We use Apple Pay and Troika card as a pass to work
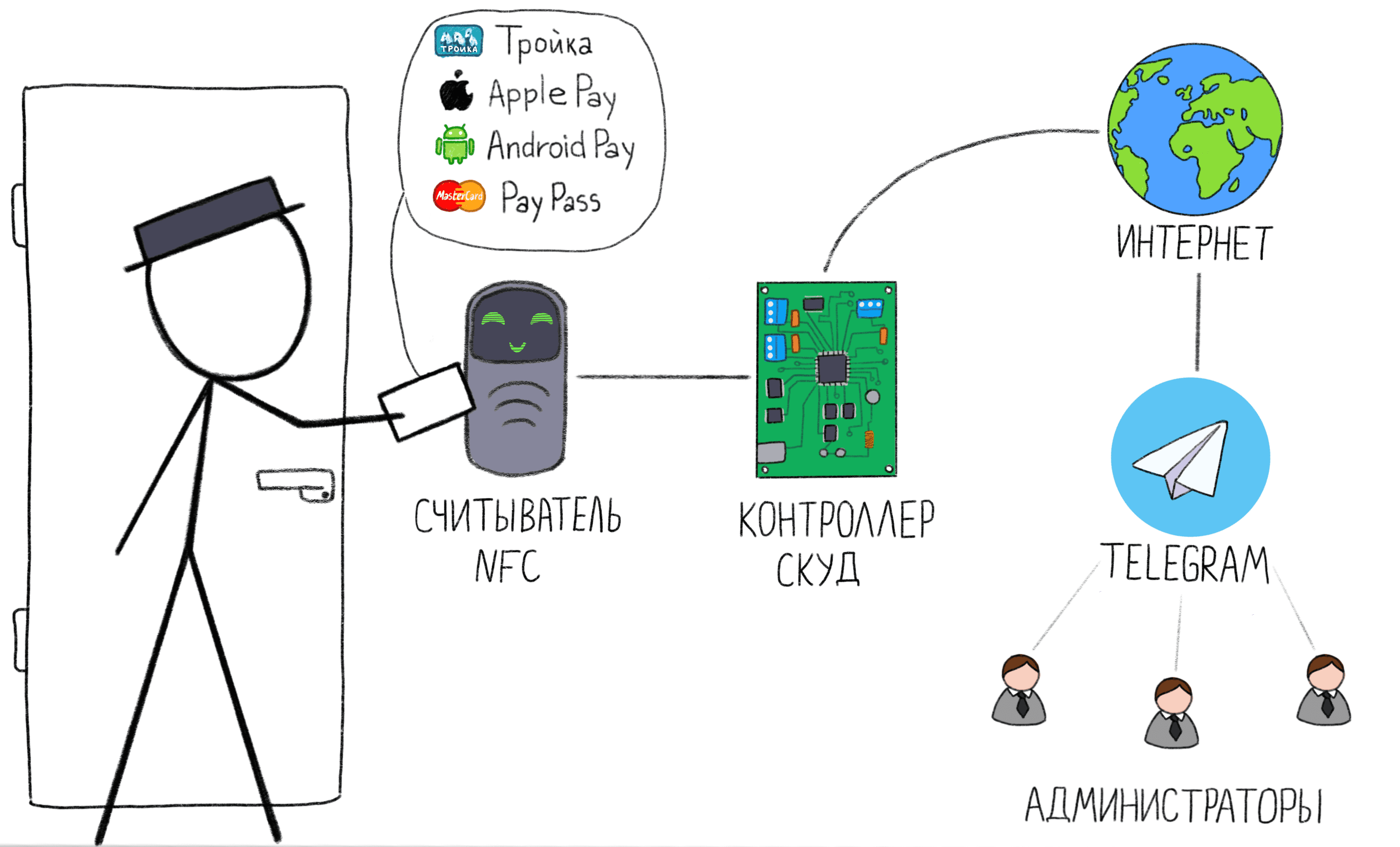
TL; DR. The article describes the process of creating an access control system (ACS), in which three cards, any contactless EMV bank cards, as well as Apple Pay and Android Pay phones can be used as an identifier. The system is controlled via Telegram-bot.
The main tasks of the system
- Get rid of unnecessary cards - as an identifier is used that which the user already has: a transport card, phone or bank card. Which ID to use - everyone chooses. The system works with all types of identifiers simultaneously.
- Get rid of the pass office and complex management programs - we are tired of issuing and collecting cards from users, keeping separate computers for managing passes, studying advanced programs.
- Management through Telegram - establishment and deletion of users occurs remotely and does not require a computer.
Please do not need more cards!

- Do you already have our card?
- have mercy ...
')
Now everyone wants to give you his card: shops, fitness clubs, parking lots, business centers, VIP-discount-points-savings. It is humiliating to offer a person to carry another card with them. And given that the EM-Marine (125kHz) standard cards, which are popular in access control systems in the CIS, are three times thicker than the usual ISO 7810 - this is triple humiliating.
