an SPN used for authentication.
The authors of the attack technique identified a minimum set of SPNs needed to go through the replication process. The results of their research show that two SPNs require another domain controller to connect to a fake server:
- DRS class ( GUID E3514235-4B06-11D1-AB04-00C04FC2DCD2 );
- global catalog class (GC).
DCShadow allows you to install these two SPNs on an attacking computer using the DRSAddEntry RPC function. Now you can register a fake domain controller to participate in the replication process and authenticate with another domain controller.
The final step in the DCShadow attack is to launch the replication process. For the following is necessary:
- wait until the KCC process of another domain controller starts the replication process (15 minutes);
- make replication by calling the DRSReplicaAdd RPC function, which names the contents of the repsTo attribute, which will immediately replicate data.
Forced replication using IDL_DRSReplicaAdd RPC is the last step of the DCShadow attack. This allows arbitrary data to be entered into the target AD infrastructure. At the same time, it becomes possible to add new users to the administrative group, etc.
It should be noted that DCShadow is not a vulnerability, it is rather an innovative way to enter illegitimate data into the Active Directory infrastructure. This may allow an attacker to apply new methods of covert seizure in successfully attacked systems.
Source: https://habr.com/ru/post/347844/
All Articles