File system steganography
Hi, Habr.
I want to introduce you to a small project on steganography , made in free time from school.
I made a project on the hidden storage of information in the file system (hereinafter FS ).
It can be applied to steal confidential information for educational purposes.

In the form of a prototype, a very old Linux ext2 FS was chosen.
Implementation
Implementation Considerations
If the ext2 standard is good, then you can replace that there is a so-called Superblocks in the file system, which contains basic information about the system. After me, Block Bitmap and Inode Table were found. Almost immediately the idea of recording information in currently empty FS blocks was born. Now it was worth thinking about protection from a programmer armed with a hex editor .
If you store the hidden information without encryption, then, despite its blurring by the file system, it will still be too striking, especially if the programmer knows what to look for. Therefore, it was decided to encrypt all blocks of the source file. I chose the AES block cipher, but as you know, it doesn’t matter.
To separate the necessary blocks from all the others, it was decided to add a special marker to the beginning of the block in each block when reading. This token was encrypted depending on the block number in the source file. This trick immediately allowed not only to find the necessary blocks, but also to recognize their correct order.
The general principle of the system.

Write algorithm
The points:
- First write any information to the original file system;
- Delete this information (not necessarily all);
- The file for hiding is divided into blocks of the same length by adding a marker;
- Encrypt these blocks;
- Place encrypted blocks in empty FS blocks.
Below is a flowchart of the recording algorithm. The algorithm receives four files as input:
- Image of a variable file system;
- File subject to steganography;
-File encryption file for AES;
-File with a marker.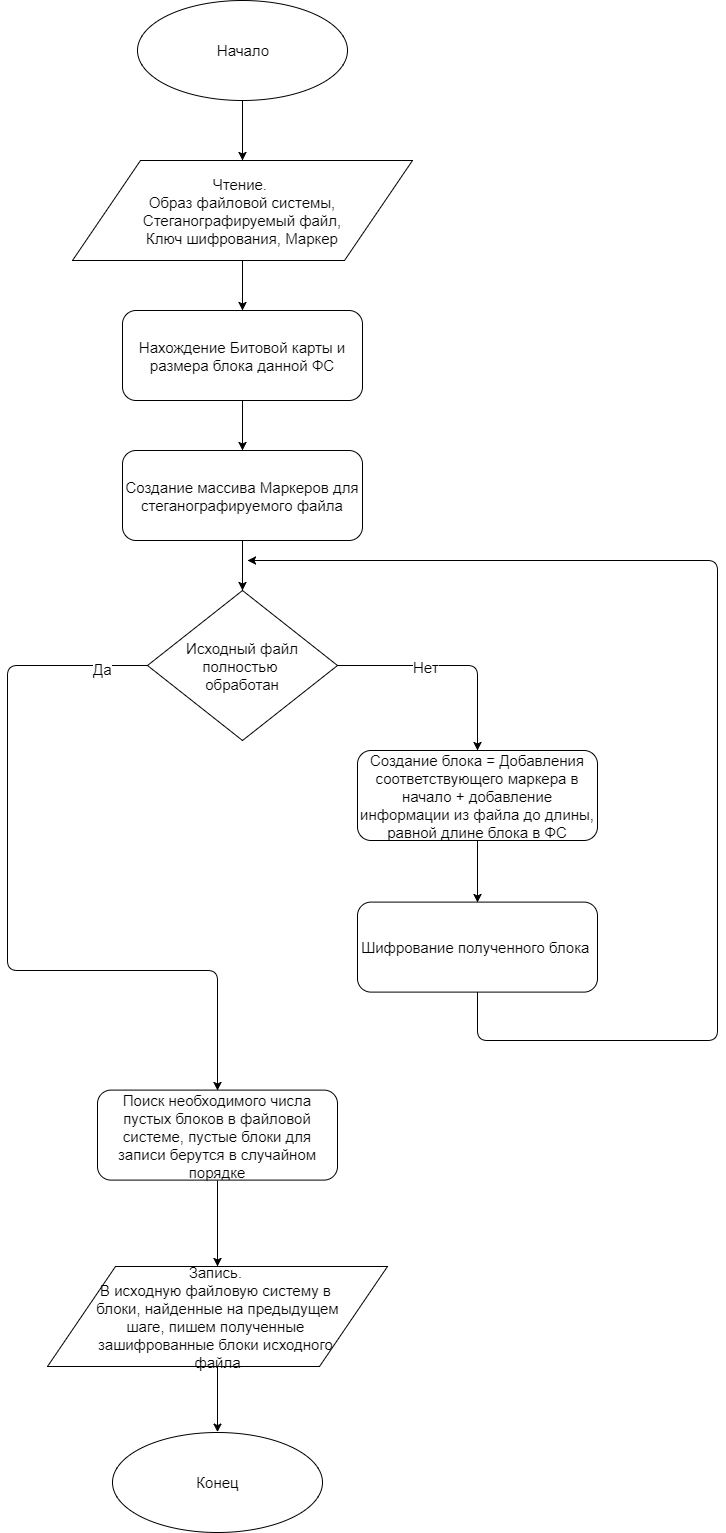
Immediately it should be noted that this algorithm has one drawback: after writing a file to the file system, you cannot write anything new to the file system, since any new information can get into those blocks that we assigned to our zip file, however, this also opens up "Fast sweeping tracks."