Therefore, the first requirement for our system is no additional cards .
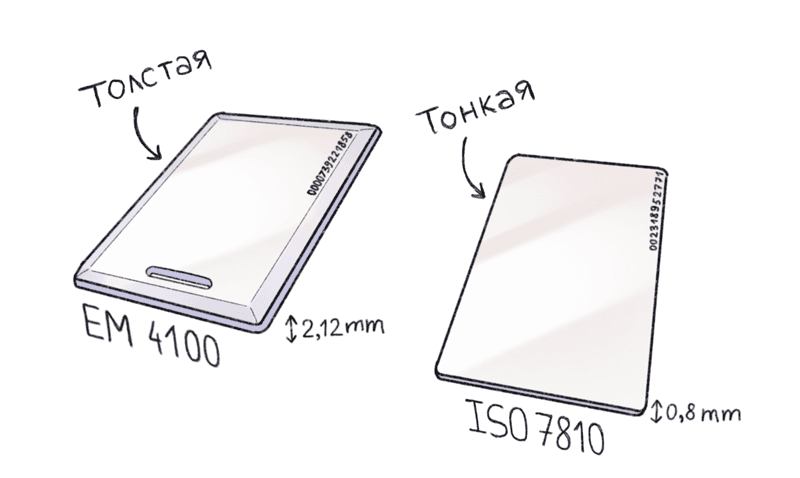
Em-Marine and ISO7810 card thickness comparison
In addition to physical dimensions, EM-Marine cards are technologically backward. Such a card can be easily cloned from a distance of half a meter straight from the pocket of a passerby.
Demo video: www.youtube.com/watch?v=qvIIUny4EWI
The video shows the reading of a thin em4100 card from a distance of 50cm, thick cards are read from a greater distance.
All access control uncomfortable
All existing access control systems, in our opinion, are too complicated and inconvenient. They require the issuance of individual cards, installation of programs, staff training, memorizing the sequence of actions with master cards, etc.
In some cases, complex access control systems are necessary: in large buildings with multiple access zones, turnstiles, security guards, temporary passes.
In cases where you need to control access to one or two doors, such complications are not justified. Even the content of a separate computer with a program for access control is a bust for us.
We do not have separate employees engaged in the issue of passes, there is no temporary passes and security. System administration should be so simple that any new person can quickly master it without instructions. Since the person responsible for the access control system may not be in place, system management must be remote.
Card "Troika" as an identifier
The Troika card is a rechargeable card for the fare payment on all types of Moscow public transport. This is the most profitable and convenient way to pay for public transport and some urban services: a planetarium, a skating rink, zoos, the Tretyakov Gallery, parking. Therefore, the "Troika" is in every Muscovite, who regularly uses public transport. You can purchase a card at the cash desks of the metro for ≈ $ 1.
Technically, the card is based on the Mifare Plus chip operating in SL1 mode - Mifare Classic 1K emulation mode. On the back of the card is a 10-digit number that is used to remotely recharge the card’s balance. This number is convenient to use as an identifier in the access control system.
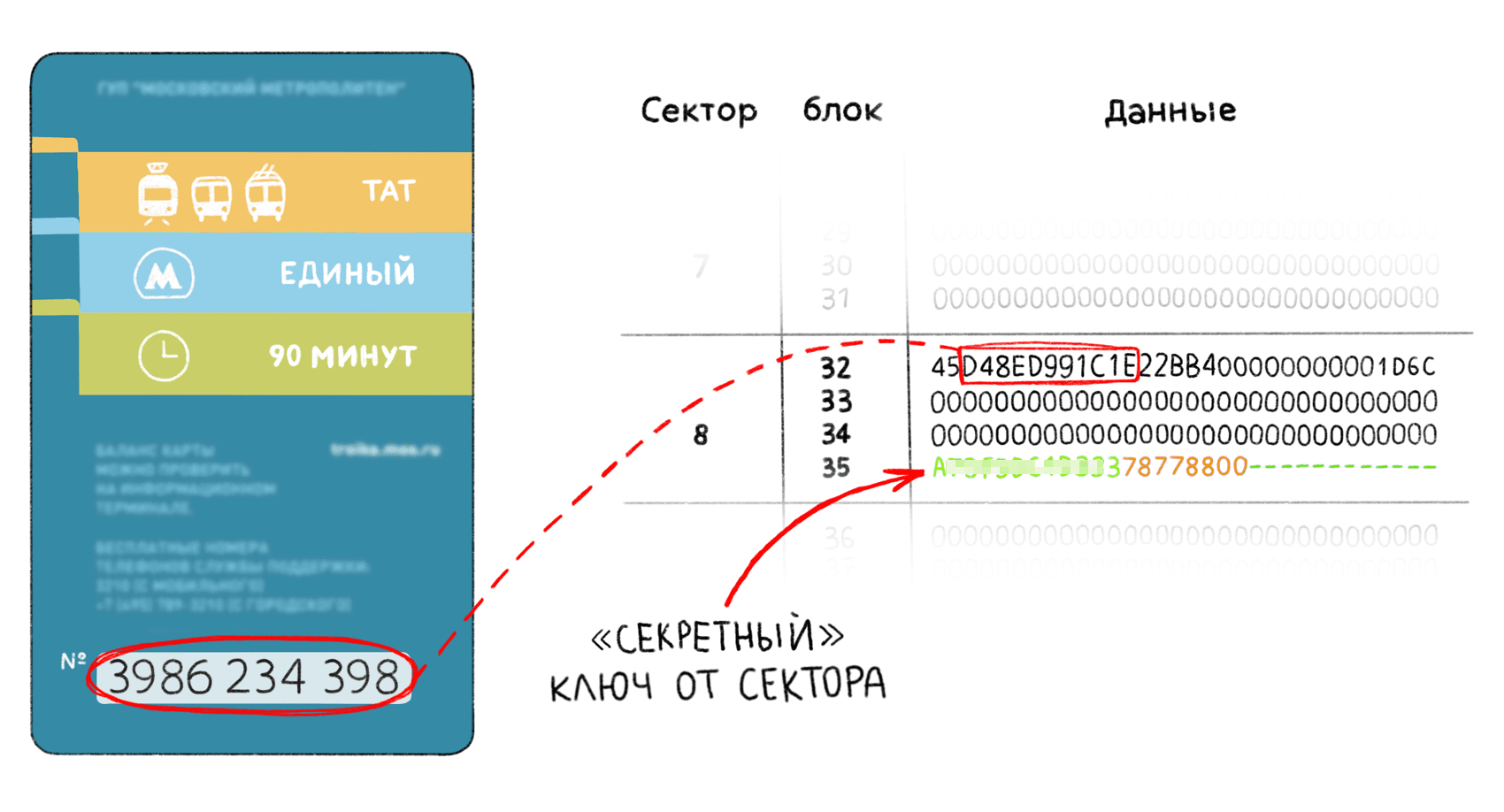
The “Troika” card number is recorded in the card's memory in the 32nd block of the 8th sector. To read a protected area of memory, a six-byte key is needed, which has not been so secret for a long time.
The “Three” card number (not to be confused with the chip's UID) is stored in protected memory in block 32 from the second byte to the lower four bits of the seventh byte. To read this area of memory, an A-key for sector 8 is needed. These keys are not a secret for a long time and are easily found on the Internet along with a detailed description of the data storage format. Since we are not going to record any data on the card, we only need key A to read the necessary sector.
Thus, to add a new pass to the database, it is enough to visually read the card number and inform the administrator. This can even be done remotely.
Security issues of this approach are discussed in the FAQ at the end of the article. Code samples for reading the Troika card number using the Arduino are in the “First prototype” chapter.In St. Petersburg, there is a similar card "Plantain." If necessary, it can also be used as an identifier, simultaneously with the Troika card.
Apple / Android Pay and Bank Cards

Payment instruments with different names work on the same EMV protocol
All payment instruments shown in the picture above work on the same EMV protocol, freely available on EMVco.com . Therefore, by saying "EMV-card", we will simultaneously mean Apple Pay, Android Pay, Samsung Pay, Visa PayWave, MasterCard PayPass.
There is a misconception that the POS terminal should separately support Apple / Android Pay, so users prefer to look at the checkout for a special icon to be sure that their payment tool is supported. In fact, almost everywhere where contactless payment is supported, any device will work.Contactless EMV cards (and contact cards too) allow you to read the data indicated below without authorization, that is, without entering a PIN code. In the last chapter, we will look at why it is safe enough.
// ( )
Cardholder Name: IVAN IVANOV
// ,
PAN: 4556 5386 2774 0649
//
Expiry date: 08/2019
// track 1 ( )
Track 1: ....
// track 2
Track 2: 4556538627740649.....
// . , .
//
Paylog: ...........
Cardholder Name , PAN ( ) . .
PAN . , 10 . , , .
, 10 , , EMV-.
EMV-
EMV- NFC-, APDU-. , Arduino $3
, EMV. — EMV Arduino .
. ( )
EMV :
SmartCard Scripter, PC/SC- HiD Omnikey. SmartCard Scripter pascal- . infintuary.org/scs_tut.php
APDU , :
: EMV Contactless Specifications — PPSE and Application Management for Secure Element
EMV- PPSE (Payment System Environment) SELECT.
APDU- SELECT PPSE
SELECT PPSE FCI (File Control Information) , . (VISA, MasterCard, AmericanExpress) , .