But it is quite obvious how this can be fixed: it is necessary to rewrite the algorithm for writing blocks in a file system. This is an understandable, but incredibly time consuming task.
For Proof Of Consept, I did not implement it.
The result is the following changes in the FS, this is how the FS looks like before steganography (the audio file was previously recorded).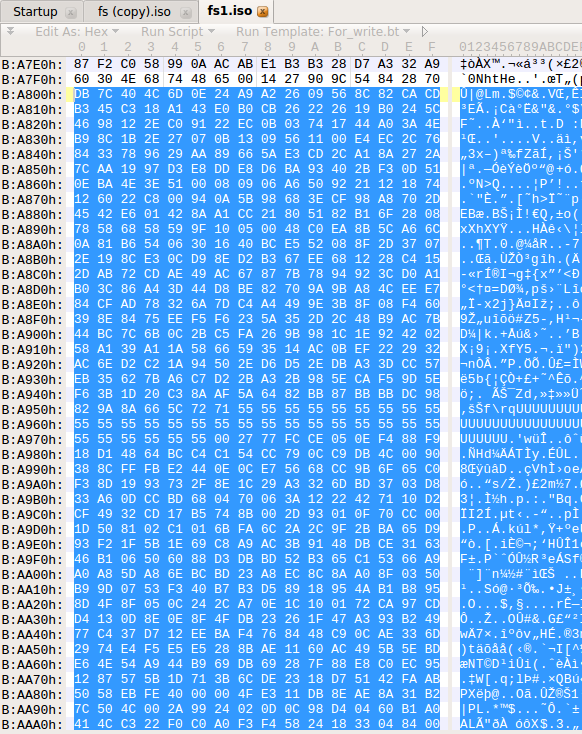
And this is what a file system looks like with already zasteganograph information.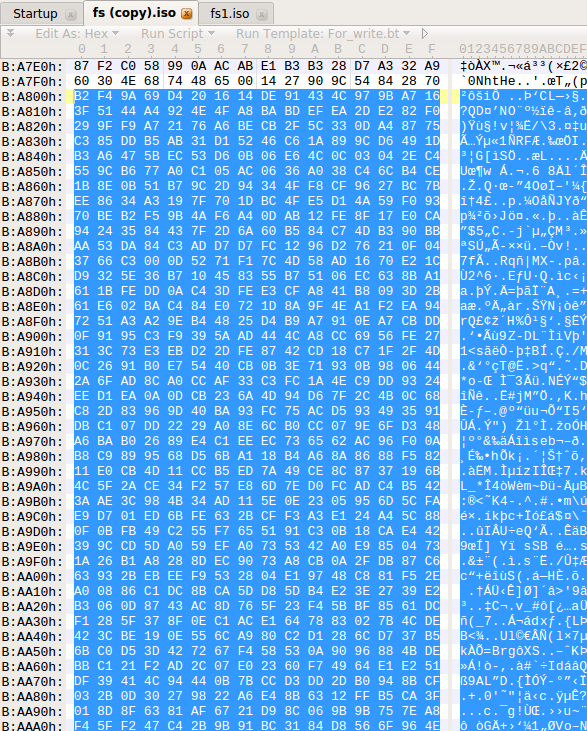
Reading algorithm
The points:
- With the knowledge of the key and the method of constructing the markers, compile the first N markers, with the guarantee that N multiplied by the file system block length is longer than the zip file;
- Search for blocks in FS, starting with markers;
- Decrypt the received blocks and separate the markers;
- Collect the received blocks in the correct order and get the source file.