VISA SELECT PPSE
- TVL emvlab.org/tlvutils/. VISA, :
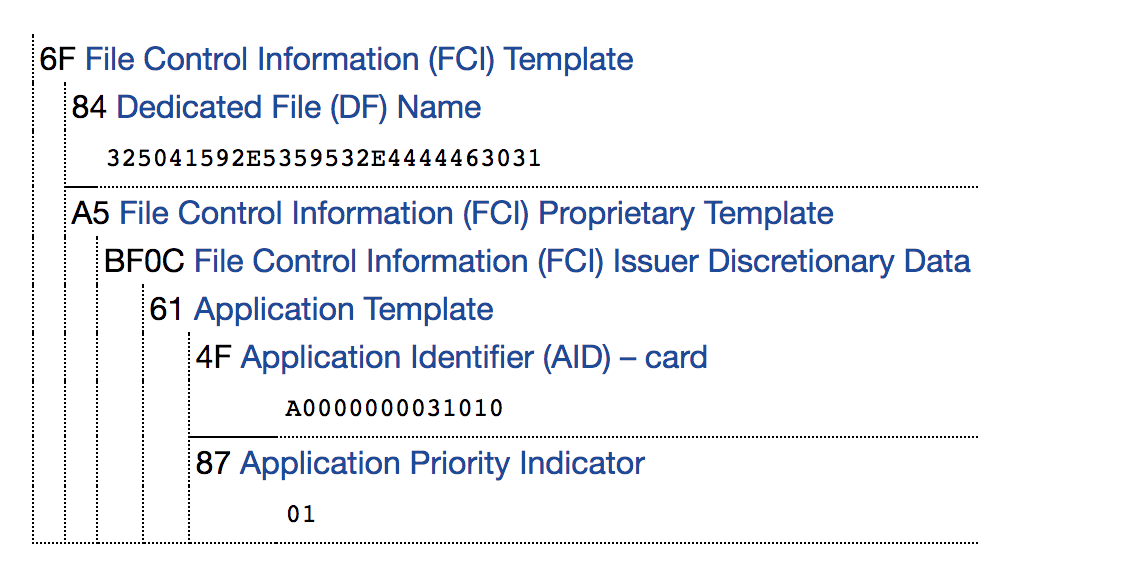
(AID). , A0000000031010, Visa International.
AID 4F. , . , AID 5 16 , 7 . AID , 4F 07 7 AID. , AID , , , Visa MasterCard. PPSE- : 6F, 90 00 4F 07, .
AID: eftlab.co.uk/knowledge-base/211-emv-aid-rid-pix
AID
AID, SELECT. Visa International, PPSE SELECT
APDU- SELECT AID
PDOL (Processing Options Data Object List). POS- — , , , , , .
PDOL . PDOL — . PDOL : eftlab.co.uk/index.php/site-map/knowledge-base/145-emv-nfc-tags.
, PDOL , , . - , — .
, PDOL. , PAN- , POS-. , PAN-. , PDOL.
. PDOL.
:
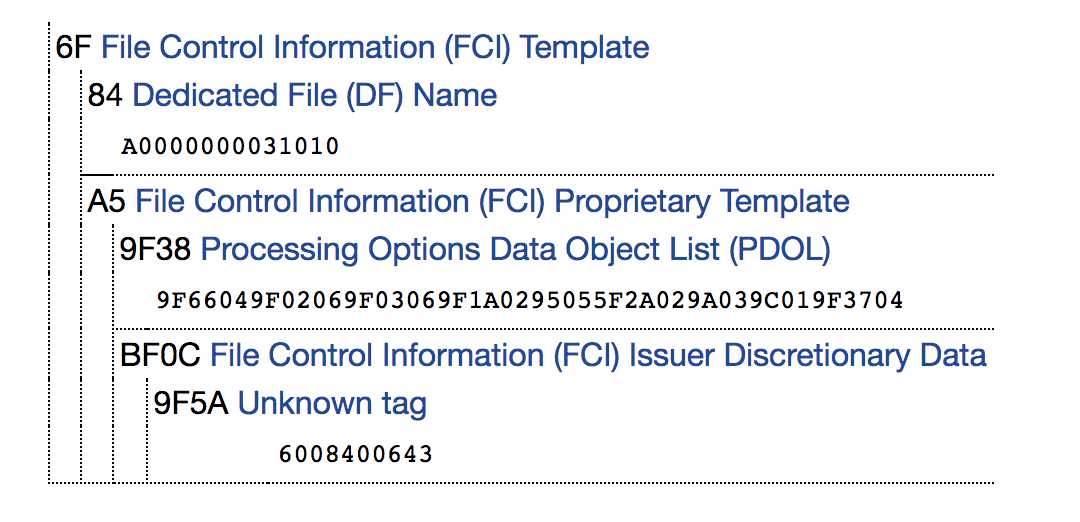
, PDOL 9F38 9F66049F02069F03069F1A0295055F2A029A039C019F3704. emvlab.org PDOL, Android- Credit Card Reader.
, . PDOL:
, emvlab.org. .
PDOL
PDOL EMV Contactless Specifications Book C-1/2/3 Kernel 1/2/3 Specification.
PDOL , , , PDOL. ( ), 33 . PDOL 33 .
, — PDOL, . , 6985 Conditions of use not satisfied.
, PDOL , Terminal Transaction Qualifiers (TTQ). VISA, , VCPS 2.1.1. TTQ :
TTQ .
MasterCard, , PDOL PAN- PDOL.
PDOL:
, , 77 SW2=9000. PAN-, . ()
EMV, , , , PAN-.
PAN- :
APDU- ( ? , )
57 13 5A 08. 8 .
, .
PAN- -
- PN532 breakout board + Arduino — pn532 Arduino SPI. pn532 — 3.3V, Arduino pro 3.3V, . EMV- Adafruit PN532, c EMV-.
- PN532 breakout board + USB-TTL — PN532 UART- libnfc
- PC/SC- — ACR122U, HiD Omnikey .
- Android NFC- — Credit Card Reader EMV- . APDU- . 100 (donate), Log APDU , . Java.
EMV. APDU EMVco, - .APDU- . PC/SC , ..
EMV , , , .
SmartCard Scripter, PC/SC- HiD Omnikey. SmartCard Scripter pascal- . infintuary.org/scs_tut.php
APDU , :
// UID
begin
APDU('FF CA 00 00 00');
end.— SELECT (PPSE)
: EMV Contactless Specifications — PPSE and Application Management for Secure Element
EMV- PPSE (Payment System Environment) SELECT.
APDU- SELECT PPSE
'00 A4 04 00 0E 32 50 41 59 2E 53 59 53 2E 44 44 46 30 31 00'
00 A4 04 00 // select
0E // command data (14 )
32 50 41 59 2E 53 59 53 2E 44 44 46 30 31 // command data 2PAY.SYS.DDF01
00 //
— SELECT AID
SELECT PPSE FCI (File Control Information) , . (VISA, MasterCard, AmericanExpress) , .
VISA SELECT PPSE
'6F 23 84 0E 32 50 41 59 2E 53 59 53 2E 44 44 46 30 31 A5 11 BF 0C 0E 61 0C 4F 07 A0 00 00 00 03 10 10 87 01 01 90 00'- TVL emvlab.org/tlvutils/. VISA, :

(AID). , A0000000031010, Visa International.
AID 4F. , . , AID 5 16 , 7 . AID , 4F 07 7 AID. , AID , , , Visa MasterCard. PPSE- : 6F, 90 00 4F 07, .
AID: eftlab.co.uk/knowledge-base/211-emv-aid-rid-pix
AID
A0000000031010 Visa International
A0000000032020 Visa International
A0000000041010 Mastercard International
A0000000043060 Mastercard International United States Maestro (Debit)
AID, SELECT. Visa International, PPSE SELECT
APDU- SELECT AID
'00 A4 04 00 07 A0 00 00 00 03 10 10'
00 A4 04 00 // select
07 // command data (7 )
A0 00 00 00 03 10 10 // AID Visa International
PDOL (Processing Options Data Object List)
PDOL (Processing Options Data Object List). POS- — , , , , , .
PDOL . PDOL — . PDOL : eftlab.co.uk/index.php/site-map/knowledge-base/145-emv-nfc-tags.
, PDOL , , . - , — .
, PDOL. , PAN- , POS-. , PAN-. , PDOL.
. PDOL.
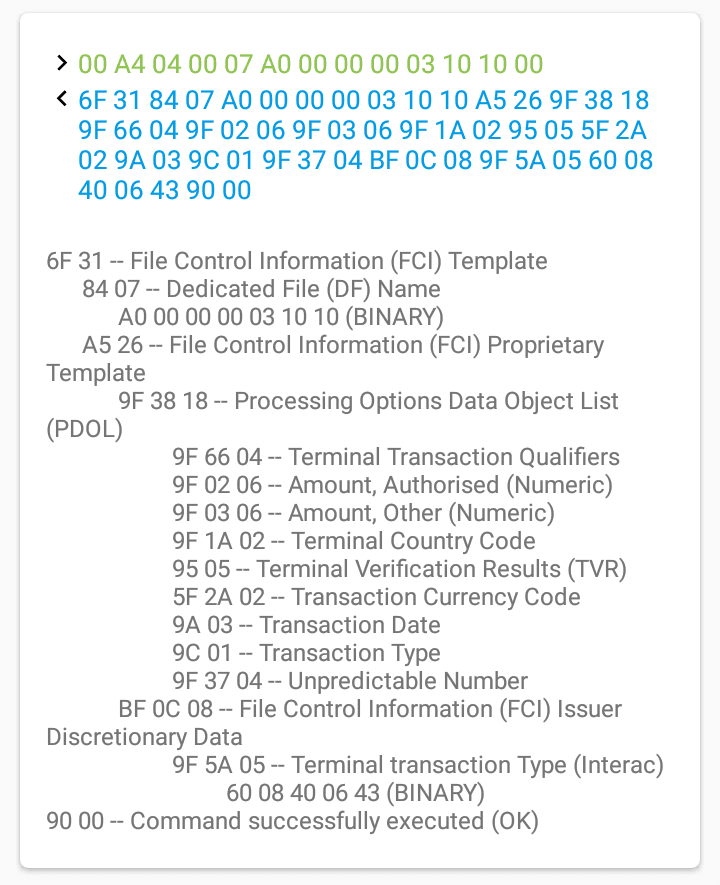
'6F 31 84 07 A0 00 00 00 03 10 10 A5 26 9F 38 18 9F 66 04 9F 02 06 9F 03 06 9F 1A 02 95 05 5F 2A 02 9A 03 9C 01 9F 37 04 BF 0C 08 9F 5A 05 60 08 40 06 43 90 00'
:

, PDOL 9F38 9F66049F02069F03069F1A0295055F2A029A039C019F3704. emvlab.org PDOL, Android- Credit Card Reader.