Below is a flowchart of the recording algorithm. The algorithm receives three files as input:
- Image file system;
-File encryption file for AES;
-File with a marker.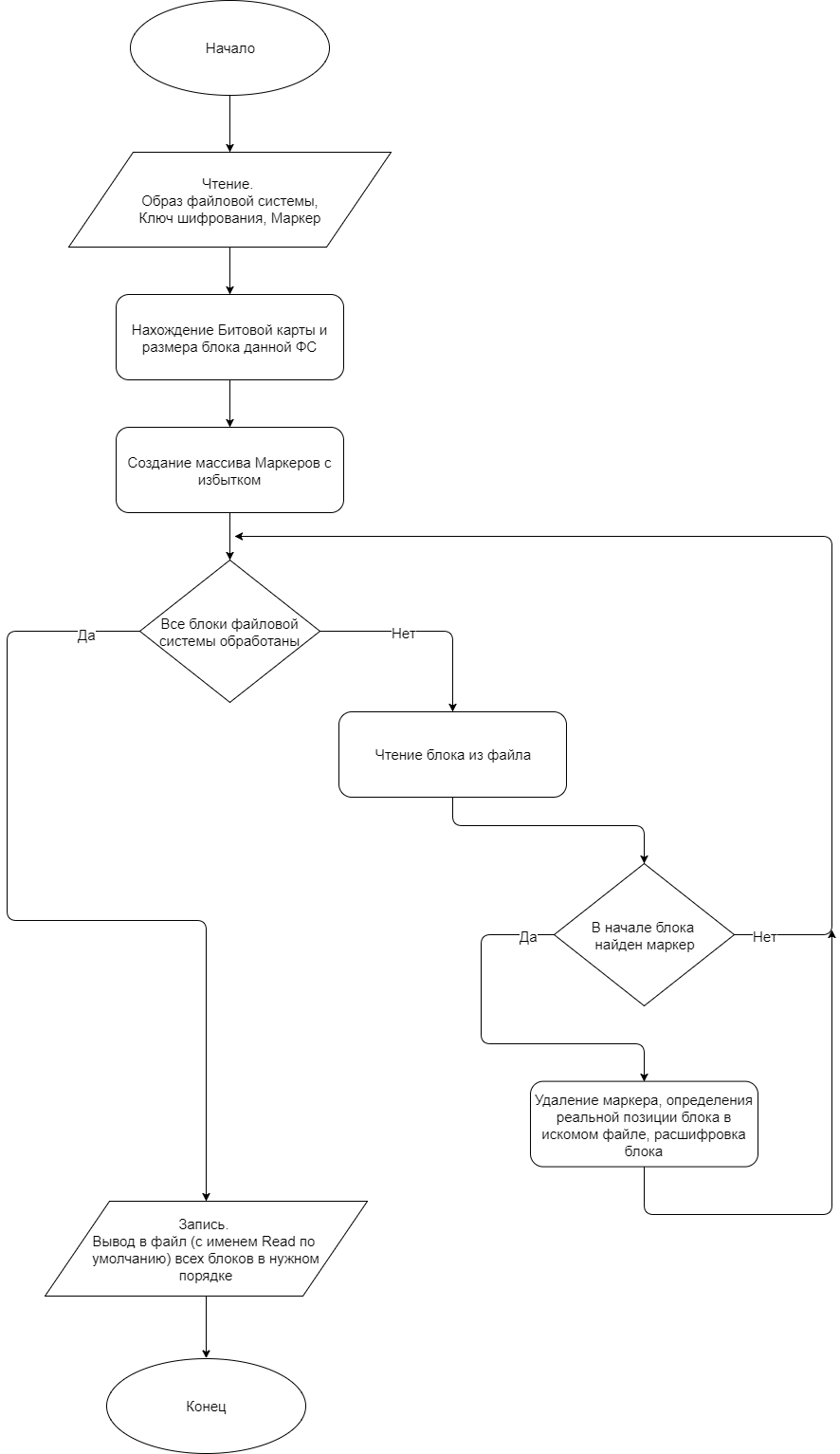
After the program has been running, the Read file appears, which will be the file extracted from the steganographized FS, if the key or token was entered incorrectly, then the Read file will be empty.
(for lovers of beautiful things, you can intersperse not only a file, but a "header" containing meta information: the name of the file, the rights, the last modification time, etc.)
Startup automation
For convenience, bash scripts have been written that automate Linux launches (tested on Ubuntu 16.04.3 LTS).
Let's sort start in steps.
Record:
- sudo Copy_Flash.sh “DEVICE” - we get the image of FS from DEVICE (flash);
- ./Write.sh “FILE” “KEY” “MARKER” - create a virtual environment, download the necessary libraries and start writing to skip;
- sudo ./Write_Flash.sh “DEVICE” - write the changed filesystem to DEVICE again.
Reading:
- sudo Copy_Flash.sh “DEVICE” - we get the image of FS from DEVICE (flash);
- ./Read.sh “KEY” 'MARKER ”- create a virtual environment, download the necessary libraries and run the skipt for reading;
- In the current directory, open the Read file - this is the zip code.
Conclusion
This method of steganography probably needs further work, additional testing and expansion to more popular file systems, such as Fat32 , NTFS and ext4 .
But the purpose of this work was to show the principle by which it is possible to carry out the hidden storage of information in the file system.
Using such algorithms, one can safely store information, and if, with knowledge of the key, such a system can be hacked without a complete search (but a very long algorithm), then without knowing the key, this system seems to me absolutely stable, however this may be the reason for a separate article.
All code is implemented in Python version 3.5.2. An example of work is presented on my youtube channel. The full code of the project is laid out on github .
(Yes, yes, I know that for the production version you need to write on something "fast", for example in C;))
In this implementation, the size of the input file for steganography should not exceed 1000 KB.
I want to thank the PavelMSTU user for valuable advice when planning a study and recommendations on the design of the article.
')
Source: https://habr.com/ru/post/347604/
All Articles