, . PDOL:

, emvlab.org. .
PDOL
9F 38 18 // PDOL. 18 (24 )
9F 66 ( 04) // Terminal Transaction Qualifiers (TTQ).
9F 02 ( 06) //
9F 03 ( 06) //
9F 1A ( 02) // ISO3166-1
95 ( 05) // Terminal Verification Results
5F 2A ( 02) // , , ISO4217
9A ( 03) // YYMMDD
9C ( 01) //
9F 37 ( 04) //
PDOL EMV Contactless Specifications Book C-1/2/3 Kernel 1/2/3 Specification.
PDOL , , , PDOL. ( ), 33 . PDOL 33 .
, — PDOL, . , 6985 Conditions of use not satisfied.
, PDOL , Terminal Transaction Qualifiers (TTQ). VISA, , VCPS 2.1.1. TTQ :
'F0 00 00 00'
TTQ .
MasterCard, , PDOL PAN- PDOL.
PDOL:
'80A80000238321F0000000000000000000000000000000000000000000000000000000000000000000'
80 A8 00 00 // GET PROCESSING OPTIONS (GPO)
23 // (35 )
83 // PDOL-
21 // PDOL- (33 )
F0 00 00 00 // Terminal Transaction Qualifiers (TTQ)
00 00 00 00 00 00 //
00 00 00 00 00 00 //
00 00 //
00 00 00 00 00 // Terminal Verification Results (TVR)
00 00 //
00 00 00 //
00 //
00 00 00 00 //
, , 77 SW2=9000. PAN-, . ()
PAN-
EMV, , , , PAN-.
PAN- :
- Track 2 Equivalent Data — 57. 0 19 , 13 (19 ). 57 13. 8 PAN-.
- Application Primary Account Number (PAN) — 5A. 8 , 5A 08. PAN .
- Track 2 Data — 9F 6B" — . 13 . PAN .
APDU- ( ? , )
'00 b2 01 1c 00'
'00 b2 01 0c 00'
'00 b2 02 0c 00'
'00 b2 01 14 00'
'00 b2 02 14 00'
'00 b2 04 14 00'
57 13 5A 08. 8 .
, .
PAN- -

10- , PAN- , «». , , , .
, 10- . , .
Arduino + PN532 breakout board.
: www.youtube.com/watch?v=aXNvjuRrCQk
Arduino, , : github.com/zhovner/Adafruit-PN532, examples/ApplePay_Troyka_ACS
, PDOL, - EMV- . .
Parsec
arduino raspberry pi, .
, , , .
, , Parsec.ru
PNR-P03E.
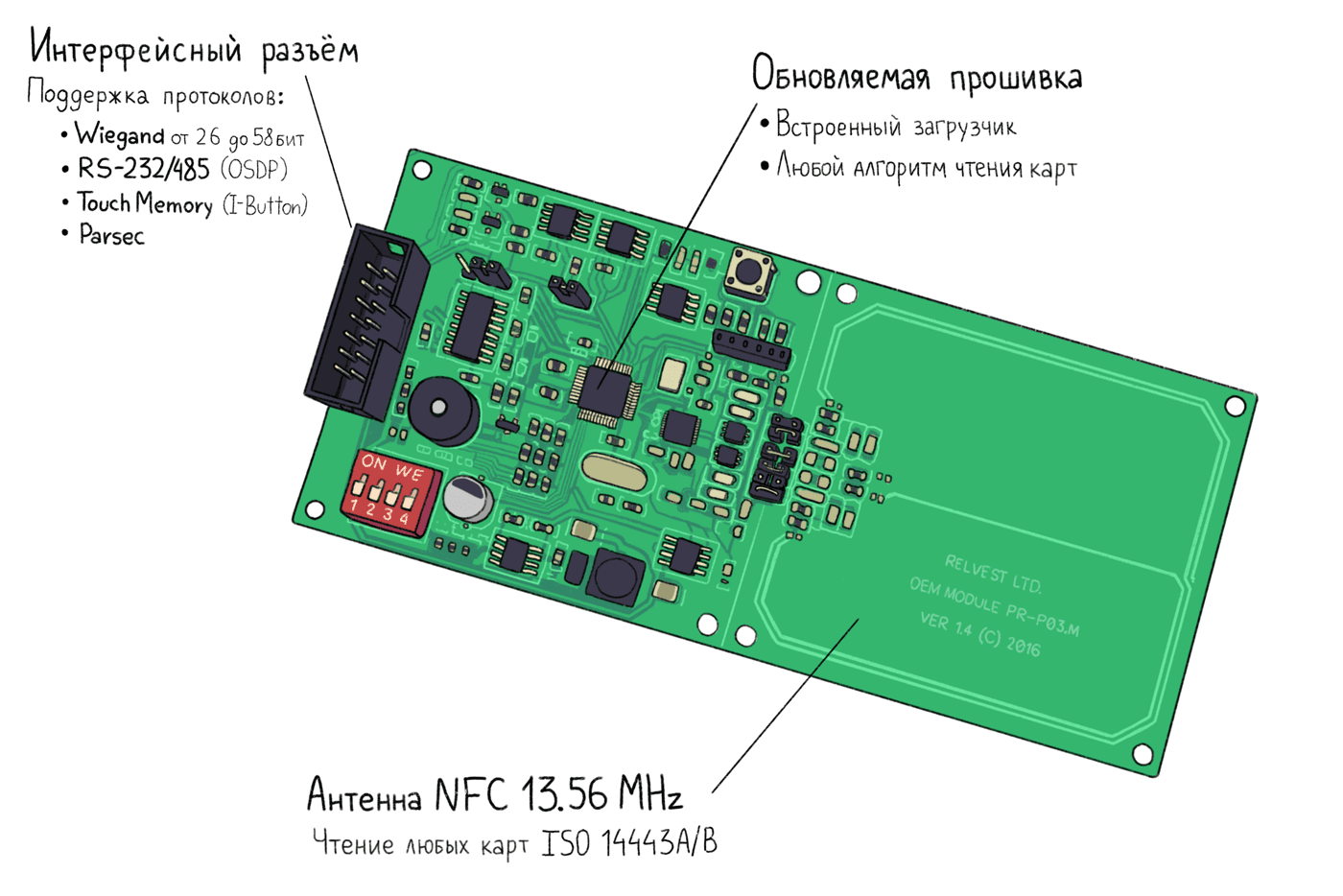
Parsec PNR-P03E
RFID-, , . Mifare, HiD iClass ..
, , EMV-.
PNR-P03E
- — , EMV, «» . .
- — : Wiegand 26 58 , OSDP (RS-485, RS-232), Touch memory (I-Button) Parsec
- — ,
- SDK —
-, . , Wiegand.
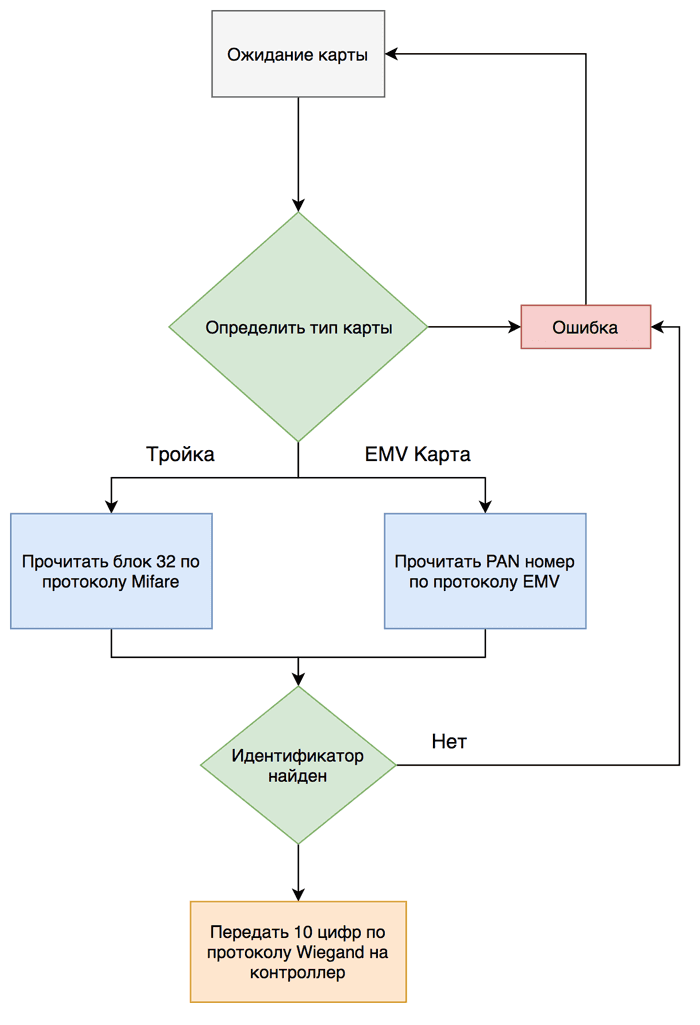
. , . .
— , . , , , .
. , API Telegram-.
, « ». rgmih , .
.
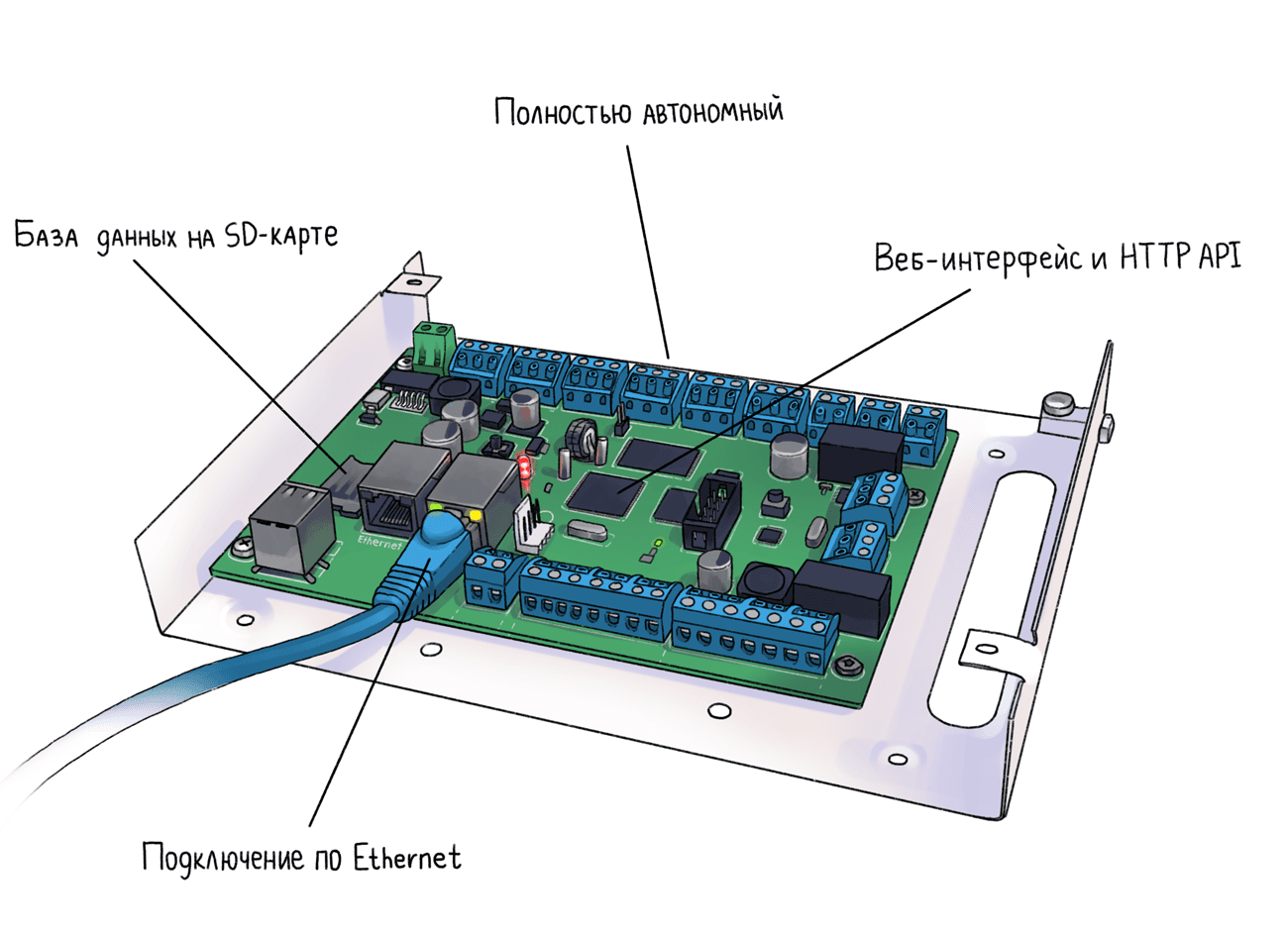
Linux ARM-.
, :
- — . . SD-. .
- Web REST API — Telegram- API. .
- Ethernet — IP-. 2 .
- 64 — . .
, Wiegand. , .
, . .
, , , .
c Ethernet-. IP- . , , .
« ». , .

-
- , . , , , .
Telegram
, - , Telegram , / . REST API.

Telegram-.
FAQ
, . :
- , ?
, , , . . - . - «» !
, . . ( Android c NFC ), Mifare. , , . , EM-Marine, - , ́ . - .
. EMV « EMV ». , : -, . - ( ) . , POS- , . POS-. -, . , , , — . - , , .
, . , , . CVV- . , , Apple Pay . , , , «». - EMV .
, EMV . ChameleonMini, . Android Host-based Card Emulation, Android . , .
, :
— aquamine
— ValdikSS
Telegram — Alexey Tsverov
— Parsec
— rgmih
Source: https://habr.com/ru/post/347574/
All Articles